Recently, the Zscaler ThreatLabZ team came across various phishing attacks leveraging Microsoft Azure custom domains. These sites are signed with a Microsoft SSL certificate, so they are unlikely to raise suspicion about their authenticity. We notified Microsoft, who quickly engaged to shut these sites down, while we took action to detect and block 2,000 phishing attempts from these domains over a six-week period.
In this blog, we will describe two of the prominent vectors used and we’ll show several examples of the phishing pages.
The following figure depicts the phishing hits that were hosted using the Azure domain (Windows.net) and blocked by the Zscaler cloud.
Fig 1: Phishing hits using the Azure domain web.core.windows.net (green) and blob.core.windows.net (orange)
The following is the Whois lookup information related to the Windows.net domain.
Fig 2: Whois lookup info for domain Windows.net domain
For these phishing campaigns, the delivery vector was spam emails.
CASE 1:
In this case, the attacker sends a spam email to a user, appearing to come from a particular organization and notifying the user that seven emails have been quarantined. It states that in order to review the emails, the user has to log in using the work or school account.
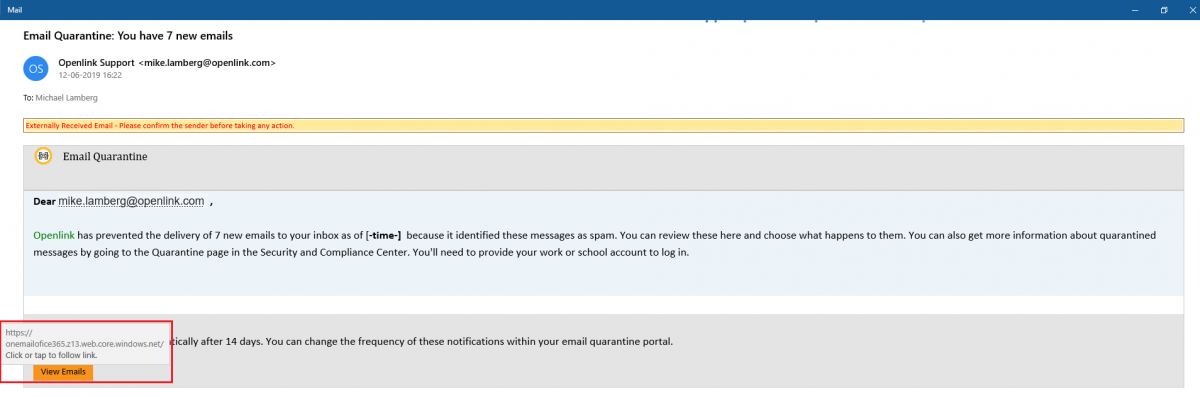
Fig 3: Spam email with direct phishing link
If the user clicks the view emails button, it will redirect to the Outlook login phishing page (hxxps://onemailofice365(.)z13(.)web(.)core(.)windows(.)net/index(.)html).
Fig 4: Outlook login phishing page
Some users may get confused because of the unknown URL hosting the Outlook login page. To trick those users, the attackers have used the SSL certificate issued by Microsoft as shown below.
Fig 5: SSL certificate page of the hosted phishing URL
The following figure depicts the source code of the phishing page, which is used by attackers to collect users’ data.
Fig 6: Source code of the phishing URL page
Once the login information has been entered by the user, the form will post the user’s credential details to the compromised domain that is operated by the cybercriminals.
Fig 7: Captured data traffic that has been sent to the attacker’s site
CASE 2:
In this method, attackers send the spam email with an attached HTML file that looks like a voice message. Once the user clicks the HTML file, it will redirect to the phishing page hosted using the Azure domain.
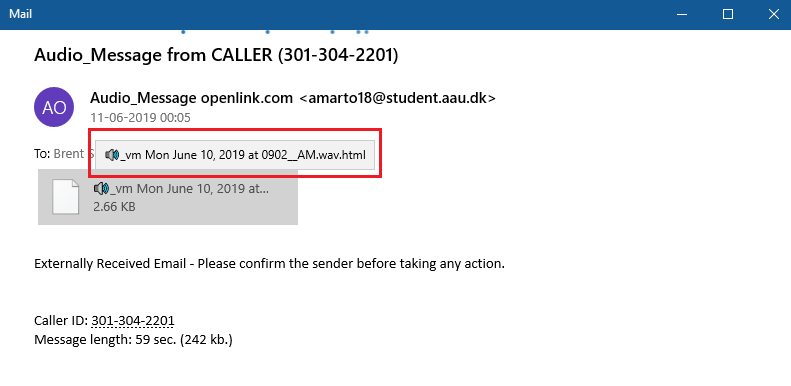
Fig 8: Spam mail with double extension method
Fig 9: Outlook login phishing page redirected from voice message
In this phishing campaign, the attackers have injected obfuscated JavaScript to validate the user credentials that are present in their database to avoid duplication.
Fig 10: Obfuscated JavaScript to validate user credentials to avoid duplication
The following figure depicts the deobfuscated JavaScript. This code will validate the user’s credential details and sent it to the attacker’s server (hxxps://validr2vtap2l3eh544kb(.)azurewebsites(.)net/v20(.)php).
Fig 11: Deobfuscated JavaScript
Fig 12: User data will be sent to the attacker’s site using the function getValidatorURL().
In addition to the Outlook phishing campaigns, we have seen phishing campaigns associated with these Azure domains:
Microsoft Phishing, OneDrive Phishing, Adobe Document Phishing, Blockchain Phishing, and more. The following figure shows the different phishing campaigns that are hosted using the Azure domain (Windows.net).
Fig 13: Microsoft login phishing page
Fig 14: Adobe login phishing page
Fig 15: Blockchain login phishing page

Fig 16: OneDrive login phishing page
Conclusion
The Zscaler cloud blocked more than 2,000 phishing attacks over six weeks that were hosted using the Azure domain (Windows.net). The following diagram represents the various kinds of phishing campaigns that were blocked by the Zscaler cloud.
Fig 17: Detected phishing hits
Fig 18: The Zscaler Zulu URL Risk Analyzer score for one of the phishing URLs
IOCs
039282fsd(.)z19(.)web(.)core(.)windows(.)net
3652adua38ea(.)z5(.)web(.)core(.)windows(.)net
378468459jjn(.)z19(.)web(.)core(.)windows(.)net
623623626638885047749469(.)z19(.)web(.)core(.)windows(.)net
86hoi2a8j592hf2(.)z14(.)web(.)core(.)windows(.)net
accounhostoutlook(.)z35(.)web(.)core(.)windows(.)net
accountsupdate(.)z22(.)web(.)core(.)windows(.)net
adobe111(.)z19(.)web(.)core(.)windows(.)net
appriver(.)z19(.)web(.)core(.)windows(.)net azaman(.)blob(.)core(.)windows(.)net
bchwalletblockchain(.)z13(.)web(.)core(.)windows(.)net
bitcoinwalletrecovery(.)z13(.)web(.)core(.)windows(.)net
blockchainofficesupport(.)z13(.)web(.)core(.)windows(.)net
blockchainrecoverywalet(.)z13(.)web(.)core(.)windows(.)net
blockchaintradindinvest(.)z13(.)web(.)core(.)windows(.)net
businessdrivefilesharing(.)z33(.)web(.)core(.)windows(.)net
dlgeus(.)blob(.)core(.)windows(.)net dlgneu(.)blob(.)core(.)windows(.)net
dlgweu(.)blob(.)core(.)windows(.)net driveoffice-
secondary(.)z13(.)web(.)core(.)windows(.)net
eastexch030serverdatanet(.)z13(.)web(.)core(.)windows(.)net
edustudioapp(.)z19(.)web(.)core(.)windows(.)net
exchangeonline80293745(.)z27(.)web(.)core(.)windows(.)net
finance51(.)z13(.)web(.)core(.)windows(.)net
fukshawefwe22(.)blob(.)core(.)windows(.)net
fundingmessan(.)z13(.)web(.)core(.)windows(.)net
gry1asdqw1(.)blob(.)core(.)windows(.)net
h0vbkkkeebweybv(.)z33(.)web(.)core(.)windows(.)net
hgnghhghkkdkdh(.)z13(.)web(.)core(.)windows(.)net
hp94549754083400j9302975(.)z21(.)web(.)core(.)windows(.)net
hsdv(.)blob(.)core(.)windows(.)net
linknec39cclzg5l591f(.)z19(.)web(.)core(.)windows(.)net
linkp4klg1qkni76yoz8(.)z19(.)web(.)core(.)windows(.)net
lpdmsonline(.)blob(.)core(.)windows(.)net
macrofinancesoftonline(.)z14(.)web(.)core(.)windows(.)net
macrosoft0nlineoffice365(.)z13(.)web(.)core(.)windows(.)net
mailingofficeupdate(.)z14(.)web(.)core(.)windows(.)net
mailofficemicr0softvalid(.)z35(.)web(.)core(.)windows(.)net
mailofficesecurity(.)z13(.)web(.)core(.)windows(.)net
mailofficeveridiers(.)z33(.)web(.)core(.)windows(.)net
mailoutlookmcrosoftupdat(.)z11(.)web(.)core(.)windows(.)net
mailoutnewsecurity(.)z14(.)web(.)core(.)windows(.)net
mak17opa54vjxu8(.)z7(.)web(.)core(.)windows(.)net
mdj34598720843(.)z10(.)web(.)core(.)windows(.)net
microexchyz42nhszseheys(.)z13(.)web(.)core(.)windows(.)net
micromuze3rlokoyg(.)z14(.)web(.)core(.)windows(.)net
microrel00ukelukleqwkoxl(.)z13(.)web(.)core(.)windows(.)net
microsofbt50xjotm45wm7al(.)z11(.)web(.)core(.)windows(.)net
microsofd8f82gtrjyaajnsj(.)z11(.)web(.)core(.)windows(.)net
microsofdi3o152rpnnt2zr8(.)z11(.)web(.)core(.)windows(.)net
microsoffn4xwr5df3emnh1m(.)z11(.)web(.)core(.)windows(.)net
microsofn642b7o2un27wptm(.)z13(.)web(.)core(.)windows(.)net
microsofq2622c5r3wpfsdnp(.)z11(.)web(.)core(.)windows(.)net
microsofzwafvh6bisrici50(.)z11(.)web(.)core(.)windows(.)net
offic664ghdtsgdyddux(.)z13(.)web(.)core(.)windows(.)net
officcee(.)z13(.)web(.)core(.)windows(.)net
office365user37773773673(.)z19(.)web(.)core(.)windows(.)net
officedelist(.)z13(.)web(.)core(.)windows(.)net
officefiledata(.)z13(.)web(.)core(.)windows(.)net
onemailofice365(.)z13(.)web(.)core(.)windows(.)net
outlookloffice365user23k-secondary(.)z14(.)web(.)core(.)windows(.)net
outlookloffice365user25u-secondary(.)z33(.)web(.)core(.)windows(.)net
outlookloffice365user65t-secondary(.)z6(.)web(.)core(.)windows(.)net
outlookloffice365user65t(.)z6(.)web(.)core(.)windows(.)net
outlookloffice365userl6m(.)z13(.)web(.)core(.)windows(.)net
outlookofficecom(.)z33(.)web(.)core(.)windows(.)net
outlookproctionmail(.)z9(.)web(.)core(.)windows(.)net
outwebsignin2094598209(.)z21(.)web(.)core(.)windows(.)net
parmalat7(.)blob(.)core(.)windows(.)net
pjkiojxyfngsss(.)z13(.)web(.)core(.)windows(.)net
pssastd(.)blob(.)core(.)windows(.)net
rel00ukelukleqwkoxl(.)z6(.)web(.)core(.)windows(.)net
sams2948818388301(.)z13(.)web(.)core(.)windows(.)net
secureofficeportal(.)z19(.)web(.)core(.)windows(.)net
sharepo7(.)z22(.)web(.)core(.)windows(.)net
sharepointewk8xpzoywq7j(.)z19(.)web(.)core(.)windows(.)net
supportoffices365(.)z33(.)web(.)core(.)windows(.)net
thursday(.)z19(.)web(.)core(.)windows(.)net
ttsokaejqumuamreio(.)z6(.)web(.)core(.)windows(.)net
under12(.)z19(.)web(.)core(.)windows(.)net
user111777999973sdxc(.)z11(.)web(.)core(.)windows(.)net
user37377377733(.)z22(.)web(.)core(.)windows(.)net
user7779793e792782(.)z14(.)web(.)core(.)windows(.)net
user8877773737(.)z11(.)web(.)core(.)windows(.)net
usernamewebmailsingin(.)z14(.)web(.)core(.)windows(.)net
v83oybtn5zp5mmz(.)z14(.)web(.)core(.)windows(.)net
validatnec39cclzg5l591f(.)z19(.)web(.)core(.)windows(.)net
voice88(.)z19(.)web(.)core(.)windows(.)net
voicserel00ukeluklwkoxl(.)z13(.)web(.)core(.)windows(.)net
webusermicr0softtonlinee(.)z33(.)web(.)core(.)windows(.)net
were12(.)z19(.)web(.)core(.)windows(.)net
weree(.)z6(.)web(.)core(.)windows(.)net
wimdowoutlkjxjy0846335f(.)z13(.)web(.)core(.)windows(.)net
yamma(.)z13(.)web(.)core(.)windows(.)net
zebra11(.)z19(.)web(.)core(.)windows(.)net
azaman(.)blob(.)core(.)windows(.)net
dlgeus(.)blob(.)core(.)windows(.)net dlgneu(.)blob(.)core(.)windows(.)net
fiattt(.)blob(.)core(.)windows(.)net
fukshawefwe22(.)blob(.)core(.)windows(.)net
gry1asdqw1(.)blob(.)core(.)windows(.)net
hsdv(.)blob(.)core(.)windows(.)net
parmalat7(.)blob(.)core(.)windows(.)net
funksha1(.)blob(.)core(.)windows(.)net




















