Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Subscribe
2023 ThreatLabz Report Indicates 400% Growth in IoT Malware Attacks
Introduction
This blog serves as a brief synopsis of the key points revealed in the Zscaler ThreatLabz 2023 Enterprise IoT and OT Threat Report.
Our report explores the growth of Internet of Things (IoT) device traffic and IoT malware attacks, in addition to how legacy vulnerabilities, targeted devices, and specific industries have become central players in the IoT and operational technology (OT) security narrative. In addition, the report outlines IoT security best practices and practical guidance for preventing IoT malware attacks.
The report also offers strategies to ensure the resilience of OT environments, spotlighting the convergence of IoT and OT driven by digital transformation in critical sectors such as manufacturing and utilities.
Growth in connected device traffic and IoT malware attacks
ThreatLabz research clearly indicates that IoT adoption remains on an upward trajectory, evidenced by an 18% increase in IoT device traffic compared to previous assessments in 2021. However, this expanding IoT ecosystem is not without its challenges. The ThreatLabz team analyzed approximately 300,000 blocked attacks on IoT devices and found a concerning surge in IoT malware attacks — 400% to be exact. Botnet activity continues to dominate the malware attack space, with the Mirai and Gafgyt malware families accounting for 66% of attack payloads.
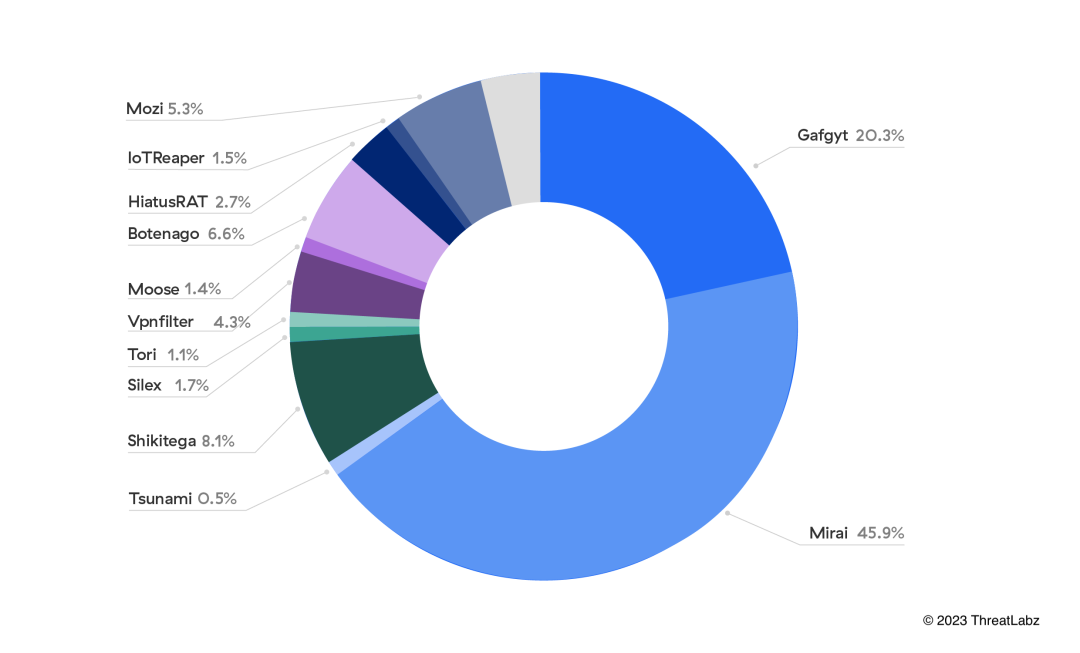
Figure 1: Top IoT malware families observed in the Zscaler cloud, January–June 2023
Manufacturing leads in unique IoT traffic and malware attacks
The manufacturing sector’s substantial lead in unique IoT devices, nearly tripling the count of other sectors. This surge in adoption underscores the industry’s dedication to embracing advanced automation and digitization, positioning it as a frontrunner in leveraging IoT for enhanced production efficiency, product quality, and innovation in the era known as Industry 4.0 or the Fourth Industrial Revolution. Industry 4.0 is characterized by the integration of digital technologies and industrial processes. IoT devices are the linchpin of Industry 4.0, providing real-time data and connectivity across the production chain. The convergence of IoT devices and data into existing OT systems is transforming industrial operations.
The explosive growth of technological innovation and IoT devices in manufacturing has made this sector a prime target for malware attacks.
On an average week, the manufacturing sector receives more than triple the number of attacks as any other sector. Manufacturing customers take the brunt of malware attacks at 54.5%. With a low tolerance for operational disruptions, manufacturing is high stakes for malware attacks. Attacks on manufacturing customers can have ripple effects that impact other sectors like:
- supply chain and logistics
- defense and national security
- finance
- retail
- technology
- construction and real estate
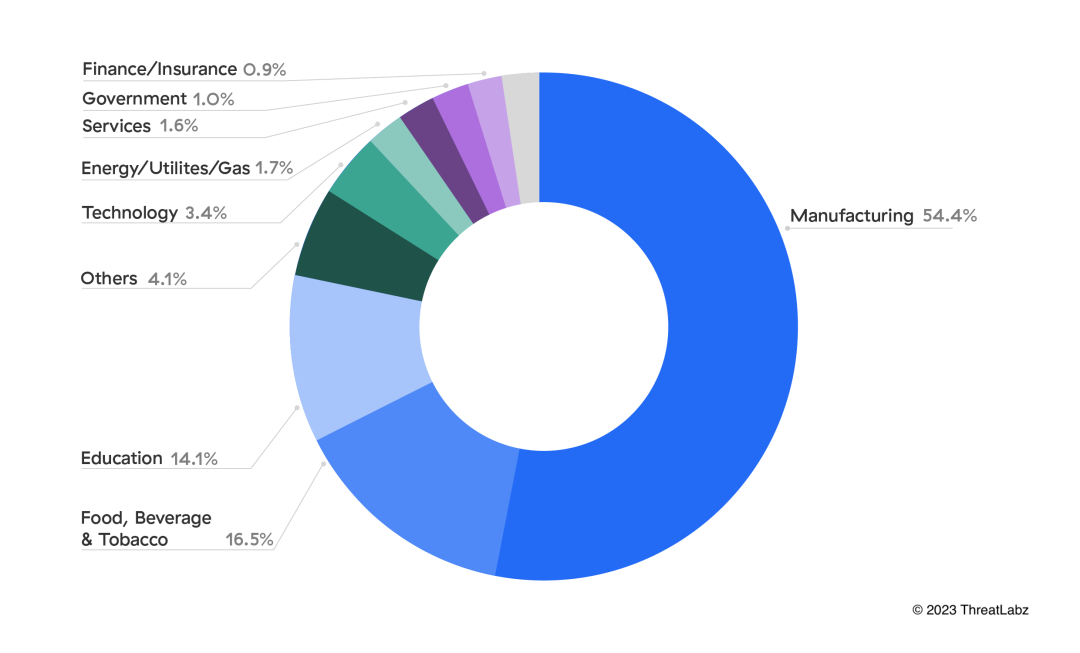
Figure 2: Breakdown of verticals targeted by IoT malware attacks
High attack volumes not only jeopardize IoT systems but also pose a serious threat to OT processes. Attacks on OT infrastructure can lead to severe disruptions in crucial industrial operations and, in some cases, even jeopardize human lives.
United States attracts the most malware authors
The United States boasts a robust and interconnected digital infrastructure that acts as a magnet for malware authors worldwide. Its extensive network and advanced technology ecosystem offer unparalleled opportunities for efficiently distributing malware, wreaking havoc with widespread impact, and ultimately compromising a wide range of systems to exploit vulnerabilities and propagate malicious software.
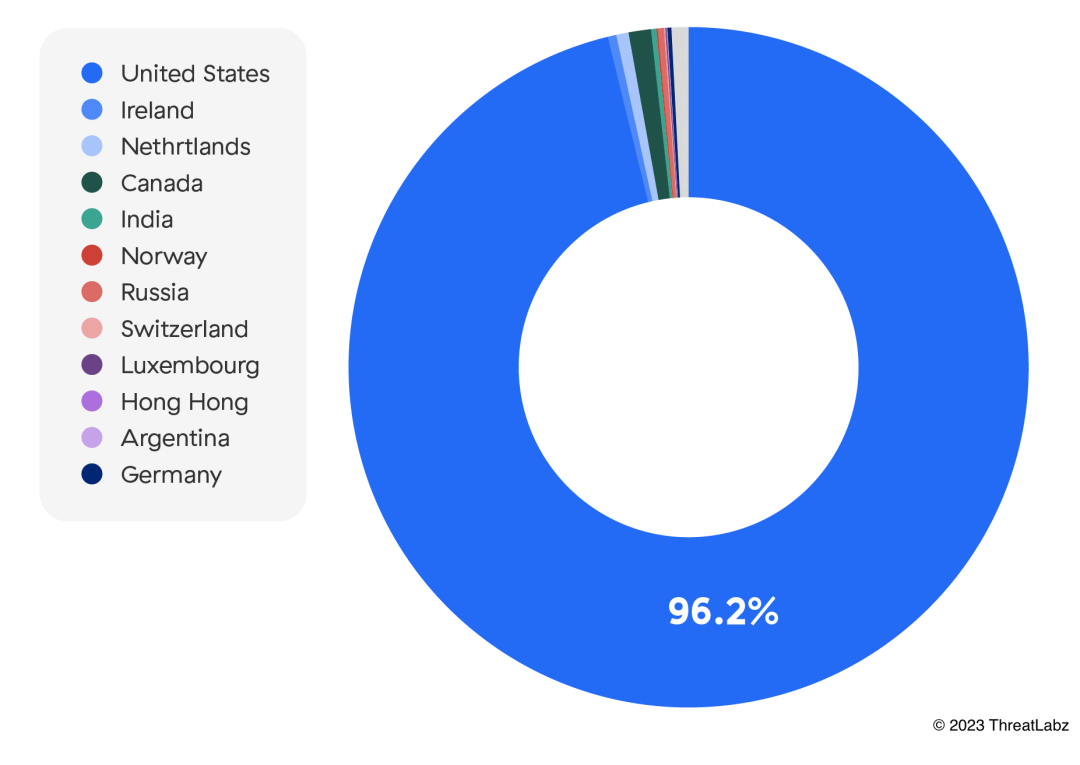
Figure 3: Top IoT malware targeted countries
IoT/OT Security Best Practices
Here is a preview of the IoT/OT best practices compiled by our team of cybersecurity experts. For the entire list of best practices, please download a free copy of the ThreatLabz 2023 IoT and OT Threat Report.
Maintain comprehensive visibility into IoT devices.
Securing IoT devices begins with knowing what devices are connected to your network and what those devices are doing. Gain visibility into all IoT devices, including unmanaged devices, by utilizing solutions that analyze network logs to monitor communications and activity. Continuous visibility and awareness of what is connected to the network at all times is critical, no matter where devices are located.
Protect admin credentials and enable MFA.
Multi-factor authentication (MFA) requires users to enter a secondary mode of verification in addition to their password. This extra layer of security can thwart attackers from gaining access to user accounts if they have obtained credentials, preventing lateral threat movement from compromised user devices.
Train employees on IoT device security.
Educate employees about the risks of connecting unauthorized devices to the network. Encourage them to report any new devices they connect and conduct security awareness training to help employees identify and avoid attacks on user devices.
Implement a zero trust security architecture.
For both IoT and OT, eliminate implicit trust. Enforce segmentation with least-privileged access to ensure users and devices can access only what they need. Any unsanctioned shadow IoT devices that need internet access should go through traffic inspection and, ideally, be blocked from corporate data via a proxy.
Zero trust is also key to preventing unplanned downtime and ensuring maximum productivity in industrial systems. Zero trust can minimize your attack surface, eliminate lateral movement, and accelerate OT/IoT convergence.
Conclusion
The convergence of IoT and OT represents a pivotal time in the evolution of technology and industry, propelled by the ever-increasing adoption of IoT, connectivity, and innovation. However, as we have seen, it also opens new avenues for cyber threats that can disrupt critical operations, as discussed in the Zscaler ThreatLabz 2023 Enterprise IoT and OT Threat Report.
As we move forward, it’s vital to remain vigilant and proactive in implementing security measures to ensure a safe and secure interconnected digital world. Zscaler ThreatLabz publishes this report year after year to help organizations recognize the importance of robust security measures and safeguarding our interconnected future.
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



