I've recently noticed a number of transactions to:
vvvvvv.dyndns-mail.com/
46.254.16.61 (PTR: www.asl-s.com)
Update: we're now seeing this attack hosted as well on:
blog.dyndns-blog.com
googlepics.dyndns.tv
whitehorse.dyndns-server.com
everybodythere.dyndns-blog.com
smalloffice1.dyndns-office.com
alwaystv.dyndns-free.com
showmustgoon.dyndns.info
webarchive.dyndns-web.com
Some of the transactions have referer strings from pages from a number of sites (i.e., these sites are compromised/hosting content that links to the attack pages), for example:
www.crescent-news.com
www.trainingmag.com
*.ejecentral.com.mx
www.louisville.com
www.investmentu.com
www.the-daily-record.com
www.tennispoint.com
www.recordpub.com
blog.eduzones.com
www.planodevivienda.com
www.surfnewsnetwork.com
(ads.)moneymorning.com
www.gooofullsearch.com
www.smartautosavings.com
www.times-gazette.com
www.daily-jeff.com
www.twinsburgbulletin.com
www.rvag.com
www.mimusicagratis.net
www.gooofull.com
elpartidodehoy.es
www.linuxforums.org
www.newtvsoft.com
(the list goes on ... I'll make additions with the more interesting sites as I see them)
Some of these sites are also blocked by GSB, but initially I was not able to
track down the malicious content. Fortunately Wepawet was able to help me through the maze of content being loaded on the pages. The report is visible here.
googlepics.dyndns.tv/news/1997
whitehorse.dyndns-server.com/news/1997
blog.dyndns-blog.com/news/1997
vvvvvv.dyndns-mail.com/news/1997
--->
Unfortunately it doesn't appear that the Wepawet sandbox falls victim to the exploit or is able to actually obtain a malicious payload from this. I'll analyze the HCP parameter / exploit further and include any information I find about the payload.
Update:
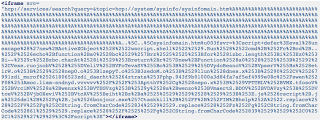
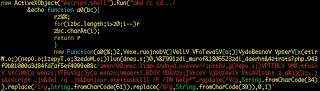
Here's the first stage decode of the payload (spaced to read better):
 Uses cscript.exe (command-line version of Windows Script Host) to run commands that are "echoed" to a file ".js" which downloads contents from:
Uses cscript.exe (command-line version of Windows Script Host) to run commands that are "echoed" to a file ".js" which downloads contents from:hxxp://vvvvvv.dyndns-mail.com:80/news/c80e9994fe5fa7af48d3a00010b9f349.php?start=4&thread_id=3256081&forum_id=1997&
and stores them into a file bonjour.exe at the root directory. This executable is then launched and all processes containing the string "help" are forcefully killed.
Unfortunately, I have not been able to directly download the executable payload from vvvvvv.dyndns-mail.com, I keep getting a 302 response to Google.
There is also a Java attack being served from this exploit kit - possibly Incognito,
but I can't access the control panel: hxxp://blog.dyndns-blog.com/admin.php (I get an "error 3" text response).
Sample of .jar file drops:
vvvvvv.dyndns-mail.com/news/8db59781b281e80e1284a8847f73d58d.jar
blog.dyndns-blog.com/news/8db59781b281e80e1284a8847f73d58d.jar
blog.dyndns-blog.com/news/ef36787f21fb429c4c7cb2212902dcbd.jar
blog.dyndns-blog.com/news/09ec45a029f86af501a1391c2a6e781c.jar
Note: I've tried to download the executable payloads spoofing the referer / user-agent and coming from different hosts without success. It is possible that the hash value filename is time or source sensitive.
Had a friend send me a copy of the binary:
V/T Report: 2/41
ThreatExpert Report shows network connectivity to:
67.18.166.173:10000/load.php?file=#
where # = 0-19 (possibly piecemeal malware building)
81.177.33.95/forum.php
Here's an earlier variant (April 12, 2011) of the malware that I was able to find, however it is just as elusive at being pinned to a specific malware family:
V/T Report: 9/42
ThreatExpert Report, network activity:
summer-ciprys.com/load.php?file=#
joomla-desing.com/admin.php