Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Subscribe
VPN vs. ZTNA: Which is Better for Secure Remote Access?
With this blog, we’re going on a journey that presents twists and turns as we compare two means of securing hybrid workforces and their access to applications, data, and other internet-based services: zero trust network access (ZTNA) and virtual private networks (VPN). Both have clear advantages, but only one provides security that scales without widening the attack surface while eliminating the costs of legacy network security tooling.
VPN vs. ZTNA for securing the hybrid workforce
Organizations adoption of hybrid work and cloud computing means both employees and applications are distributed physically and virtually. In this context, a perimeter-focused security strategy is no longer a viable approach to safeguarding organizations against an evolving threat landscape. Adopting a proactive security approach is a must—not an option.
VPNs and ZTNA are two primary means of securing both users and data—but they are very different approaches, so which is right for your organization? Let’s examine the pros and cons of each along with common use cases.
Virtual private networks secure access, but create latency issues
A virtual private network creates a secure and encrypted connection over a network—and in the age of hybrid work, the internet has become an extension of the corporate network. Employees use VPN to connect to a corporate network and its resources from wherever they’re located. This enables them to access applications, files, databases and other resources as if they were in the office.
VPNs also protect users' online privacy by masking their IP addresses and encrypting internet traffic. Companies have deployed VPNs since the ‘90s as a means of securing remote connectivity so that data transmitted over the internet remains private and secure. Sensitive information, such as financial data, customer details and confidential communications, stay protected when employees work remotely or when sharing data with partners and clients—even when using untrusted public networks.
Sounds good, right? It does on the surface, but let’s look at the tradeoffs of using VPN. Here’s a quick-hit list of VPN advantages:
- Enhanced security: VPNs provide an encrypted connection, protecting data in transit from being intercepted or monitored by unauthorized parties. This is crucial when remote staff use public Wi-Fi networks, which extend the attack surface since they are vulnerable to hacks that lead to data breaches.
- Protect privacy: By masking the user's IP address and encrypting internet traffic, VPNs help protect users' online privacy. They prevent internet service providers (ISPs) and websites from tracking browsing activities, making it more difficult for third parties to collect personal information.
- Enable remote access: Remote workers and business partners can securely connect to corporate networks from anywhere. This facilitates remote work, collaboration, and access to resources.
- Encrypt data: VPNs encrypt all data transmitted between the users’ devices and a VPN server, making it difficult for threat actors to decipher sensitive information.
VPNs impact productivity and create management overhead
VPN deployment and usage does introduce significant issues for both IT teams and end users:
Complex configuration and management: Setting up a VPN can be difficult for less experienced IT staff, especially when dealing with advanced configurations.
Latency impacts the user experience: VPNs require backhauling user traffic through a data center which means data must travel farther, impacting web app performance.
Connectivity issues result in slower performance: VPN connections may occasionally experience disruptions or unstable connections or slower performance. This can frustrate your staff, especially when they need to get something done quickly.
ZTNA provides secure access to apps, data, and other cloud resources
Zero trust network access is an architectural approach that challenges the traditional network security model with a core principle of "never trust, always verify": this is shorthand for no user or device being inherently trusted and access to applications is granted only to authorized users with continuous verification. This model ensures that users are granted the least amount of access required to perform their work tasks, minimizing the potential attack surface and reducing the risk of unauthorized access.
How organizations can apply ZTNA operationally across industries
There are many scenarios where applying ZTNA secures users, apps and data while ensuring the highest level of security. Here a few examples:
- Consistent security controls across multicloud environments: In multicloud architectures, ZTNA helps manage access to resources across different cloud service providers, ensuring consistent security policies and access controls.
- Internet of things (IoT) security: By enforcing strict access controls and device authentication, organizations can prevent unauthorized access to IoT infrastructure.
- Healthcare and Financial Services: These industries have strict data privacy regulations and benefit from ZTNA by ensuring secure access to sensitive information while meeting regulatory compliance.
- Government and Defense: Government agencies can protect classified information and prevent data breaches by ensuring that only authorized personnel can access critical systems and data stores.
- Education: these institutions can secure access to student records, research data, and administrative systems, protecting sensitive information from unauthorized access.
Requirements for zero trust network access
The advantages of ZTNA are significant and leveraging them requires planning with a phased approach to adopt this new architecture. These challenges are summarized below. Zscaler works closely with customers so they can ramp up quickly with ZTNA while significantly reducing IT costs:
- Implementing ZTNA requires planning to implement, especially in large and established networks. Zscaler mitigates this with our team’s thorough understanding of network architecture, user roles, and application dependencies and more, all so our customers can ramp up quickly and realize fast time-to-value. Moreover, our platform’s architecture and deployment generally requires no hardware; only a small software agent called the Client Connector that is deployed on endpoints to route traffic to our global security cloud. The Zero Trust Exchange acts as a switchboard to continuously evaluate users’ identity, behavior, and device posture as well as inspect content and apply policy to prevent threats from reaching the endpoint.
- Transitioning from a traditional network architecture to a zero trust model may require changes in infrastructure, policies, and user access procedures—all of which require time and resources to adapt. Zscaler works with customers using a phased approach to adopting ZTNA and has done so for many organizations globally across various industries. Due to our expertise in ZTNA and the technical advantages of our platform, we can get customers up and running in just days or weeks.
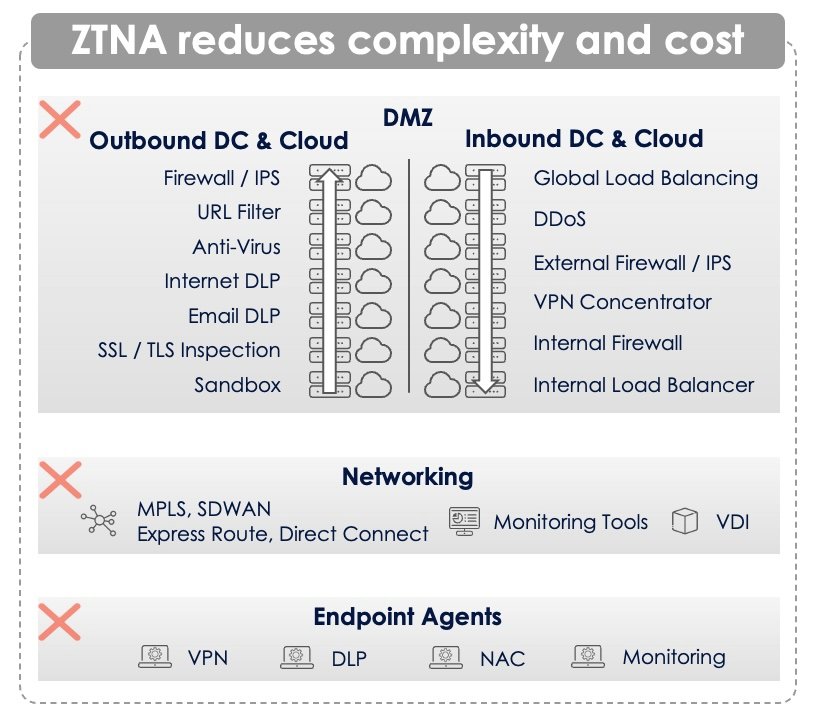
- Investing in ZTNA involves an upfront purchase of new software and services. With Zscaler, customers can eliminate IT costs while leveraging industry-leading security. Our platform’s architecture and protective capabilities remove the need for many inbound and outbound DMZ legacy devices and services such as firewalls, VPN concentrators, MPLS routers, DDoS, and VDI to name a few, resulting in a rapid return on investment.
ZTNA vs. VPN
Now that you understand the pros and cons of both VPNs and ZTNA, let’s directly compare the two through the lenses of security, management, scalability, performance and ease of use. The table below provides a summary of these considerations:
Security Advantages: | |
ZTNA ZTNA provides a more robust security model by enforcing strict access controls, continuous verification, and the principle of least privilege. It minimizes the attack surface by granting users and devices the minimum access required. This significantly reduces the risk of data breaches and lateral movement within the network. | VPN VPNs offer secure encrypted tunnels for data transmission, protecting users from unauthorized access and monitoring, especially on public Wi-Fi networks. They can ensure privacy and secure remote access to a company's internal network when users are within a defined perimeter. |
Management: | |
ZTNA ZTNA provides centralized management and control over user access policies, making it easier to manage and enforce security policies. Administrators can define granular access controls and continuously monitor user activities. Setup and migration to a ZTNA model requires careful planning and understanding of user roles and application dependencies. | VPN VPNs are relatively straightforward to manage for basic remote access scenarios. VPN servers can be configured to allow or deny access to specific users or networks. Managing a large-scale VPN deployment can become complex, especially when dealing with multiple remote locations and a diverse user base. Configuring and maintaining VPN clients on various devices can also be challenging. |
Scalability: | |
ZTNA Highly scalable due to its granular access controls and micro-segmentation capabilities. It can easily accommodate growths in users, devices, and applications without compromising security. ZTNA architecturally is designed to handle large-scale deployments efficiently. Since authorized users can only access the apps and data necessary for their job functions, this minimizes the attack surface. | VPN VPNs struggle to scale, especially when a large number of users connect simultaneously. Scaling a VPN infrastructure often involves adding more VPN servers, which can be costly and complex to manage and extend the attack surface since these devices have active “listeners” for new connections, making them targets for threat actors. |
Performance: | |
ZTNA ZTNA has minimal impact on network performance since it is designed to optimize access to specific applications and resources. The microsegmentation-based approach ensures that network traffic is directed efficiently. | VPN VPNs require backhauling traffic to a remote data center and thus introduce latency and slow down internet speeds, especially when using servers located far from the user's physical location. |
User experience: | |
ZTNA For end users, ZTNA is transparent; they may not even be aware of the security measures in place. Once authenticated, users can access authorized resources seamlessly. | VPN VPNs are generally easy to use for basic remote access scenarios. Users typically need to install a VPN client and connect to the VPN server with their credentials. However, configuring VPN clients on various devices and managing access for a diverse user base can be challenging for IT teams. |
In summary, ZTNA offers a more modern and robust security framework with granular access controls, making it highly secure and scalable. VPNs, on the other hand, provide a simple solution for secure remote access and privacy protection, but face challenges with scalability and performance.
Transitioning to ZTNA is a journey that will pay dividends with security that scales while reducing IT cost
At Zscaler we know the road to zero trust is a journey that requires planning and thoughtful implementation. This means ZTNA adoption often happens in phases, not all at once. Transitioning from VPN to ZTNA can occur in steps:
- Assessment: Evaluate your current security needs and IT stack, then identify areas where ZTNA can provide better protection and seamless access to the apps and internet-based resources.
- Planning: Develop a migration plan that includes timelines, resources, and training for your IT team.
- Implementation: Deploy ZTNA solutions gradually, starting with critical applications and data.
- Testing: Conduct thorough testing to ensure that the new system meets your security and performance requirements.
- Training: Provide training for end users to familiarize them with the new authentication processes.
By following these steps, you can successfully transition to ZTNA and enhance your organization's security posture.
Congratulations dear reader, you’re well along the path of understanding the advantages of ZTNA over VPNs! Now you know that when compared to VPNs, ZTNA is a more robust and scalable solution for securing the hybrid workforce, making it a worthwhile investment for modern enterprises.
With Zscaler’s architecture that leverages the world’s largest security cloud with over 160 edge nodes, you’ll save money by leaving legacy network security tooling behind and embracing a true zero trust architecture that will scale as your business grows.
Learn more by scheduling a demo with our zero trust experts.
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




