Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Isolating Encrypted Threats to Cloud Browser when SSL/TLS inspection is not fully enabled
SSL/TLS inspection
With the increasing popularity of cloud SaaS applications more and more sensitive data is exchanged over the internet, as a result of this it is imperative to ensure that the data is transmitted privately and without modifications, loss or theft. SSL/TLS encryption has emerged as a clear winner and has been widely adopted by both client and server side software to ensure confidentiality of the data exchanged. Especially with most SAAS and other internet based applications adopting web access, all major browsers and web content providers on the internet today exchange data securely over the internet using the HTTPS protocol which is HTTP over TLS/SSL . Unfortunately, in hindsight, HTTPS can not only be used to encrypt confidential data for secure exchange over the internet, but be used to hide threats.
As per Google's Transparency Report, more than 94% of webpages accessed from chrome browser are over HTTPS. According to Zscaler Threat Labs, encrypted threats have surged by 87% annually, highlighting the urgent need for robust security measures.
Considering the majority of the traffic is TLS encrypted it is imperative that inline security solutions such as Secure Service Edges employ SSL inspection techniques to allow organizations to scan and enforce policies to ensure that the transacted traffic is free of threats and curtail any attempts to leak confidential data.
Benefits of SSL Inspection
Implementing SSL inspection on a SASE solution allows organizations to keep their end users, customers, and data safe, with the ability to:
- Prevent compromise by performing inline scanning of the transacted data to find hidden malware and other malicious payload.
- Monitor and control confidential/sensitive data being sent outside the organization, intentionally or accidentally by the virtue of enforcing granular DLP policies.
- Meet regulatory compliance requirements, ensuring employees aren’t putting confidential data at risk
- Support a multilayered defense strategy that keeps the entire organization secure
While it appears to be a no-brainer that every organization should enable ssl inspection, organizations often experience challenges in implementing the same.
Potential Challenges in Implementing SSL/TLS Inspection
1. Testing and Validation: Enabling SSL inspection involves rigorous testing and validation to ensure website compatibility and functionality. For large enterprises, this can be a daunting task.
2. IT Environmental complexities: Conducting SSL/TLS inspection in complex environments might be a challenge. These challenges could be on the PKI infrastructure needed to perform SSL inspection or could be as simple as complexities in deploying the necessary certificates to the end user devices.
3. Compliance and Regulatory Requirements: Various countries have specific regulations that prohibit SSL/TLS inspection of users' web transactions to protect privacy. While these regulations aim to safeguard user privacy, they inadvertently accept the risk of encrypted threats, creating a potential security vulnerability.
4.TLS/SSL configurations:
The website TLS settings for bypassing SSL/TLS inspection are the use of non-standard ciphers, unsupported SSL/TLS versions, and encrypted Server Name Indication (SNI) with TLS 1.3,etc.
These challenges either completely deter an organization from enforcing TLS inspection or could result in significant delays in adopting TLS inspection exposing the organization to encrypted threats for extended periods of time.
Is there a security cover that an organization can adopt to reduce their risk exposure for the duration of time while organizations perform the necessary groundwork to enable TLS inspection?
Inspection Alternative via Cloud Browser Isolation
There are two schools of thought when it comes to security
Security by Inline Scanning: Where every packet of data exchanged is intercepted, decrypted, scanned and enforced with policies. The payload is inspected and matched against signatures, patterns or behaviors to detect and block threats.
Security by Confinement: The other approach to security is Isolation. In this school of thought, the content is not inspected to identify and block threats based on signature and behavior, instead an secure ephemeral vaulted environment is provided to the user to access the content of his choice. The content accessed from the secure environment could be malicious or benign, irrespective the content is confined to the secure environment and completely isolated from the user’s end machine and the corporate network.
Cloud Browser Isolation follows the concepts of security by confinement explained above. Browser Isolation provides an organization the capability to isolate users from potentially harmful content on the internet. This is done by loading the accessed web page on a remote ephemeral browser in any one of the many Zscaler data centers across the globe, and streaming the rendered content as a stream of pixels to the user’s native browser. The actual content served by the webpage accessed is always confined to the isolated browser on the Zscaler cloud and never makes it down to the user’s computer or the corporate network.
Zscaler Cloud Browser Isolation:
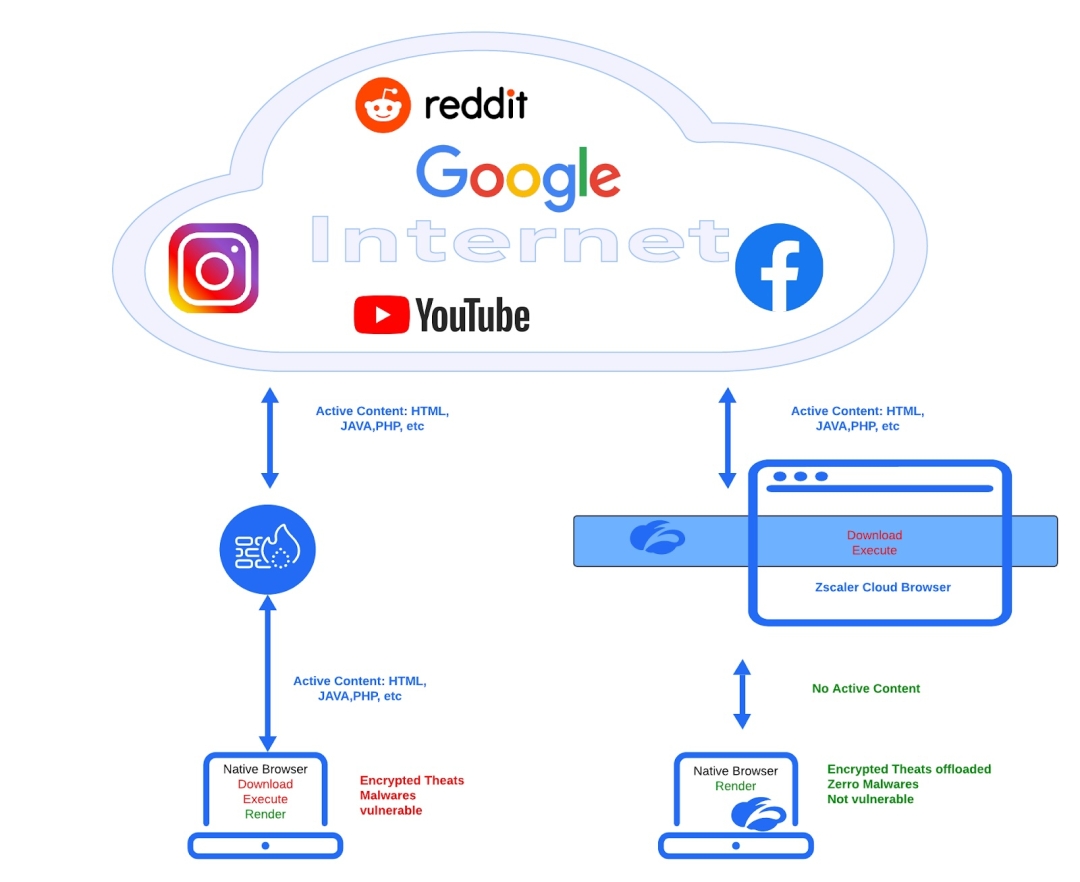
In addition to isolating the web content on the remote browser and creating the airgap between the user and the isolated webpage, cloud browser isolation allows an organization to enforce additional controls to protect data exfiltration and secure processing of web content.
Some of the key Data Exfiltration controls that browser isolation allows you to accomplish are
- File transfer Controls (Uploads & Downloads)
- Clipboard Controls
- Print Controls
- Read Only Webpage Access
Some of the key security capabilities that browser isolation offers from the perspective of threat protection are
- Ability to view Office and PDF documents in the isolated environment.
- Download Secure Flattened PDF copies of documents rendered in isolation.
- Achieve Level 3 CDR by out of band submission of files.
- Out of Band submission of files to sandbox.
All these above controls can be enforced without the organization having to perform MITM SSL inspection.
Browser isolation is not to be construed as an alternative to full inline TLS inspection, however can serve as an excellent layer of security when an organization goes through the journey of adopting TLS Inspection.

Videos
No SSL inspection
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



