Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Subscribe
Enhancing Zero Trust Security for Unmanaged Devices with Google Chrome and ZPA
The rapid adoption of web-based applications is transforming the way businesses operate. With the growing prevalence of remote work, contractors, gig workers, and bring your own device (BYOD) models, security teams are increasingly challenged with providing secure access to sensitive applications for unmanaged devices.
Key concerns include the lack of control over unmanaged devices, increased risk of data exfiltration, and the complexity of implementing security controls. These issues can negatively impact the user experience and drive up operational costs.
According to a report by research firm Gartner,
By 2030, Enterprise browsers will become the core platform for delivering workforce productivity and security software on devices.
Enterprise browsers enable conditional access policies restricting web application access to authorized employees and contractors connecting through the browser using an endpoint with a healthy security posture.
The Gartner report highlights the transformation of browsers from a productivity tool to a core enterprise platform.
Introducing zero trust security for unmanaged devices with Chrome Enterprise Browser and ZPA
The integration of Chrome Enterprise Browser with Zscaler Private Access (ZPA) enables easy and secure onboarding of contractors and third-party users to access private applications. Security teams can onboard users in minutes instead of days, reducing delays, improving security, and streamlining business operations.
Key benefits of this integration:
- Seamless user experience: The browser, familiar to billions of users, transforms into a secure enterprise application when users log in. Users can access private applications directly through Chrome Enterprise Browser while retaining their browser preferences. Once their work is done, they can securely log out, removing the need to manage contractor devices.
- Enhanced security: The access engine checks for Chrome Enterprise Browser and various posture signals before providing access to critical applications. Organizations gain real-time visibility into user activity when accessing applications. This enables data loss prevention (DLP) and post-encryption security, ensuring that sensitive data remains protected even after the user session ends.
- Reduced complexity: By leveraging the device trust connector (DTC) architecture, Chrome and ZPA handle the complexities of user security management. Security administrators can easily define policies, verify the security posture of unmanaged devices, and activate DLP with just a few simple steps. As a result, user onboarding can be completed in minutes, significantly reducing operational costs and complexity.
Technical architecture: Integration of Chrome Enterprise Browser and Zscaler Private Access
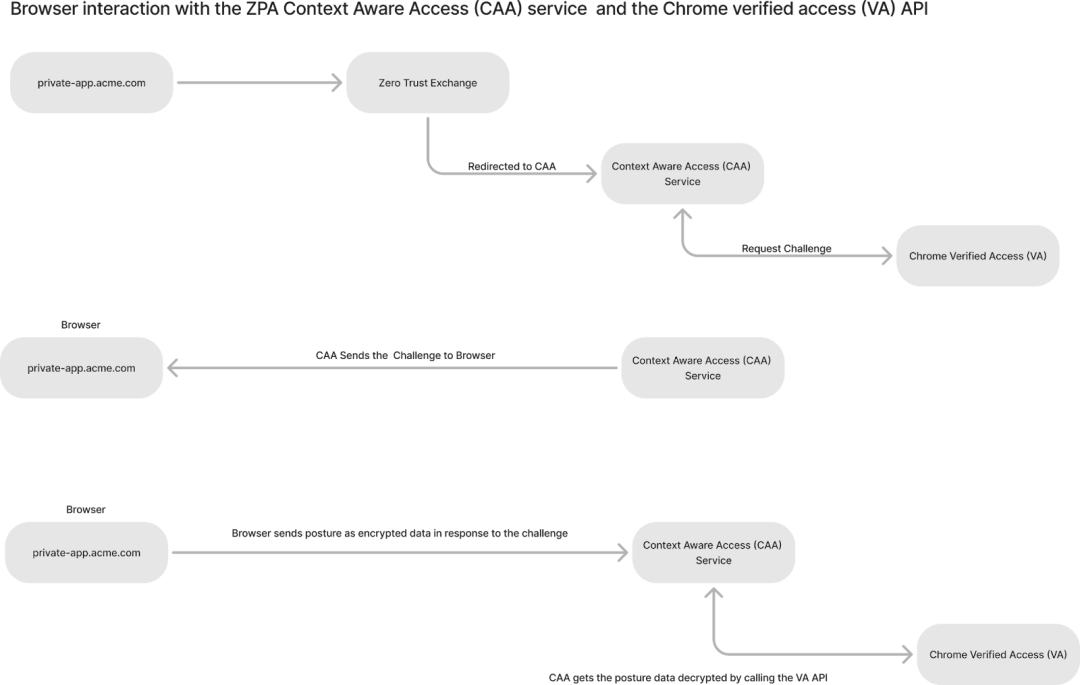
1. Chrome DTC and ZPA Context Aware Access (CAA) service
The Chrome DTC interacts seamlessly with the Zscaler Zero Trust Exchange platform to share device posture information, enabling secure access based on predefined policies.
When a user attempts to access a private application (e.g., by entering private-app.acme.com into their browser), the request is first routed to the Zscaler platform. To handle this interaction, Browser Access needs to be configured (Link). Upon receiving the request, the Zscaler platform forwards it to the CAA service for further validation.
The CAA service initiates the security workflow by calling the Chrome Verified Access API, which generates a challenge. This challenge is sent to the browser, which responds with encrypted posture information. The CAA service then forwards this encrypted response to the Verified Access API service, which decrypts it and sends the device posture data to CAA service. Once the CAA service receives this verified posture information, it checks the access policy to determine if the device meets the required conditions for accessing the requested application.
This secure flow ensures that only devices meeting posture requirements are allowed access, reinforcing the zero trust architecture.
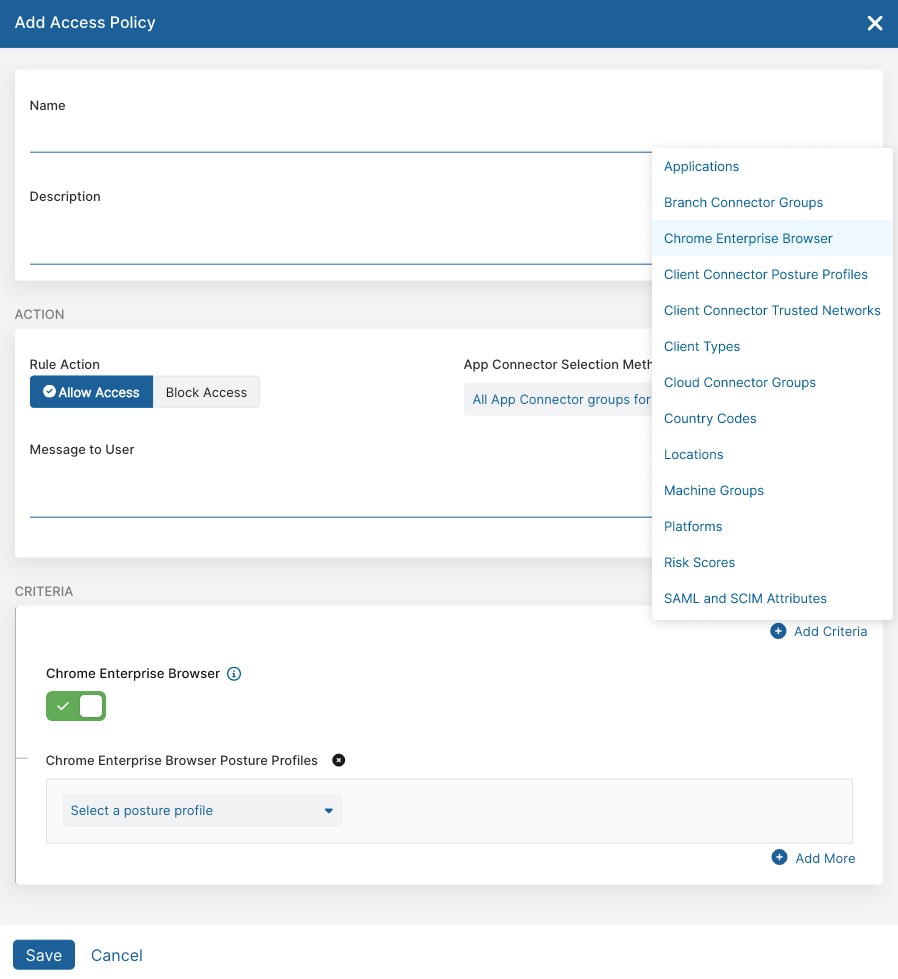
2. ZPA security policy definition
Once the user is authenticated and verified as using the Chrome Enterprise Browser, the ZPA policy engine can optionally conduct further posture checks before granting access. These posture checks ensure that the device complies with security requirements, reinforcing the zero trust architecture.
ZPA security administrators have the flexibility to create detailed posture profiles, which consist of various key-value pairs that define the criteria necessary for accessing specific applications. These profiles may include device attributes, security settings, or other critical posture elements that align with the organization’s security policies.
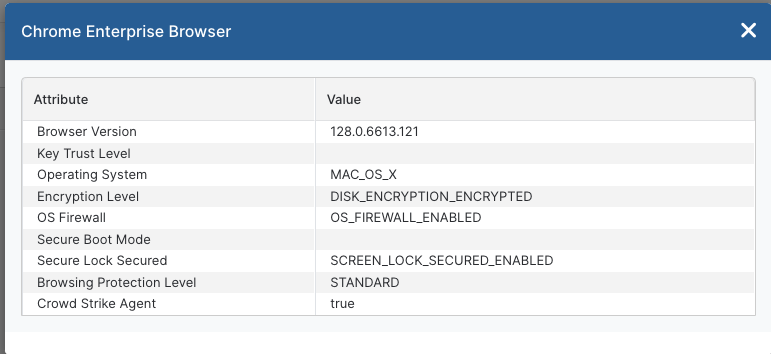
Example: Posture information that will be sent to ZPA for evaluation via the DTC
Name | Key | Value |
Browser version | browser_version | 126.0.6478.127 |
Key Trust level | key_trust_level | CHROME_BROWSER_HW_KEY |
Operating System | operating_system | MAC_OS_X |
Disk Encryption | disk_encryption | DISK_ENCRYPTION_ENCRYPTED |
Host Firewall | os_firewall | OS_FIREWALL_ENABLED |
Boot Mode | secure_boot_mode | SECURE_BOOT_MODE_ENABLED |
Screen Lock | screen_lock_secured | SCREEN_LOCK_SECURED_ENABLED |
Safe Browsing | safe_browsing_protection_level | STANDARD |
EDR | crowd_strike_agent | true |
Example: Policy definition in ZPA
3. Advanced security controls
Zscaler and Chrome come together to deliver advanced security and data protection capabilities, ensuring complete control over sensitive data, even when it’s accessed from unmanaged devices. With Chrome Enterprise Browser and ZPA, organizations can implement robust DLP controls to prevent data leakage.
Key features include:
- Print controls: Prevent unauthorized printing of sensitive documents, ensuring that confidential data isn’t exposed through physical means.
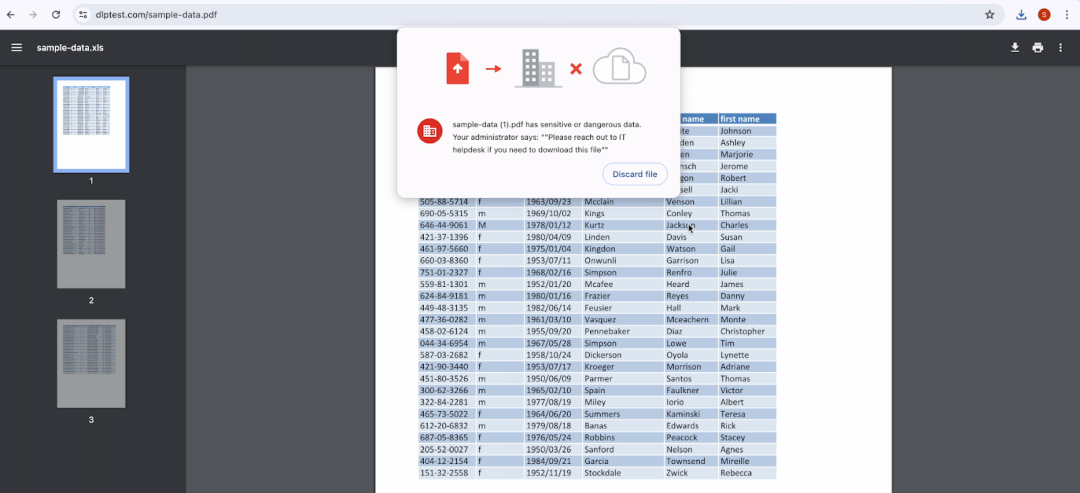
- Upload/Download controls: Restrict unauthorized downloads and uploads, protecting sensitive data from being inadvertently or maliciously transferred to unsafe locations.
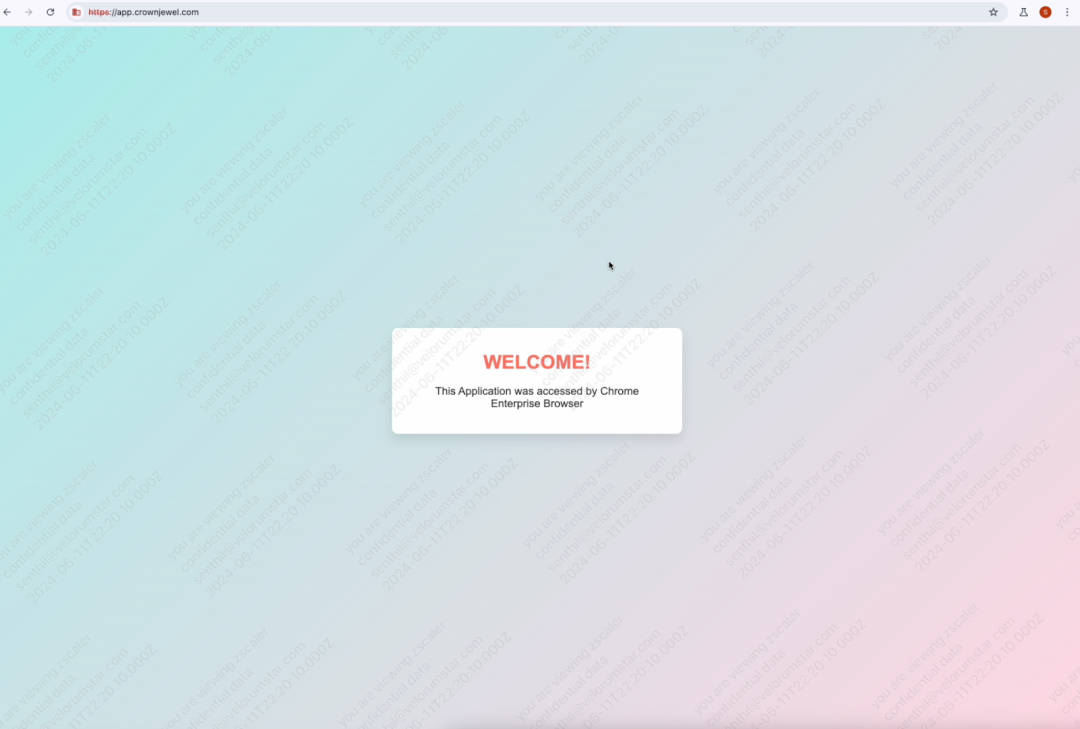
- Watermarking capabilities: Add user information and timestamps to specific applications, helping prevent unauthorized screen captures and tracking any sensitive content that may be shared.
ZPA also enhances security by offering advanced application controls. Through user fingerprinting, ZPA continuously identifies and tracks the user throughout their browsing session. If an anomaly in the fingerprint is detected, it can indicate potential session hijacking, providing an additional layer of protection.
Example: Download controls - PII data download being blocked with custom notification
Example: Watermarking capabilities - added with username and timestamp to discourage screen captures
4. Comprehensive traffic visibility and device context with ZPA and Chrome
ZPA provides administrators with complete visibility into all traffic passing through the system, capturing critical system information from unmanaged devices. This enables security teams to monitor user activity, enforce security policies, and respond to potential threats in real time. By having detailed device posture and traffic data, ZPA ensures robust protection across all user interactions.
In addition, Chrome Enterprise enhances this visibility by sharing additional context about the browsers in your environment. Chrome Browser collects and reports device signals, providing administrators with deeper insights into browser usage and user behavior. This combined visibility helps strengthen the security enforcement.
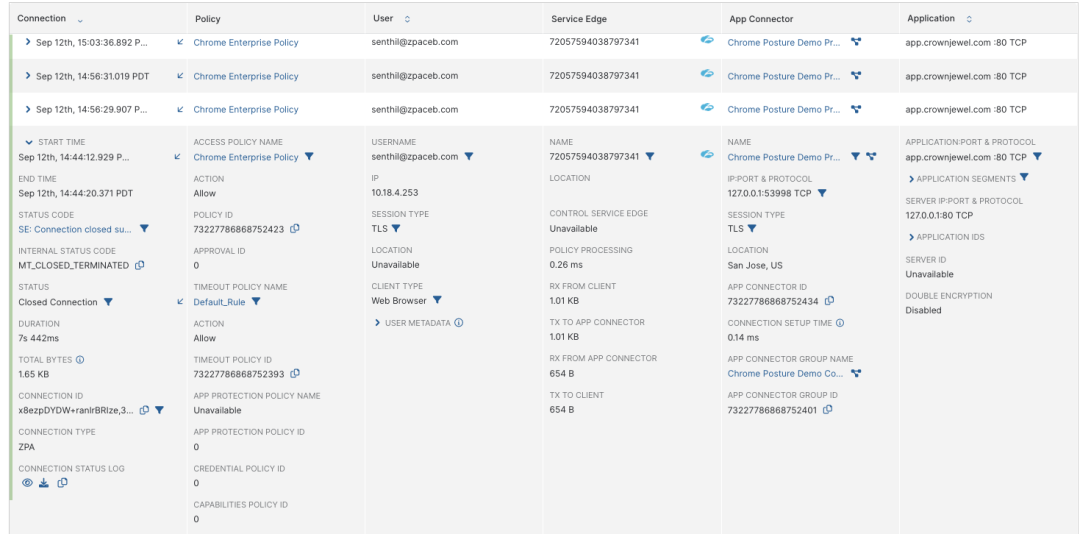
Example: Transaction logs for the traffic flow with Chrome posture signal.
Example: Extensions and applications installed in the Chrome user base. 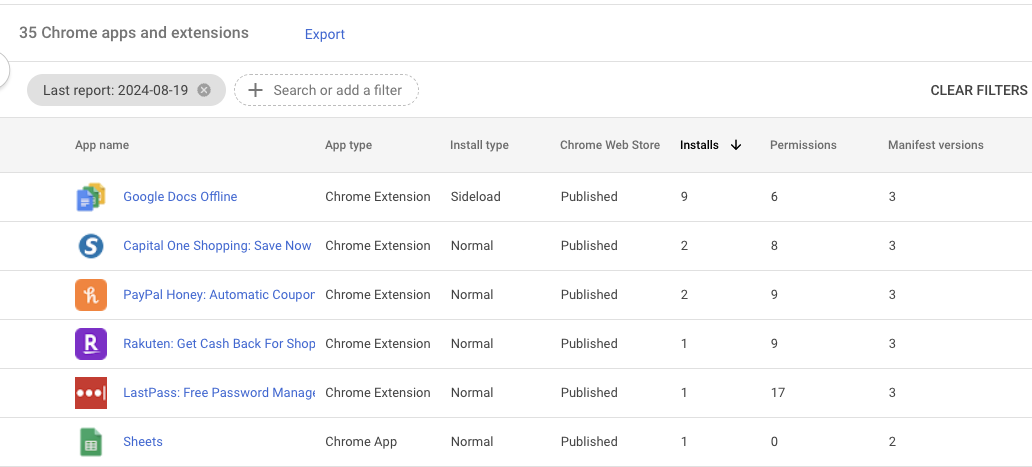
Conclusion
In today’s fast-evolving digital landscape, securing access to critical applications while maintaining a seamless user experience has never been more important. By integrating Chrome Enterprise Browser with Zscaler Private Access, organizations can drastically simplify security, reduce operational costs, and provide users with a familiar and secure platform. Contractors and remote users can be onboarded securely and efficiently in just a few steps, ensuring that your business remains agile and protected.
Ready to see how the Chrome Enterprise Browser and ZPA integration can transform your business’s security and user experience? Register now to explore the full potential of this integrated solution!
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




