Register for our webinar discussion on Thursday, March 3rd to hear directly from customers and product leaders about the Zscaler + SentinelOne integration.
Zscaler’s customers rely on us as the leader in zero trust to limit their security risks as they expand their organization’s digital footprints to new globally distributed devices, application stacks, and infrastructures. Anyone who has undergone any level of zero trust deployment knows that the central credo is ‘assume breach.’ Architect your IT and security systems as though there are already malicious actors in your system, then disrupt their ability to operate.
Security operations teams play a critical role in zero trust. If we’re ‘assuming breach,’ then we’d better be hunting and investigating those threats. Our new integration with SentinelOne allows SecOps teams to do that with even greater confidence and efficiency.

Breaking security silos with XDR
Most enterprise security stacks contain an array of disjointed point products that each have their own security controls, and that offer little or no meaningful correlations between them. When security operations teams see something suspicious in their logs, they have to pivot between various tools and manually piece together information to understand the scope of the threat. Remediation is the same: each security control often must be updated individually.
The net result is far from ideal. It takes 280 days, on average, to mitigate a threat. And this inefficient pivoting is a waste of analysts’ critical time.
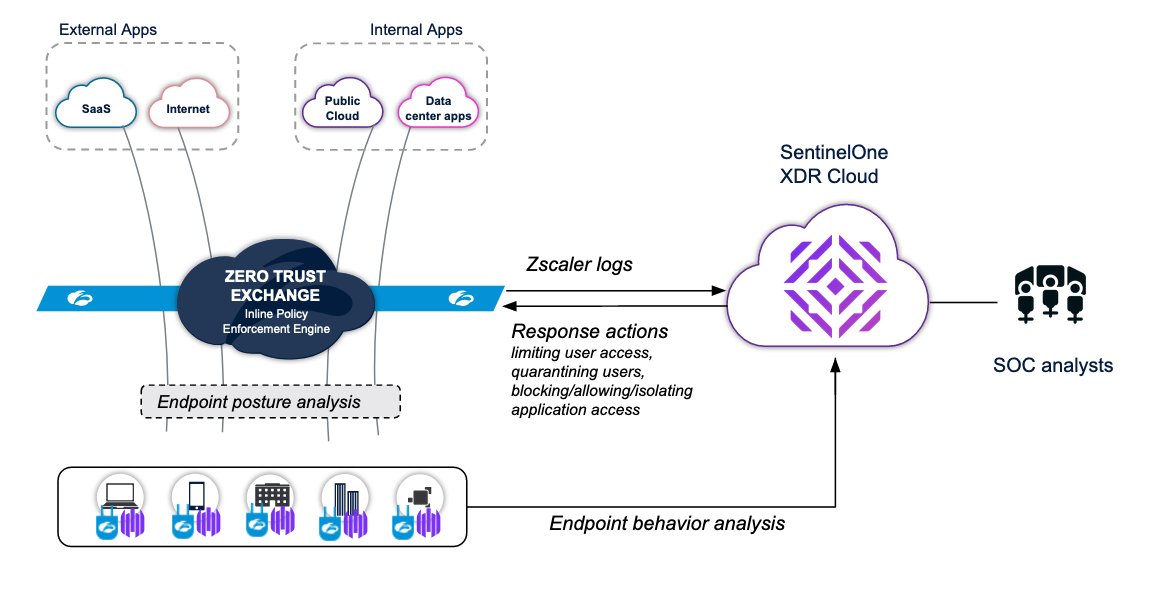
Zscaler and SentinelOne are tackling this challenge head-on. With integration into SentinelOne Singularity XDR, logs from the Zscaler Zero Trust Exchange —the world’s largest security cloud—are ingested into SentinelOne's Scalyr back end where they can then be queried and faceted, allowing security operations teams to quickly triage and respond to attacks.
This joint solution empowers security operations to take policy-driven actions across platforms that remediate threats automatically before an endpoint compromise results in cloud data exfiltration or other damage.
Analysts can trigger automatic and manual response actions from SentinelOne into Zscaler such as revoking access or quarantining users or moving them into a more restrictive group, based on which access policy to selective applications can be applied. This automatically limits an attacker’s ability to infiltrate and launch an attack.
Zscaler + SentinelOne integration
Key use cases
Extended visibility and accelerated remediation
SentinelOne consumes both Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) logs for expanded visibility, and enables security analysts to configure flexible response policies right from the SentinelOne console. These logs add context to help triage and investigate threats without needing to pivot from the SentinelOne console, where analysts can also quickly and automatically mitigate threats by limiting user access, quarantining a user, blocking access to one or a group of critical applications, or restricting access to specific applications with browser isolation.
Zero trust conditional access
SentinelOne continuously checks policy and enforces compliance in accordance with Zscaler policies. When an endpoint attempts to access a corporate application, Zscaler first performs a posture check to ensure that SentinelOne is installed and running before granting access. The SentinelOne and Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) integration enables seamless conditional access, ensuring that the trusted identity on a trusted device can directly access authorized corporate applications without exposing the network.
Extending best-of-breed zero trust for faster investigations and better response
Extended detection and response (XDR) and zero trust are two sides of the same coin, both fundamentally seeking to simplify and reduce the risk of digital transformation by increasing visibility and reducing the attack surface. Zero trust defines the architecture, policy, and strategy; XDR provides the analytics and drives the SecOps workflows.
Zscaler is excited to partner with SentinelOne to take both zero trust and XDR to the next level, extending our platform from the cloud to the endpoint with shared telemetry and coordinated response actions. This powerful integration is only the start of the many benefits we expect to bring to our joint customers.
If you’d like to learn more, download our solution brief – or better yet, join us for our upcoming webinar on March 3rd, where you can hear directly from product leaders and customers about this integration and what it means for you.





