/ What Is Spear Phishing?
What Is Spear Phishing?
How Do Spear Phishing Attacks Work?
A spear phishing attempt starts as an email, social media message, text message, or other communication that seems to be from a trusted source. Cybercriminals use information they know about their target to make the message seem authentic, and then ask the recipient to take some action, such as opening an attached file, following a benign-looking malicious link.
A phishing email might copy visual elements from the target’s bank and ask the target to verify a transaction or check an important notification. A link in the email takes the target to a bogus website that looks and feels like the bank’s real site, where a prompt asks for bank account login credentials, confirmation of a credit card or Social Security number, or similar.
Some threat actors impersonate someone their target knows, such as a friend, family member, or colleague. An email from a “friend” might ask the recipient to look at a funny link or download a useful file. Because the target thinks they know the sender, they let their guard down and are less likely to notice warning signs or suspect a scam.
Advances in generative AI have made sophisticated phishing easier than ever.
With just a few minutes of samples, deepfake voice generators can realistically imitate a speaker for use in phishing phone calls.
Zscaler ThreatLabz created the basic fake Microsoft login page shown here with just three prompts.
Types of Spear Phishing
There’s a litany of different techniques and types of phishing scams out there. Let’s look at a few techniques frequently seen in spear phishing campaigns:
- Angler phishing: Hackers pose as company representatives to address complaints, offer deals, etc. through social media (e.g., Twitter or LinkedIn) or text message (smishing). If a company representative reaches out to you this way, try to confirm their identity before you interact.
- Business email compromise (BEC): Attackers gain access to a business email account, or create a lookalike account, and impersonate its owner to send phishing messages to the owner’s colleagues or partners. These attacks are often paired with wire fraud.
- Whaling attacks: Threat actors target members of an organization likely to have privileged access—generally senior-level executives or equivalents. These types of attacks are often the most sophisticated and well-planned, making them even more dangerous.
- CEO fraud: Closely related to whaling, attackers use this form of BEC attack to impersonate an organization’s CEO or equivalent, creating a sense of urgency in scam messages to employees.
- Clone phishing: Phishers send malicious emails that seem to be from senders the victim trusts, such as financial institutions or business services. This type of attack often also indicates that the spear phishers have some measure of access to the victim’s email account.
To learn about other common phishing techniques, you can read our companion article, What Is Phishing?
Phishing attacks surged by 58.2% in 2023, compared to 2022, reflecting the growing sophistication and persistence of threat actors.
What Are the Targets of Spear Phishing?
Individuals
Spear phishing attacks can target anyone. Phishers can use someone’s personal details, especially confidential information, to make their attack more convincing. People with elevated roles in their organizations are generally at greater risk, as they’re often responsible for more sensitive data.
Finance and Insurance
The finance and insurance sector experienced both the highest number of phishing attempts and the most significant increase in attacks, rising 393% compared to the previous year. This industry is an attractive target for threat actors aiming to engage in identity theft or financial fraud.
Businesses
Infiltrating a company’s system can give cybercriminals access to huge amounts of sensitive information, and data breaches—especially in the financial and technology sectors—can cost companies millions in recovery costs, fines, and loss of customer trust. The shift to the cloud and remote work has made businesses even more vulnerable, as distributed IT environments introduce many more possible vectors of attack.
(Source: 2023 ThreatLabz Phishing Report)

How to Defend Against a Spear Phishing Attack
Preventing successful spear phishing is a matter of taking the right precautions. In terms of what that means at the organizational level, there’s a lot to consider.
Follow Spear Phishing Prevention Best Practices
Reduce your overall risk with key security solutions:
- Email security: Secure the most common phishing vector with a cloud-based service that inspects emails before they reach your perimeter—with real-time protection against malicious attachments and links as well as domain name spoofing.
- Reporting: Enable users to report phishing attempts, ideally with a reporting button built into their email client. Implement a playbook to investigate and respond to phishing incidents.
- Multifactor authentication (MFA): Bolster security with additional authentication. Apps such as Okta Verify or Google Authenticator improve defense against MiTM tactics that may intercept SMS messages.
- Encrypted traffic inspection: More than 95% of attacks use encrypted channels. Inspect all traffic, encrypted or not, to prevent attackers from compromising your systems.
- Antivirus software: Endpoints should be protected with regularly updated antivirus to identify known malicious files and prevent them from being downloaded.
- Advanced threat protection: Stop unknown malware with an inline sandbox that can quarantine and analyze suspicious files, and browser isolation to protect against malicious web content without disrupting your users.
- URL filtering: Limit your phishing risk with URL filtering that uses policy to manage access to the riskiest categories of web content, such as newly registered domains.
- Regular patching: Keep applications, operating systems, and security tools up to date with the latest patches to reduce vulnerabilities and ensure the latest protections.
- Zero trust architecture: Enforce granular segmentation, least-privileged access, and continuous traffic monitoring to find threat actors who may have compromised your infrastructure.
- Threat intel feeds: Gain automated context enrichment—on reported URLs; extracted indicators of compromise (IOCs); and tactics, techniques, and procedures (TTPs)—to speed up detection and remediation.
- Follow tight security protocols. Require strong passwords, define what employees are allowed to share on social networks, and ensure effective countermeasures are in place. Modern security software will block many phishing attempts before they ever reach your users.
Learn How to Identify a Spear Phishing Attack
As part of general security awareness training, your organization’s users should all learn how to spot spear phishing red flags, such as:
- Overlooked details: Cybercriminals can mimic URLs, email addresses, company branding, and so forth, but minor details can give them away. For example, a suspicious email may look like it’s from a trusted organization, but come from an unfamiliar, mismatched, or incorrectly formatted sender address.
- Poor grammar and spelling: Most professional communications—especially business-to-customer messages—are proofread prior to sending, and most email services automatically flag simple errors. Thus, if a message contains many such errors, it can be more likely that it’s from an illegitimate source.
- Unusual language: Sometimes, the language in an email can be suspicious, even without errors. It may seem disjointed or otherwise strange in some way. If a message seems to be from someone you know, but the writing style doesn’t seem like theirs, you may have good reason to suspect phishing.
- Unusual requests: Be wary of odd requests, particularly with little or no explanation. For example, a spoofed email from “your bank” might ask you to confirm your identity by performing a wire transfer to yourself. If a request seems suspect, consider whether a legitimate sender would make such a request. If not, it may be phishing.
- Frequently imitated senders: Phishers continue to impersonate popular brands to deceive consumers. Zscaler ThreatLabz research found that Microsoft remains the most imitated brand, with 43.1% of phishing attempts targeting it. Microsoft’s OneDrive and SharePoint brands were also among the top five targeted, indicating a persistent trend of threat actors seeking user credentials from critical Microsoft applications.
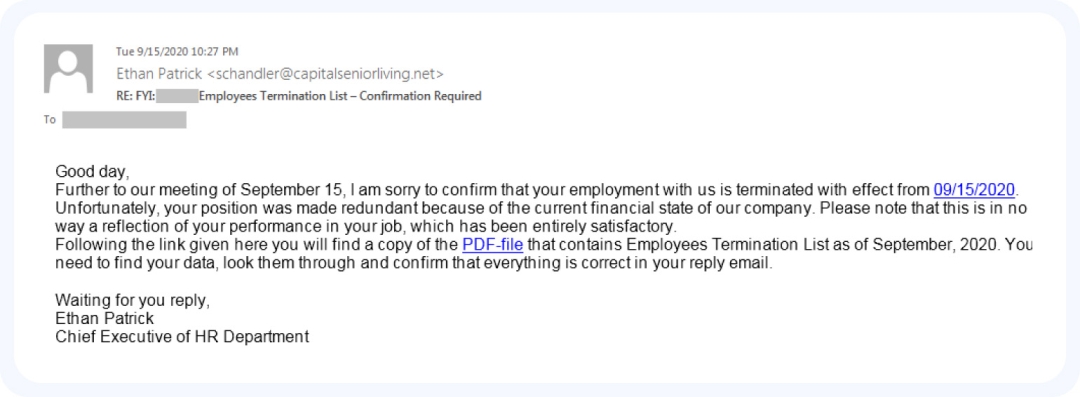
An example of a spear phishing email. Pay attention to the unusual phrasing and the framing of specific details.
How Do Businesses Increase Their Phishing Awareness?
It pays dividends to keep everyone in your organization up to date on current security threats and policies. All phishing relies on hijacking human trust, and it only takes one person following a malicious link for your environment to be compromised.
Your security awareness training program should educate people about cyberthreats they might face in their role, how to identify spear phishing emails and other targeted attacks, how and where to report phishing, and more.
You may also need to engage the services of cybersecurity specialists. Social engineering techniques are always evolving with trends and new technology, and it can be daunting to keep up. Working with experts who know the business inside out, you’ll have all the guidance and support you and your team need.
How Can Zscaler Help?
User compromise is one of the most difficult security challenges to overcome because it relies on exploiting human nature to succeed. By exploiting victims from such close range, spear phishing can be all the more dangerous, quickly leading to breaches. To minimize the damage, you need to implement effective phishing prevention controls as part of a broader zero trust strategy.
The Zscaler Zero Trust Exchange™ platform, built on a holistic zero trust architecture to minimize the attack surface and prevent compromise, helps stop phishing by:
- Preventing attacks: Features like full TLS/SSL inspection, browser isolation, and policy-driven access control prevent access from malicious websites.
- Preventing lateral movement: Once in your system, malware can spread, causing even more damage. With the Zero Trust Exchange, users connect directly to apps, not your network, so malware can’t spread from them.
- Stopping insider threats: Our cloud proxy architecture stops private app exploit attempts and detects even the most sophisticated attack techniques with full inline inspection.
- Stopping data loss: The Zero Trust Exchange inspects data in motion and at rest to prevent potential data theft from an active attacker.
Protect your organization against spear phishing attacks with the power of a complete zero trust architecture.
Suggested Resources
Frequently Asked Questions
While most phishing targets victims at random, spear phishing targets specific individuals. Attackers generally already have some information about their targets before they carry out the attack, which they can use to make their phishing messages much more convincing.
Between 2013 and 2015, an attacker invoiced Facebook and Google for roughly US$100 million while posing as Quanta, a real technology firm that worked with them. The companies only recovered about half after the attacker was charged.
In 2016, a BEC scammer defrauded the Belgium-based Crelan Bank of more than 70 million euros by posing as an executive and requesting transfers of funds.
Cybercriminals generally craft a spear phishing attack after obtaining information about their target, either stolen or from publicly available sources, such as social media.
If you receive a phishing email, report it. Don’t respond to it or otherwise interact with it. Your security team, incident response, or IT personnel will notify relevant parties such as software vendors to reduce the likelihood of a repeat attack.
The most common types of phishing attacks come through email, with messages designed to trick you into giving up your data or downloading malware. Voice phishing attacks (vishing) and SMS message phishing (smishing) are also becoming more common.


