/ Che cosa si intende per accesso a privilegi minimi?
Che cosa si intende per accesso a privilegi minimi?
Perché l'accesso a privilegi minimi è importante?
Con lo spostamento di volumi sempre maggiori di dati verso e attraverso gli ambienti cloud pubblici e multicloud, e con l'aumento della frequenza e della sofisticatezza di attacchi informatici come i ransomware, le organizzazioni sono alla ricerca di modi per proteggere le loro superfici di attacco in espansione e mitigare i rischi. Qui entra in gioco l'accesso a privilegi minimi, detto anche principio del privilegio minimo (Principle of Least Privilege, POLP), che è uno degli elementi fondamentali di un approccio zero trust.
L'accesso a privilegi minimi prevede tre elementi fondamentali: l'autenticazione dell'identità dell'utente, il profilo di sicurezza del dispositivo e la segmentazione da utente ad app. Li approfondiremo nel dettaglio tra poco.
Accesso a privilegi minimi e zero trust
Prima di andare avanti, vediamo come questi due termini si relazionano l'uno con l'altro. L'accesso a privilegi minimi può sembrare molto simile allo zero trust, e in effetti si tratta di concetti strettamente correlati, ma radicalmente diversi.
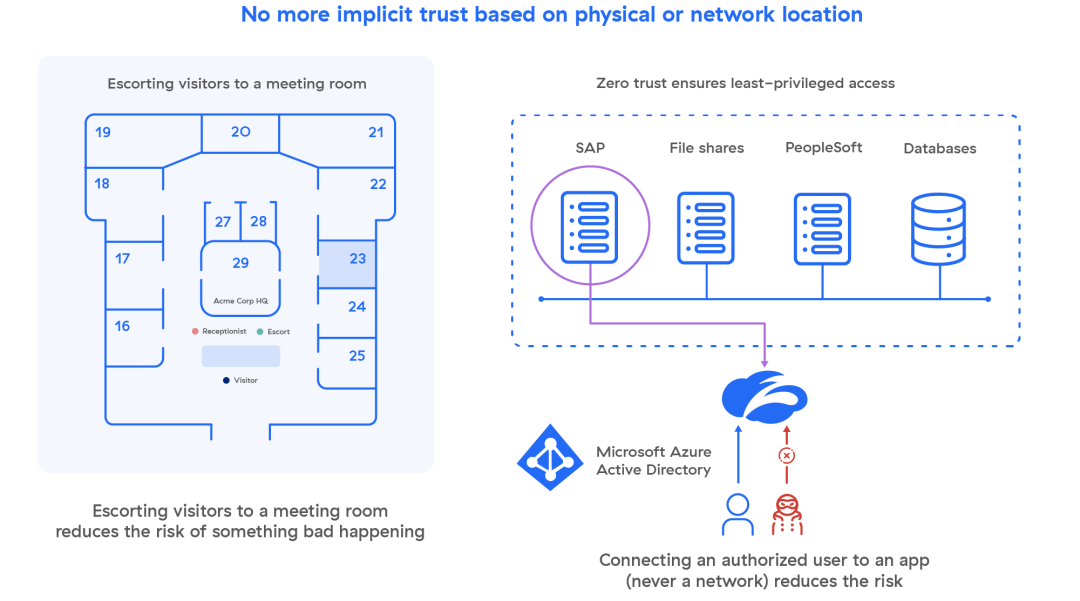
L'accesso a privilegi minimi può essere descritto come un tesserino che viene dato a ogni dipendente e che viene programmato in base alla funzione lavorativa. In questo modo, è possibile personalizzare i controlli di accesso, così la maggior parte degli utenti potrà accedere alle aree comuni, come Microsoft 365, ma solo alcuni di essi avranno le credenziali per accedere a materiale più sensibile, come ad esempio informazioni finanziarie, dati sulle risorse umane e così via, riducendo il rischio che vi siano violazioni dei dati a causa di autorizzazioni troppo permissive.
La sicurezza zero trust si spinge oltre, e non basta che un dipendente abbia un tesserino affinché venga considerato attendibile. Prima di concedere l'accesso, una policy zero trust stabilisce l'identità di un utente e il contesto completo della richiesta di connessione, come il dispositivo dell'utente, la sua posizione, l'applicazione in questione e il relativo contenuto. In questo modo, per estendere la metafora, a un altro utente non basterà semplicemente impossessarsi di un tesserino altrui per sfruttarne i diritti di accesso ed entrare in luoghi che dovrebbero invece risultargli inaccessibili.
Come funziona l'accesso con privilegi minimi moderno
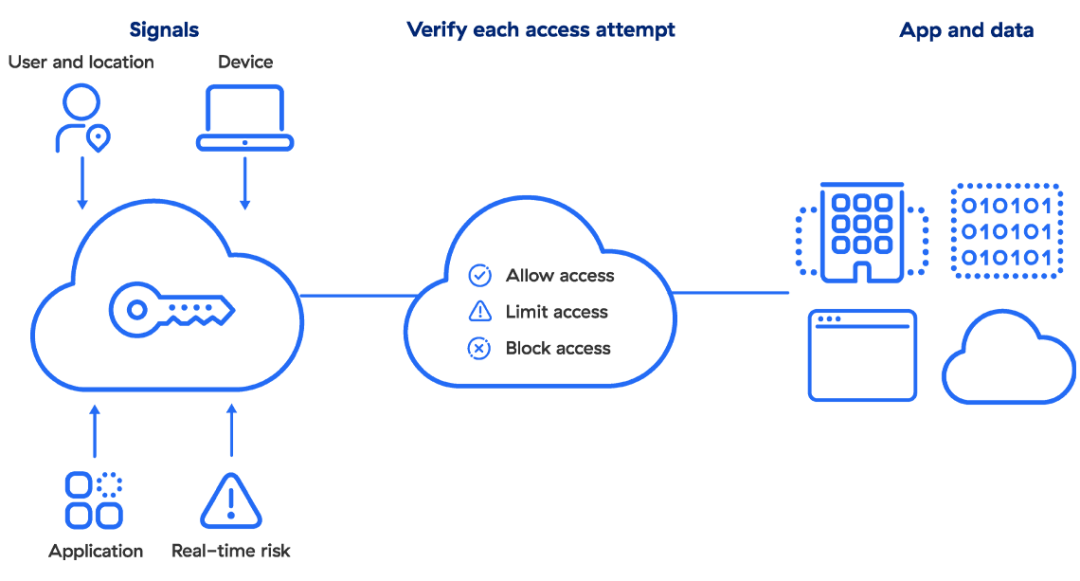
Oggi, l'accesso a privilegi minimi e lo zero trust sono essenzialmente inseparabili, ed è necessario adottare un approccio moderno che incorpori nei controlli l'autenticazione dell'identità dell'utente, il profilo di sicurezza del dispositivo e la segmentazione da utente ad app. Esaminiamo questi tre elementi fondamentali.
Autenticazione dell'identità dell'utente
In questo modo, è possibile stabilire se gli utenti sono chi dichiarano di essere. I provider e i servizi di gestione dell'identità e dell'accesso (IAM) (ad es. Okta, Azure Active Directory, Ping Identity) creano, conservano e gestiscono le informazioni sull'identità, offrendo diversi servizi di provisioning e autenticazione.
Profilo di sicurezza del dispositivo
Un utente in buona fede con privilegi elevati può comunque cadere vittima dei malware. Abbinate a una valutazione continua del profilo di sicurezza degli endpoint (fornita ad esempio da CrowdStrike, VMware Carbon Black, SentinelOne, ecc.), le moderne policy basate sui privilegi minimi consentono di modificare persino le autorizzazioni con privilegi di un utente in base allo stato del suo dispositivo.
Segmentazione da utente ad app
Il metodo tradizionale per limitare l'esposizione della rete e il movimento laterale è quello della segmentazione della rete, che prevede l'impiego di firewall sulla rete aziendale per consentire che a determinati segmenti possano accedere solo gli account con privilegi. Sebbene sia fondamentale limitare il movimento laterale interno, questo approccio è complicato e non fornisce il controllo granulare di cui le organizzazioni moderne hanno bisogno.
La segmentazione da utente ad app è resa possibile da un servizio ZTNA (Zero Trust Network Access), che consente una segmentazione granulare tramite policy aziendali gestite dall'IT, non da una serie di firewall. Lo ZTNA collega gli utenti verificati direttamente alle applicazioni che sono autorizzati a utilizzare, senza mai connetterli alla rete, rendendo quindi impossibile il movimento laterale. Questa policy di accesso viene estesa sia agli utenti in remoto che a quelli on-premise, indipendentemente dalla loro posizione, con i medesimi controlli di sicurezza.
I vantaggi dell'accesso con privilegi minimi
La convergenza dei tre elementi fondamentali, con un servizio ZTNA efficace, costituisce la base di un profilo di sicurezza forte e resiliente per l'organizzazione, in cui:
- Gli account utente vengono sempre autenticati prima che venga concesso l'accesso
- I dispositivi vengono monitorati e i livelli di accesso degli utenti si adattano in base al profilo di sicurezza
- La segmentazione delle app riduce al minimo il movimento laterale, eliminando la necessità di una configurazione complessa dei firewall
Considerazioni sul privilegio amministrativo
Ovviamente, ci sono altre considerazioni da fare per gli account amministratore. Ai superutenti viene assegnata moltissima attendibilità e, per loro natura, questi utenti non possono lavorare con un accesso limitato. La soluzione tradizionale consiste nella gestione degli accessi privilegiati (PAM), che gestisce i diritti, gli account e i sistemi operativi a livello di data center. Tuttavia, il passaggio al cloud sta rendendo la PAM meno efficace e mettendo in evidenza la necessità di un metodo diverso per distribuire l'accesso amministrativo.
Oggi, la diffusione dell'approccio DevOps ha portato a una crescita esponenziale delle modifiche ai permessi sul cloud, con migliaia di potenziali variazioni ogni giorno. La gestione delle autorizzazioni nell'infrastruttura cloud (Cloud Infrastructure Entitlement Management, CIEM) ha successo dove la PAM inizia a fallire, in quanto una soluzione CIEM efficace è in grado di gestire e inventariare i diritti cloud, eseguire audit dei privilegi, rilevare e correggere il cosiddetto "privilege creep", ossia l'accumulo di diritti eccessivi, conferire diritti amministrativi ai servizi e svolgere varie altre funzioni a una scala e un livello di complessità che la PAM non può raggiungere.
Per gli ambienti cloud di oggi, è importante considerare soluzioni CIEM, se si sta pianificando o perfezionando il proprio approccio all'accesso a privilegi minimi.
Come implementare l'accesso a privilegi minimi all'interno dell'organizzazione
Ottenere una modalità di accesso moderna zero trust a privilegi minimi è più facile di quanto sembri, e bisogna seguire solo tre passaggi fondamentali:
- Adotta il servizio di un provider di identità (IdP). Data la popolarità dei servizi Single Sign-On, molte organizzazioni utilizzano già un IdP.
- Utilizza anche un servizio per il profilo di sicurezza del dispositivo. L'abbinamento del monitoraggio dello stato dei dispositivi con delle policy flessibili riduce il rischio generato dagli endpoint compromessi, a cui sono sottoposti i sistemi e i dati critici.
- Abilita un servizio ZTNA. In questo modo potrai eliminare con un'unica tecnologia sia l'accesso laterale che i firewall interni. Alcuni servizi ZTNA possono essere completamente distribuiti in poche ore.
L'accesso a privilegi minimi secondo Zscaler
I firewall tradizionali, le VPN e le app private generano una superficie di attacco molto estesa. Gli hacker e gli altri utenti malintenzionati possono vedere e sfruttare le vulnerabilità, le risorse esposte all'esterno e le soluzioni obsolete per la sicurezza della rete, come le VPN, che collocano gli utenti sulla rete e consentono agli aggressori di accedere facilmente ai dati sensibili. Queste soluzioni non sono in grado di adattare le proprie prestazioni o di offrire un'esperienza utente rapida e fluida; infatti, richiedono il backhauling del traffico, introducono costi e complessità aggiuntivi e sono troppo lente per supportare la forza lavoro distribuita di oggi.
Zscaler Private Access™ è la piattaforma ZTNA più distribuita al mondo, che applica il principio dei privilegi minimi per offrire agli utenti una connettività diretta e sicura alle app private, eliminando così gli accessi non autorizzati e il movimento laterale. Questa soluzione può essere distribuita in poche ore per sostituire le VPN e gli strumenti di accesso remoto legacy con una piattaforma olistica zero trust nativa del cloud. Zscaler Private Access è l'evoluzione dello ZTNA.


