Blog Zscaler
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
What Did Plato Have to Say About Zero Trust Security?
Plato was a philosopher from the fifth century B.C. whose work guided human thought for centuries. Nearly 2,500 years later, his influence still echoes everywhere. This is true even in cybersecurity when it comes to zero trust. How so? To answer that question, let’s take a look at one of Plato’s famous teachings.
Plato’s allegory of the cave
This allegory might sound somewhat strange to our modern ears, but let’s dive in. Imagine a deep, dark cave. Within the cave, several individuals have been chained up for the entirety of their lives, and the only thing they have ever been able to see is the cave wall in front of them. Behind them is another group of people. This latter group is using the light from a fire, along with shapes and replicas of things that exist outside the cave, to cast shadows onto the aforementioned cave wall (take a look at the image below if you’d like some help visualizing things).

When the prisoners see these shadows, they are left to believe that the shadows themselves are the “real things,” and that the shadows do not correspond to anything else. For example, if they see shadows of bird shapes, they assume that the shadows are what birds truly are; they do not know that what they see are just shadows cast by replicas that are designed to look like real things (real birds) that exist outside the cave. To see the true forms behind the shadows and the imitations casting them, one would need to leave the cave and behold reality in the light of the sun—where things are quite different. (If you would like to read more about this allegory, you can find a highly scholarly source here).
What does this have to do with cybersecurity?
Now, we can’t be sure that Plato was thinking about cybersecurity when he came up with the above allegory (although he almost certainly was). Either way, the allegory of the cave has clear applicability when it comes to our present topic.
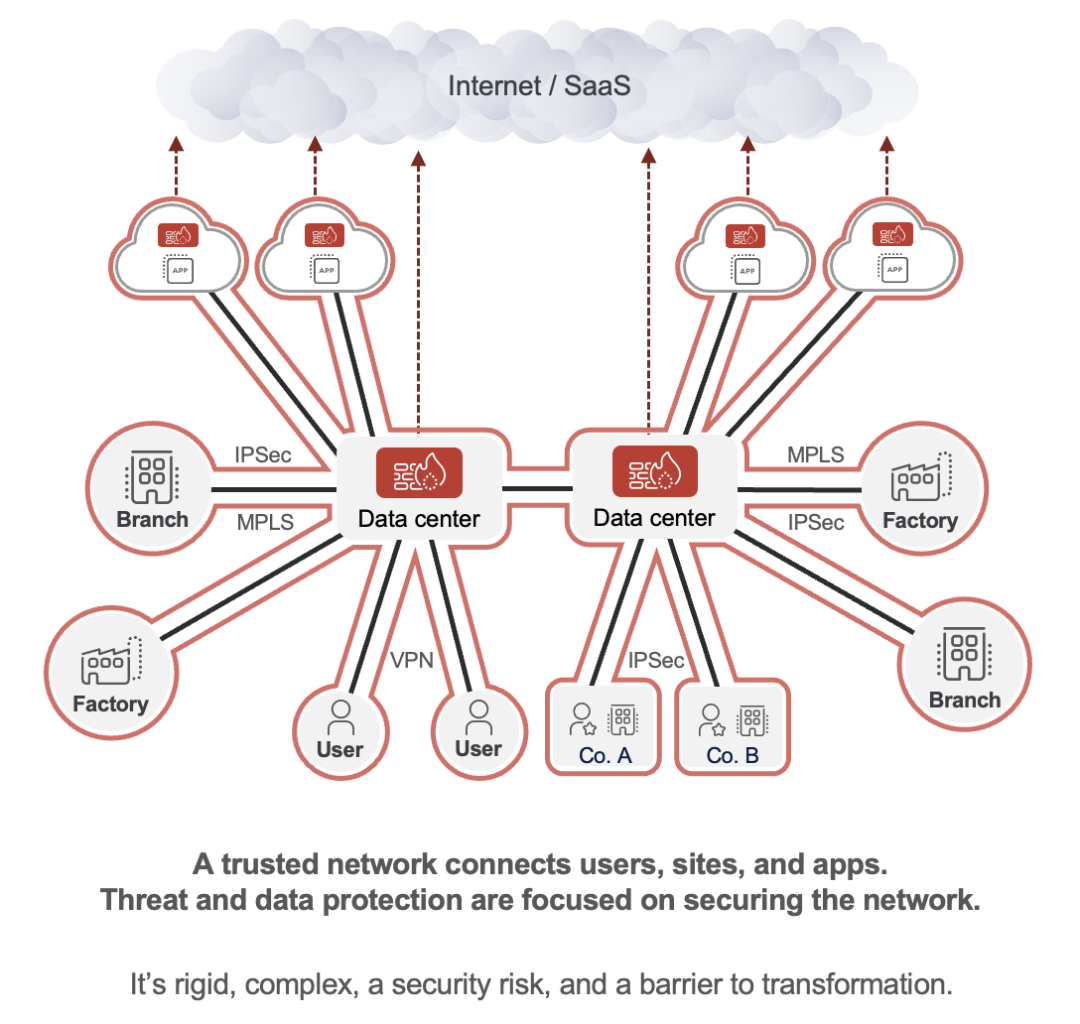
For decades, organizations have been shown the shadows of faulty replicas of what cybersecurity actually is. They have been led to believe that what they are seeing is the “true form” of how security is supposed to look. Specifically, they have been presented continually with hub-and-spoke networks guarded by castle-and-moat security models. But this kind of architecture is a poor fit in the modern world with its remote workers, cloud applications, and increasingly sophisticated cyberthreats that know how to take advantage of the security status quo.
Today, these perimeter-based architectures have multiple, crucially important challenges:
- They endlessly extend the network to more and more users, locations, devices, and clouds, meaning that the attack surface is expanded for cybercriminals
- They enable cyberthreat infections and data loss because the appliances on which they are built lack the scalability necessary to inspect traffic (particularly encrypted traffic at scale) and enforce real-time security policies
- They permit lateral threat movement by placing users and entities onto the network, where they can move from resource to resource and cause extensive damage
- They also suffer from a variety of other challenges related to cost, complexity, operational inefficiency, poor user experiences, organizational rigidity, and more
Zero trust for true security
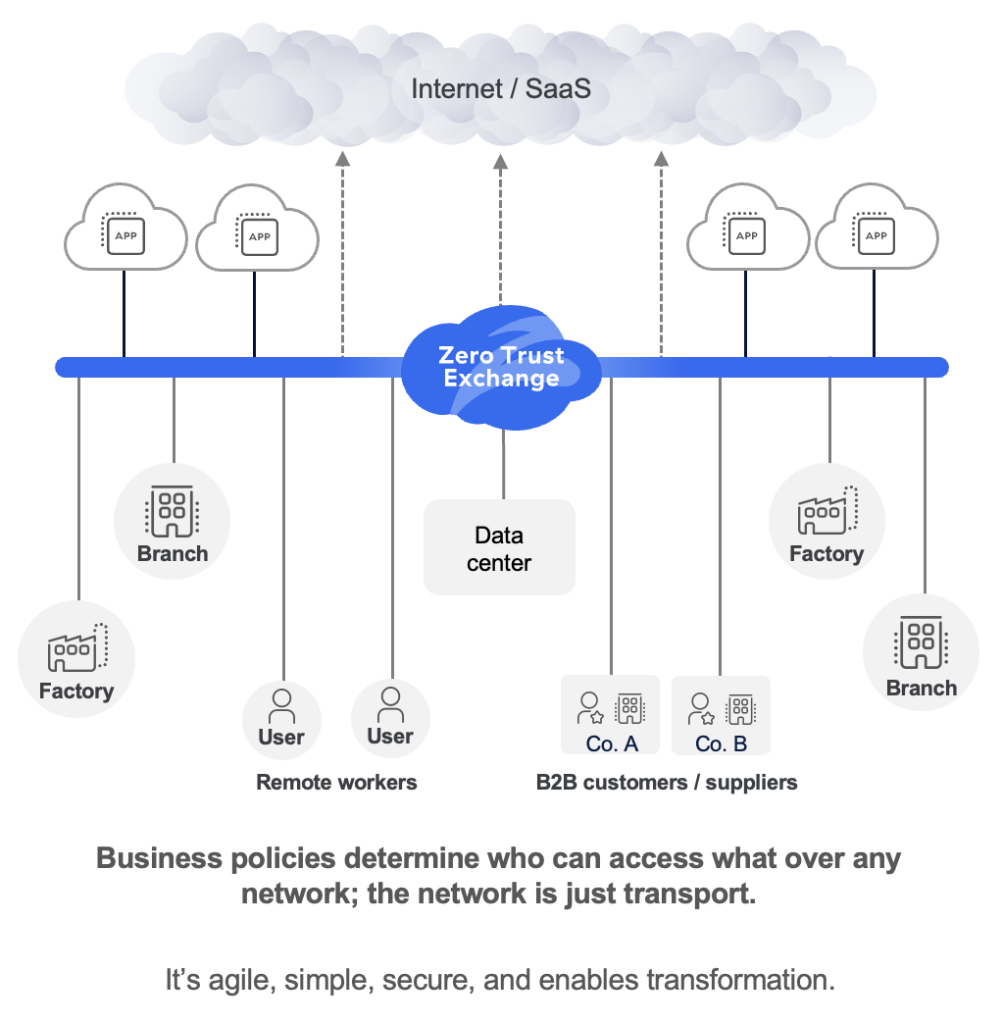
Zero trust is the security reality that makes the perimeter-based shadows and shapes pale in comparison. In fact, the truth is even harsher: perimeter-based architectures are not even shadows or shapes of zero trust, the true form of security. That’s because zero trust is a fundamentally different architecture that separates security and connectivity from network access, and delivers comprehensive security as a service from the cloud. As a result, it does not suffer from the aforementioned challenges of perimeter-based architectures. With a zero trust architecture powered by the Zscaler Zero Trust Exchange, organizations can:
- Minimize the attack surface by hiding devices and apps behind the Zero Trust Exchange, eliminating exploitable tools (e.g., firewalls and VPNs), and stopping endless network expansion
- Stop compromise and data loss through high-performance, cloud-powered inspection of all traffic, including encrypted traffic at scale, to block threats and data loss in real time
- Prevent lateral threat movement by connecting users, devices, and workloads directly, one to one, instead of connecting them to the network as a whole
- Solve other critical challenges by decreasing complexity, increasing operational efficiency, enhancing user experiences, and improving organizational agility, all contributing to greater economic value
It’s time to cast the shackles aside, depart from Plato’s cave, and behold the true form of security in the light of day. It’s time to embrace zero trust and never look back.
Register for our upcoming webinar, “How to Reduce Cyber Risk While Embracing Digital Transformation,” to learn more about zero trust architecture and how it is helping modern organizations solve their networking and security problems. You will also hear firsthand from a Zscaler customer as they discuss their benefits and learnings from embracing the Zero Trust Exchange.
Questo post è stato utile?
Esclusione di responsabilità: questo articolo del blog è stato creato da Zscaler esclusivamente a scopo informativo ed è fornito "così com'è", senza alcuna garanzia circa l'accuratezza, la completezza o l'affidabilità dei contenuti. Zscaler declina ogni responsabilità per eventuali errori o omissioni, così come per le eventuali azioni intraprese sulla base delle informazioni fornite. Eventuali link a siti web o risorse di terze parti sono offerti unicamente per praticità, e Zscaler non è responsabile del relativo contenuto, né delle pratiche adottate. Tutti i contenuti sono soggetti a modifiche senza preavviso. Accedendo a questo blog, l'utente accetta le presenti condizioni e riconosce di essere l'unico responsabile della verifica e dell'uso delle informazioni secondo quanto appropriato per rispondere alle proprie esigenze.
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Inviando il modulo, si accetta la nostra Informativa sulla privacy.




