Blog Zscaler
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Iscriviti
SASE o SSE: i nuovi (di)lemmi nel dizionario della sicurezza informatica
Cybersecurity has no shortage of acronyms. With DLP, SSL, IPS ATP, DSPM, DNS, ML, and many others, “alphabet soup” comes to mind. Most of these correspond to technologies or frameworks that address unique challenges organizations must solve to maintain a robust security posture. When a new term is coined, IT teams need to understand what it means, why (or perhaps if) it matters, and whether they need to change the way they go about security as a result.
One such term, SASE, took the world by storm in 2019 and called existing IT paradigms into question. But shortly thereafter in 2021, SASE’s creator Gartner coined another, similar term: SSE. Naturally, this has led to some confusion. Why did we need this new addition to the cybersecurity dictionary, and how is SSE different from SASE?
The short answer
SASE is an overarching paradigm envisioned by Gartner, while SSE is a subset of SASE. The creation of SSE was effectively an admission that SASE represented too big of a change for organizations to implement all at once, and that they needed to start with a “smaller bite” in the form of SSE. Let’s explore each of the two in more detail.
SSE: Unified, edge-delivered security
SSE, which stands for security service edge, is one part of a complete SASE implementation. Specifically, it is the portion of SASE focused on the consolidation and delivery of security services from the edge meaning from as close to the end user as possible. As a first step into the overarching SASE philosophy, SSE equips organizations with a single, cloud-delivered security platform that provides various integrated technologies locally, for any user, anywhere.
It represents a significant departure from legacy security architectures. Traditional methodologies require backhauling traffic to a central location and through a number of disjointed security appliances that can’t scale to inspect encrypted traffic, and are costly to purchase and maintain. Security, user experience, productivity, and the corporate coffers all suffer under that status quo.
Additionally, even modern cloud security solutions, when deployed as point products, can lead to added burdens for IT teams. The lack of integration between solutions and the need to manually duplicate (disparate) policies across them will—all too often—create inconsistent security.
SSE has emerged as a critical solution to these challenges. With the power of a high-performance cloud (like Zscaler’s, in particular), an SSE offering can scale as needed to inspect encrypted traffic, which is critical for security now that more than 95% of web traffic is encrypted. On the back of this capability, SSE platforms provide comprehensive security by integrating three primary solution sets:
- Cloud access security brokers (CASBs) secure the use of SaaS applications. Originally focused on shadow IT discovery, CASBs now do far more. For example, they integrate with SaaS apps via API to scan for misconfigurations (known as SSPM), identify sensitive data and malware-infected files at rest, and revoke risky or external file shares.
- Secure web gateways (SWGs) secure the use of the web. Some may assume this just means URL filtering, but SWGs have evolved to provide a variety of protections on the web. Intrusion prevention system (IPS) functionality defends against advanced threats and botnets, while cloud sandboxing identifies and stops zero-day threats in real time—not after it is already too late.
- Zero trust network access (ZTNA), despite its unfortunate naming convention, is not supposed to extend access to the corporate network. Rather, it is meant to provide secure access directly to private applications hosted in the data center or a cloud like AWS. ZTNA is not just a different type of VPN; it’s more like an upgrade and replacement for the entire inbound stack.
Beyond these three tips of the trident, SSE platforms bring together a variety of other complementary functionality:
- Data loss prevention (DLP) identifies sensitive data and enforces policies that are designed to protect it.
- Browser isolation stops threats and data loss by spinning up virtual sessions in the cloud that connect to apps and stream only pixels or images of sessions to end users.
- FWaaS (a.k.a. firewall as a service or cloud firewall) offers firewall protections across all ports and protocols without the need for hardware or virtual appliances.
- User behavior analytics (UBA) uses AI/ML to baseline user behavior and detect suspicious or unusual departures from the norm, preventing risky user actions.
- And, of course, a lot more.
This unified approach enhances security across the IT ecosystem while reducing complexity and saving time for administrators. Additionally, as mentioned above, SSE offerings deliver their comprehensive security functionality through the cloud and as close to the end user as possible, reducing latency and enhancing productivity.
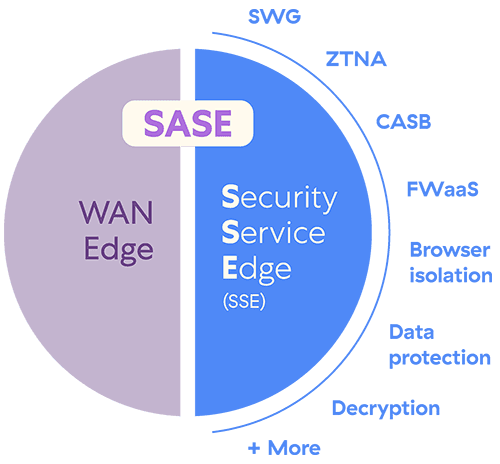
SASE: The core framework
Secure access service edge (SASE), pronounced “sassy,” is a framework, not one specific technology. While security capabilities and network services are disjointed in legacy data center architectures, SASE envisions a cloud-based ecosystem that unifies the two. With users, services, applications, and devices existing everywhere, organizations need a means of connecting them effectively and securely, ensuring a productive user experience while keeping data safe and threats like ransomware at bay.
In other words, SASE combines SSE and WAN edge solutions—namely SD-WAN (software-defined wide area network), which is a faster, cheaper, more secure alternative to traditional WAN networks with MPLS links.
Interestingly, Gartner developed SASE before SSE. The creation of SSE acknowledged that many organizations were not ready to revolutionize their security and connectivity, and needed to start smaller. Even today, many organizations begin with SSE instead of embracing complete SASE. Perhaps partly because of this, many organizations have a so-called multi-vendor SASE, where one vendor provides SSE while another provides WAN edge functionality.
Gartner’s ultimate vision is for organizations to use a single vendor for all aspects of SASE. Increasingly, organizations are turning to comprehensive platforms like Zscaler to fulfill this vision and obtain its simplification, savings, and performance benefits.
What about zero trust?
At this point in the discussion about SSE and SASE, many will want to ask, “How does zero trust fit into this picture?” Indeed, in conversations about one of the three, the other two are typically not far behind. So, first things first: What even is zero trust?
Zero trust is an architecture built on the principle of least-privileged access, which states that entities should only be given access to an individual resource they are authorized to access, at the moment they need it, and nothing more. In other words, zero trust means secure connectivity for any entity accessing any IT resource, in a one-to-one fashion that eliminates excessive permissions. This direct-to-app access is delivered as a service at the edge through a global security cloud, meaning no traffic backhauling is required.
There are overlaps here, between zero trust and the edge-delivered security of SSE, as well as between zero trust and the edge-delivered security and connectivity of SASE. However, there are key differences. For example, SSE and SASE are focused specifically on providing services to users, while zero trust is broader in scope and provides security and connectivity for any entity, going beyond the workforce alone to include workloads, IoT/OT devices, and B2B partners.
Additionally, SSE and SASE are not inherently zero trust solutions. They are edge-delivered, but they still normally focus on establishing a defensive perimeter around the network. In other words, they try to secure network access instead of providing secure, direct-to-app access. Sadly, many purported solutions for ZTNA (a core pillar of SSE that one would expect to provide least-privileged access to private apps) do not provide true zero trust, and still involve routable IPs and network connectivity. You can read more about the weakness of perimeter-based architectures and routable networks in this blog.
To summarize, zero trust is the more foundational paradigm, with SSE and SASE being narrower in scope (both in terms of entities securely connected and zero trust principles applied).
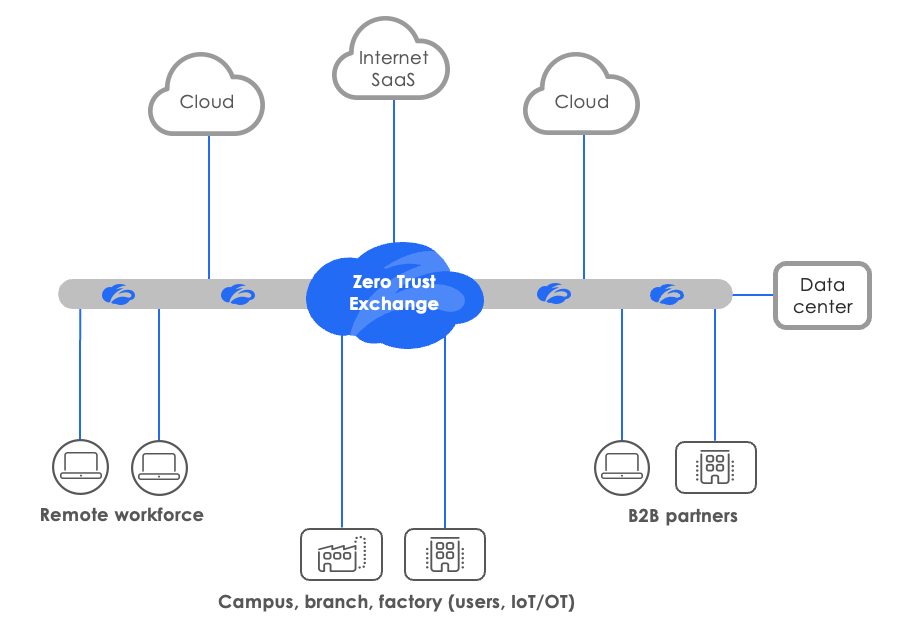
The Zscaler Zero Trust Exchange, the world’s largest inline security cloud, serves as an intelligent switchboard that provides any-to-any connectivity, delivering comprehensive zero trust architecture as a service and at the edge. So, while other SSE and SASE offerings cannot check all the boxes of zero trust, zero trust with Zscaler can check all the boxes of SSE and SASE, all while providing least-privileged access. That’s what makes it the world’s first zero trust, single-vendor SASE offering.
Where do we go from here?
With so many acronyms in cybersecurity, IT must work to separate the wheat from the chaff. In the case of SSE and SASE, Gartner has its finger on the pulse of what IT teams need in order to evolve—as long as they are deployed as a part of a broader, more secure, zero trust implementation. In other words, when combined with a heavy serving of zero trust, SSE and SASE make an alphabet soup that is sure to be both delicious and nutritious.
If you’d like to learn more about SSE and SASE, as well as why you need to marry them with zero trust, download this ESG white paper.
If you’d like to learn more about zero trust from an entry-level perspective, sign up for the webinar, “Zero Trust 101: Start Your Journey Here."
Questo post è stato utile?
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Inviando il modulo, si accetta la nostra Informativa sulla privacy.





