App : SMS touch
Price : $1.99
Category : Utility
Platform : iOS
Updated : Jul 06, 2015
Version : 4.5
Size : 16 MB
Languages: English, Dutch, French, German, Italian, Spanish
Seller: Alco Blom
Rated 4+
Background:
![]() Fig 1: iTunes page
Fig 1: iTunes page
SMS touch is a text messaging app that allows you to send an international SMS message over 3G, 4G, or Wi-Fi. It's available across 820 mobile networks in 220+ countries for a price far lower than the cost of a regular mobile plan. While most plans would charge upwards of 60 cents for an international SMS message, SMS touch charges a flat rate of 9 cents, without any roaming or international charges, allowing the user to recover the purchase price of the app in fewer than 5 texts.
Cost isn't the only reason why users choose the app. SMS touch is also popular among people, especially kids, that don't have cellular plans, as the app allows them to use their iPod touch or other such devices to send text messages in any Wi-Fi zone. However, while SMS touch presents an economical choice for consumers, it still may come at too high a cost.
Recently our ThreatLabZ team discovered that the app sends customer information and SMS messages over a cleartext network, presenting malicious actors the perfect opportunity to intercept login credentials as well as gain access to messages that may contain private information.
Vulnerability:
When users begin to create an account, they are presented with the following screen.

Once the user selects "Create account," the app asks for a username and email address.

After the user has entered all the registration information, the app creates a request to the server and sends the user’s details. In response to this request, the server sends a PIN to be used for login.
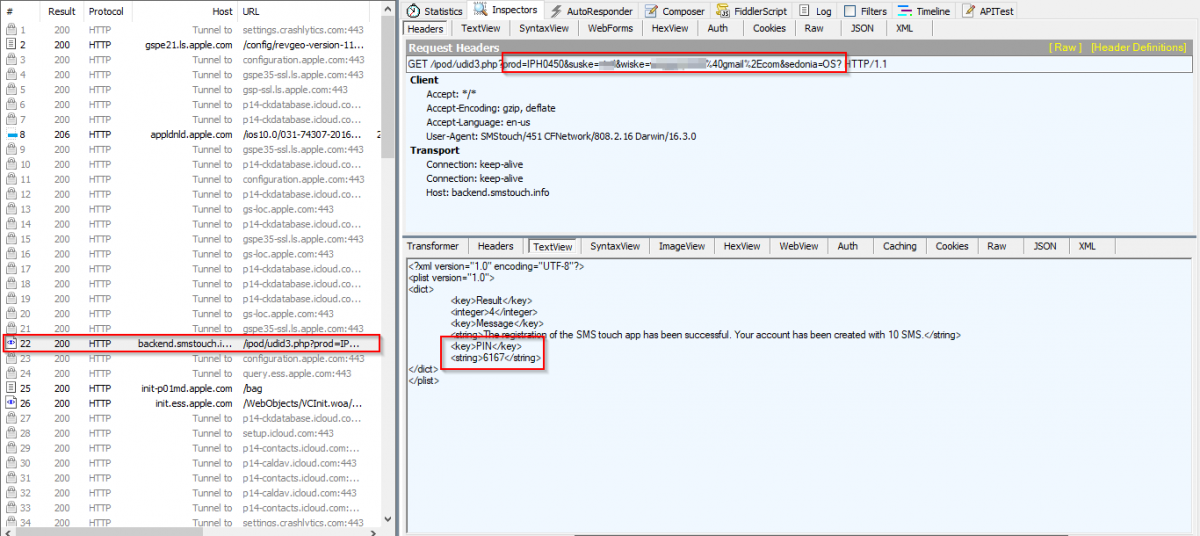
Fig 4: Request to server and response with login PIN.
During login, the app automatically supplies the PIN and email to the server as shown below.
Fig 5: Login screen
Upon clicking “Login,” the user's ID and PIN are sent to the app’s server in plain text. Observe below.
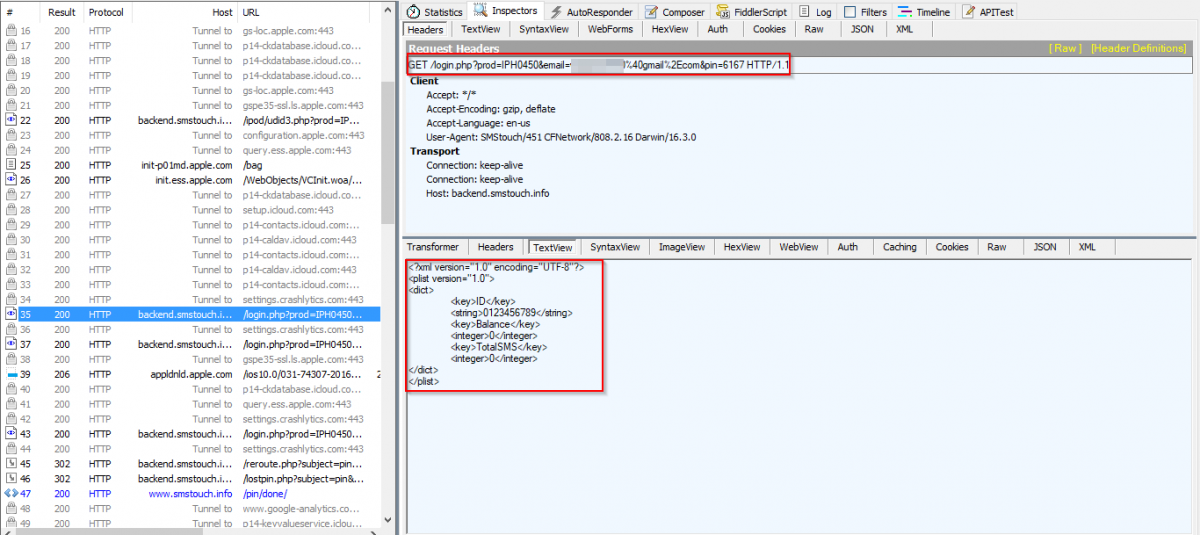 Fig 6: During login, user's ID and PIN are sent to the app’s server in plain text
Fig 6: During login, user's ID and PIN are sent to the app’s server in plain text
The username and password can be easily spoofed by an attacker, given that the information is sent to the server in cleartext.
The following image displays the SMS texting screen.
Fig 7: Send SMS with text in the app's message screen
Once the user clicks "Send," the app also sends the SMS content to the server over a cleartext network channel, as shown below.
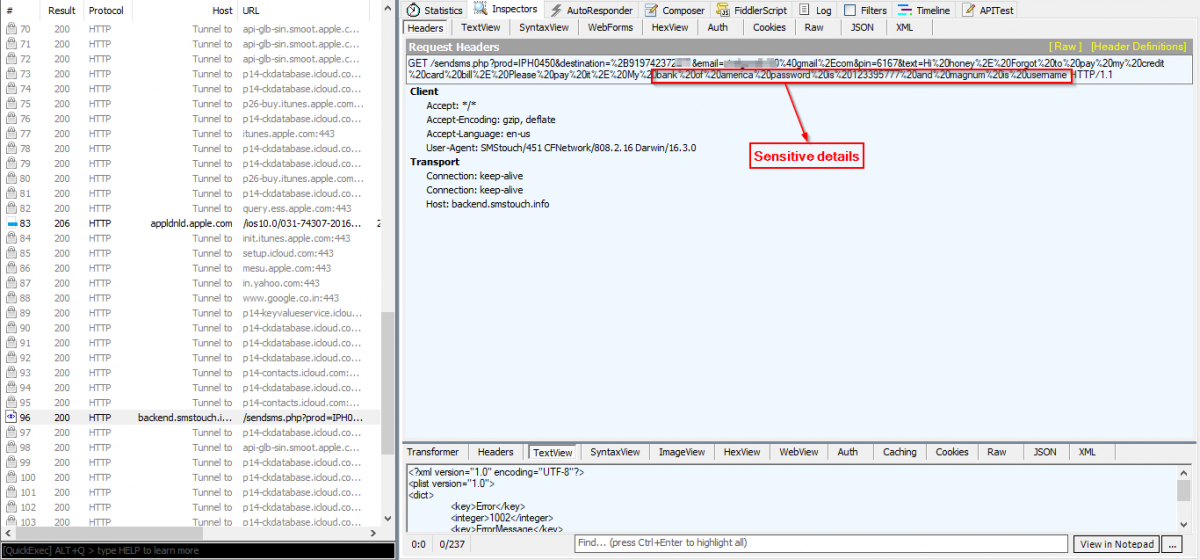
Fig 8: SMS content is sent to the server over a cleartext network channel
Many users send sensitive information over SMS, similar to the example shown above. This data can easily be accessed by an outsider simply tapping in to the application’s network. We witnessed such a transaction in the Zscaler cloud with a user of this app. See below.
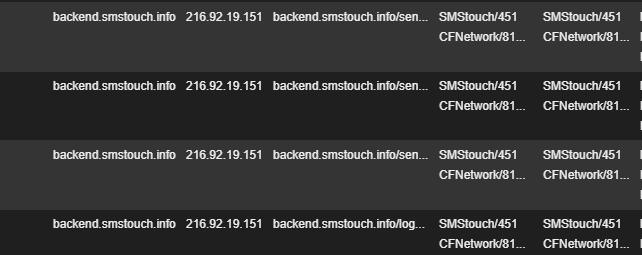


Fig 9: SMS information sent in cleartext, observable in the Zscaler cloud
Conclusion:
The list of mobile applications in Google Play and the iTunes App Store that transmit sensitive information in cleartext continues to grow. In our research report entitled “Are mobile apps a leaky tap in Enterprise?,” we found that 0.5% of transactions from iOS and 0.3% of transactions from Android platforms have some level of privacy leakage.
A study by IBM & The Ponemon Institute shows that of 400 companies studied, almost 40 percent do not scan the apps they develop for security vulnerabilities. Of those that do scan their apps before releasing them to market, only 15 percent test them as frequently as they should. And, even more worrisome, 50 percent of those that develop mobile apps do not allocate any budget at all to testing for security vulnerabilities. Thus, leaky apps are created and users of such apps are unaware that their private data is at risk of exposure.
Even though SMS touch is a paid app, it fails to accommodate standard code security practices. Encryption is absolutely necessary to protect user information and to prevent privacy leakage.
Note: We reached out to the developer of the SMS touch app about this issue. They were prompt to acknowledge the issue and committed to releasing a patch by the end of this year.






