Over the last two years, organizations have significantly accelerated their shift to the cloud. IT teams who hadn’t already started this process by 2020 were kickstarted by the global pandemic, when they suddenly found themselves needing to support a remote workforce. This trend only increased in 2021 as more and more companies and employees realized the scale, performance, and flexibility of cloud computing.
This transformation has come with its own set of challenges, specifically security. Cloud security is its own beast: you can’t just lift and shift on-premises technologies and policies and expect that they will work, at least not well. There’s a new set of best practices that must be followed around access control, monitoring, attack surface management, encryption, and more. Unfortunately, many organizations are immature in this area, leaving them vulnerable.
The Zscaler Threatlabz team analyzes the world’s largest security data set, which is built off of over 200 billion daily transactions across the Zscaler platform. Each year, ThreatLabz compiles anonymous cloud workload statistics from this data to get an understanding of the current state of cloud security and its various challenges. This year’s study of several thousand cloud workloads shows that compared to 2020, the range and prevalence of cloud security issues have only increased.
Key findings
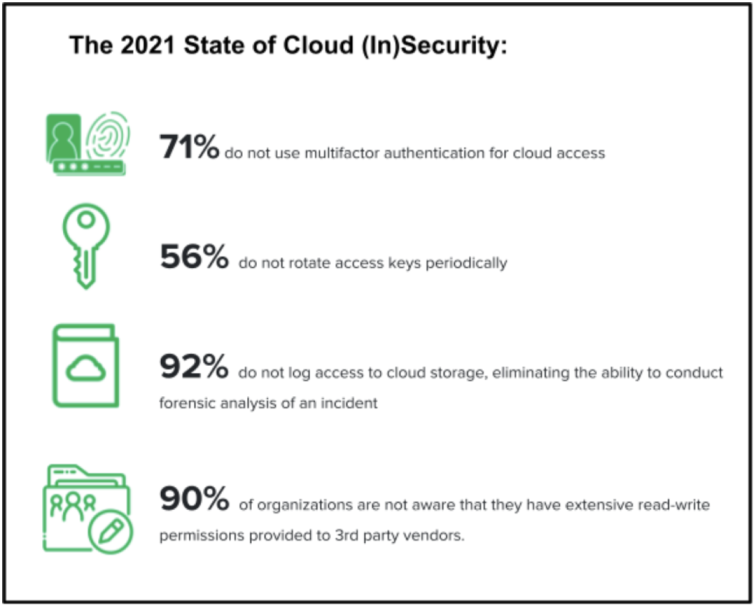
- 71% do not use multifactor authentication for cloud access
- 56% do not rotate access keys periodically
- 92% do not log access to cloud storage, eliminating the ability to conduct forensic analysis of an incident
- 90% of organizations are not aware that they have extensive read-write permissions provided to 3rd party vendors.
Identity and Access Control
Cloud providers continue to add more services, and the average number of distinct entitlements for these services now exceeds 5,000. This volume of entitlements has become exceedingly challenging to manage using traditional identity and access management (IAM) approaches like static policy and role-based access control (RBAC), and are much better managed by a Cloud Infrastructure Entitlements Management (CIEM) solution. Access control and password management have long been weak points for organizational security generally, and this remains true in cloud environments as well.
- 71% of cloud accounts did not make use of software or hardware based multi-factor authentication, up from 63% last year
- Over 25% of the user accounts had not been logged into for more than 45 days. Old and unused accounts are potential entry points into cloud accounts.
- Access keys pose a much bigger risk compared to passwords as they are routinely at risk of being exposed by either hard coding into the source or being leaked through config files.
- 56% of access keys had not been rotated in the previous 90 days, which is an increase of 6% over last year.
- 22% of accounts were found to have access to instances and data which have not been accessed in over 180 days. This indicates that they might have been provided excessive privileges or the data may no longer be required.
- 91% of accounts had been provided permissions which had never been used at all. The use of AWS IAM Access Analyzer would have helped identify these issues.
- A majority of granted entitlements are unnecessary or incorrectly configured. More than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted, which greatly increases the attack surface for account compromises.
The move to the cloud also enables interesting paradigms in centralizing access control specifically to databases. 96% of the databases on AWS did not use IAM authentication. This would have allowed for a truly password-less but authenticated access to all DBs without the need to manage additional users for each database.
Logging, Monitoring and Incident Response
Comprehensive and accurate logs are the cornerstone for a proper incident response. We observed that most accounts were ill-equipped for this purpose as they did not sufficiently log everything.
- 92% of accounts did not log access to the accounts beyond 90 days. This is the same as last year.
- Access logs for object stores like S3 and blob stores were not enabled for over 90% of the buckets. This is an increase of 20% over the previous year and points to an increase in storage requirements. Without monitoring of these logs, any unauthorized accesses could not be identified.
- 54% of the key vaults did not maintain access logs. This leaves security teams blind to any compromise.
- Diagnostics data serve as an early warning against potential problems in a system. Detailed diagnostics were not enabled for 89 percent of databases and VMs in 2020. This number has improved to 75% this year but still requires significant improvements.
Infrastructure Security
- EC2 Instance Metadata Service (IMDS) v1 is known to be insecure and opens up EC2 instances to SSRF vulnerabilities. Over 22% of the instances were still found to have the deprecated version enabled.
- Exposing management ports over the internet opens up the risk of compromise through zero-day or known vulnerabilities in the management services themselves. The incidence of this has reduced significantly compared to last year. Only 11% of the SSH ports are exposed to the internet compared to 26% last year; 4% of RDP ports are exposed this year compared to 20% last year.
Storage and Encryption
- Queueing and notification services often hold sensitive information before it is processed and proper security measures applied. The sensitivity of this is frequently overlooked. 78% of such services were found to be missing server-side encryption.
- It is important to make use of customer-managed keys wherever possible. 99% of the keys used were cloud service provider (CSP) managed. CSPs have vulnerabilities too, and these could result in a loss of confidentiality and integrity of the data stored in the cloud environments. The ChaosDB vulnerability in Microsoft Azure is a recent example.
- 99% of storage buckets did not require mandatory encryption of data at rest or in transit. This risk remains the same as of last year. This exposes the files stored in these buckets to inadvertent compromise due to mistakes.
- The “Block Public Access” setting on S3 is a similar option which reduces the risk of public exposure of the files because of mistakes by users. 71% of the buckets did not have the setting enabled this year, which is a reduction of 7% over the year.
- 80% of block storages did not have disk encryption enabled. This is an increase of 7% over last year. Azure storage sets an example of having disk encryption enabled by default.
Cloud Ransomware
Cloud environments are not immune from malware and ransomware attacks. Threat actors continue to evolve their malware to target cloud environments and the data stored there more effectively. The most common ways attackers infiltrate businesses are by taking advantage of a 'misstep' or ‘misconfiguration’, such as an improperly configured asset, exploiting weak passwords, or exploiting insufficient policy controls. All of these are pervasive cloud security issues – thus cloud-based services are attractive targets for hackers who wish to steal or encrypt data.
- BCP/DR planning is critical to recover from these kinds of attacks. While preventive measures can be taken, this acts as an insurance in the event of an attack. Cloud services make it extremely easy to back and recover assets and data.
- Most newer ransomware not only encrypts the data but also threatens to exfiltrate and release the data. This can be made void by choosing to encrypt all data at rest. This makes the exfiltrated data useless to the adversary.
- Patching – Besides taking advantage of misconfigurations, most malware are able to take hold because of unpatched vulnerabilities. Choosing cloud services where the shared responsibility of patching rests with the CSP completely eliminates this threat vector in cloud services.
- During a malware attack, speed of response is of primary importance. This means the ability to collect logs from all sources, monitor them and automatically respond to critical events before they’ve had the chance to inflict damage.
Supplier Chain Attacks in Cloud
Cloud environments are at increased risk of a supply chain attack and can even lead to compliance risks. Data shows that only 4% of organizations don’t have any 3rd party apps in their environment. This means that the risk of excessive exposure matters for almost all cloud-run organizations. Security teams need to focus on minimizing the risk of 3rd parties in a cloud environment, because it provides room for a supply chain attack. Reducing the permissions provided to 3rd parties should be considered as a top priority and a shared responsibility between customers and vendors alike.
- 15% of vendors receive extensive write-permissions that allow them to modify active cloud resources. In most cases, the access could have been restricted.
- Over 90% of organizations were not aware that they have extensive read-write permissions provided to 3rd party vendors.
Recommendations
- Use zero trust network access (ZTNA) to secure user access to cloud applications. The transformation from an office-based work environment to a secure work-from-anywhere environment cannot happen by adapting the same trust relationships. Companies have to adapt to ZTNA where access to applications is allowed only for authorized users. Zscaler Private Access (ZPA) can help you get zero-trust right by eliminating external attack surfaces and risks of lateral propagation. ZPA hides applications behind a cloud-native proxy and brokers 1:1 connections between users and applications so as not to expose the network.
- Use zero trust for cloud workloads. The transformation to the cloud from the legacy data centers to globally distributed cloud environments faces similar challenges. Companies should expand zero trust to the cloud as they do with people. This trust can go as broad as the communication between VPCs to as granular as communication between applications. Zscaler products such as Zscaler Cloud Connector and Zscaler Workload Segmentations can help solve these problems.
- Log and monitor access and traffic. Besides maintaining visibility as part of a zero trust deployment, incident response activities require comprehensive logging across all assets and services.
- Take responsibility for configuring and maintaining your own environment. While cloud environments are covered under a shared responsibility for security with the service provider, the proper configuration of these environments is the responsibility of the consumers. A cloud security posture management service can help identify misconfigurations, coupled with Cloud Infrastructure Entitlement Management can be used to identify permission issues and act as a logical progression from long-established identity and access management (IAM) and privilege access management (PAM) solutions built on least privilege approaches.
Conclusion
The use of public clouds is growing and so are the attacks targeting them. But that doesn’t mean public clouds are risky and organizations should stay away from them. ThreatLabz has found that the biggest factor in most successful cyberattacks on public cloud instances is security misconfigurations rather than underlying vulnerabilities in these infrastructures.
The pandemic has only accelerated the shift to a distributed workforce and distributed applications. While the risks from these are expanding and the attacks exploiting them are increasing, companies should provide additional focus and scrutiny to their public cloud and focus on adapting their mindset towards securing a distributed workload.




