Update 15/04/11 @ 3.40pm IST: With further research, it has come to our attention that many different pages like main homepage, about us page are infected with malicious Iframe pointing to different malicious sites.
We often blog about popular web sites being infected with different exploit kits. The attack vector remains the same, namely injecting a malicious HTML Iframe or script tag into the legitimate pages. One of our blog readers, Mr. David S. emailed me to share a popup alert that he was receiving on one of the pages of Geek.com. Geek has been a very popular site for online technology resources since 1996. They feature the latest news and reviews from the technology world. Here is the home page:
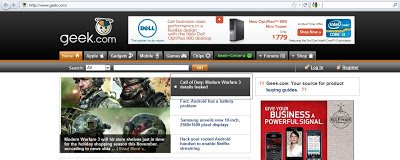 If you look at the screenshot above, you will notice that they feature the latest articles on the home page. The latest topic or article currently discussed is “Call of Duty: Modern Warfare 3 details leaked”. As this is first article is highlighted and “Call of Duty” is a very popular game, one can assume that many people have fallen victim to this attack. It is in the article itself where the malicious Iframe has been injected. Here is the screenshot of the article in question:
If you look at the screenshot above, you will notice that they feature the latest articles on the home page. The latest topic or article currently discussed is “Call of Duty: Modern Warfare 3 details leaked”. As this is first article is highlighted and “Call of Duty” is a very popular game, one can assume that many people have fallen victim to this attack. It is in the article itself where the malicious Iframe has been injected. Here is the screenshot of the article in question: The article was published on May 13th. As usual, the malicious Iframe is injected at the bottom of the page. Here is a screenshot of the malicious Iframe:
The article was published on May 13th. As usual, the malicious Iframe is injected at the bottom of the page. Here is a screenshot of the malicious Iframe: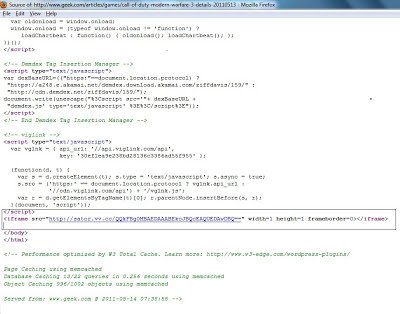 The malicious Iframe redirects victims to a malicious website hosting an exploit kit. Once you visit, heavily obfuscated JavaScript is returned which will target various known vulnerabilities. Here is what the exploit looks like:
The malicious Iframe redirects victims to a malicious website hosting an exploit kit. Once you visit, heavily obfuscated JavaScript is returned which will target various known vulnerabilities. Here is what the exploit looks like:
The decoded version of this malicious JavaScript results in the same vulnerabilities being exploited as we have seen in past blogs on exploit kits, so I will omit details on decoding the JavaScript. For interested readers, a Webpawet report is available for the malicious JavaScript.
Unfortunately, we see hundreds of attacks such as this each and every day. Many legitimate websites are being compromised by taking advantages of poor coding practices in web applications. Attackers are constantly on the lookout for popular websites or top news sites as targets for their attacks. Users need to be aware that no site is a safe site.
Umesh




