Introduction
An aggressive ransomware campaign went viral on May 12, 2017, that impacted over 200,000 systems worldwide and the attack remains active. The use of the leaked NSA "ETERNALBLUE" SMB exploit by the dropper payloads, which target a Microsoft Windows vulnerability in the Microsoft Server Message Block (SMB) v1.0 protocol, made this campaign virulent. Microsoft released a patch for this vulnerability in March 2017 for all the supported operating systems; however, there are still organizations with legacy systems running older and now unsupported operating systems like Windows XP for which the patch was not available in March. Microsoft released an emergency patch over the weekend for the unsupported operating systems in the wake of this attack.
As predicted in the WannaCry Zscaler Security advisory, we are now seeing different variants of the initial dropper in the wild that are leading to the WannaCrypt ransomware infection. In this blog, we will provide a technical analysis of different dropper variants we have seen till now, propagation vectors, and the final ransomware payload.
Figure 1: WannaCrypt infection vectors
1. Initial WannaCry Dropper Variants – May 12, 2017 onwards
The WannaCry dropper variants that we saw in the first 24 hours were all performing the following activities:
a. Killswitch domain check before starting the infection cycle
The dropper payload will attempt to make a direct connection to a hardcoded domain over HTTP and, if the connection is successful, the malware will terminate. The malware payload will begin the infection cycle if the connection is not successful. There have been more variants seen in past 72 hours with different killswitch domains that include:
- iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
- ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
- iuqerssodp9ifjaposdfjhgosurijfaewrwergwea[.]com
- ayylmaotjhsstasdfasdfasdfasdfasdfasdfasdf[.]com
Organizations can locally resolve these domains to a local webserver as an additional safeguard mechanism to mitigate infection from these dropper variants. It is also important to monitor the logs to identify systems that hit this local webserver to perform isolation and remediation activity. The following is a screenshot showing the killswitch domain check:
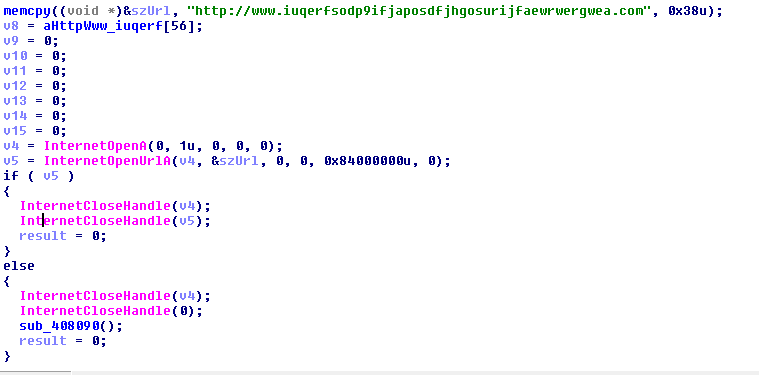
Figure 2: Killswitch domain check from a sample
b. Network propagation using the MS17-010 exploit
The dropper variant will spawn multiple threads to scan for internal as well as external IP addresses on ports 139 and 445 in the /24 subnet range. If the malware finds any IP address with active SMB ports, it will attempt to trigger the MS17-010 exploit and perform remote code execution on the target system. Upon a successful exploit run, the malware will copy the dropper variant on the target system and execute it to perform a similar activity.
Several factors made this attack extremely virulent. They include the use of the recent SMB exploit to perform lateral movement, the delay that exists in most enterprise environments to apply security patches, and the fact that there are still thousands of legacy systems running older operating systems that had no security patch availability until May 13, 2017.
c. Embedded WannaCry 2.0 payload
The dropper payloads contain a WannaCry 2.0 ransomware executable embedded in the resource section. The ransomware executable will be installed on the target system once the SMB exploit is successful, effectively encrypting all the user documents.
Figure 3: Embedded WannaCry 2.0 payload in the dropper
2. New downloader variant using web channel (HTTP) – May 15, 2017
Earlier today (May 15, 2017), we saw a new downloader variant that had an embedded link pointing to the WannaCry 2.0 payload hosted on a compromised server. The downloader payload is packed using UPX packer and is compiled using a "php2exe" tool that converts PHP code into a Microsoft Windows Executable.
- Filename - wcrydl.exe
- MD5 - 2788541f68a8bf3f9f8405bf6fdcd033
The code responsible for downloading and executing the WannaCry 2.0 payload is present in the resource section of the main executable as seen in the screenshot below:
Figure 4: Resource section containing downloader PHP scripts
Here is a screenshot showing the decompiled PHP version of the dropper executable.
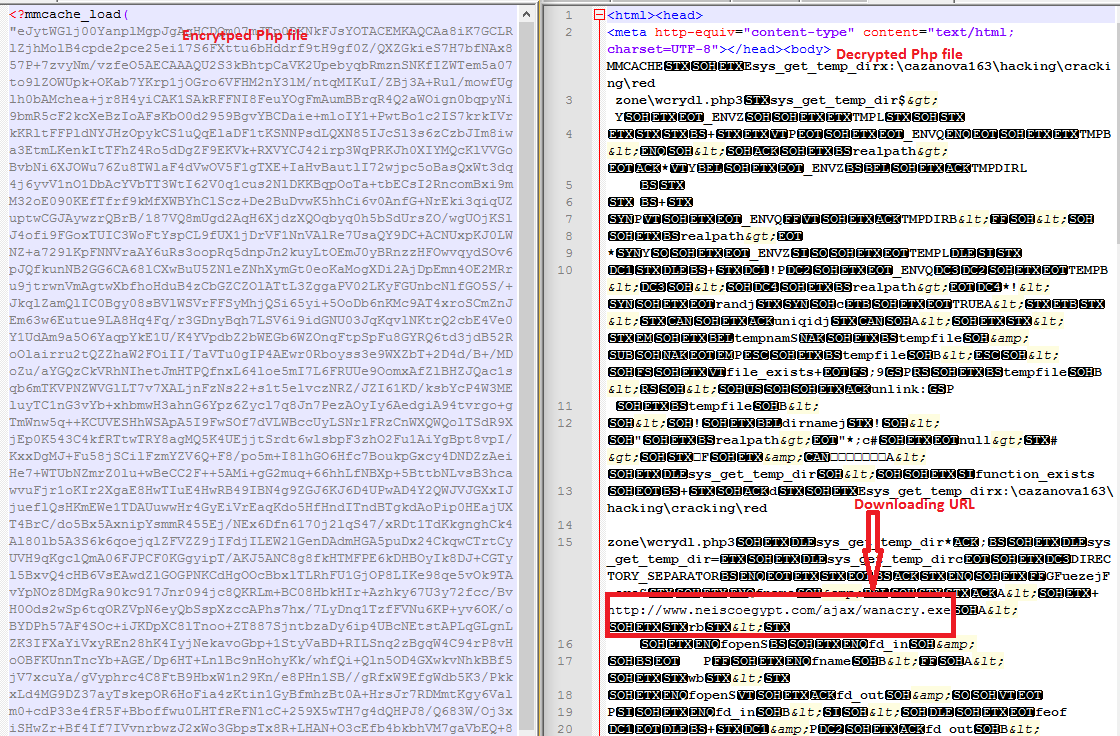
Figure 5: Decompiled downloader PHP code
The remote server hosting the WannaCry payload appears to be compromised. The WannaCry executable is hosted at the following location:
- neiscoegypt[.]com/ajax/wanacry.exe
WannaCry 2.0 payload analysis
The ransomware executables seen in all the campaigns appear to be similar, as we have been able to flag all of them using the first set of signatures deployed on Friday (May 12). The ransomware executable contains a password-protected resource section containing configuration data.
The WannaCry payload performs following activity when executed on the victim system:
- It uses a random string, referred here as RAND_Install_STRING ( e.g - bcjlwytjyjlj255), created based on computer name and random values for installation folder and service name.
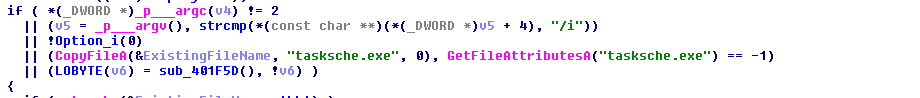
Figure 6: Installation folder and service name
- If C:\ProgramData folder exists, it creates a new folder with name as RAND_Install_STRING inside ProgramData folder. Otherwise, it creates a folder "Intel" in <Window_InstallationDrive> and a sub-folder with a random name. In both cases it copies itself with the name tasksche.exe.
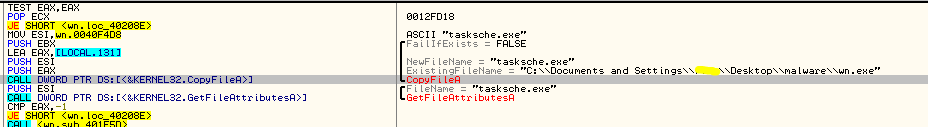
Figure 7: Installation folder and payload
- It checks if there is a service with name RAND_Install_STRING; if not it creates a service with the name RAND_Install_STRING and starts it.
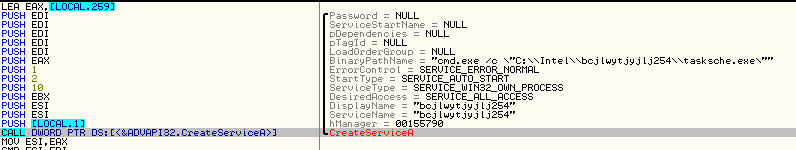
Figure 8: New process to run the dropped executable
- CIt creates a registry key with name "WanaCrypt0r" to store the installation path.
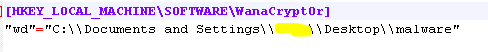
Figure 9: Registry entry to store installation path
- The malware has all its config data in the resource section and the password is “WNcry@2ol7.” These additional components are extracted from resource section "XIA" to the current execution path.
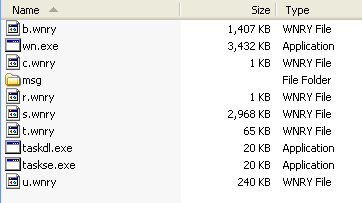
Figure 10: Additional ransomware resources including ransom note
- The ransom note is embedded in 28 different languages inside the ransomware payload:
Figure 11: Ransom note in multiple languages
- It loads encrypted DLL and starts the file encryption process on the victim's machine. It will look for user files with the following extensions to encrypt:
.lay6 .sqlite3 .sqlitedb .accdb .java .class .mpeg .djvu .tiff .jpeg .backup .vmdk .sldm .sldx .onetoc2 .vsdx .potm .potx .ppam .ppsx .ppsm
.pptm .pptx .xltm .xltx .xlsb .xlsm .xlsx .dotx .dotm .docm .docb .docx
The encrypted files are renamed with the “.wnry” extension and the ransom instructions are in text file name “@Please_Read_Me@.txt.”
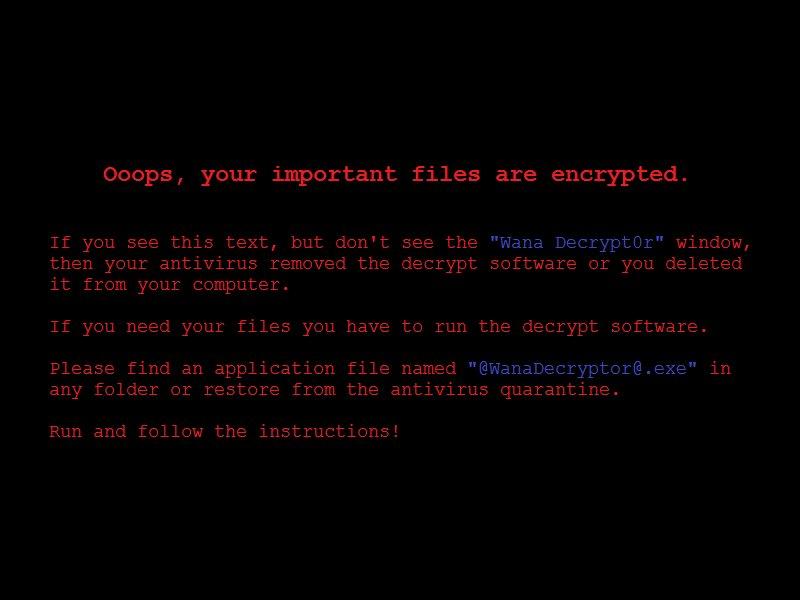
Figure 12: WannaCry ransom note
Conclusion
Several ransomware outbreaks started in 2016 and we have seen dozens of new strains in the past year and a half. However, the delivery vector seen in the case of WannaCrypt 2.0 makes it highly virulent and successful in impacting thousands of users in a short time frame. We will continue to see newer delivery vectors and various copy-cat strains of this malware in the coming weeks, given the global impact this has had.
Zscaler ThreatLabZ is actively monitoring this threat and will continue to ensure coverage for Zscaler customers.
Acknowledgement
Abhaykant Yadav, Amandeep Kumar, Nirmal Singh for helping with the analysis
Indicators of compromise
MD5 hash
84c82835a5d21bbcf75a61706d8ab549
7f7ccaa16fb15eb1c7399d422f8363e8
2b4e8612d9f8cdcf520a8b2e42779ffa
509c41ec97bb81b0567b059aa2f50fe8
835fff032c51075c0c27946f6ebd64a3
86721e64ffbd69aa6944b9672bcabb6d
f9cee5e75b7f1298aece9145ea80a1d2
b7f7ad4970506e8547e0f493c80ba441
c61256583c6569ac13a136bfd440ca09
f9992dfb56a9c6c20eb727e6a26b0172
d6114ba5f10ad67a4131ab72531f02da










