Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
ThreatLabz-Report: 87,2 % der Bedrohungen werden über verschlüsselte Kanäle übertragen
Verschlüsselung hat sich längst als Standard für die Online-Kommunikation etabliert. Heute wird fast der gesamte Webtraffic durch sichere Protokolle wie TLS/SSL geschützt. Doch da Verschlüsselung zunehmend allgegenwärtig wird, erhöhen sich auch die Möglichkeiten für Bedrohungsakteure, verschlüsselte Kanäle auszunutzen.
Verschlüsselung schützt nicht nur legitime Aktivitäten, sondern fungiert auch als Kanal für schädliche Aktivitäten. Angreifer nutzen verschlüsselte Kanäle, um herkömmliche Abwehrmaßnahmen zu umgehen und Malware, Phishing-Kampagnen, Kryptomining/Kryptojacking und Datendiebstahl heimlich durchzuführen.
Der Report von Zscaler ThreatLabz untersucht diese sich entwickelnde Bedrohungslage auf Grundlage einer umfassenden Analyse von Milliarden von Bedrohungen, die über HTTPS übermittelt und von der Zscaler-Cloud blockiert wurden. Der Report beleuchtet aktuelle Trends, die wichtigsten Bedrohungskategorien, die häufigsten Ziele verschlüsselter Angriffe und andere Erkenntnisse darüber, wie Angreifer verschlüsselten Traffic als Waffe einsetzen.
5 wichtige Erkenntnisse zu verschlüsselten Angriffen
Das Forschungsteam von ThreatLabz analysierte 32,1 Milliarden verschlüsselte Angriffe, die zwischen Oktober 2023 und September 2024 von der Zscaler-Cloud blockiert wurden, um aktuelle Bedrohungsmuster zu erkennen und zu verstehen. Im Folgenden werden einige der wichtigsten Trends und Angriffsziele erläutert.
- Stetiger Anstieg verschlüsselter Angriffe: Die Zscaler-Cloud blockierte während des Analysezeitraums eine beispiellose Menge von Angriffen im TLS/SSL-Traffic. 87,2 % aller blockierten Angriffe waren verschlüsselte Bedrohungen. Dies entspricht einem Anstieg der verschlüsselten Angriffe um 10,3 % im Vergleich zum Vorjahr und zeigt, dass Bedrohungsakteure sich zunehmend auf Verschlüsselung verlassen, um ihre schädlichen Aktivitäten zu verbergen.
- Malware dominiert die Landschaft: Malware bleibt die am weitesten verbreitete verschlüsselte Bedrohung und macht 86,5 % der blockierten Angriffe aus. Dieser Trend unterstreicht die Anpassung von Malware-Taktiken an verschlüsselte Kanäle, indem Verschlüsselung zum Maskieren von Payloads und Umgehen herkömmlicher Sicherheits- und Erkennungsmaßnahmen eingesetzt wird.
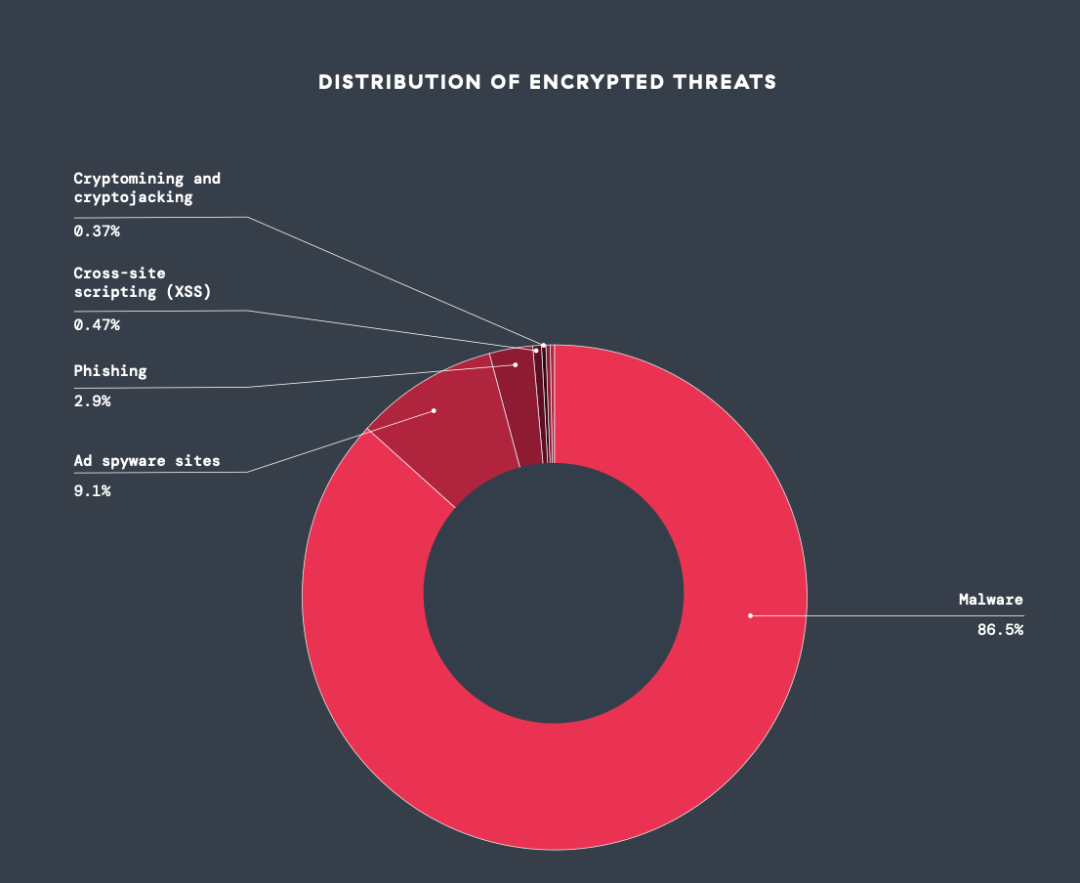 Abbildung 1: Die wichtigsten beobachteten Bedrohungskategorien
Abbildung 1: Die wichtigsten beobachteten Bedrohungskategorien - Kryptomining/Kryptojacking,Cross-Site-Scripting und Phishing-Bedrohungen nehmen zu: Kryptomining/Kryptojacking und Cross-Site-Scripting (XSS) gehören zu den am schnellsten wachsenden verschlüsselten Bedrohungen, mit einem Anstieg von 122,9 % bzw. 110,2 % im Vergleich zum Vorjahr. Beim Phishing gab es einen bemerkenswerten Anstieg von 34,1 %. Möglicherweise sind diese Spitzen auf die zunehmende Nutzung generativer KI-Technologien zurückzuführen, die die Erstellung komplexer Kryptomining-Skripte, die Automatisierung schädlicher XSS-Skripte und die Durchführung äußerst überzeugender Phishing-Kampagnen vereinfachen.
- Die Fertigung führt die Liste der am stärksten betroffenen Branchen an: Die Branchen Fertigung, Technologie und Dienstleistungen waren am stärksten betroffen. Zwischen Oktober 2023 und September 2024 wurden 13,5 Milliarden verschlüsselte Angriffsversuche auf Fertigungsunternehmen beobachtet.
- Die USA und Indien bleiben die Hauptziele: Mit 11 Milliarden (USA) bzw. 5,4 Milliarden (Indien) verschlüsselten Angriffen während des Analysezeitraums blieben die USA und Indien die am häufigsten angegriffenen Länder, gefolgt von Frankreich, Großbritannien und Australien.
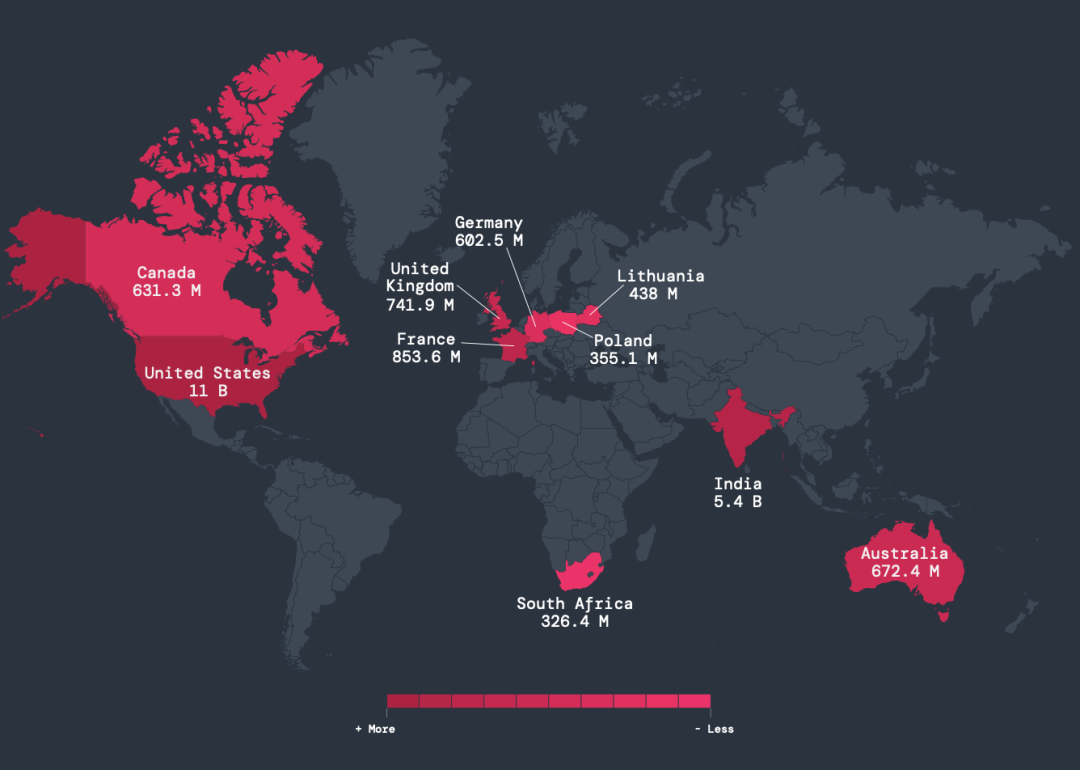
Abbildung 2: Eine Karte der Länder, in denen die meisten Verschlüsselungsangriffe stattfinden
Neue Trends bei verschlüsselten Angriffen
ThreatLabz hat viele wichtige Trends bei verschlüsselten Angriffen aufgedeckt, von Angreifern, die Verschlüsselungskanäle nutzen, um vertrauliche Daten abzugreifen, bis hin zu AiTM-Methoden (Adversary-in-the-Middle), bei denen komplexe Tools zum Einsatz kommen, und TLS/SSL-Verschlüsselung zur Erstellung schwer erkennbarer Phishing-Kampagnen. Der Report enthält Beispiele für alle diese Methoden.
Ein bemerkenswerter Trend, den ThreatLabz im Detail untersucht hat, ist der zunehmende Missbrauch von Cloud-Services durch APT-Gruppen (Advanced Persistent Threats). Indem sie ihre schädliche Kommunikation im legitimen Traffic von Cloud-Services verbergen, können APT-Gruppen die standardmäßige TLS/SSL-Verschlüsselung ausnutzen, um Netzwerksicherheitskontrollen zu umgehen. ThreatLabz hat diesen Trend eingehend untersucht und stellt eine detaillierte Analyse mit Informationen zu folgenden Schwerpunkten bereit:
- Die größten APT-Gruppen, die Cloud-Services missbrauchen
- Die 10 am häufigsten missbrauchten Cloud-Services
- Die am häufigsten zur Bereitstellung von Payloads missbrauchten Services
- Die häufigsten Taktiken beim Missbrauch von Cloud-Services
So stoppt Zscaler verschlüsselte Bedrohungen
Die Zscaler Zero Trust Exchange stellt eine leistungsstarke Lösung zur Abwehr verschlüsselter Bedrohungen bereit, angefangen mit der Beseitigung von Transparenzlücken durch Funktionen zur TLS/SSL-Überprüfung und KI-gesteuerte Abwehrmaßnahmen. So bekämpft Zscaler verschlüsselte Bedrohungen in allen Angriffsphasen.
Minimale Angriffsfläche
Unkontrollierte verschlüsselte Verbindungen, etwa über VPNs oder exponierte Workloads, können die Angriffsfläche vergrößern und Angreifern ermöglichen, sich problemlos zu verstecken. Zscaler eliminiert dieses Risiko und die Angriffsfläche, indem Anwendungen und Dienste im Internet unsichtbar bleiben. Dieser Ansatz verhindert, dass verschlüsselte Bedrohungen kritische Anwendungen und Systeme erreichen, und bietet proaktiven Schutz, der nicht auf gemeinsamen Netzwerkzugriff angewiesen ist.
Verhinderung des Erstzugriffs
Zscaler Internet Access™ (ZIA) gewährleistet lückenlose TLS/SSL-Überpürfung, um sämtliche Verbindungen zu verifizieren und versteckte Bedrohungen zu stoppen, ohne die Performance zu beeinträchtigen. Die Überprüfungsfunktionen von ZIA nutzen KI-gestützte Analysen und Inline-Erkennung, um komplexe Bedrohungen im verschlüsselten Traffic schnell zu identifizieren und zu blockieren. Durch diesen Ansatz werden herkömmliche, ressourcenintensive physische Geräte überflüssig, sodass Unternehmen das Wachstum des verschlüsselten Traffics problemlos und ohne Unterbrechungen bewältigen können.
Keine laterale Ausbreitung
Sobald sich Angreifer Zugang zu Netzwerken verschafft haben, versuchen sie sich häufig lateral darin zu bewegen. Zscaler verhindert dies mit Zero-Trust-Segmentierung und KI-gestützten, kontextbezogenen Richtlinien, die über Zscaler Private Access™ (ZPA)bereitgestellt werden. ZPA erzwingt detaillierte Zugriffskontrollen und beschränkt User auf bestimmte Anwendungen basierend auf Identität, Kontextdaten und Richtlinien. Dadurch wird die komplexe regelbasierte Netzwerksegmentierung durch eine optimierte, identitätsbasierte Zugriffskontrolle ersetzt. Darüber hinaus nutzt Zscaler eine Deception-Technologie und platziert Decoys, um laterale Begwegungen innerhalb des verschlüsselten Traffics zu erkennen und zu vereiteln.
Blockieren von Command-and-Control-Rückrufen
Malware nutzt für die Kommunikation mit C2-Servern häufig verschlüsselte Kanäle. Dadurch können Angreifer Befehle ausführen, zusätzliche Malware herunterladen oder vertrauliche Daten exfiltrieren. ZIA überprüft den gesamten ausgehenden und eingehenden verschlüsselten Traffic, um C2-Kommunikationen zu unterbrechen. Die KI-gestützten DLP-Tools (Data Loss Prevention) von Zscaler erkennen und blockieren schädlichen Traffic und verhindern so, dass vertrauliche Daten exfiltriert werden und verschlüsselte C2-Rückrufe das Netzwerk gefährden.
Fallstudie: Erfahren Sie, wie Wipro mit Zscaler in einem Quartal 8,2 Millionen verschlüsselte Bedrohungen blockierte
Wipro ersetzte herkömmliche Firewalls und VPNs durch Zscaler und stärkte die Abwehrmaßnahmen mit Inline TLS/SSL-Überprüfung des gesamten Internet- und SaaS-Traffics, um verschlüsselte Bedrohungen zu erkennen und zu blockieren. Zur Fallstudie
Warum lückenlose TLS/SSL-Überprüfung unverzichtbar ist
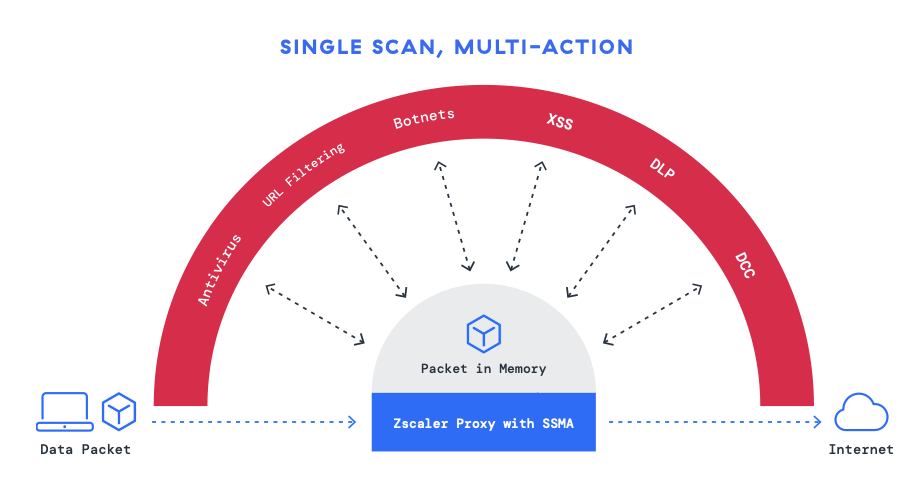
Die Grundlage der Abwehr von Zscaler gegen verschlüsselte Bedrohungen sind die Funktionen zur lückenlosen TLS/SSL-Überprüfung, die durch eine skalierbare Proxy-basierte Architektur ermöglicht werden. Anders als bei herkömmlichen hardwarebasierten Lösungen, bei denen Unternehmen Kompromisse zwischen Sicherheit und Geschwindigkeit eingehen müssen, ermöglicht der Cloud-native Ansatz von Zscaler Unternehmen eine umfassende und skalierbare Überprüfung des Traffics mithilfe der einzigartigen Single Scan, Multi-Action-Engine, die den Traffic einmal verarbeitet, um mehrere Sicherheitskontrollen gleichzeitig anzuwenden. Dadurch profitieren Unternehmen von mehreren Vorteilen:
- Lückenlose Überprüfung des gesamten verschlüsselten Traffics prüfen: Im Gegensatz zu Lösungen, die aufgrund von Hardwareeinschränkungen nur einen Bruchteil des verschlüsselten Traffics prüfen, stellt die Cloud-native Architektur von Zscaler sicher, dass ausnahmslos jedes Paket geprüft wird.
- Erweiterte Sicherheitskontrollen auf mehreren Ebenen: Integrierte, KI-gestützte Sicherheitskontrollen erkennen und blockieren Bedrohungen, die in verschlüsseltem Traffic eingebettet sind.
- Hervorragende Performance: Die Architektur von Zscaler beseitigt Engpässe, die typischerweise mit Hardwaregeräten verbunden sind.
Bleiben Sie verschlüsselten Bedrohungen immer einen Schritt voraus
Aus den Ergebnissen des ThreatLabz-Reports zu verschlüsselten Bedrohungen geht deutlich hervor, dass Bedrohungsakteure zunehmend raffinierte Verschlüsselungs- und KI-Technologien nutzen um einer Entdeckung zu entgehen und ihre Wirkung zu maximieren.
Informieren Sie sich über die aktuellen Forschungsergebnisse und erfahren Sie mehr darüber, wie Sie verschlüsselten Bedrohungen immer einen Schritt voraus sind. Schwerpunkte des Reports:
- Tiefgehende Analyse: Detaillierte Erkenntnisse und Fallstudien darüber, wie Angreifer Verschlüsselung ausnutzen.
- Prognosen für 2025: Experteneinblicke in die Entwicklung der verschlüsselten Bedrohungslage
- Umsetzbare Best Practices: Eine praktische Checkliste zur Verbesserung Ihrer Abwehrmaßnahmen gegen verschlüsselte Angriffe.
Schützen Sie Ihr Unternehmen vor verschlüsselten Bedrohungen. Holen Sie sich noch heute Ihr Exemplar des Reports.
War dieser Beitrag nützlich?
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.



