- hxxp://kivancoldu.com/, redirects to hxxp://click-videox.com/
 |
| http://kivancoldu.com on 05/02/2013 |
- hxxp://fastcekim.com/, redirects to hxxp://click-videox.com/
- hxxp://kivanctatlitug.tk/ d(down)
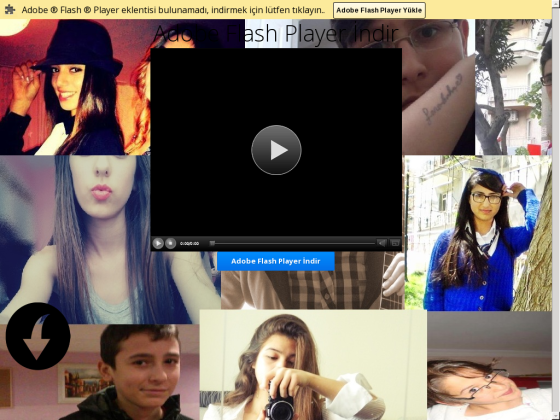 |
| hxxp://kivanctatlitug.tk/ |
What is interesting is that the malicious executables are actually hosted in a DropBox account and have not been taken down since they were found about seven days ago. I have spotted two different executables so far:
- FlashPlayer.sfx.exe (detected by only 2 of 46 AV vendors)
- Videonuizle.exe (detected by 5 of 46 AV vendors)
Interestingly, there is a link on the malicious websites that shows how many people visited it. There were 1,412 unique visitors in a single day.
There is another peak of traffic report and on 05/02 registered 1,700 visitors...and counting.
These sites keep popping up and the are still able to fool users.






