We hope you enjoyed your own Black Friday and found everything you wanted as you were shopping the sales. The threat actors certainly attempted to take advantage of the zeal of holiday shoppers. As a follow-up to our previous blog on shopping scams, we’d like to show some of the other attacks we saw during the Thanksgiving break. We’ll highlight a few more phishing tactics commonly used, a Magecart POS skimmer attack on a major brand, and further evidence of Emotet’s prevalence in the overall threat landscape.
The primary motivation of attackers is to take advantage of the online shopping season. Sales are already up for most retailers as consumers snap up deals.
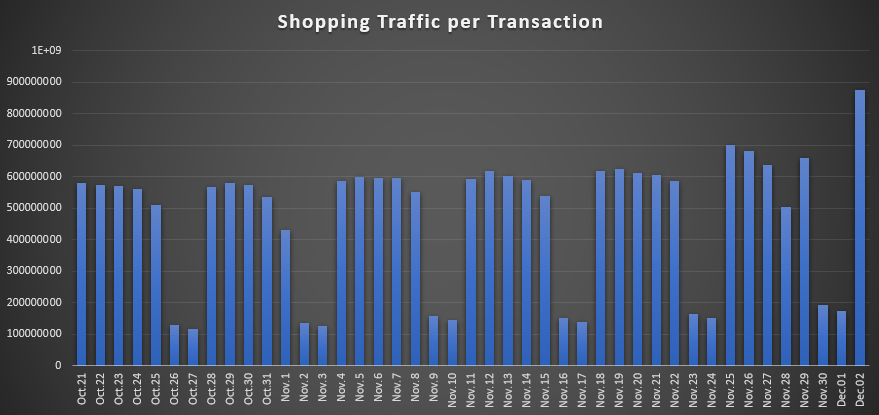
Fig 1: Shopping trends continued to rise through November (the spike at the end is Cyber Monday)
Scams and phishing attempts continue at a steady pace into the holiday shopping season. Attackers know that they can cast a wide net of branded phishing attacks, gift card scams, and malicious files to boost their profitability every year.
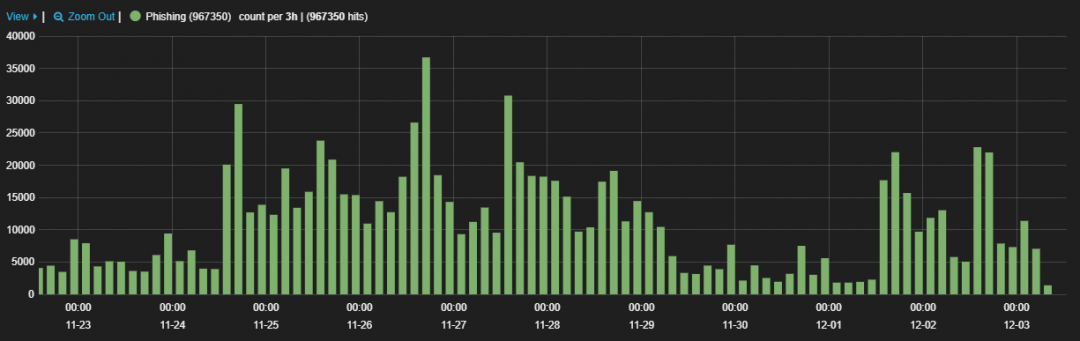
Fig 2: Phishing attempts rose during the week before Thanksgiving and Black Friday
Magecart
Magecart has been quite active so far. We have observed consistent hits in the weeks leading up to the holiday season and they persist. The chart below shows that Magecart infections are proving to be quite a sustainable means for attackers.
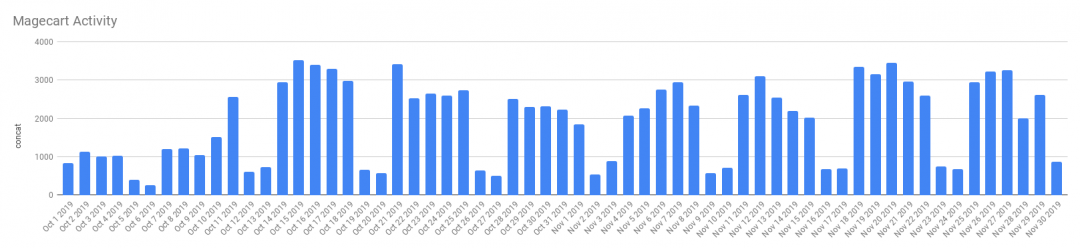
Fig 3: Magecart activity tracked over two months (Oct-Nov 2019)
Recently, threat actors targeted the Macy's website. Macy's released a “Notice Of Data Breach” on November 14, 2019. The company stated that the site was compromised by attackers on October 7, 2019. The attackers had inserted an obfuscated version of a Magecart script to the Macy's Checkout and My Wallet pages. According to the breach notice, attackers were able to capture user credit card data. The user-submitted details were exfiltrated to a command-and-control (C&C) server at barn-x[.]com.
Phishing
As we reported in the previous blog, Amazon has been heavily targeted this season, but it isn’t the only brand under attack. All major brands are considered fair game to threat actors. This season, Apple has become a focus of attackers. Below is one such case.

Fig 4: Fake Apple login page
One of the first things you should do before logging into sensitive websites is to check the address bar to ensure you are in the correct place. If you are unfortunate to enter your Apple ID into this portal, your information will be sent to the attackers.
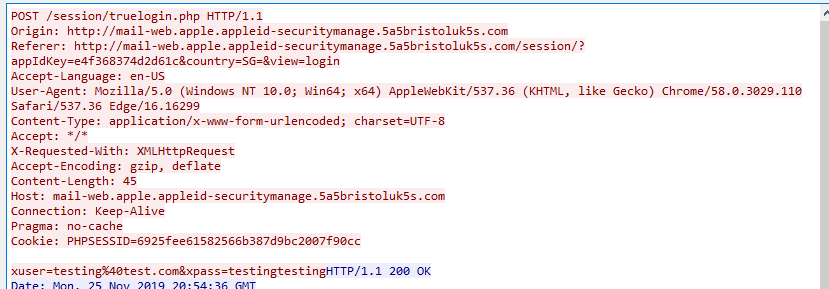
Fig 5: Information is sent in clear text to the attackers as well as any other attackers currently performing a man-in-the-middle (MitM) attack
After a phishing attack is successful, users get redirected to a message about their account being locked.

Fig 6: after entering Apple login information, the user receives a message from the attacker saying the account has been locked
Black Friday Phishing
Black Friday offers aren’t just big in the U.S.—the start of the shopping season is celebrated all around the world. The image below shows a phishing page claiming to offer Black Friday deals from Americanas.com.br, a major Brazilian retail chain. Notice the domain: the entire content is hosted on Joomla. A legitimate vendor would never host its products via a content management/publishing framework.
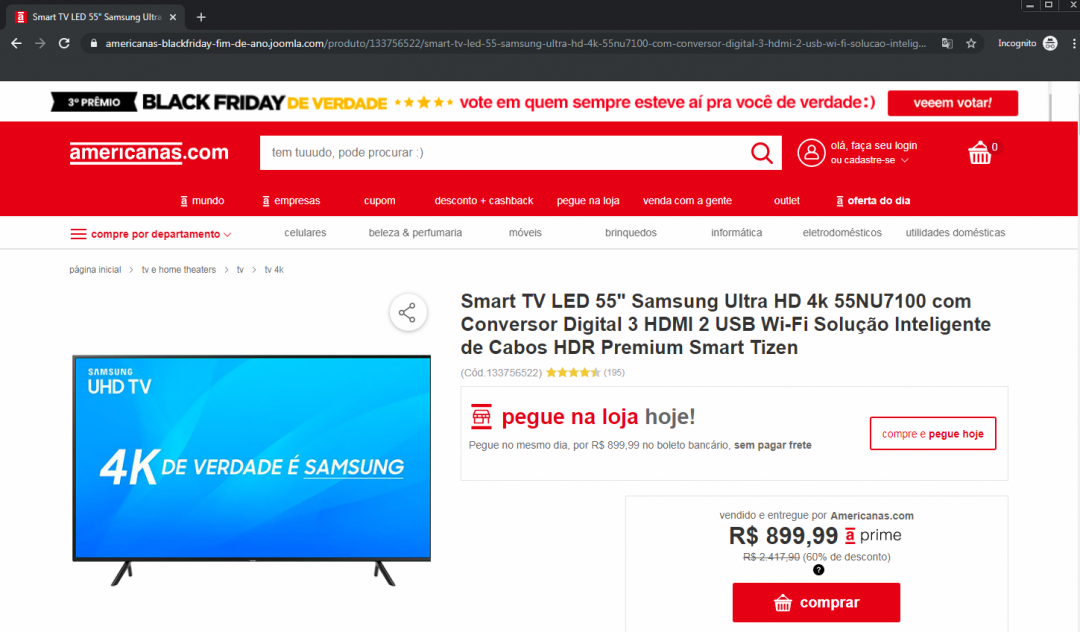
Fig 7: Faked Americanas site being hosted on Joomla
The screen below is another example of threat actors targeting users via a fake Americanas.com.br site. As of the writing of this blog, the domain hosting this page was only five days old.
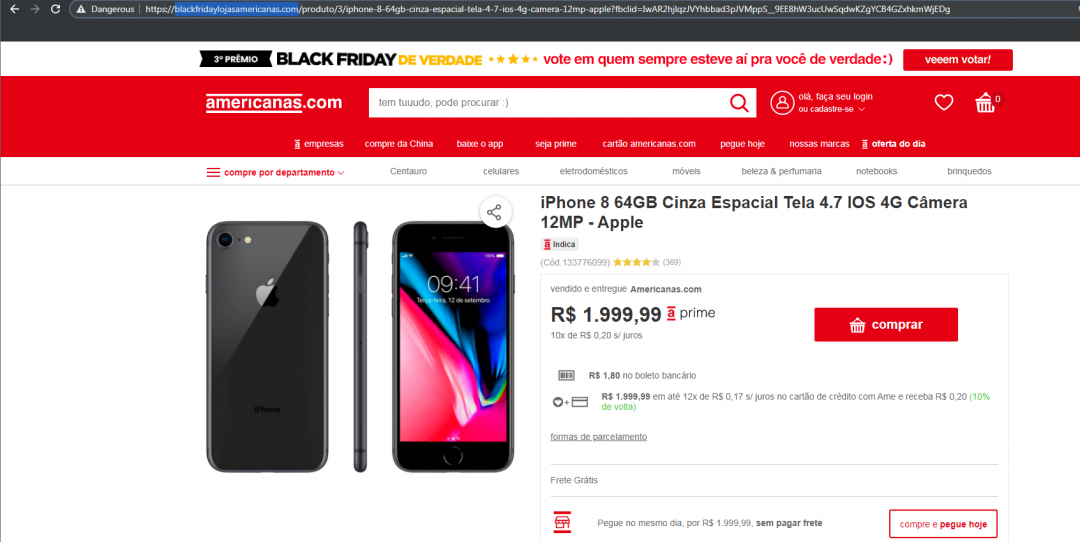
Fig 8: Faked Americanas site on a newly registered domain
Emotet
In our previous blog, we discussed how webmail was a critical element in Emotet infection downloads. Another attack vector favored by threat actors is leveraging compromised WordPress sites—specifically, SSL-secured WordPress sites. Attackers assume (correctly, in many cases) that consumers don’t have a security solution that inspects encrypted traffic (HTTPS). In fact, when you look at the last 1,000 confirmed Emotet samples on URLhaus, 475 of them at the time of this research were using HTTPS to infect users.
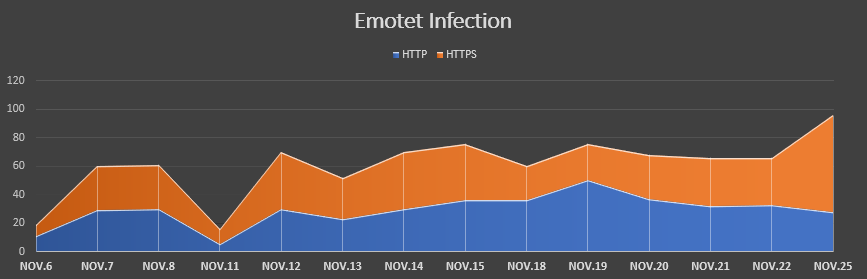
Fig 9: HTTPS is the primary method of infection
Conclusion
The Zscaler ThreatLabZ team will continue to track and block various campaigns and tools used by threat actors. We work diligently to protect our customers from these malicious attacks. Users should be cautious and protect themselves, particularly during the shopping season, by reviewing our security checklist:
- Change your passwords for critical and important accounts
- Enable two-factor authentication, or “2FA”
- Ensure HTTPS is inspected by your security solution; check for HTTPS/secure connections when visiting shopping/e-commerce/financial websites
- Be vigilant about invoices/orders arriving in email; do not forward such attachments to anyone and be sure to follow IT protocol
- Be vary of tracking number links in emails from shipping/courier companies, as they may direct you malicious sites
- Do not click on any links from unrecognized senders; even if you do not follow through, the action of clicking the URL is a beacon for the attacker
- Do not provide any credentials via Google docs; legitimate vendors do not ask for credentials via this medium
- Avoid using public or unsecured Wi-Fi connections for shopping
- Review helpful instructions by the Federal Trade Commission (FTC) on Identify Theft, Recognizing and Avoiding Phishing Scams, and Understanding Mobile Apps and Malware
- Review the National Cybersecurity and Communications Integration Center's (NCCIC) Holiday Scams and Malware Campaigns warning and recovery actions message
- Report incidents to the FTC





