Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Zero Compromise with Content Disarm and Reconstruction (CDR), powered by Zscaler Browser Isolation and Votiro
Files are the core of business operations, whether your employees need to download/upload a file or transfer to/from partners, customers and suppliers. Zero-day threats could often hide within benign looking files. At the same time, your employees may be working from anywhere and need to upload an important file, albeit infected due to mobility flexibility, to your web portals and Internet applications. Moreover, steganography attacks are on the rise as well, whereby a malware or a risky employee may exfiltrate data by hiding the sensitive data within an image file to avoid detection.
AI-powered Sandbox can do a comprehensive analysis and protect your organization from any file borne threats coming from web destinations or your customer-facing portals. However, in a bid to improve productivity, access to the content or those files may still be needed.
So, the key question becomes - can you boost productivity without incurring the security risk inherent in file-borne threats?
Zscaler Browser Isolation + Votiro
The Zscaler Zero Trust Exchange platform protects thousands of customers from cyberattacks and data loss by securely connecting users, devices, and applications in any location. Zscaler Browser Isolation, natively integrated within the platform, detonates the web content and isolates any associated zero day threats in an air-gapped cloud container, while enforcing clipboard, upload/download, read-only etc. controls and streaming safe pixelated content to the user’s favorite browser. The built-in document processing technology can allow the productivity related files (docx, pptx, vsdx, rtf etc.) to be safely viewed within isolation (‘protected storage’) or downloaded as sanitized pdf (Level-1 CDR).
Votiro’s Zero Trust DDR (Data Detection and Response) provides organizations around the globe with real-time privacy masking, data compliance, proactive file-borne threat prevention, and actionable data insights. This multi-faceted approach to cybersecurity prevents risks to private data in-motion by detecting and masking information while also disarming known and unknown cyber threats before they reach user endpoints.
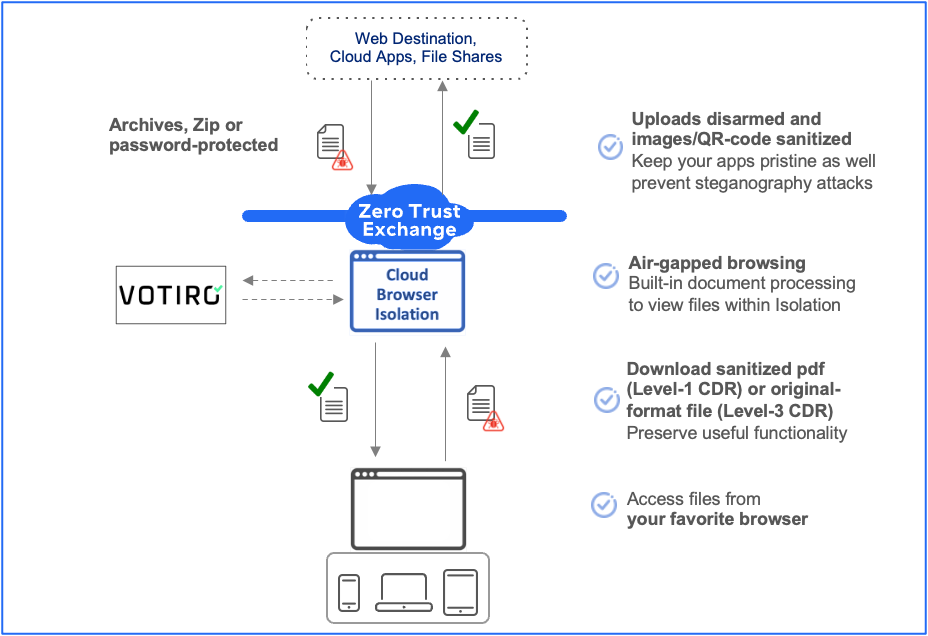
Together, the architecture entails regeneration of file content by stripping out potential threats and reconstructing only safe, known good content, ensuring the resulting original-format file is safe and fully functional for end users and apps to use (Level-3 CDR). This means you can edit a Word document or build over the data model within an Excel file or a financial planning workbook. Same can be done for archives, images, zipped and password-protected files.
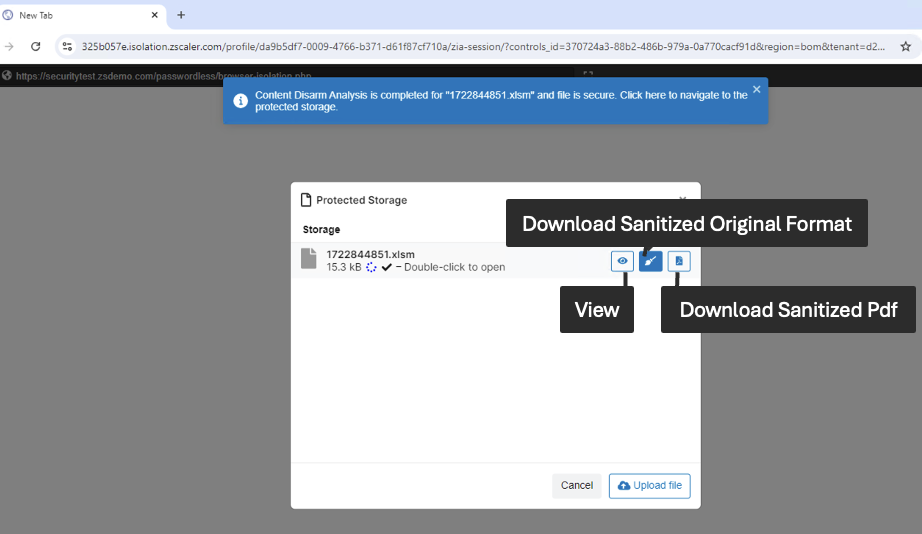
End-user options
The end-user gets the full flexibility to choose among different options, within the Browser Isolation session, depending upon the use case requirements.
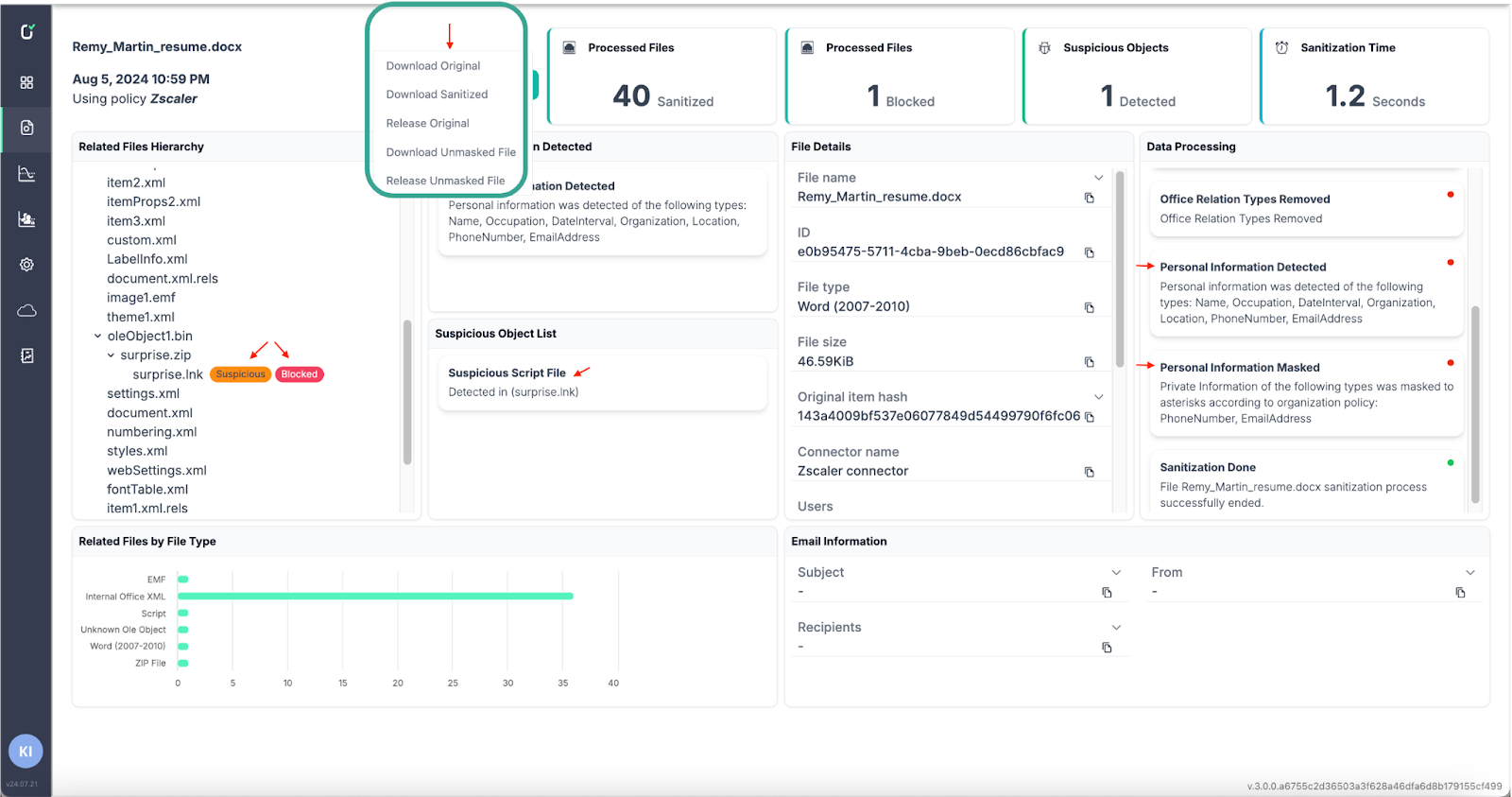
Admin control and visibility
The security team can access the original file for further investigations and threat hunting.
Benefits
This integration provides zero compromise - allows non-stop productivity and ensures cyber protection while keeping intact the file functionality and quality.
Threat Protection: The architecture detects the true type of the files and performs actions accordingly e.g. weaponized files with misleading file type extensions are automatically blocked. The file structure is analyzed for the hidden file objects and the file content is checked for any risky URLs. Any active content, such as VBA macros, are analyzed and ruled out based on a Machine Learning (ML) trained algorithm. Based on the security policies, metadata can be discarded or preserved for security and audit requirements. Archives are being extracted and processed recursively, and embedded objects in documents are handled as well, thus preserving the end user experience while protecting from file-borne threats.
Data Protection: Any images are reconstructed as part of the sanitization process, eliminating any hidden code, without compromising the quality. The process is also applied for images embedded in documents and in archive files. Moreover, any QR codes are disarmed as well, this effectively thwarting any steganography attacks.
Embark on your CDR journey now…
In a nutshell, Zscaler Browser Isolation and Votiro integration allows non-stop productivity without incurring the security risk inherent in the file borne threats. Drop us a line for a quick demo, or refer to the deployment guide! We will partner with you on your CDR journey, so you can accelerate your innovation path with zero compromise!
War dieser Beitrag nützlich?
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.



