PDF exploits have been targeted by Blackhole exploit kits for some time now. The Blackhole exploit kit will deliver various malicious PDF files to a user if the victim is running a potentially vulnerable version of Adobe Reader. When these PDFs are opened through Adobe Reader, a known vulnerability is exploited which will then compromise the user’s machine.
Let’s look at the de-obfuscated portion of the Blackhole exploit kit. The exploit kit for this sample was delivered from “flightpub.net/l/src.php?case=46677c190b37f2d6”.
 The de-obfuscated code above shows how an iFrame of 1x1 pixels is created to load a malicious PDF file residing at “./content/ap1.php?f=97d19::182b5” or “./content/ap1.php?f=97d19::182b5”, depending upon the version of Adobe reader installed. These two files are hosted on same the domain - “flightpub.net”.
The de-obfuscated code above shows how an iFrame of 1x1 pixels is created to load a malicious PDF file residing at “./content/ap1.php?f=97d19::182b5” or “./content/ap1.php?f=97d19::182b5”, depending upon the version of Adobe reader installed. These two files are hosted on same the domain - “flightpub.net”.
The absolute paths of the malicious files are,
hxxp://flightpub.net/l/content/ap1.php?f=97d19::182b5 and
hxxp://flightpub.net/l/content/ap2.php?f=97d19::182b5
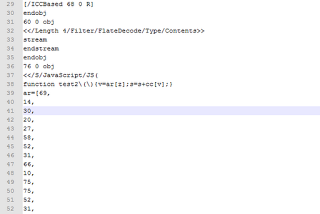
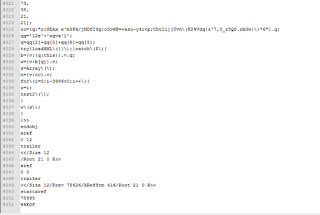
For analysis purposes, we can manually downloaded the aforementioned PDF files. The PDF files contain a JavaScript object, which contains obfuscated JavaScript, as shown below:
The JavaScript code loops through array ‘ar’ and converts each element of the array with logic included in function ‘test2()’. The de-obfuscated code targets a three year old vulnerability in Adobe Acrobat reader.
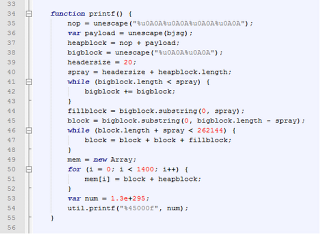
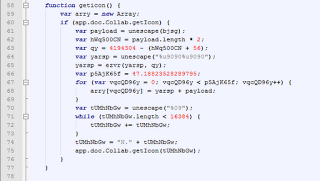
Let’s take a look at the some of the de-obfuscated code,
A stack based buffer overflow vulnerability exists in the ‘getIcon()’ method, which is detailed in CVE-2009-0927.
This vulnerability is widely targeted by various versions of the Blackhole exploit kit. I have seen different variants of the payload URL used to host these PDF exploits. The URL pattern changes with different variants of the exploit kit. The different URL path patterns seen so far are:
/content/ap1.php?f=97d19::182b5
/content/ap2.php?f=97d19::182b5
/content/fdp1.php?f=63
/content/fdp2.php?f=63
/content/adfp2.php?f=193
/content/adfp1.php?f=193
The common pattern in the above URL paths are ‘/content/’ and ‘.php?f=’. By identifying these common patterns one can write a network signature on URL strings to catch these malicious URLs.
Let’s take a look at couple of snort signatures for detecting these malicious URL’s.
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET CURRENT_EVENTS Blackhole Acrobat 1-7 PDF exploit download request 3"; flow:established,to_server; content:"/fdp1.php?f="; http_uri; reference:md5,8a33d1d36d097ca13136832aa10ae5ca; reference:cve,CVE-2011-0611; classtype:trojan-activity; sid:2014052; rev:2;)
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET CURRENT_EVENTS DRIVEBY Blackhole PDF Exploit Request /fdp2.php"; flow:established,to_server; content:"/fdp2.php?f="; http_uri; reference:md5,8a33d1d36d097ca13136832aa10ae5ca; reference:cve,CVE-2011-0611; classtype:trojan-activity; sid:2014035; rev:2;)
Most of the vulnerabilities targeted by various exploit kits are public. Making sure all of your applications are updated regularly with the latest security updates will go a long way in helping to keep your computer secure.
Pradeep