Santander, a well-known banking site, has often been the target of phishers. In fact, Santander UK often makes the top-10 list of most popular targets according to Phishtank. Last week, we found a phishing site for the Brazilian branch, santander.com.br, that was receiving traffic from a DNS cache poisoning attack.
The phishing site hosted on 200.252.58.134 looks identical to the original site. The attackers have replicated the entire login process in order to gather the login, password, and security code of the bank users.
 |
| Santander Brazil phishing site |
 |
| Original Santander Brazil home page |
The DNS poisoning made this attack much more effective. The hijacked DNS servers were resolving santander.com.br to 200.252.58.134 (phishing site) instead of 200.220.178.3 or 200.220.186.3 (legitimate sites). In such a situation, phishers do not need to blast emails to random Brazilian email accounts. They just need to wait for the Santander customers to log in to their bank accounts when accessing the site via the poisoned DNS servers.
DNS poisoning also renders virtually all browser phishing defenses useless. Google Safe Browsing (Firefox, Safari, Chrome, etc.) and Phishtank (Opera, etc.) both rely on denylists, which are lists of URLs or domains to block. It can be very hard for the user to realize this is a phishing site because it looks exactly like the real site, and the URL shows the correct domain.
In this attack, there were only two oddities that advanced users could have spotted. First, the phishing site did not support HTTPS traffic. Advanced users should know that credentials should be sent over secure HTTPS sessions only, and banking sites always redirect to HTTPS enabled pages when the user must log in. The second clue is in the source of the page: the last line, an HTML comment, shows that the page was copied from the original site:
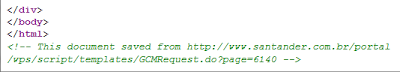 |
| Last few lines of HTML code on the phishing site |
A week later, the phishing site is still up. It is not blocked by Phishtank or Google Safe Browsing. However, the hijacked DNS servers have been cleaned up, making this site a lot less dangerous.
-- Julien




