Mjag dropper
Mjag dropper is compiled in the Microsoft .NET framework, and its original binary is obfuscated using SmartAssembly. The installation path and other details are stored in encrypted form using AES encryption (Fig. 1), and the decryption key is hardcoded.

The payload and decoy PDF is encrypted and stored in the resource section, and a custom encryption method has been used. The decryption key is hardcoded (Fig. 2).

The decoy document claims to be an India Overseas Bank NEFT transaction statement. It lures users to click the “Click here to view full document” link, which points to a malicious website hosting a copy of the Mjag droppper payload. (Fig. 3).

Installation
- Copies itself in “%APPDATA%\FolderN\name.exe” location
- Creates startup key: “HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\Load” with values as “%APPDATA%\FolderN\name.exe.lnk”
- Copies “C:\Windows\Microsoft.NET\Framework\<Version>\msbuild.exe” to “%TMP%\svhost.exe”
- Starts svhost.exe in suspend mode and injects the final payload (Fig. 4)

However, the injected payload does not run properly and displays an error message (Fig. 5).
Fig. 5: Unhandled exception popup
This error is due to the injector code not being able to inject the overlay part of the payload, the part that contains the command-and-control (C&C) server details. As shown in the injection code snapshot below, it allocates memory in a target process similar to the size of image length defined in the PE header of payload (Fig. 6). This means Mjag will not be able to properly inject payloads (like Punisher RAT) that contain important data in the overlay.
Fig. 6: Injector code
For the purpose of this blog we patched the memory mapping issue and continued our analysis of the infection cycle involving Punisher RAT.
Analysis of Punisher RAT
Punisher RAT is packed and written in .NET. The Punisher RAT builder is publicly available and can be configured with a range of features. In the builder (Fig. 7), you can configure the server IP, name, password, and listening port. The RAT will communicate on the given server IP and send all the information stolen from the victim’s machine. There is also a feature to add more functionality in binary, including anti-VMware, anti-AV, sandbox detection, and USB spread for further infection, among others.

During analysis, we saw various functions of this malware, including:
1. Password stealing module
The malware hunts for various application data and steals the credentials. Here (Fig. 8), it is trying to steal the stored login credentials for the Chrome browser. The stolen information will look like:
|URL| http://facebook.com
|USR| username or e-mail
|PWD| userpassword
Fig. 8: Stealing module
The Punisher RAT attempts to steal sensitive data from the following applications on the infected system: Filezilla, No-IP Dynamic Update Client, Dyn DNS, Paltalk, FireFox, Chrome, Hotmail, Yahoo, Opera, and Internet Explorer.
2. Anti-task manager
The malware checks for the following applications’ processes, and does not allow these applications to terminate any other processes running on the user's system.
- Process Explorer
- Process Hacker
- Task Manager
This allows malware author to ensure that the malware processes cannot be terminated. Fig. 9 shows that while attempting to kill 'a.exe' process using the Process Explorer, the “OK” button will be replaced by an “Error” button.

3. Keylogging
The malware can capture keystrokes (Fig. 10) and store the data into the %AppData%/{random digits}.log file.

4. Persistence
The malware copies itself in the startup folder and creates a run key of this location.
HKCU\\software\\microsoft\\windows\\currentversion\\run
5. Spreading vector
It looks for a removable drive and CD-ROM for infection and creates an .lnk file.
Below (Fig. 11) depicts the spreading mechanism through a USB device.
Fig. 11: USB spread
6. AV checks
The Punisher RAT checks for installed AV software (Fig. 12) and updates to the server.

Network activity
The hardcoded C&C information (Fig. 12) is extracted from the payload, and it will split the data with the delimiter “abccba.”

It also collects the information about the multiple running processes:
AW|BawaneH|Process Explorernj-q8
AW|BawaneH|Notepadnj-q8
The table consists of extracted C&C information from the payload.
This RAT uses “BawaneH” as a delimiter to split the server response data. It performs various actions based on received commands. There were a total of 59 commands used by the server, shown in the following table:
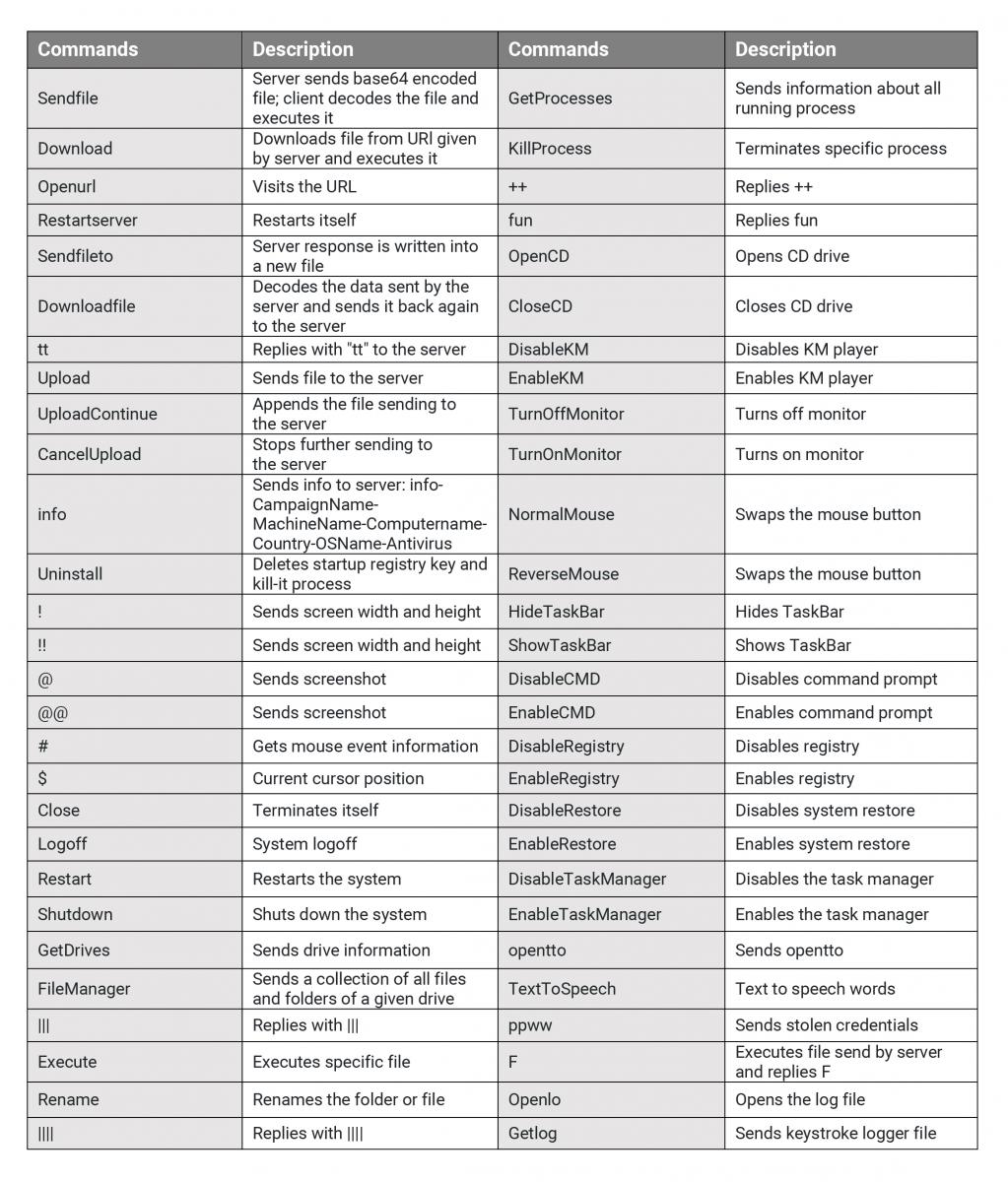
Fig.14: Received commands
IOCs
Md5: 0a459c18e3b8bdef87a6fb7ea860acdb
Filename: NEFTIOBAN1830369427520181030ABBIdiaLtddt30102018_pdf.exe
Download URL: tenau[.]pw/owa/neftioban1830369427520181030abbidialtddt30102018_pdf.exe
C&C: chris101.ddns.net
Sandbox Report
Fig. 15: Zscaler Sandbox report










