March Madness is in full swing and the Sweet 16 games are upon us! While enthusiasts everywhere prepare to stream their favorite teams' games, the increased interest in the tournament has also attracted the attention of threat actors who've produced a variety of ways to trick fans into downloading malicious code. Zscaler researchers have observed multiple threats, and we hope the information outlined here can help some fans avoid becoming victims.
Through the first round of the tournament, Zscaler saw increased activity from users streaming games and checking their brackets for updates as shown in Figure 1. We saw the traffic in this category increase by 100% during the game week. We also observed an increase in malicious activity related to the sports category. As shown in Figure 2, there was a clear upward spike in malicious activity over the last 15 days, such as phishing pages, adware downloads, improper handling of user data, and attempts at domain squatting.
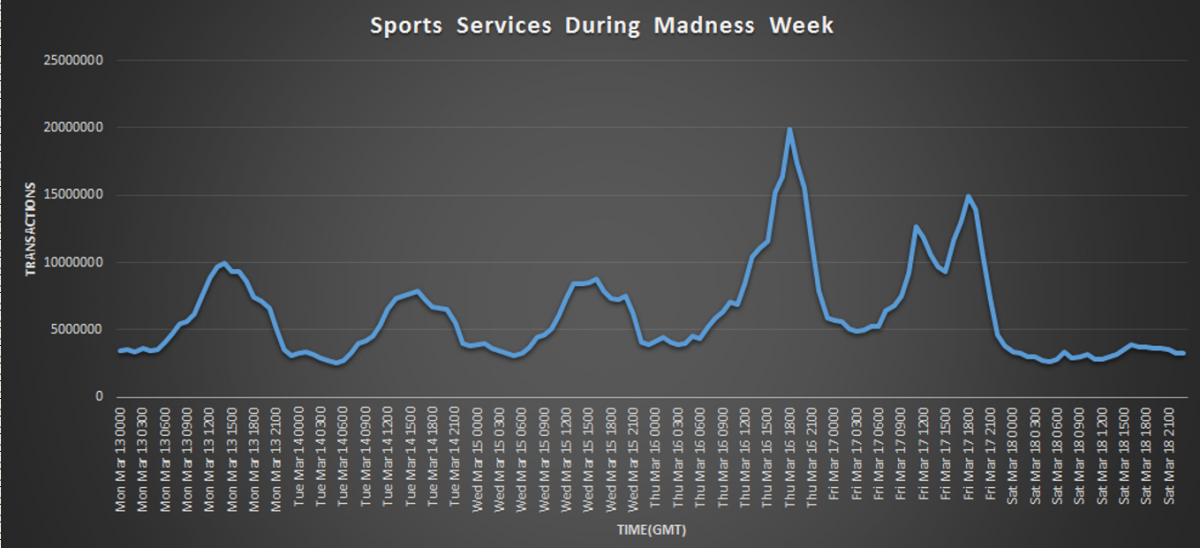
Figure 1. Total traffic in sports category, 13 March 2017 to 18 March 2017
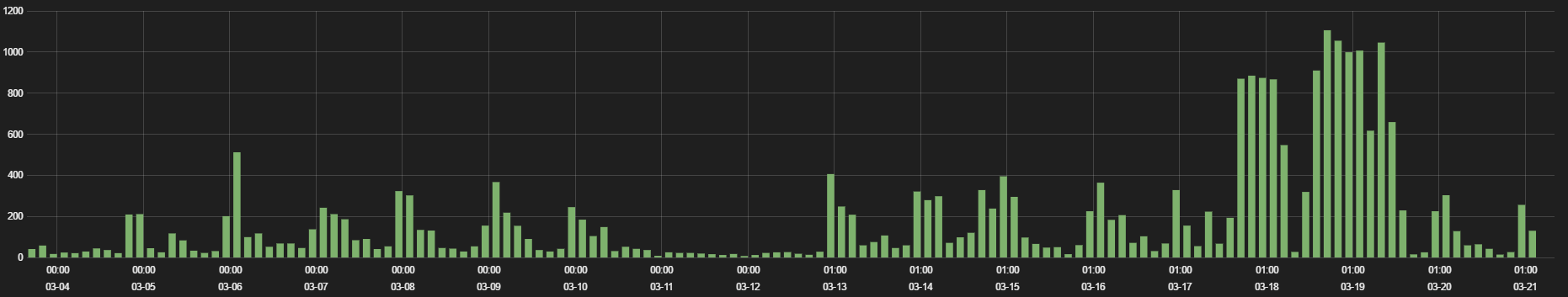
Figure 2. Malicious activity blocked for web activity in the sports category , 4 March 2017 to 21 March 2017
We checked our data to monitor for attacks that might affect users through March Madness. The best advice we can offer is to be sure to use NCAA-sanctioned bracket applications through your web browser. There are many third-party sites out there that attempt to probe the user to create login credentials. In the example below, we observed that one such application collects a username and password and then transmits it in the clear. This plain text credential transfer makes the connection vulnerable to sniffing attacks. Since users commonly set the same login credentials for multiple websites, the attackers might gain access to users email accounts, bank accounts, tax preparation accounts etc.
website: bracketintel[.]net
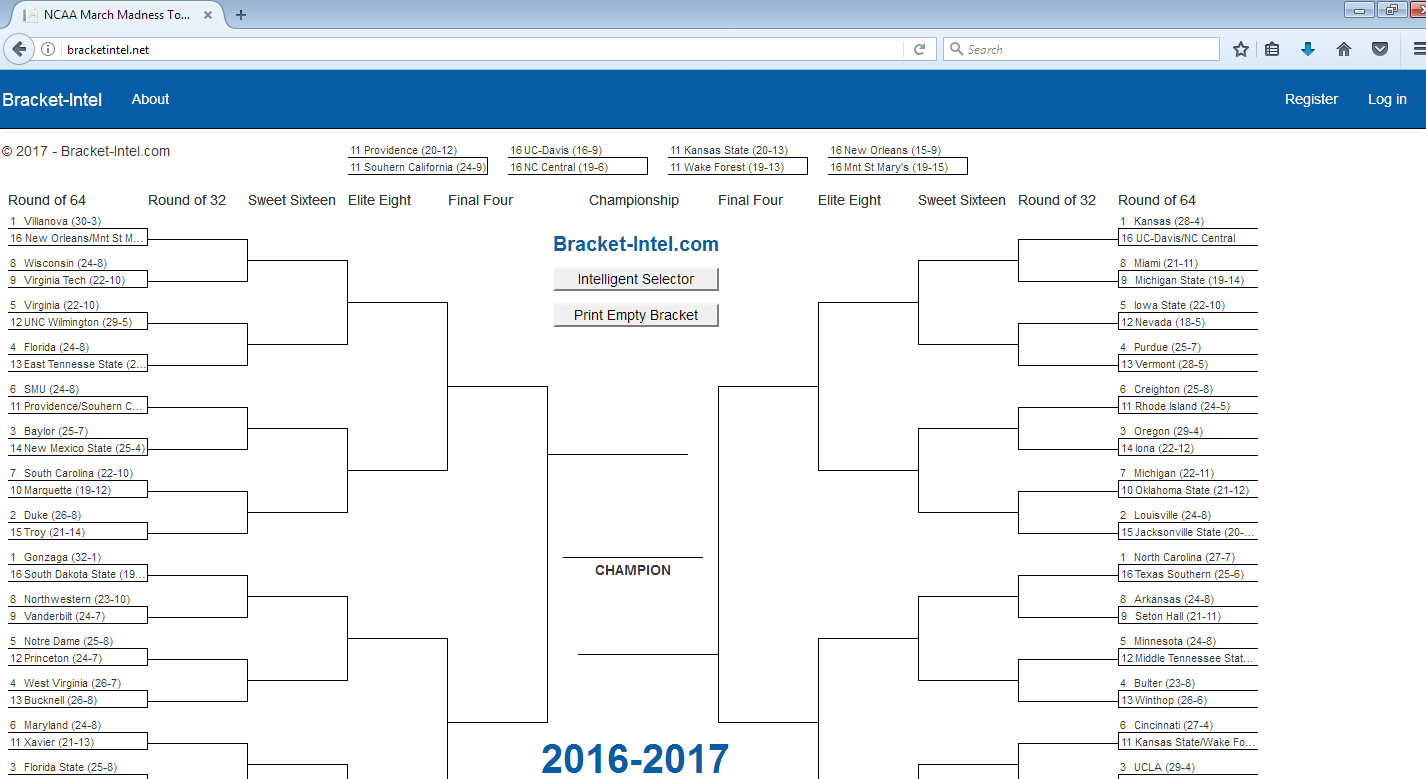
Figure 3. Generic bracket filling page.
When we tried to register for an account we saw the Register page on bracketintel[.]net as shown below.
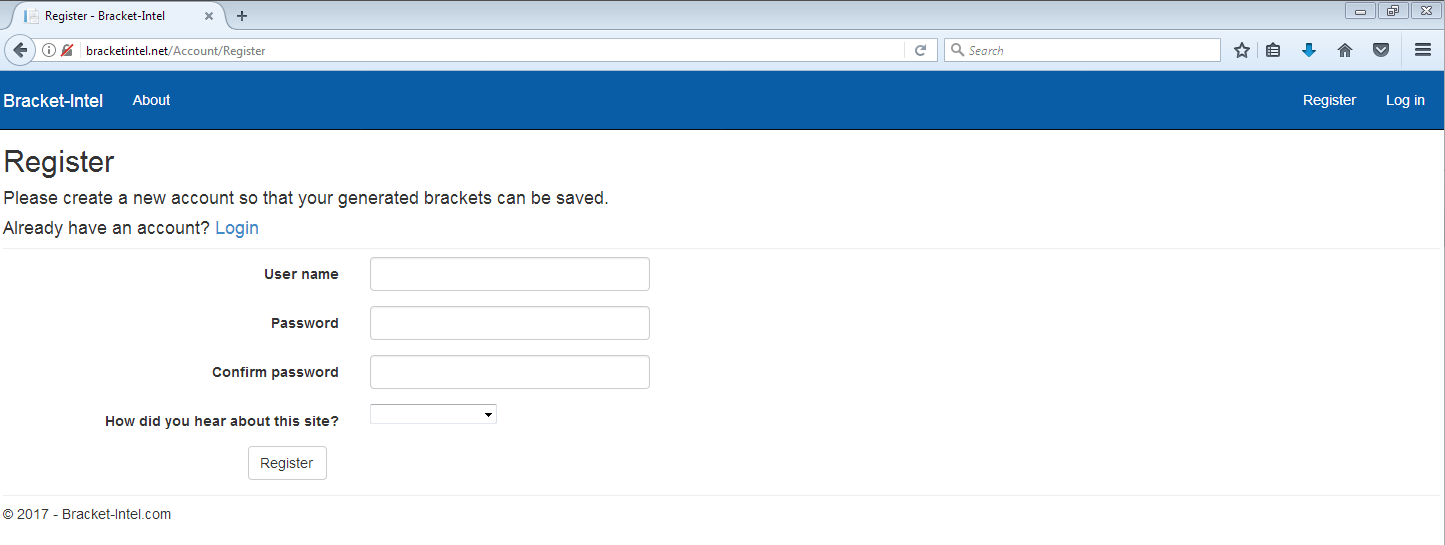
Figure 4. Registration page on bracket filling website.
Packet capture shows the registration process taking place in clear text,
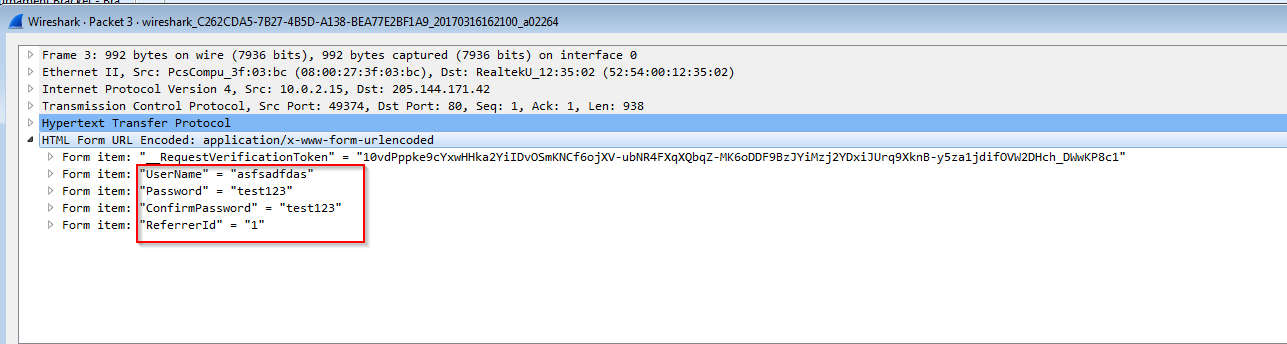
Figure 5. Plain text credential seen on packet capture.
If fans are looking to stream the NCAA tournament for free, they can easily find the games at www.ncaa.com. However, a simple Google search of the phrase “NCAA free streaming” yields some dubious results including this one from ifirstrowus[.]eu which comes up as the fifth hit on the search page. Basketball enthusiasts that click through this site to watch the games will be sorely disappointed. Instead of watching their alma mater, they will be redirected to a site that installs a browser hijacker, which prompts users to install toolbars and change the homepage to search.searchliveson[.]com to continue watching the game.
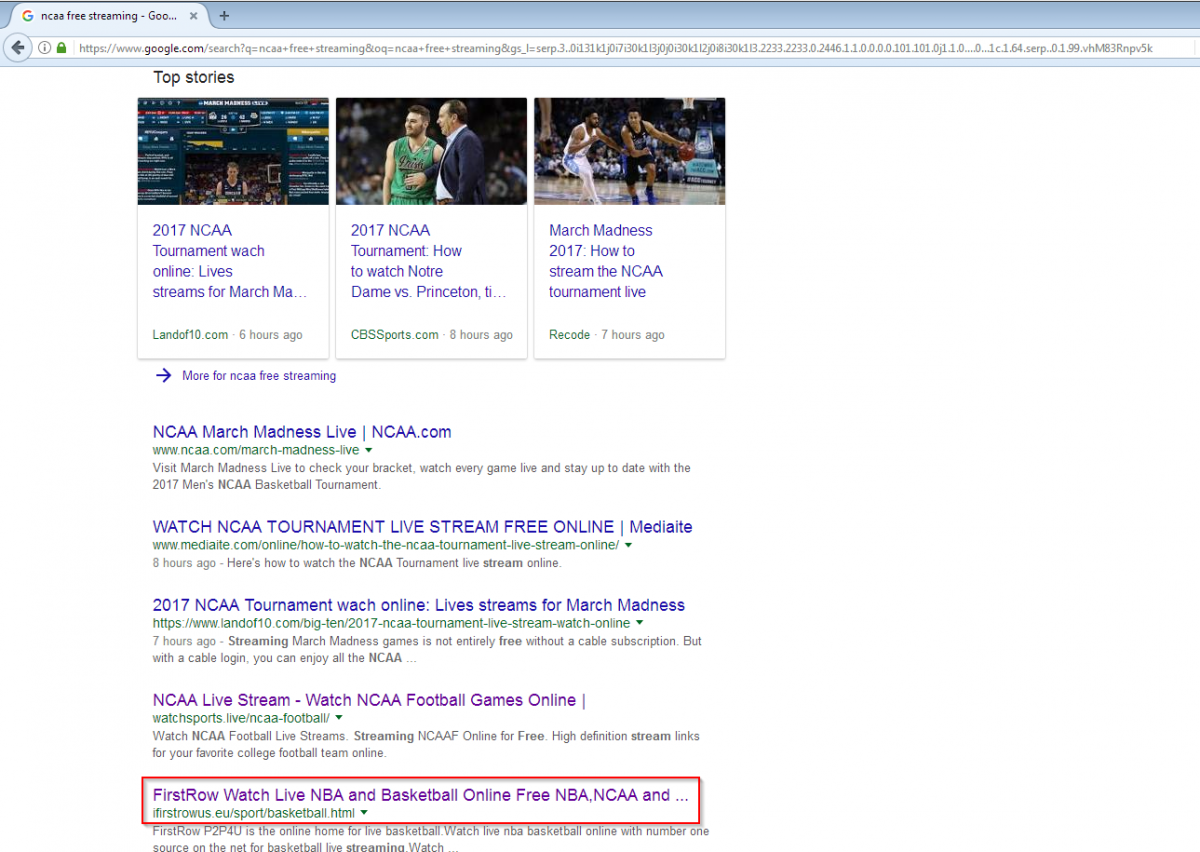
Figure 6. Google search results for "NCAA free streaming"
Clicking the streaming link takes users to websites using social engineering techniques to prompt them to click on advertisements on the page which say content cannot be played.
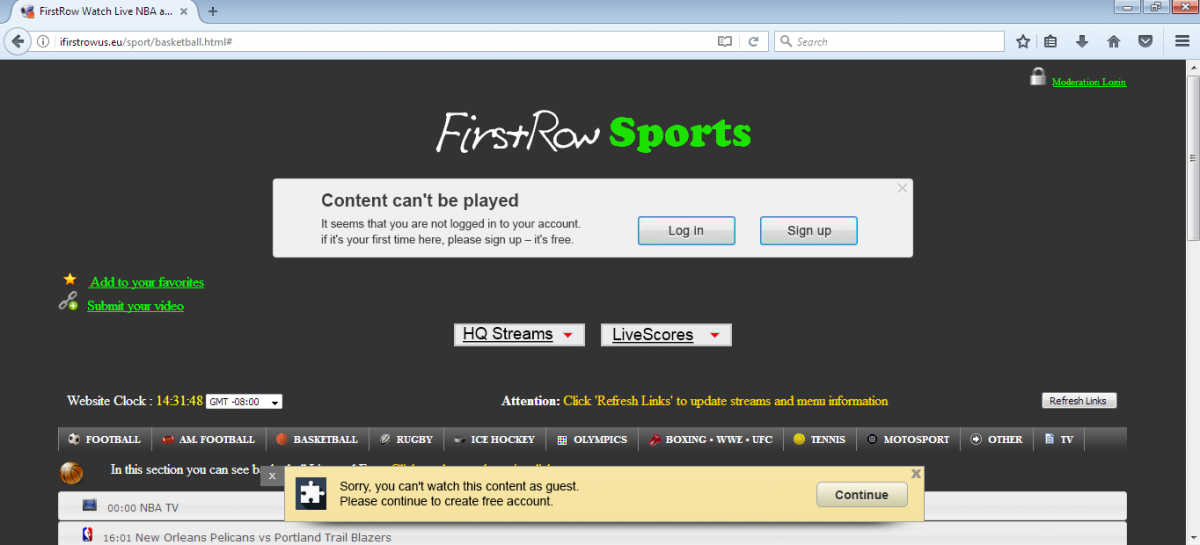
Figure 6. Free streaming website.
Clicking on the advertisements serves up a webpage prompting users to download adware.
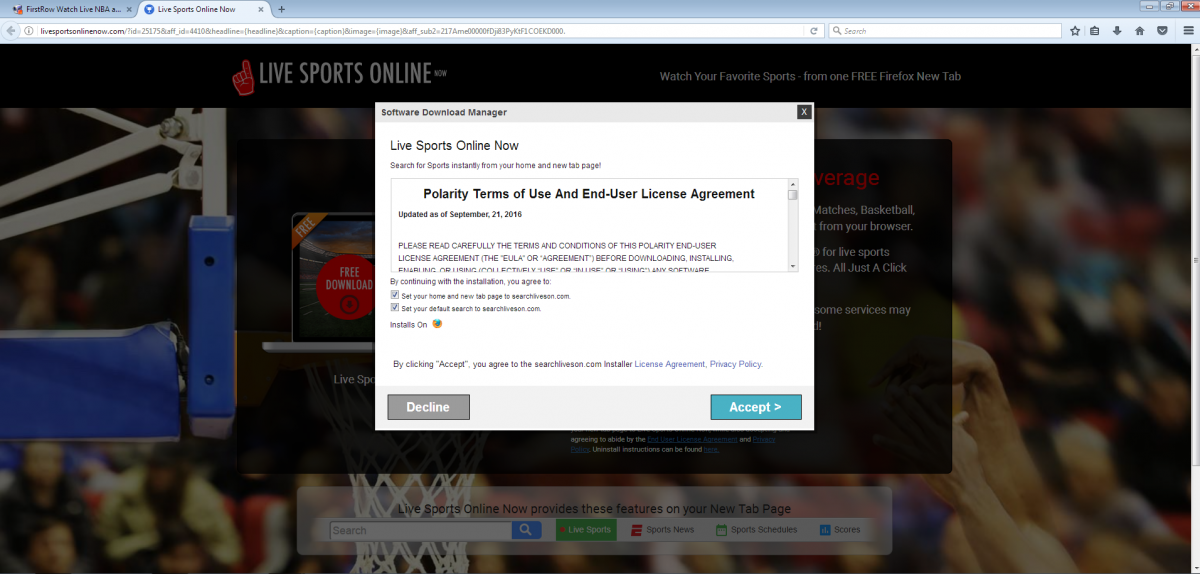
Figure 7. Redirected page prompting for plugin download.
The homepage is changed and a plugin is added to the browser
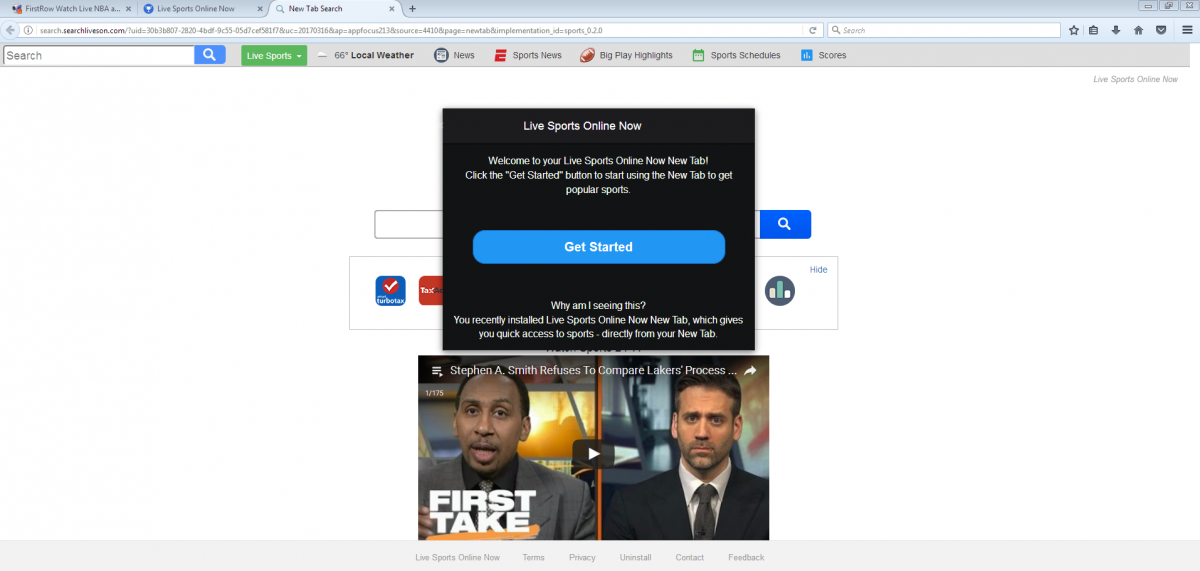
Figure 8. Browser hijacker installed on the user machine
Based on the geographic location of the user, the site also serves a series of suspicious pages that have the same theme but different names as shown below,
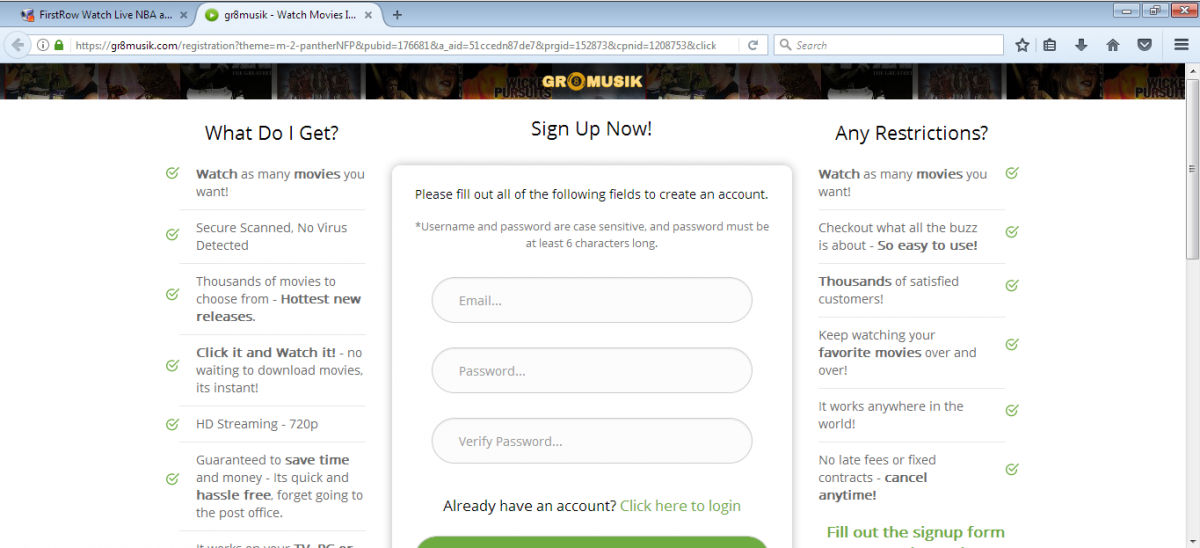
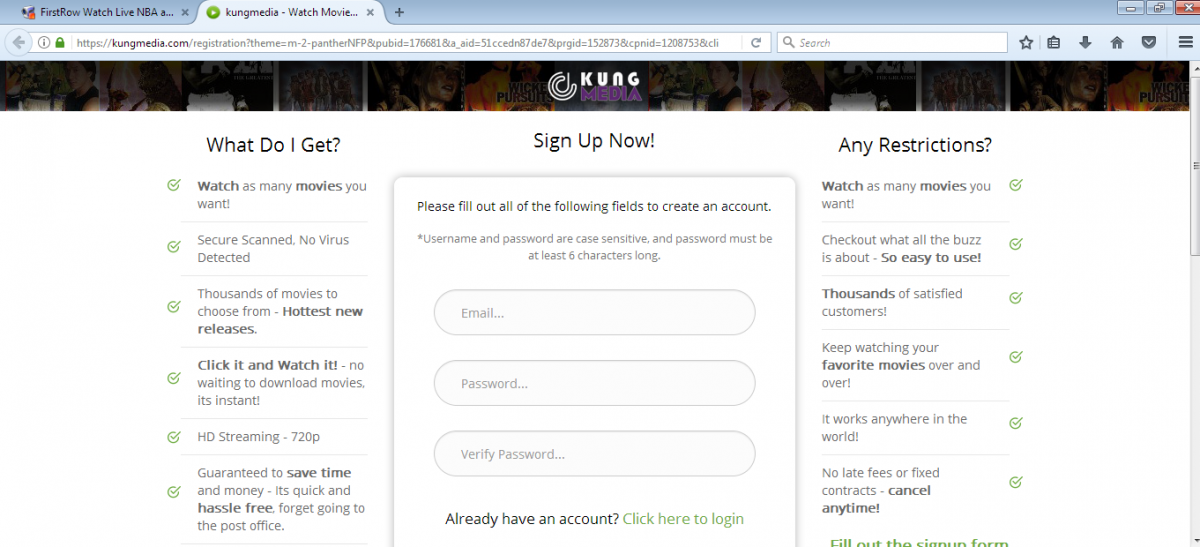
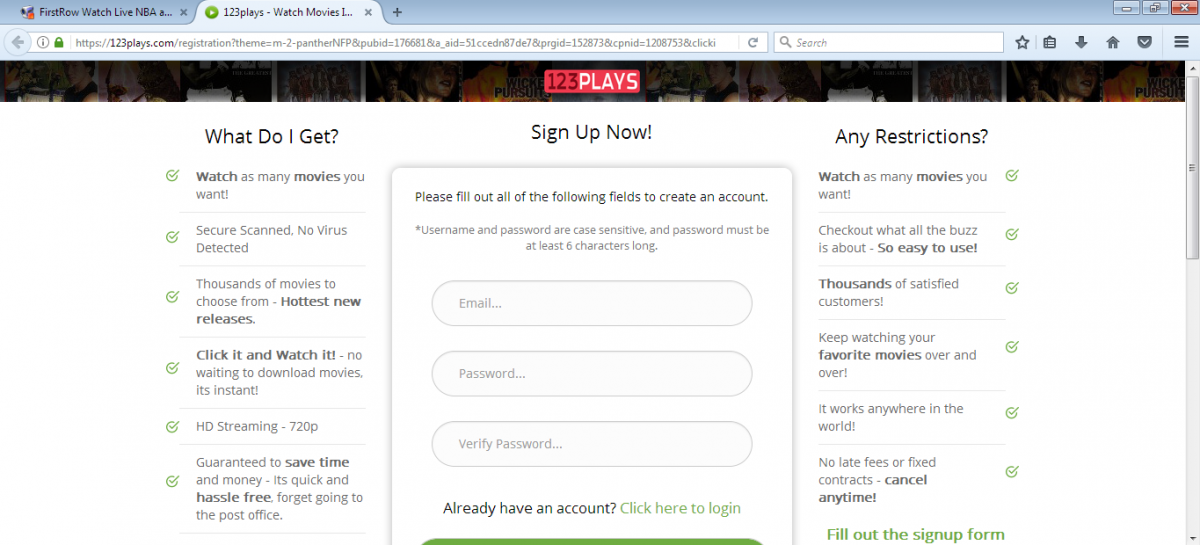
Figure 9. Suspicious websites with same theme but different names.
The browser hijacker itself will modify the user’s homepage and redirect browser searches.
Another example of an adware download instance can be seen below. The streaming website provides a free ESPN streaming service.
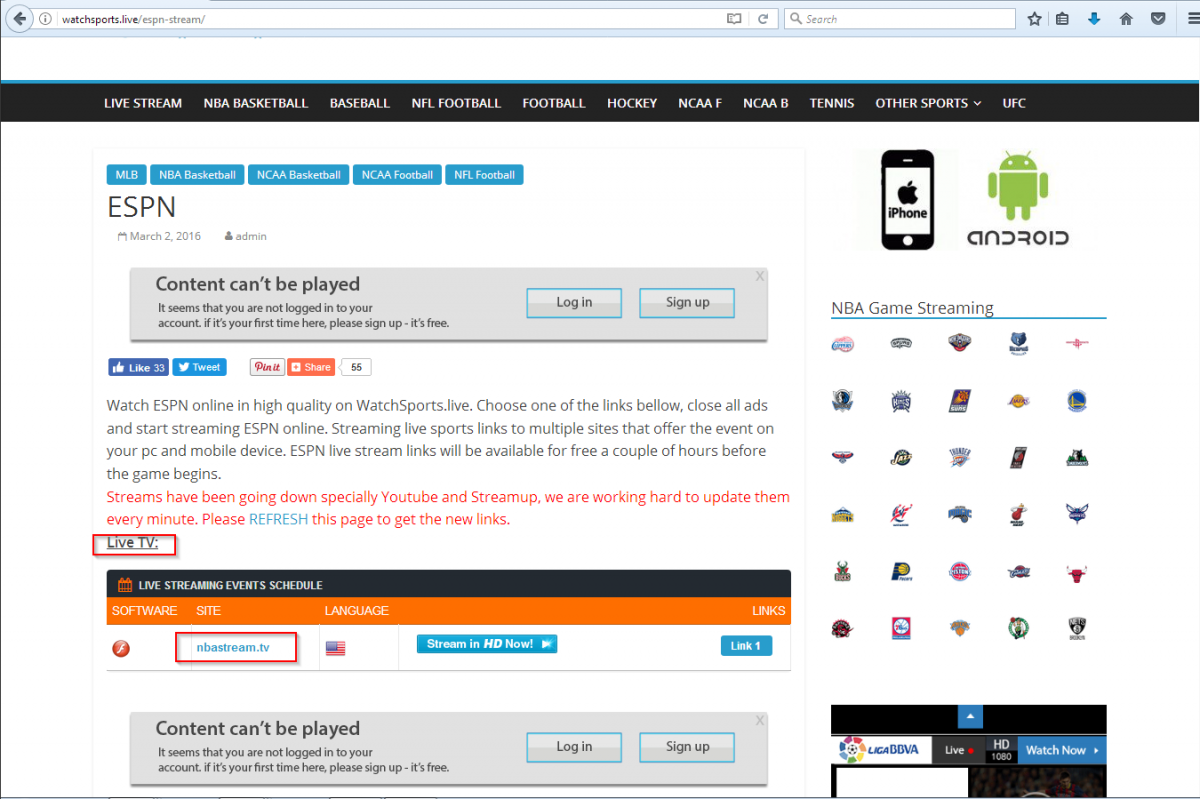
Figure 10. Website providing free streaming acccess to ESPN
Clicking on this stream sends users to the site below which has advertisements and fake "close" buttons.
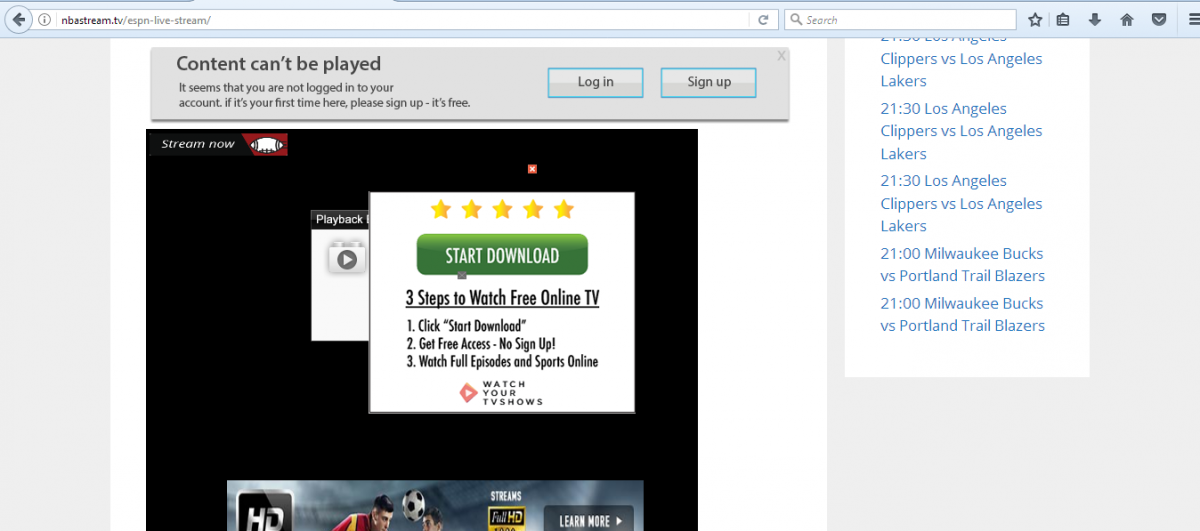
Figure 11. Flash player with ads having fake close buttons.
Attempting to close the advertisements by clicking the fake close buttons prompts a user to download the Potentially Unwanted Program(PUP) known as ReimageRepair.
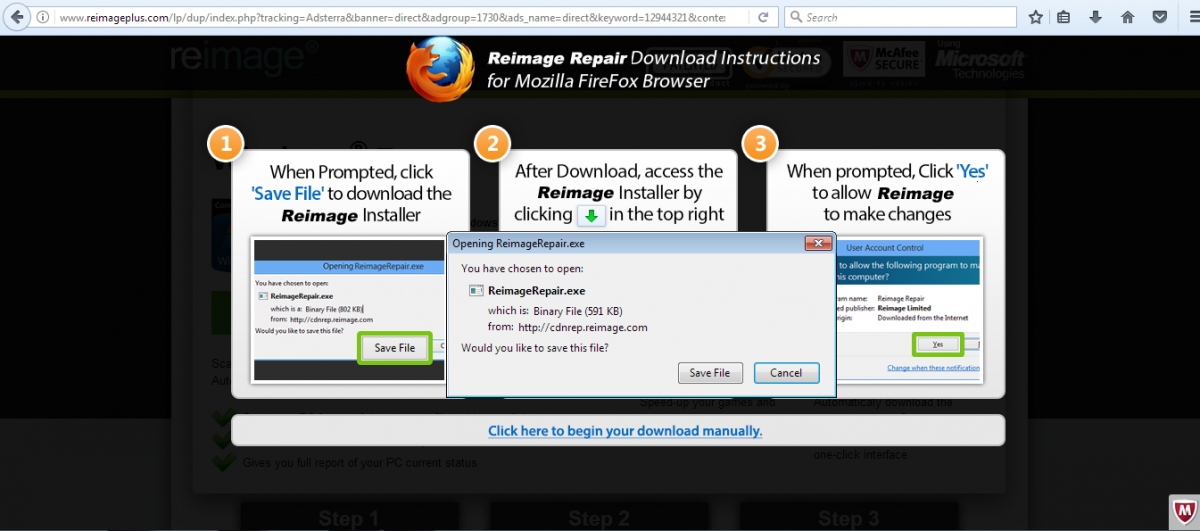
Figure 12. Download of PUP
We also observed domain squatting attempts for known websites in the sports category, a few of those domains include:
www[.]cbssports[.]comespn[.]com
www[.]cbssport[.]com
www[.] cespn[.]com
www[.]1010espn[.]com
www[.]foxsportla[.]com
Domain squatted addresses can be used to host phishing webpages which look like genuine websites but steal user credentials and other information. They can also be used as mail server domains to send out spam emails.
Conclusion
All these examples should highlight the diversity of threats that attempt to exploit the popularity of March Madness. We encourage readers to exercise caution when doing searches or clicking on links related to March Madness. Zscaler ThreatLabZ continuously monitors online activity worldwide to ensure that Zscaler customers are protected from threats, even if they become tricked into clicking a nefarious link.
Researched by Chris Mannon and Rohit Hegde




