In Zscaler’s daily scanning for mobile malware, we came across a sample of Android Mouabad.p. Lets see what is inside.
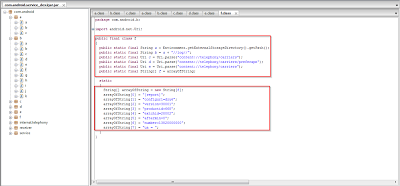
Application static info:
Package name = com.android.service
Version name = 1.00.11
SDK version: 7
Size: 40 kb
Permissions:
- android.permission.INTERNET
- android.permission.ACCESS_NETWORK_STATE
- android.permission.READ_PHONE_STATE
- android.permission.SET_WALLPAPER
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.MOUNT_UNMOUNT_FILESYSTEMS
- android.permission.RECEIVE_SMS
- android.permission.SEND_SMS
- android.permission.RECEIVE_WAP_PUSH
- android.permission.READ_PHONE_STATE
- android.permission.WRITE_APN_SETTINGS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.WAKE_LOCK
- android.permission.DEVICE_POWER
- android.permission.SEND_SMS
- android.permission.WRITE_APN_SETTINGS
- android.permission.CHANGE_NETWORK_STATE
- android.permission.READ_SMS
- android.permission.READ_CONTACTS
- android.permission.WRITE_CONTACTS
- android.permission.CALL_PHONE
- android.permission.INTERNE
- android.permission.MODIFY_PHONE_STATE
Used features:
- android.hardware.telephony
- android.hardware.touchscreen
Services:
- com.android.service.MessagingService
- com.android.service.ListenService
Receivers:
- com.android.receiver.PlugScreenRecevier
- com.android.receiver.PlugLockRecevier
- com.android.receiver.BootReceiver
- com.android.receiver.ScreenReceiver
Virustotal scan:
Now Lets dissect the code.
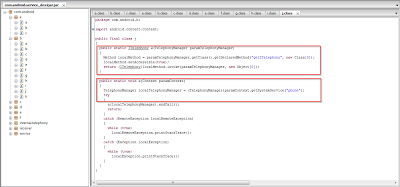
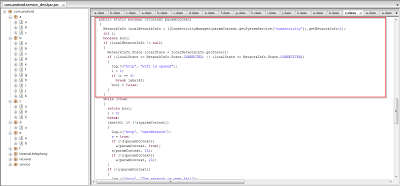
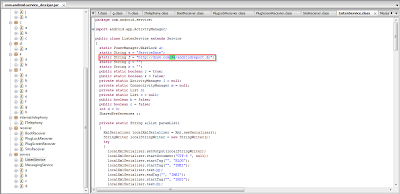
This application is using telephony services as shown in the code as well as in static analysis. You can see the use of premium telephone numbers.
In this particular screenshot, you can see functions which are using phone services for making calls to the premium numbers in order to generate revenue as the numbers would be controlled by the attackers and earn a small payment for each call made.
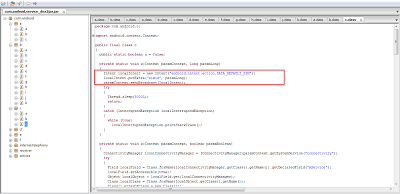
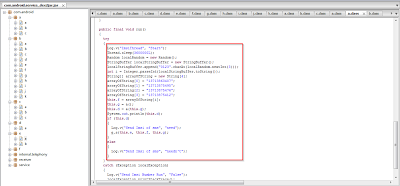
Here you can see that the application is harvesting SIM card information.
This application also checks for mobile data and the WIFI network status to determine if Internet connectivity is available.
The code includes a hardcoded list of premium telephone numbers, which are all located in China.
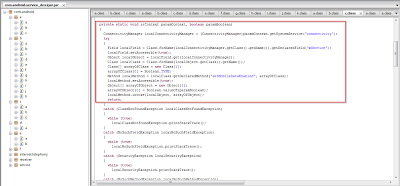
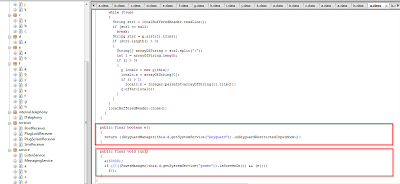
In this screenshot you can clearly see that application also keeps watch on the screen and keyguard status (on/off).
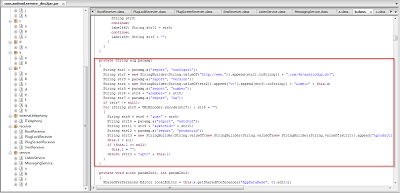
This screenshot clearly denotes that the application tries to send SMS to the premium rate numbers previously seen in the code. Forcing Android applications to initiate calls to premium phone numbers controlled by the attackers is a common revenue generation scheme that we see, particularly in Android application distributed in third party Android app stores.
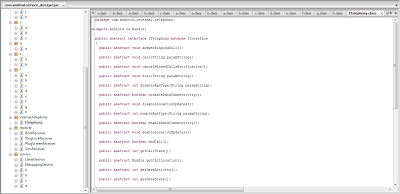
Here you can see various function names which are suspicious such as call, dial, disableDataConnectivity, get call location, etc. These functions suggest that the application is also trying to keep watch on other phone calls too. Function getCallstate, endCall, Call, CancleMissedCallNotification Illustrates that the application tries to control phone call services.
The application installs itself silently. Once installed, no icon is observed for this app. Also shown in the previous screenshot is the fact that the application waits for the screen and keyguard events before triggering its malicious activity. It does all of the activity without user intervention. This allows the malware to function without a suspicious icon on the home screen that just one of technique used by malware authors to evade its presence to the device owner.
From above screenshots, you can see that the application is using the XML listener service. Also, in the second screenshot, you can see that the application is trying to create a URL by assembling various strings. This is likely command and control (C&C) communication sent to a master server. The parameter &imei denotes the harvesting of the phone's IMEI number for tracking the device.
In conclusion, this malware will defraud the victim by silently forcing the phone to initiate premium rate SMS billing to generate revenue. The application may give control to the author for monitoring or controlling phone calls.