In the modern healthcare landscape, the ability to securely access critical applications from remote locations is crucial for doctors and other healthcare professionals. With the rise of telemedicine and remote work post-COVID, ensuring a seamless and secure connection to clinical applications has become a top priority.
Sure, you could do the traditional VPN solution. You know how it goes: you set up a dedicated VPN network appliance, you point it internally to your network, usually in the DMZ. Then your users can connect to whatever app they need. The problem with that is now they can move wherever in that network they want as well. You just gave a potential malicious actor the keys to the kingdom. You’re probably thinking, “oh, that user can’t connect to Active Directory because of permissions.” That doesn’t mean they can’t try to brute force it or plant a MitM attack to sniff those credentials. Any information about your network accessible to a bad actor is too much.
The other thing is the history of VPN appliance vulnerabilities. In 2020, there were 28 CVEs in total around VPN vulnerabilities as read here at Institute of Physics. Though we are in 2023 now, that does not mean these systems still aren't being compromised.
Two articles highlighting these vulnerabilities are:
Fortinet fixes critical RCE flaw in Fortigate SSL-VPN devices, patch now
Zyxel warns of critical vulnerabilities in firewall and VPN devices
This means cycles to patch or hardware upgrades to fix these vulnerabilities which both cost money.
I know you have heard that message time and time again. So, if no VPNs then how about VDI? Sure, you can do VDI as I was a VDI admin and deployment specialist for many years. The challenge with VDI is that unless you do underlying microsegmentation, you are still giving lateral movement to someone. You also have to keep that hardware up to date and refreshed to ensure the best performance possible.
VDI is also not immune to compromise as we saw with Log4j, those external attack surfaces are just another hole in the firewall that bad actors will try to exploit as demonstrated in the following articles:
Why VMware Horizon became a ‘top choice’ for Log4j attacks
Citrix urges admins to patch critical ADC, Gateway auth bypass.
These are not new attack surfaces, but because of our reliance on these technologies we have had no choice. We are also seeing traditional EUC vendors being bought by private equity companies, then raising prices that are unaffordable for the healthcare market. So how do you give clinicians flexibility, save costs, and provide a seamless experience?
Let's talk about a new way of giving users access to their critical apps like EMR/EHRs. What if I told you that you could give someone access to their app from any device and also ensure they only would be able to access that app, and nothing more? No, this isn't a scene our of The Matrix. You don't need to pick between the red or blue pill. You can actually have both. Let's talk about how Zscaler Private Access (ZPA) gets you that ability to connect your users to the apps they need - nothing more, nothing less. We'll break this up into a few themes: how hard is it to set up, the benefits to your clinicians, and the ease of administration.
Easy setup process
Setting up secure remote access to clinical app systems can be a complex and time-consuming task. You need to deploy the VPN client usually or a VDI infrastructure, put all the firewall rules in place, ensure device redirection works, etc. However, Zscaler Private Access simplifies this process, making it quick and straightforward. You just need two components: a Zscaler Client Connector which is our lightweight tamper-resistant client. So if you are already using Zscaler Internet Access (ZIA) or Zscaler Digital Experience (ZDX), then this is just a toggle in your admin portal to enable ZPA. You don't need 10 different agents for remote access, just a simple client software. From here, you can use our browser-based access vs. a client to avoid installs on devices you don't manage.
By deploying the ZPA App Connector, a lightweight VM, healthcare organizations can establish secure connections between authorized users and the clinical app systems without the need for traditional VPNs or complex network configurations. As a result, healthcare IT teams can streamline the setup process, saving time and resources, while ensuring secure and efficient access to their systems. No more hardware appliances to worry about patching and updating. We can get rid of some of those very expensive MPLS circuits by being able to hook back into the main data center from a branch hospital as well. If you are worried about all of your printers or IoT devices, we support those as well. They often can't install Zscaler Client Connector on them, but by utilizing Zscaler Branch Connector we can provide the same level of security and access that our traditional Zscaler client gives. This App Connector makes outbound connections to our Zscaler Zero Trust Exchange which then the cloud talks back to your end user’s client. Below is an example configuration of OpenEMR running in a home lab:
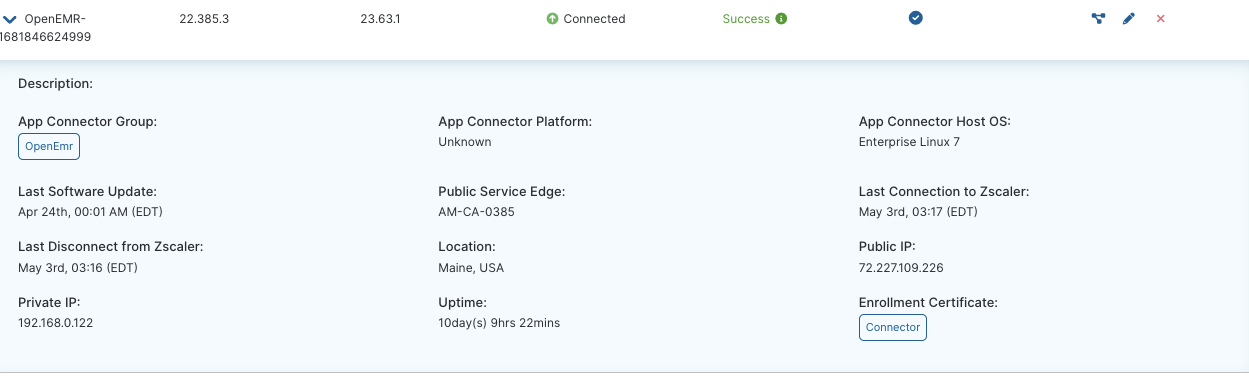
We also integrate with your SAML provider so authentication is a breeze. Just plug in your SAML provider information and with SCIM we will pull in all the necessary users so you can assign them policy. This makes setup even faster if you are using something like an Azure Active Directory or Okta already.
This configuration took five minutes from the start of the download to finishing the configuration. I can now have my users access their applications from anywhere that I deem appropriate using posture checks such as:
- Are you on a trusted network or a non-trusted network?
- Do you have antivirus?
- Are you allowed access to this application?
You might be thinking this sounds like a VPN. Sure, I could see how someone may think that but I assure you it is not your standard VPN. As we discussed, a VPN allows me to move laterally, and this prevents me from going anywhere but that application. If you allow RDP through ZPA they may still be able to move laterally, but you can always lock that access down through traditional segmentation or even the Zscaler client on top of that RDP machine.
The benefits for remote clinicians
With ZPA in place, doctors and nurses can securely access their critical apps from any location, using any device with an internet connection. Whether they are at home, on the go, or in a remote clinic, doctors can review patient records, update treatment plans, and securely communicate with other healthcare providers. The best part is this doesn’t disrupt your doctors’ and nurses’ workflows. They may never even see the client show up as we can auto-enroll and auto sign in on boot. They just go about their job as it was.
I recently showed someone how I can even access my EMR now via my phone with no Wi-Fi access, just 4G with only the Zscaler Client Connector installed on my Android Device.
One of the other benefits to your users is the ability to reset passwords, getting new group policies, and joining domains—things you traditionally would need to be on the network or have a way to push out via an internet-facing website. We can actually bring your machine onto the network before you ever log into Zscaler Client Connector.
We had a customer recently who had a large remote workforce and they needed to change domains on all of their machines. They could have them fly into HQ and spend a large amount of money on expenses all for a five minute changeover but with ZPA we were able to do that all remotely. We saved them a lot of unnecessary expenses by using this functionality of our platform. This means your doctors don’t need to drive from a rural area into the office just to do simple tasks or access network shares. Again, we do this securely via those TLS tunnels from our App Connectors, to the cloud, and to the endpoint.
Ease of administration
We talked about the ease of setup and the benefits to your end users but what about administration? IT administrators can easily define and enforce access policies based on user roles, ensuring that only authorized individuals can access sensitive patient data. The Linux appliance software can be kept up to date through the portal and you can easily patch the Linux OS through normal patch management systems or use the OVA for even easier patch cycles.
The number one thing I also get asked about is, “how do I know what my users are using, because my IT staff do not have time to chase everyone around to figure that out?” I remember dealing with this when I was a customer rolling out a virtual microsegmentation product. My App owners could not tell me what ports or protocols they needed, or even who needed access most of the time.
When we work with a customer, we set up what we call a discovery segment that acts more like a traditional VPN for a brief period of time. It still gains the same security benefits from Zscaler, but it isn’t true segmentation, yet. We can then see what users are going and start to logically and dynamically wrap policy around these apps to create segments. Our software will recommend things to you based on what it sees, such as if you have EMR1.acme, EMR2.acme, and EMR3.acme we can tell you that those may belong in a single app segment. This makes the discovery and policy creation process much easier, allowing you to do more with less.
We also discussed a bit about MPLS during the setup process. Hospitals often get stuck having to have MPLS circuits to every network hospital or every data center to provide application access. The challenge with that is those circuits cost money and often are pretty pricey. We saw this need for healthcare customers and believe we can solve this with the ZPA platform. You don’t need a circuit when using ZPA because it treats your users as if they were on the network. Again saving you cost and time which is very important in today’s age of negative margins for some providers. Branch Connector, as mentioned previously, also allows IoT devices to talk back to the data center so things like printers can be on your centralized print server instead of needing to use local printing methods.
These are just some of the benefits you can achieve by leveraging ZPA. It doesn’t stop or start at clinical apps either. We can do this for a wide variety of applications in your private data center or public cloud. You don’t need a full VDI desktop anymore to get tasks done remotely or a traditional VPN appliance. You just need our Zero Trust Exchange and a small appliance on prem or in the cloud. We can then tie in ZPA with our other products, such as ZIA, for all of your internet-facing traffic or ZDX to monitor the digital experience of your employees.
This blog is the third in our series on securing healthcare with a zero trust architecture to do more with less. Read the other blog here:
Empowering your healthcare organization to do more with less: Zero Trust Architecture
Zscaler Internet Access: Securing Your Hospital and Staff
We look forward to exploring how Zscaler can help you do more with less, as we have for hundreds of other customers in the healthcare sector. You can also find more information on Zscaler for healthcare here.




