Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Outsmart Evasive HTML Smuggling Attacks
HTML smuggling is a highly evasive malware delivery technique that exploits legitimate HTML5 and JavaScript features to evade detection and deploy remote access trojans (RATs), banking malware and other malicious payloads. HTML smuggling bypasses traditional security controls like web proxy, email gateway, and legacy sandbox. These attacks are difficult to stop and are just one of many inventive ways in which threat actors compromise organizations daily.
The Zscaler Zero Trust Exchange protects against these attacks with natively integrated prevention capabilities for zero-day protection.
The Blueprint of HTML Smuggling
Attackers are able to hide malicious HTML smuggling activity within seemingly harmless web traffic, making it difficult for legacy security tools to detect and block the attack.
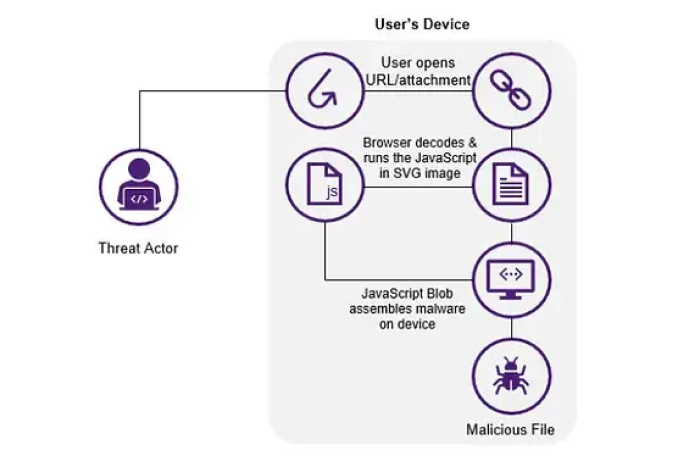
Source: emcrc.co.uk
Most modern advanced prevention layers do not protect against HTML smuggling attacks as those look for malware or files being transacted between the end user’s browser and the webpage. When a user accesses a web page intended to deliver an HTML smuggling attack, the content exchanged between the user’s browser and the webpage is an immutable blob containing binary data and JavaScript, not as a file. The JavaScript is executed on the user’s browser, and using the binary data in the immutable blob, the malicious file is constructed on the end user’s computer. As there is no file transferred over the wire, the attack goes unnoticed by the legacy sandbox and anti-malware engines.
Zscaler Approach: Power of Platform
As attackers continue to innovate with new and sophisticated threat vectors, organizations need to put in dynamic, integrated, layered security controls to stop threats that have never been seen before. The Zscaler Zero Trust Exchange has been built with this goal in mind, providing defense in depth against new and evasive techniques, including HTML smuggling, patient-zero malware, and more.
Zscaler products such as AI-powered Browser Isolation, natively integrated with AI-powered Sandboxing and Advanced Threat Protection (ATP), thwart such attacks comprehensively.
AI-powered Browser Isolation
Browser Isolation stops web-based threats in their tracks. It isolates suspicious web pages in the Zero Trust Exchange and streams only the real-time, safe pixels of the sessions to the end user and not the active content. This keeps threats from reaching endpoints, thereby disrupting the kill chain of modern-day browser exploits. It creates an air gap between users and the web while keeping the user experience intact.
Risky internet destinations, whether accessed directly or via email URLs, can be configured via policy to be fired up within Browser Isolation. AI-powered Smart Isolation enablement can accomplish that automatically. Thus, any malicious payload delivered via HTML smuggling from these risky destinations is restricted to the ephemeral container in the Zero Trust Exchange itself, thus protecting the endpoints.
Together with AI-powered Sandbox and ATP
For productivity reasons, it may be required that the Browser Isolation profile is configured to allow file downloads to the user’s endpoint. The user may try to download that malware to the endpoint out of curiosity. Even in that scenario, the unique Zscaler architecture with native integration of ATP and AI-powered Sandbox will prevent such malware from being downloaded to the endpoint. This dynamically generated malware could either have known signatures or be a patient-zero. Either way, users will be protected
Known Malware
Here are some examples of signatures (as seen in the Zscaler ThreatLabz Library) leveraged by ATP to block such malware.
HTML.Downloader. SmugX (protected by Anti-Malware engine)
JS.Dropper.GenericSmuggling (protected by Intrusion-Prevention Service)
JS.MalURL.Duri (protected by Intrusion-Prevention Service)
Patient-Zero Malware
AI/ML-driven Zscaler’s Cloud Sandbox can stop unknown threats inline, preventing the patient-zero malware from being downloaded to the endpoint.

Embark on the platform journey!
In a nutshell, attacks like HTML smuggling, no matter how evasive they may be, cannot escape the Zscaler Zero Trust Exchange. That’s the power of the platform! Experience the One True Zero!
Tech Tidbit - The Russian cybercriminal collective Nobelium – the group behind the SolarWinds attacks – is infamous for using HTML smuggling to deliver malware.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



