Zenith Live 2023 was chock full of announcements about new platform features to help our clients address important challenges and use cases. Around every corner were dizzying numbers of improvements to security, connectivity, manageability, and user experience. Cyberthreat protection was a particular hot topic, with innovations covering the full Lockheed Martin kill chain from reconnaissance to actions on objectives.
Among these cyberthreat protection innovations were some important tools to improve analytics and visibility into security incidents:
- Zscaler Traffic Capture: Granular packet capture that allows incident responders and threat researchers to access raw traffic data in forensic activities
- Cybersecurity Insights Dashboard: A SecOps dashboard that provides a unified view (with the ability to click deeper) into all security incidents and overall cybersecurity posture
These innovations, both slated for release in late 2023, will make it even easier for security practitioners to understand and improve their security posture using the Zscaler Zero Trust Exchange. Read on to learn more about these great features.
Traffic Capture
We are excited to announce and introduce a flexible new way for organizations to securely capture network traffic across numerous ZIA policies as well as access it via PCAP files that are tied to transactions and stored securely in the Zscaler cloud.
The Zscaler Internet Access (ZIA) portfolio protects end users from inappropriate or risky internet content with a deep and broad set of capabilities, spanning numerous content inspection engines and defense-in-depth–oriented security layers of protection. For example, the Advanced Threat Protection policy engine is constantly updated with threat intelligence and fortified with threat signatures based on content patterns that future-proof protection against fast-moving threat actors and evolving tactics. Similarly, the URL Filtering and Cloud App Control policies protect users from accessing inappropriate sites and content that may expose your organization to undue risk.
However, in some cases, security practitioners and threat researchers need to access the raw traffic associated with a policy match or security detection to support deeper incident response, detection fidelity improvements, retrospective analysis, and other forensic use cases. With Zscaler Traffic Capture, that raw unencrypted content will be accessible.
Traffic Capture Integrated with Policies
The Zscaler Traffic Capture capability will enable your teams to define granular capture policy decisions across numerous ZIA policies, initially including:
- URL Filtering
- Malware Protection
- Advanced Threat Protection
- Firewall and IPS Control
- File Type Control
Capture decisions will be wired directly into existing policies, allowing you to capture content from any policy decision that results in a Block or Deny. This gives you granular flexibility as to the policies and/or specific rules for which to capture content.
Here is an example of simply enabling Traffic Capture on a URL Filtering rule:

Zscaler administrators will be able to search for transaction logs where content was captured via a new filter:
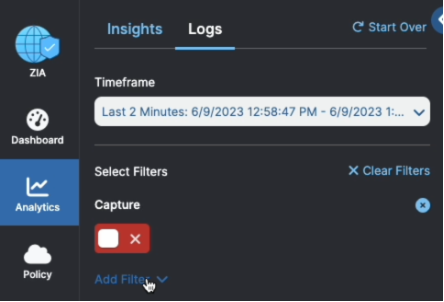
Quickly enabling access directly to the transactions with captured content:
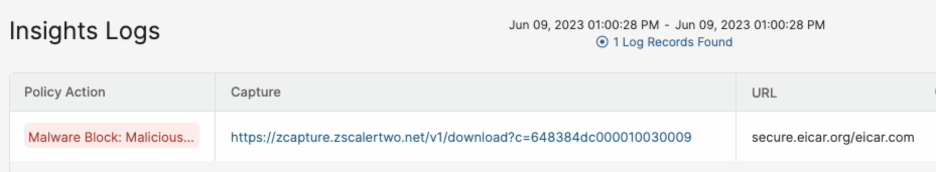
And then downloading and decrypting the PCAP file, opening with Wireshark, showing the raw content:
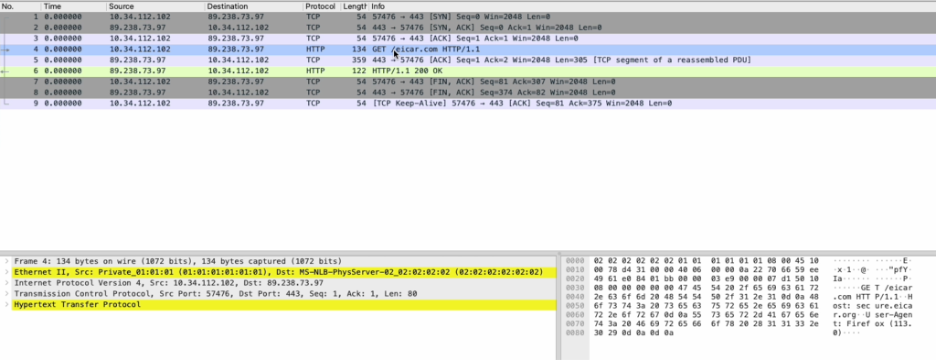
IP, port, and protocol detail is also preserved:
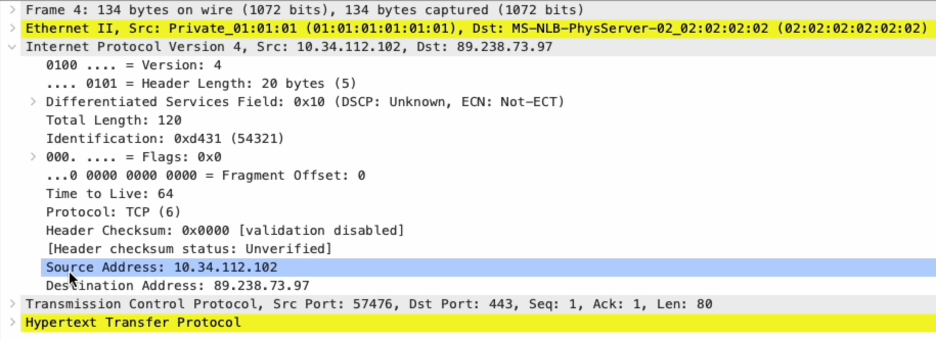
While the captured content would include decrypted content (assuming an HTTPS connection and the SSL inspection policy allowed decryption), content will be encrypted both in motion and at rest. Public encryption keys will be required for encrypting of content, ensuring that only those who possess the matching private key can decrypt the same content.
You will also be able to configure aggregate and per-capture transaction settings:
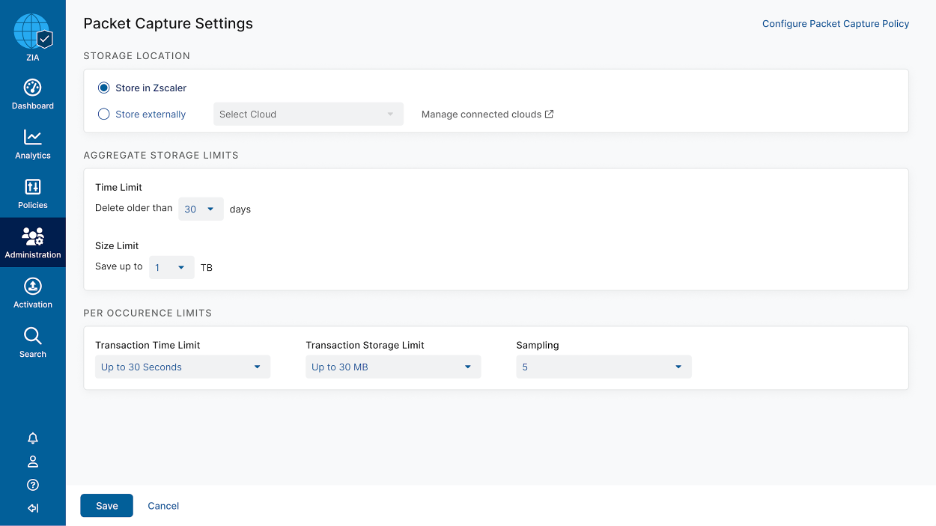
This will allow for flexibility in how much data is captured per policy rule with capture enabled as well as how much is stored and retained, and for how long, in aggregate per customer.
Benefits
Benefits to your organization include:
- Time and cost savings: With Traffic Capture integrated directly into ZIA policies, you will save time and effort associated with alternatives that would require legacy appliance-based solutions to decrypt and capture content for these use cases.
- Infrastructure savings with granular capture criteria: Instead of needing to capture all content (which can result in enormous infrastructure and bandwidth costs) defining capture criteria specifically at the policy or rule allows you to capture only content associated with risky events—as opposed to any/all content, which can be high volume and of little or no security interest (e.g., corporate web conferencing).
- Decrypted data kept secure and private: Recognizing that this capability would enable customers to capture decrypted content, safeguarding the privacy and security of that data is critical. With the integrated, native Zscaler Traffic Capture, only those who have access to transactions via the Zscaler management console and also possess private keys will be able to access said content.
Release and Future Direction
Zscaler Traffic Capture is planned for release in late 2023 for the ZIA policies mentioned above. A separate subscription license will control access.
Future directions of this capability may include:
- Ability to capture content for other Zscaler policies and traffic paths (e.g., ZPA)
- Ability to store the PCAP files in customers’ preferred storage (outside of Zscaler)
- More capture policy flexibility and other integrations
Please reach out to your account teams to learn more and share your use case details with us.
Cybersecurity Insights Dashboard
We are excited to announce and introduce a new Cybersecurity Insights Dashboard, providing a unified view of overall cybersecurity detections; security incidents; impacted locations, users, or assets; threat intelligence; and research. This dashboard consolidates information that was previously found in disparate sources, such as:
- Other dashboards and reports
- Risk report views and alerts
- ThreatLabz blogs and the Threat Library
Cybersecurity Insights not only makes it easy to assess overall cybersecurity posture, but also enables you to double-click into tangible and actionable details.
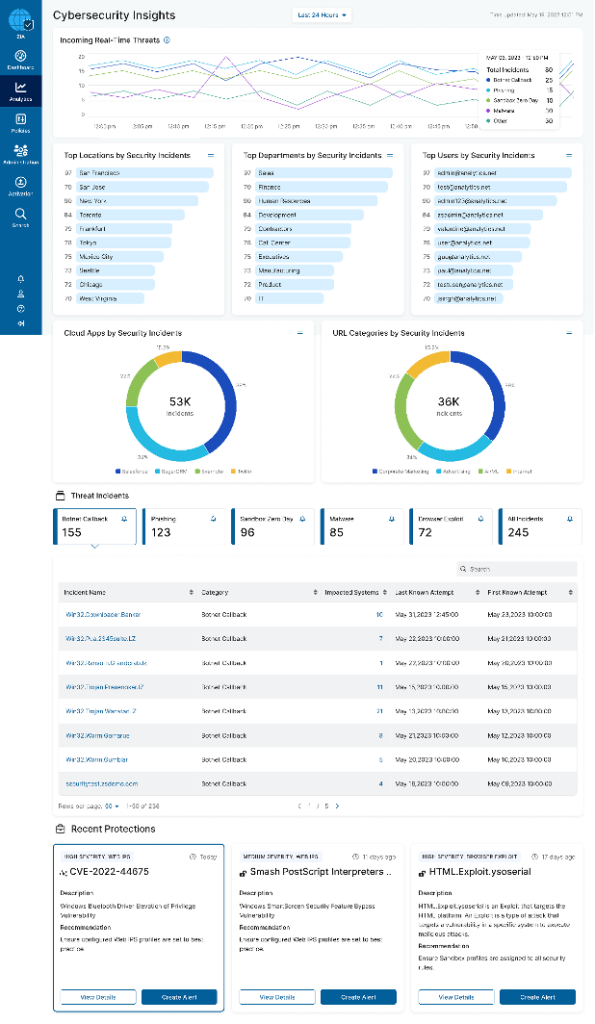
The dashboard contains five key security incident data visualizations, from top to bottom:
- A time-view of threats by category, highlighting trends and deviations easily and quickly.
- At-risk locations, departments, and users by security incident count. This can be a great indicator of locations or user groups that may be at greater risk because they are associated with more targeted attacks, lack in sufficient security awareness training, etc.
- Security incidents by cloud app and URL category, which can give a sense of higher risk cloud apps and URL categories that may warrant limited or “Caution” interrupts before allowing end users to access.
- Threat incident details that break down recent incidents in each of the Malware and Advanced Threat categories, with a convenient clickable link to get to the details behind each.
- Recent protections and security updates, which highlights recently published and added threat research and protection intelligence and/or signatures, continuously updated by our global ThreatLabz research team.
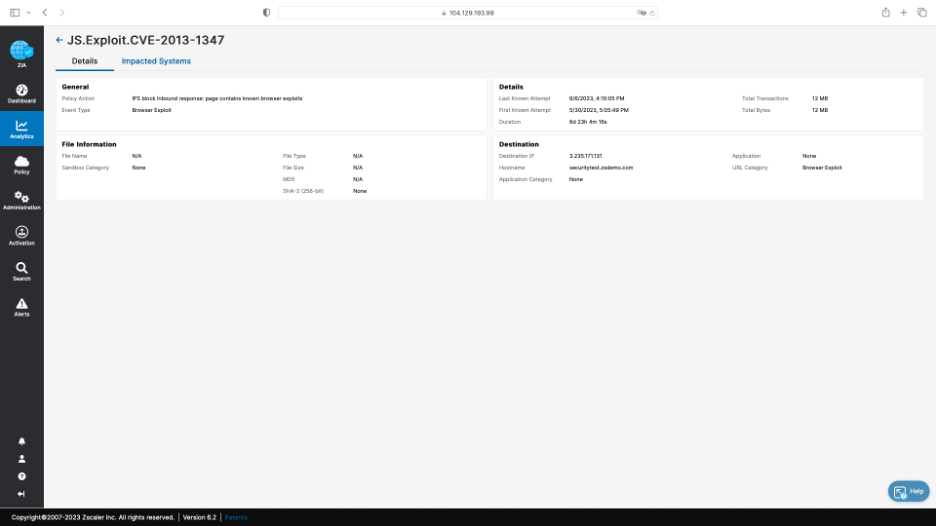
When you click into a threat incident, you can quickly see more detailed information, including description, action, and first and last known attempt:
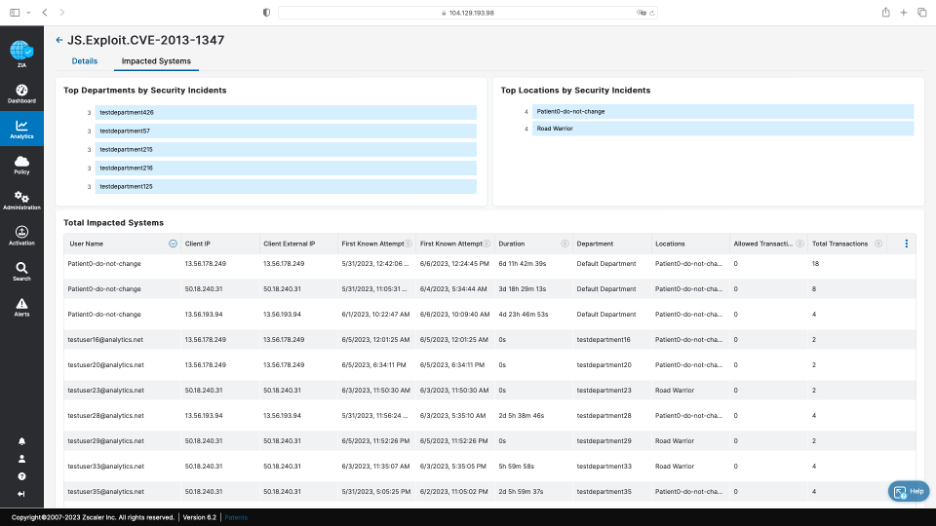
The “Impacted Systems” tab shows you all impacted systems with IP, user name, department, location, and first known attempt:
Benefits
The new Cybersecurity Insights Dashboard provides a single view of all the actionable insights security leaders need to quickly understand, socialize, and react to changes in their security posture. You can stay even more on top of these trends with customizable alerts for new threat incidents and ThreatLabz threat research updates.
Release and Future Direction
This capability is planned to be released before end of August. Please reach out to your account teams to learn more and share your use case details and other feedback with us.
For more about our latest cybersecurity innovations, check out the rest of our Zenith Live Cybersecurity Innovations blog series.




