Zscaler Blog
Get the latest Zscaler blog updates in your inbox
SubscribeDefending Against Encrypted Threats: A Guide to SSL Traffic Inspection with Zscaler
Full traffic inspection at scale over all ports and protocols is fundamental to the protection Zscaler provides customers: without inline inspection of encrypted traffic, customers cannot leverage the full visibility Zscaler provides to effectively block malware and prevent data loss.
In the Zscaler ThreatLabz 2024 Encrypted Attacks Report, our threat intelligence analysts determined that 87.2% of attacks are executed via HTTPS traffic including SSL and TLS, 86.5% of which involve malware. Moreover, with over 95% of global traffic encrypted most threats are passed within that encrypted traffic and can hide without implementing inline SSL/TLS inspection. As the stats below from the report show, full visibility into encrypted traffic is no longer an option but a must for security stakeholders:
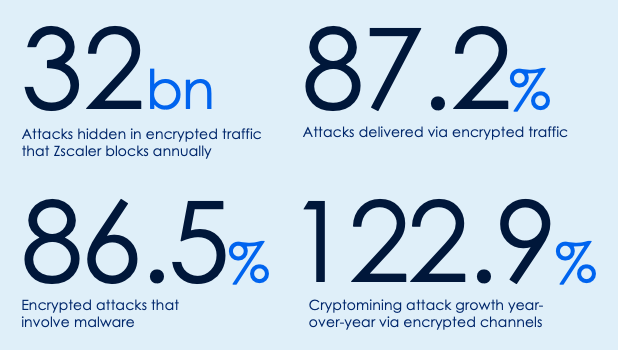
This blog covers the best practices for enabling encrypted traffic inspection after an initial Zscaler Internet Access deployment. We’ll also look at the insights traffic inspection provides so you can further tune your inspection policies for maximum effectiveness.
Encrypted traffic inspection best practices
Zscaler Internet Access (ZIA), a cloud-native Secure Web Gateway (SWG) that’s part of the Zero Trust Exchange, enables organizations to defend against a wide array of threats while providing employees access to business-critical applications. Zscaler can still protect traffic with zero trust strategies without encrypted traffic inspection, but organizations miss out on the full benefit of Zscaler security capabilities from Cloud Sandbox to Advanced Threat Prevention if they don’t enable encrypted traffic inspection.
Recommended initial encrypted traffic inspection policies
Let’s look at what a set of SSL inspection rules look like from a “best practices” standpoint. Logged into a ZIA tenant, customers go to “Policy” then “SSL Inspection” and click “Add SSL Inspection Rule” to implement policy rules:
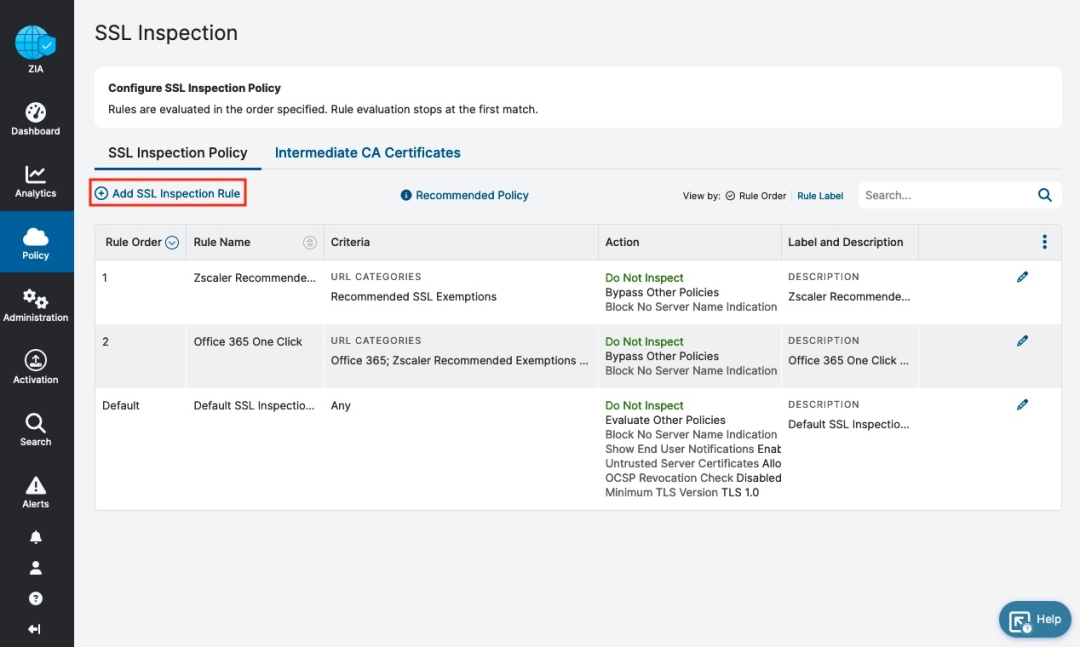
A set of SSL/TLS Inspection policies for ZIA can be looked at as a cascading set of rules with criteria customers determine for what traffic should or should not be inspected.
Before getting into a recommended set of policy rules, it’s important to point out that not all web-based services pose risk or enough risk to warrant encrypted traffic inspection. These include conferencing and communication systems (Microsoft Teams or Zoom). Additionally, our customers often configure rules to exempt inspecting traffic for URL categories that have Personal Identifiable Information (PII) concerns such as Health Care or Finance/Banking due to regulatory compliance. But it’s still possible to inspect the majority of traffic even with requirements to carve out inspection exemptions.
Zscaler recommends inspecting as much traffic as possible and defining how to handle non-inspected traffic as part of a zero trust strategy. You should implement a baseline traffic inspection policy, and then expand inspection to additional URL categories.
Recommended inspection best practices and initial policies
Given Microsoft 365’s wide usage across organizations, Zscaler devised in consultation with Microsoft “click-to-run” policies: this is a set of rules that result in the best experience for Microsoft 365 users. If Microsoft makes a change on their side, Zscaler automatically updates the Microsoft 365 click-to-run policies. To enable these policies:
- Go to Policy > URL & Cloud App Control > Advanced Policy Settings.
- Select to "Enable Microsoft-Recommended One Click Office 365 Configuration" and save changes.
- Go to Policy > SSL Inspection
In terms of an overall encrypted traffic inspection policy framework, you want to build rules that align closely with the leading practices examples as discussed in Configuring SSL Inspection Policy, available in Zscaler’s Help Portal that provides product documentation and deployment guidance.
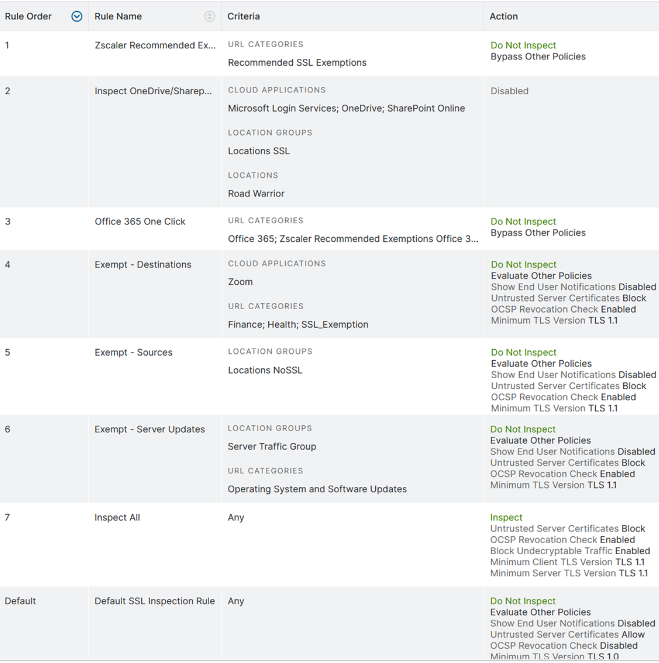
Our Help Portal also provides the document ZIA SSL Inspection Leading Practices Guide: it contains additional content and guidance on SSL/TLS inspection deployment, including a table with recommended SSL inspection policies. Here’s a quick summary of what those recommended inspection policies do:
- Zscaler Recommended Exemption Rule: This is a predefined rule enabled by default to automatically exempt known destinations that cannot be SSL inspected for various reasons, such as certificate pinning as well as Zscaler-owned domains. The percentage of traffic that matches this rule is commonly very small and less than 1%. To see the traffic exempted by this rule, search the weblogs using the SSL Policy Reason field for the reason Not inspected because of Zscaler best practices.
- Inspect OneDrive and SharePoint: you would select only those traffic sources currently being inspected – this might require multiple policies.
- Microsoft 365 click-to-run exemption: as discussed above
- Destination-based exemptions for Health, Finance, Custom Lists, and Cloud Applications categories: certain industries place regulatory restrictions on what sensitive information should be protected, and thus not inspected. You can gain more context and guidance in our document Encryption, Privacy, and Data Protection: A Balancing Act
- Source-based exemptions: this policy rule will result in traffic originating from specific sources not being inspected. You can add a rule to inspect any Zscaler Client Connector device before this exemption.
- Specific exemptions: this policy rule gets granular and lets you ensure specific source and destination exemption needs are met without being excessive.
- Inspect all traffic not exempted. New Zscaler customers during a pilot can select specific groups as opt-in to inspect instead of all users by default.
- Default rule: this rule essentially directs ZIA to evaluate all other web and cloudapp rules.
Here’s what this inspection and exemption rule set looks like in ZIA:
Options for handling certificate pinning
Certificate pinning is a coding technique developers use to prevent Man-in-the-Middle (MiTM) inspection. In certificate pinning, the application is hard-coded with a server certificate and treats any other certificate as invalid. This prevents MiTM attacks, but it also prevents a MiTM proxy like the Zscaler Zero Trust Exchange from intercepting, decrypting, and inspecting traffic and applying security policy before re-encrypting the session before sending it to its destination. A few caveats here:
- Zscaler cannot inspect TLS traffic from sites or applications that use certificate pinning including Microsoft 365 and apps like WebEx, Dropbox and others. Zscaler is not alone in this regard as other SWG vendors also face this constraint. However, we do offer one-click access to Microsoft 365 apps with a simple configuration.
- The good news: the industry overall is deprecating certificate pinning due to certificate issues that block access. Both application vendors and public Certificate Authorities (CAs) are moving to shorter lifetimes for their intermediate CAs.
We provide a few options for customers with applications using pinned certificates:
- Bypass the traffic if you encounter certificate pinning but only if the application is of such high value to the organization that it’s worth the associated risk caused by not inspecting the traffic. Otherwise, deny the traffic outright.
- Out-of-band inspection: when traffic cannot be inspected inline, we can still enable customers to secure any sanctioned or unsanctioned SaaS app or IaaS platform: ZIA provides out-of-band CASB scanning using APIs to connect to your applications and storage providers. Files and data are scanned by Zscaler Cloud DLP, and our anti-malware engines scan data at rest. This means you can scan for data leaks and identify malicious files in cloud apps that might have been uploaded by employees, partners or customers.
Custom Certificate Store application inspection
When Zscaler SSL inspection is enabled, the organization’s certificate facilitates secure web access by default, with root and intermediate certificates preinstalled in the system's certificate store. However, certain applications rely on custom trust stores, potentially causing the TLS validation failures. To ensure seamless connectivity, administrators must manually import the root CA into the custom trust store or disable server certificate validation when necessary.
Understanding the critical role of SSL traffic inspection in defending against cyber threats, we took proactive steps to assist our customers. We identified widely used applications within popular developer tool bundles and researched the necessary configurations. This ensures that the data exchanged through these applications is thoroughly inspected and scanned for potential threats and data leaks, reinforcing a secure and resilient network environment.
For a deeper dive, check out the article published on our help portal, which outlines these steps in detail. Applying these configurations can help you expand your SSL inspection coverage and strengthen your organization’s security posture.
Leverage insights gained from inspecting encrypted traffic
Once you have your traffic inspection ruleset in place, ZIA provides analytics reports that provide insights gained from the inspected traffic so you can better understand:
- The prevalence of protocols and client-side ciphers
- Threat types by protocol
- What policy adjustments to make to more effectively inspect traffic
Let’s look at how you can access the reports that will show you all this and more.
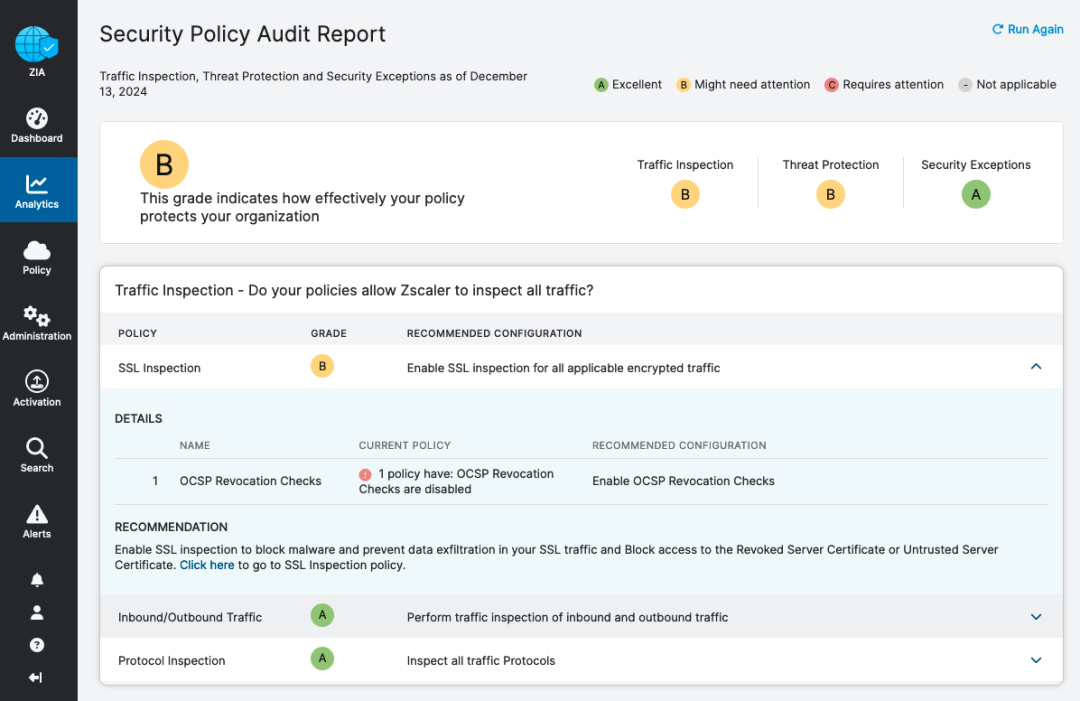
If you want to know what policy actions you should take to inspect more encrypted traffic, you can view these recommendations in the “Security Policy Audit Report”: log into the ZIA Admin a Portal, then go to Analytics > Security Policy Audit Report > Traffic Inspection. Click on the down caret symbol (⌄) to expand and view any recommendations that will improve your “Traffic Inspection” grade (currently a “B” grade as shown in the screenshot below):
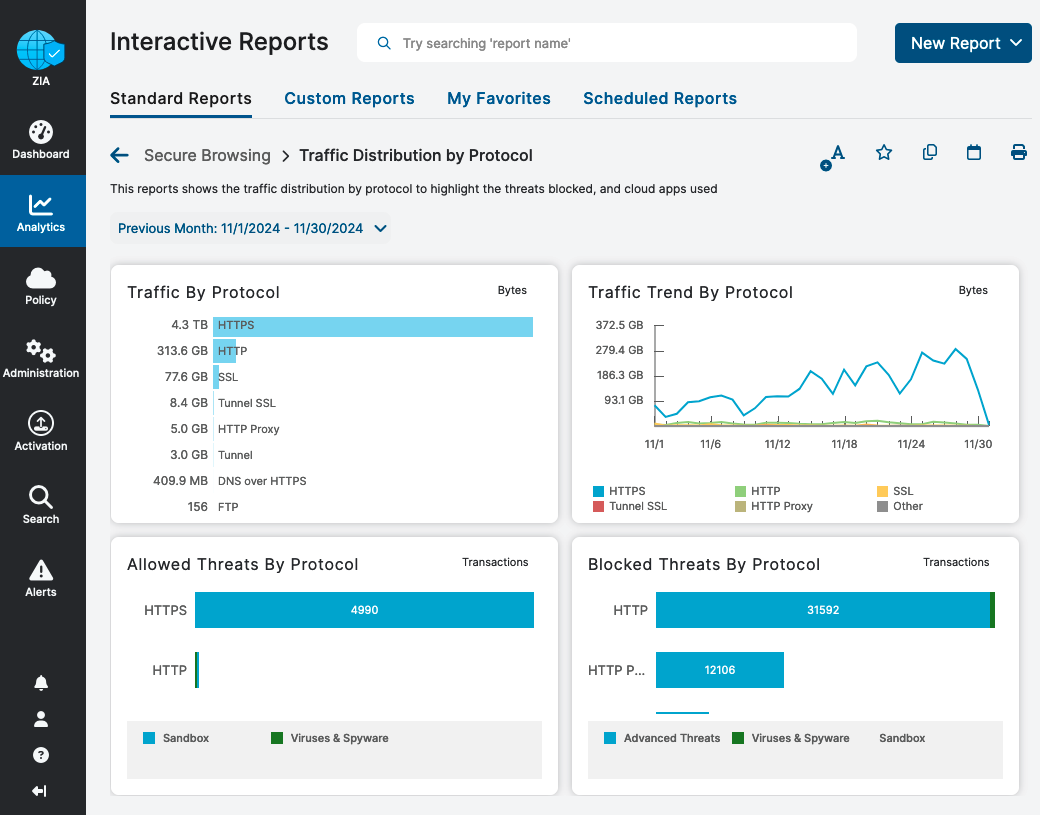
Other encryption-related reporting is available includes the Interactive Reports for Traffic Distribution by Protocol, shown below, which displays:
- Traffic by protocol
- Threats by protocol
- Top applications by protocol and more
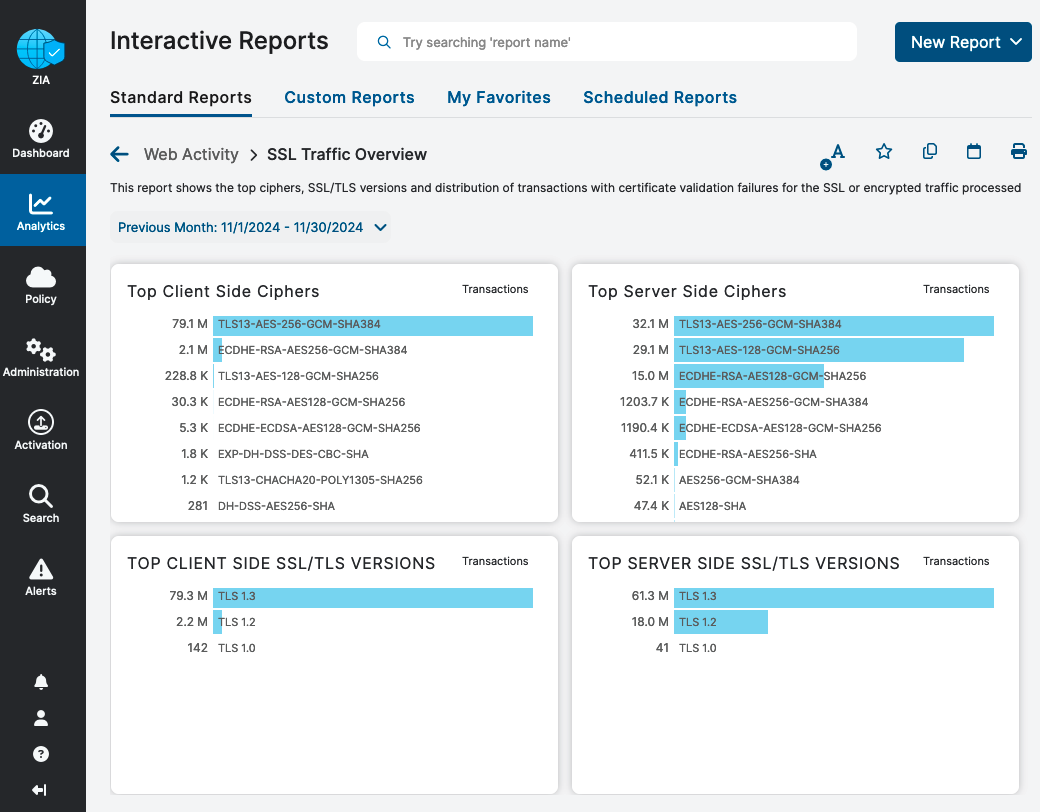
You can also view an Interactive Report for Web Activity: SSL Traffic Overview, which shows:
- Top client- and sever-side ciphers
- SSL/TLS versions
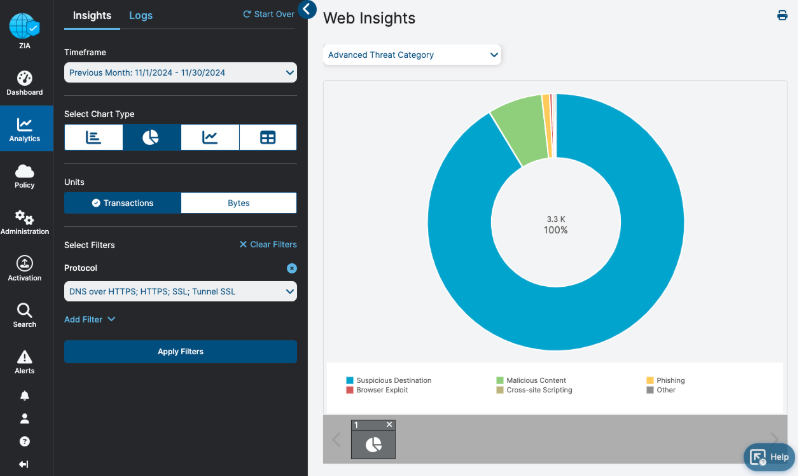
The Web Insights Report can be customized for a chosen timeframe to display granular information related to SSL and other protocols including:
- Threat categories
- Volume of threats
You can drill down further into the above by User, User Agent, Location, File Name and more. All of ZIA’s reporting provides information you need to further bolster your security posture and take further action if necessary.
Conclusion
With SSL/TLS traffic inspection enabled, Zscaler Internet Access provides full visibility into blocked attacks and is easily configured yet highly effective — so much so that CyberRatings, the leading non-profit security testing organization, awarded the Zero Trust Exchange an “AAA” rating in its 2024 Threat Protection Test. Download a copy of the CyberRatings report now.
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




