Blog Zscaler
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Iscriviti
Phishing Via Typosquatting and Brand Impersonation: Trends and Tactics
Introduction
Following the 2024 ThreatLabz Phishing Report, Zscaler ThreatLabz has been closely tracking domains associated with typosquatting and brand impersonation - common techniques used by threat actors to proliferate phishing campaigns. Typosquatting involves registering domains with misspelled versions of popular websites or brands to capitalize on user errors, while brand impersonation involves creating fake online entities that closely mimic a brand’s official presence. The big difference is that typosquatting relies on typographical mistakes, whereas brand impersonation focuses on deceiving users through visual and contextual similarities. These two techniques are closely interconnected and often work in tandem to deceive users, steal information, and/or install malware.
From February 2024 to July 2024, ThreatLabz analyzed typosquatting and brand impersonation activity across over 500 of the most visited domains, examining more than 30,000 lookalike domains, and discovering that over 10,000 were malicious. This blog summarizes our findings, highlighting the trends and tactics used to carry out these phishing campaigns.
Key Takeaways
- From February 2024 to July 2024, Google accounted for the largest percentage of phishing domains that leveraged typosquatting and brand impersonation. Microsoft and Amazon followed closely behind. Collectively, these three brands accounted for nearly three quarters of all these types of phishing domains.
- Nearly half of the phishing domains that were discovered used free Let's Encrypt TLS certificates to appear more authentic and avoid web browser warnings.
- The .com top-level domain (TLD) accounted for a significant amount of the phishing domains with English speakers being a primary target.
- The Internet Services sector was the most heavily spoofed vertical, followed closely behind by Professional Services and Online Shopping.
Threats And Trends
Understanding typosquatting and brand impersonation trends is essential for users and organizations to defend against phishing attacks, safeguard brand reputation, enhance cybersecurity measures, and promote a safer online experience.
Most targeted verticals
The breakdown by vertical for phishing domains was the following:
- The Internet Services sector, which emerged as the most frequently impersonated vertical (29.2%), often handles large volumes of user data and financial transactions, making it a lucrative target for attackers.
- Professional Services, closely following at 26.09%, likely attract attackers due to the sensitive and confidential client information they manage.
- Online Shopping websites, accounting for 22.3% of phishing domains, are targeted because they involve direct financial transactions and possess a wealth of user payment data.
- By comparison, other verticals such as Social Networking (4.5%), Streaming Media (3.3%), AI/ML Apps (3.3%), Information Technology (3.1%), Corporate Marketing (1.6%), Finance (1.1%), File Hosting (0.7%), Science and Technology (0.4%), Web Search (0.4%), and Discussion Forums (0.3%), faced a relatively low percentage of attacks. This discrepancy can be attributed to the lower immediate financial returns associated with the data linked to these sectors.
Most targeted brands
During our observations, ThreatLabz identified threat actors targeting a range of popular brands, including file-sharing services, email providers, digital payment platforms, and online shopping services. However, Google, Microsoft, and Amazon emerged as the top three targeted vendors by far. Google accounted for the highest percentage of typosquatting and brand impersonation instances at 28.8%, followed by Microsoft at 23.6%, and Amazon at 22.3%. Meta was also targeted, albeit to a lesser extent, at 4%. Attackers mimic top brands because the global user base offers a vast number of accounts that can be targeted and easily monetized. The figure below shows the distribution of brands abused by threat actors leveraging typosquatting and brand impersonation.
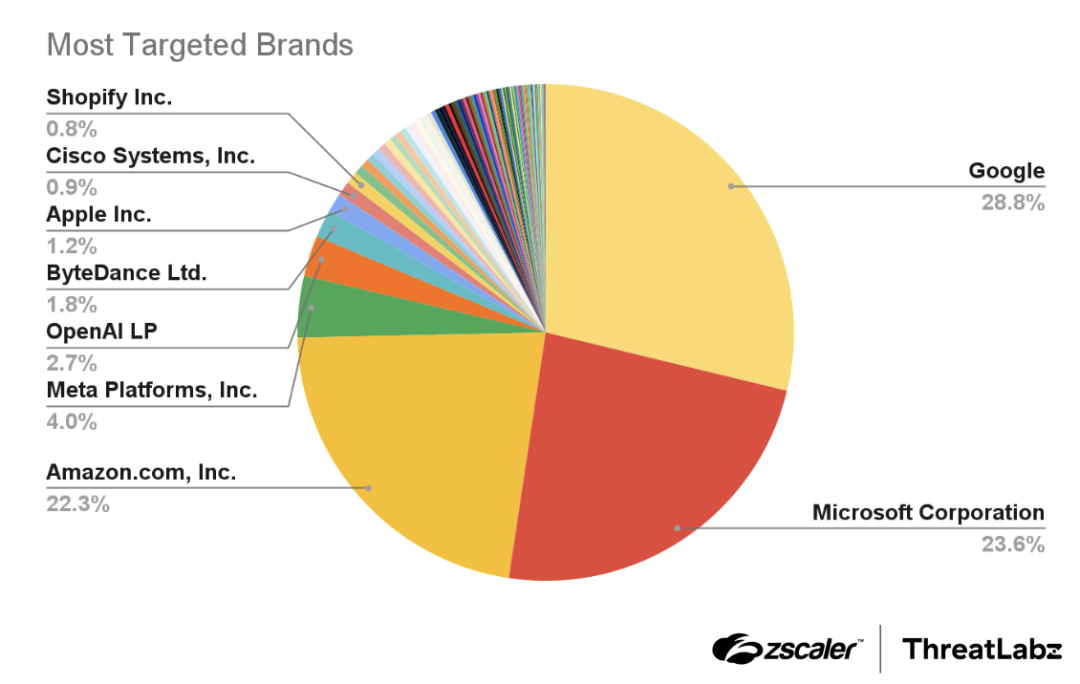
Figure 1: The most imitated brands by typosquatting and brand impersonation.
Most commonly abused certificate issuers
Threat actors often utilize HTTPS to create the illusion of legitimacy for their phishing sites. Among the analyzed phishing domains, 48.4% were discovered to have certificates issued by Let's Encrypt, a widely-used free and open certificate authority (CA). Let's Encrypt is known for its ease of use and minimal security checks required for obtaining TLS certificates, thus making it the most popular CA used by the threat actors. The second preferred CA used by attackers was Google Trust Services accounting for 21.5% of the total certificates, benefiting from Google's strong brand trust. GoDaddy issued 15.2% of the certificates, making it the third most popular CA due to its significant market presence and the convenience of obtaining certificates when registering domains. The figure below shows the most commonly used certificate authorities used by malicious domains.
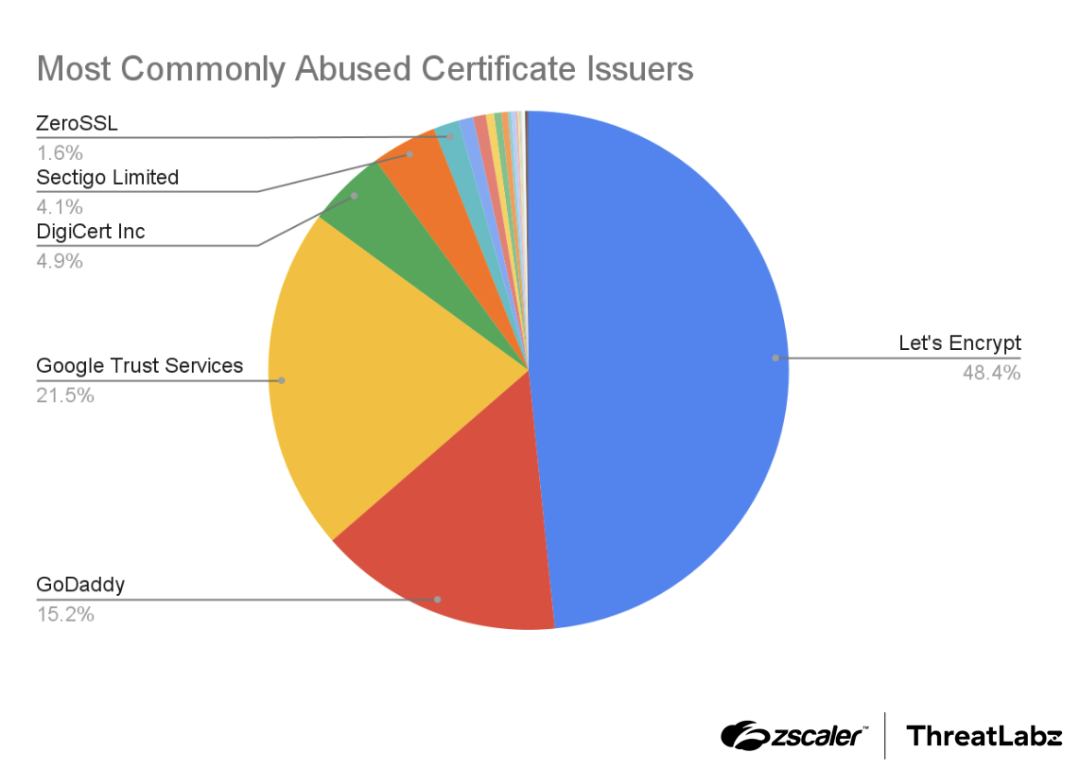
Figure 2: The most common certificate authorities used by typosquatting and brand impersonation domains.
Most commonly abused domain registrars
Domain registrars are consistently abused by threat actors to register their typosquatting and impersonation domains. GoDaddy stood out with the highest percentage of domains, accounting for 21.7% of the instances, followed by NameCheap at 7.3%, and NameSilo at 6.4%. Attackers use such established registrars primarily for their reputation, cost effectiveness, and privacy options. The figure below shows the most commonly used domain registrars for typosquatting and brand impersonation attacks.
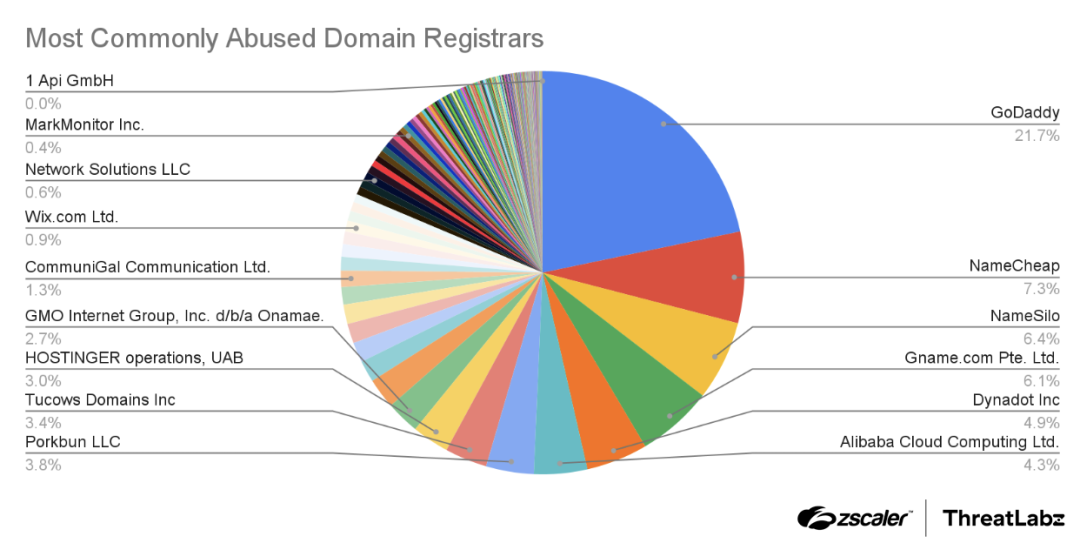
Figure 3: Domain registrars used for registering malicious typosquatting and brand impersonation domains.
Most commonly used TLDs
Threat actors leverage commonly used top-level domains (TLDs) typically associated with legitimate websites. This tactic aims to deceive unsuspecting users, fostering a false sense of security by making the phishing domains appear harmless. Interestingly, TLDs such as .xyz and .top, which are not commonly associated with benign sites, have emerged as popular choices among threat actors.
The .com TLD was the most popular with 39.4% likely due to the fact that it is the most recognizable, and therefore may increase the chances of success. The .xyz and .top stood at 11.1% and 5.4%, respectively. These TLDs are relatively unknown, but were likely used because they are less expensive to register. The figure below shows the most commonly used TLDs.
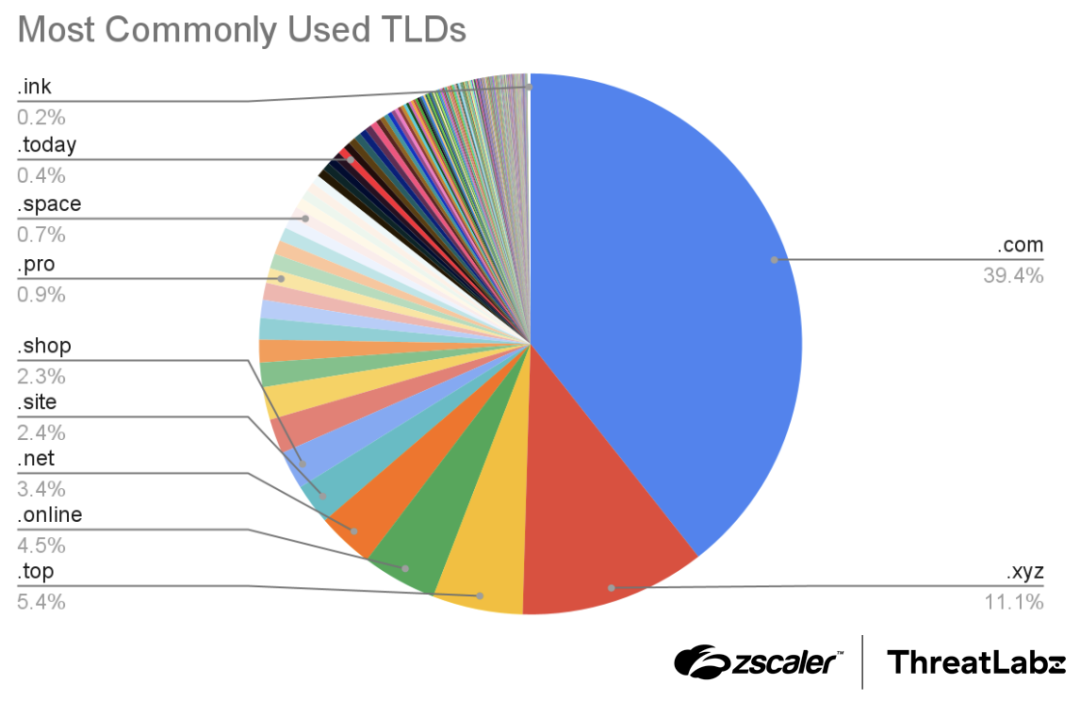
Figure 4: The most commonly used TLDs for typosquatting and brand impersonation domains.
Case Studies
The following examples show how threat actors leverage typosquatting and brand impersonation to perpetrate phishing campaigns. These domains were used for malware distribution, credential theft, scams, and malware command-and-control (C2) communication.
Malware distribution
An example domain discovered by ThreatLabz used for malware distribution was “acrobatbrowser[.]com”, which impersonated the official Adobe website. The domain displayed a fake Adobe page with an embedded iframe window. As soon as the website was loaded, an MSI file (disguised as an Adobe plugin), was downloaded automatically. The MSI file contained the Atera Remote Access Trojan (RAT) providing attackers with remote control over a device and allowing them to steal personal data, spy on user activity, and deploy additional payloads.
The figure below shows the fraudulent domain along with the embedded iframe, and the subsequent MSI file that was downloaded.
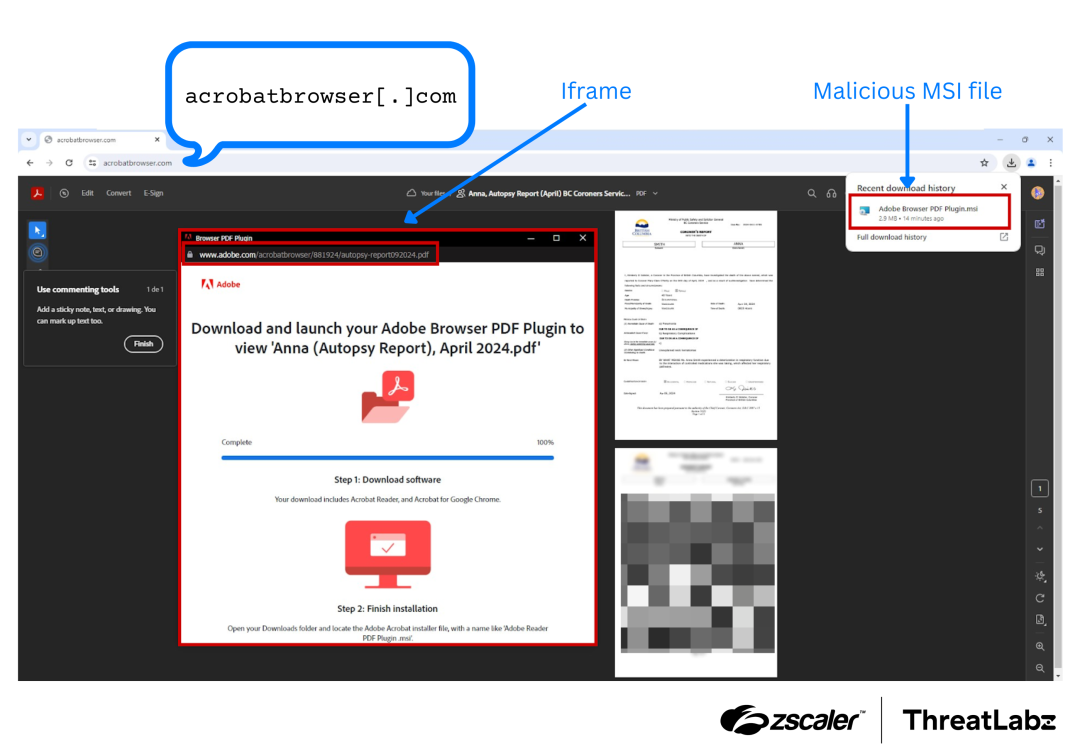
Figure 5: Example brand impersonation domain used to distribute the Atera RAT.
Credential theft
ThreatLabz discovered some of the typosquatting domains used for credential theft. The figure below shows the domain named “offlice365[.]com” imitating the legitimate domain office365.com using a character insertion technique. The attacker hosted a fake Office 365 page to trick victims into entering their credentials. If a user entered their credentials, they would be redirected to the real office365.com website after their login information was stolen.
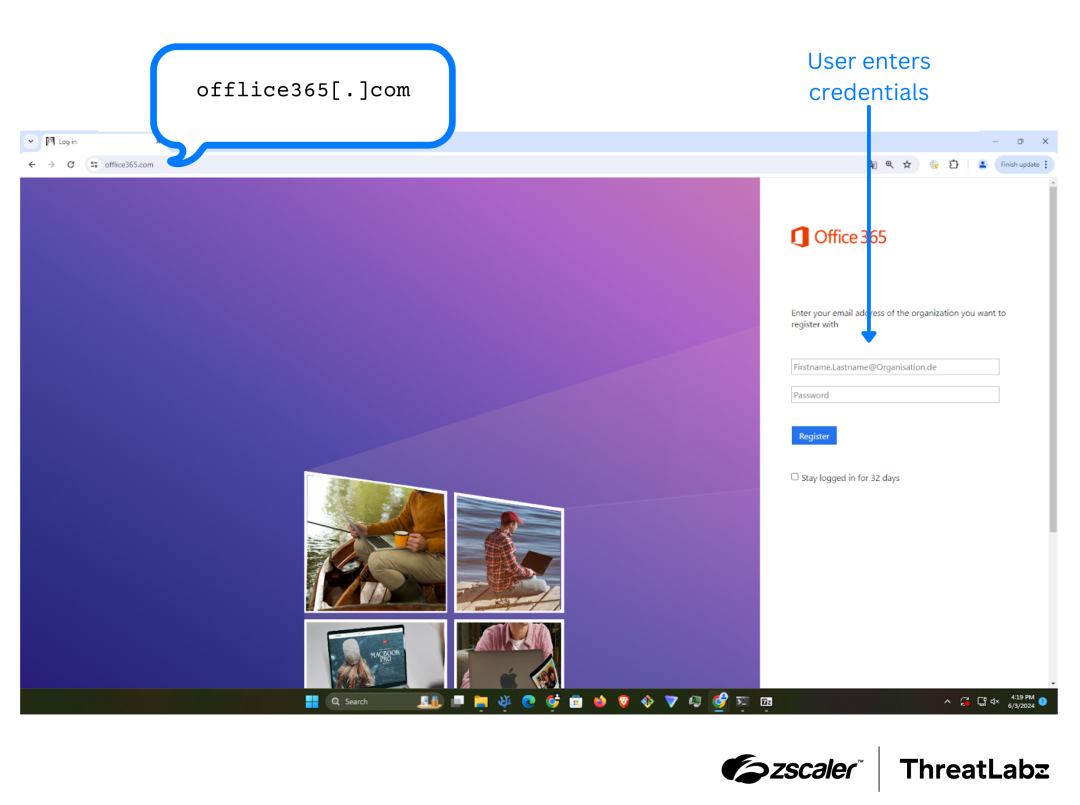
Figure 6: Example typosquatting domain designed to trick users into providing their login credentials for Office 365.
Scams
ThreatLabz discovered instances where scammers targeted users through messaging platforms by impersonating reputable brands. The figure below shows scammers posing as Amazon on WhatsApp and encouraging users to “apply” for a job. By mimicking well-known brands, scammers use these lookalike domains to lure users into sharing personal information.
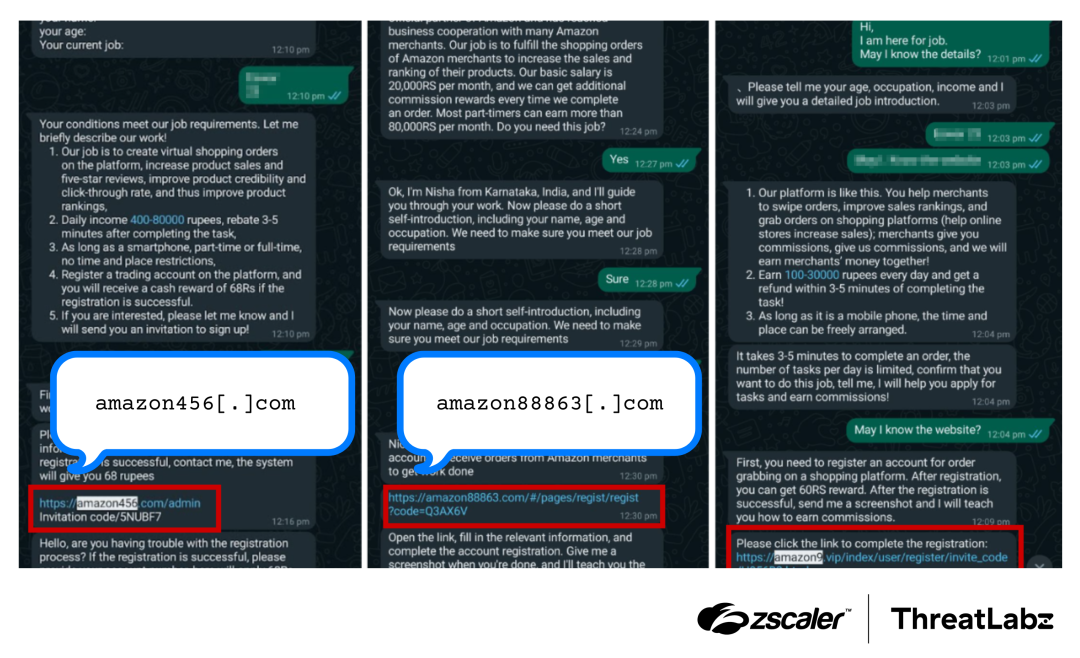
Figure 7: Scammers impersonating Amazon, making contact via WhatsApp, and encouraging victims to “apply” for a job.
C2 communication
Threat actors often employ typosquatting domains to disguise C2 communication channels. For example, ThreatLabz discovered the domain “onedrivesync[.]com” hosting a TacticalRMM tool, a remote monitoring and management software application that is often leveraged for malicious purposes, as shown in the figure below. This threat actor attempted to evade detection by spoofing Microsoft OneDrive, which is commonly used in corporate environments.
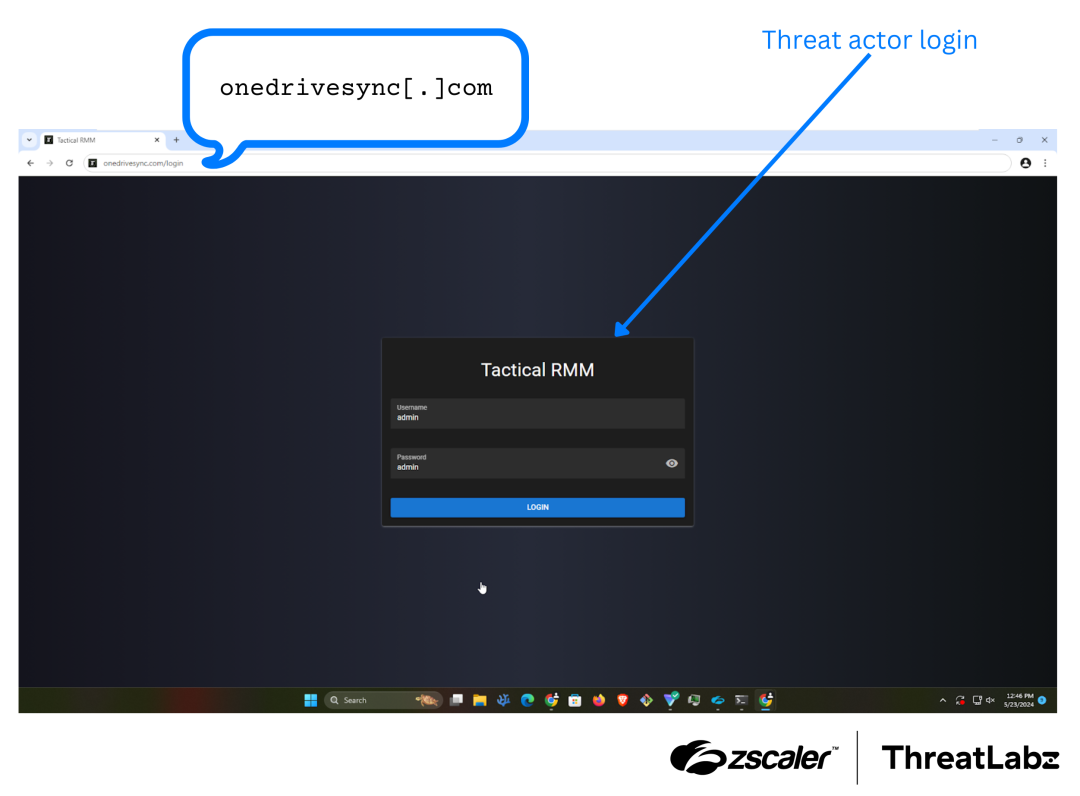
Figure 8: An example Tactical RMM C2 server impersonating Microsoft OneDrive.
Conclusion
Typosquatting and brand impersonation are common methods used in phishing attacks, abusing typographical errors entered by users and the trust those users place in well-known brands. These deceptive domains lure users into visiting fraudulent websites, where their personal information can be stolen or their systems compromised. Understanding the current trends and tactics in typosquatting and brand impersonation can help empower users and organizations to better recognize and defend against these phishing techniques.
Zscaler ThreatLabz is dedicated to actively monitoring and blocking these threats, stopping them before they can facilitate phishing attacks and cause harm to customers.
Zscaler Coverage
Zscaler’s multilayered cloud security platform effectively blocks malicious indicators across multiple levels. Additionally, ThreatLabz conducts proactive scans of newly registered domains and swiftly blocks any identified risks.
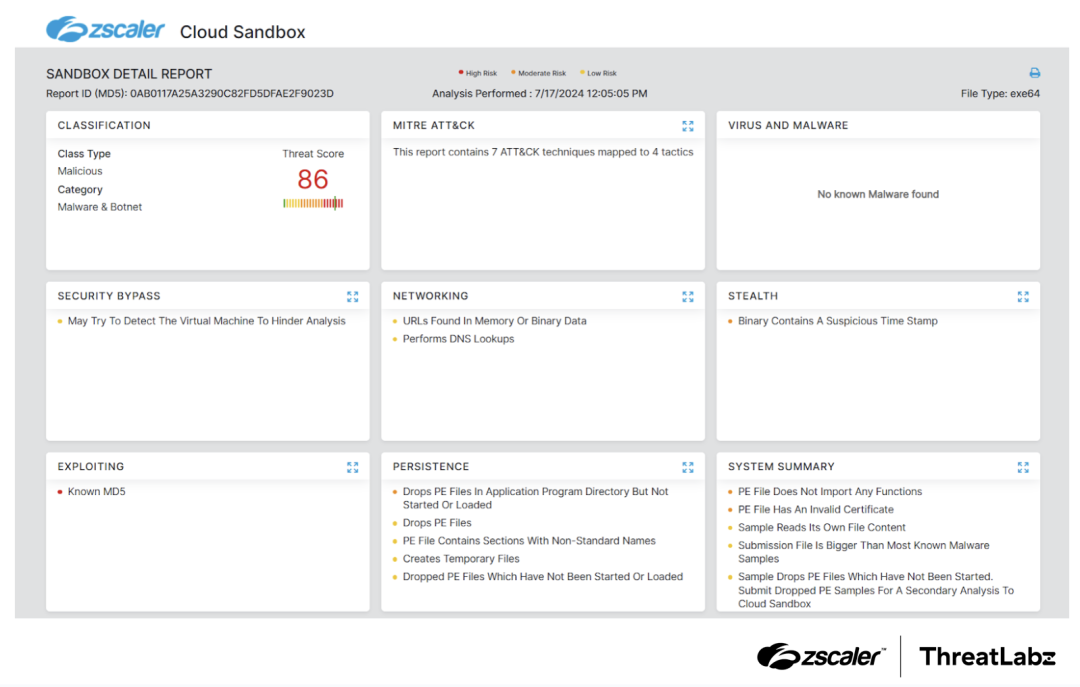
Figure 9: Zscaler cloud sandbox report
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to typosquatting at various levels with the following threat names:
Indicators Of Compromise (IOCs)
- acrobatbrowser[.]com
- browserpapernews[.]pages[.]dev
- googleupdate[.]vip
- offlice365[.]com
- whatsapp-web[.]cn
- googqle[.]com
- play-store-google[.]com
- onedrivesync[.]com
- adobevn[.]pro
- whatsapp2024[.]ru
In addition to those indicators, we added malicious domains likely belonging to the threat actor to our GitHub repository.
Questo post è stato utile?
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Inviando il modulo, si accetta la nostra Informativa sulla privacy.



