Recently, the U.S. Department of Homeland Security (DHS) released an article warning mobile users about the increasing use of spyware apps.
The US-CERT (Computer Emergency Response Team) issued the following statement:
The statement was released just after the Federal Trade Commission (FTC) marked its first case against stalking apps (also known as stalkerware or spyware apps). A case was filed against a company that developed and distributed stalking apps that could track smartphone activities like call history, text messages, photos, locations, browser history, and more. These apps were marketed as apps for monitoring the location and activities of children, employees, or spouses.
According to the FTC's complaint, the company did not take steps to ensure that purchasers were using the apps for legitimate purposes.
During the timeframe when the US-CERT released its statement, we noticed some hits on the Zscaler cloud in relation to spyware activities. We frequently detect the presence of spyware apps such as Spymie, TruthSpy, iSpyoo, GuestSpy, Spynote, NeoSpy, among others, on the Zscaler cloud, but we also found some new actors in this period.
In this blog, we will briefly discuss these new spyware apps. The blog is divided into three parts. First, we discuss typical stalkerware functionalities, then we'll explore some of the different types of spyware apps we've seen in the last few months, and in the final part we'll cover the indicators of compromise (IOCs).
Stalkerware (stalking apps or spyware), as the name suggests, is a type of app that spies on victims. Stalkerware apps are capable of, but not limited to, performing the following functions:
- Stealing contacts
- Spying on text messages
- Stealing photos
- Spying on browsing history
- Spying on banking apps
- Stealing GPS locations
Normally, one is required to have physical access to a mobile device in order to install spyware apps, but an attacker can use social engineering tactics to get the victim to install spyware.
Once installed, the typical spyware app will typically gain admin-level access, hide itself, spy on the victim, and, finally, send the stolen data to the attacker.
The following is an abstract about some spyware apps we found on the Zscaler cloud.
Android Monitors
Package Name: com.ibm.fb
Hash : 97c6c8b961d57d4ebad47f5c63ec6446
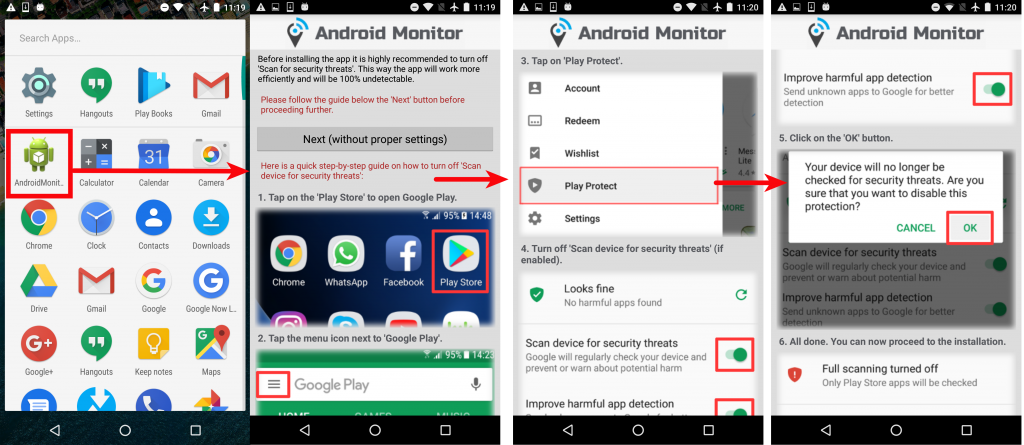
We saw multiple entries of spyware apps dubbed Android Monitors. Upon looking at the icon, we believe it is in its development phase. Once installed, it cleverly safeguards itself from Google's security framework, Play Protect.
|
|
| Fig 1: Android Monitor initial setup |
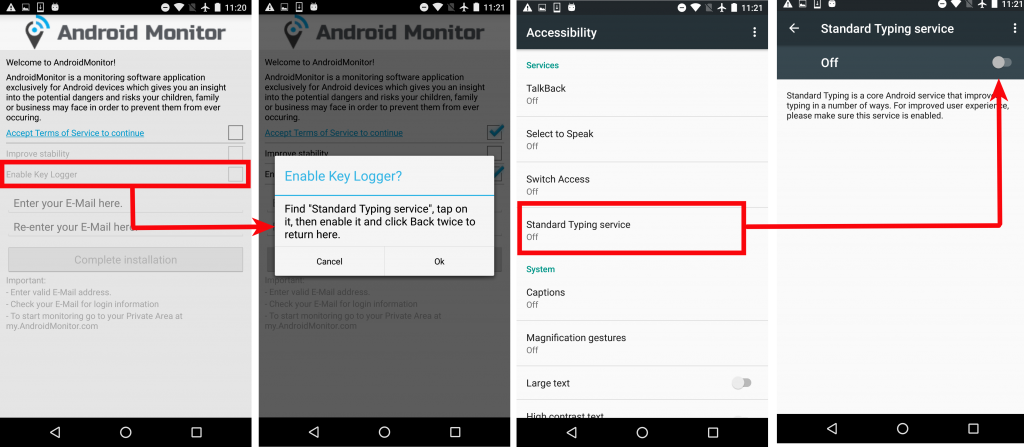
The screenshot below shows the functionality of the app's keylogger. If enabled, this app can spy on everything that the victim types, which can include personal WhatsApp messages, Facebook chats, emails, banking activities, and much more.
 |
|
Fig 2: Android Monitor keylogging |
The above screenshot also has an email ID column to which all the stolen data is sent.
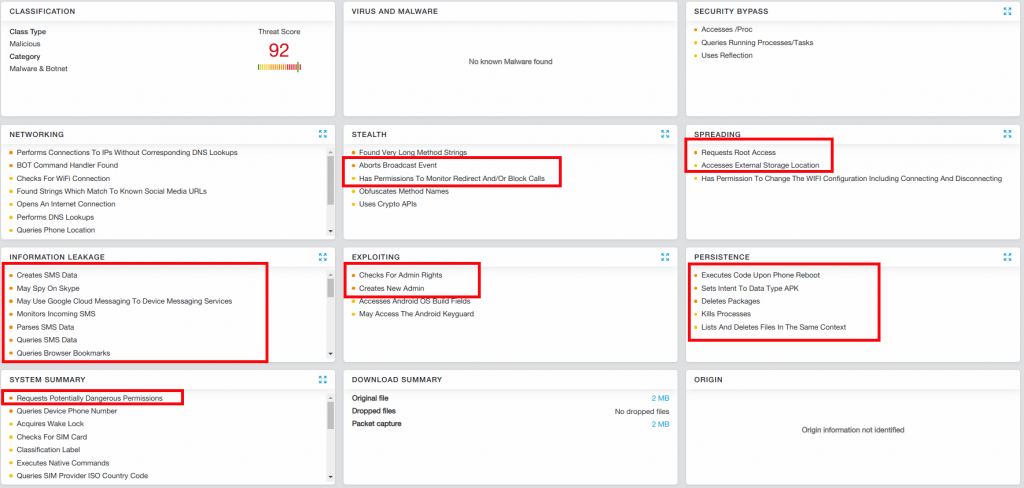
The Zscaler analytical system precisely detects this spyware. The following screenshot highlights the main functionalities of the app.
 |
|
Fig 3: Zscaler Cloud Sandbox with Android Monitor sample |
Russ City
Package Name: city.russ.alltrackercorp
Hash: 3b388138584ad3168e745097d5aa4206
This spyware app portrays itself as Thief Tracker. Further hunting for similar samples from the same source, we found two more apps, named System Info and System Updater. Upon analysis, we noticed that all three apps were the same; their only difference was their names.
The screenshot below shows how the three spyware apps appeared upon installation:
 |
|
Fig 4: Spyware app icons |
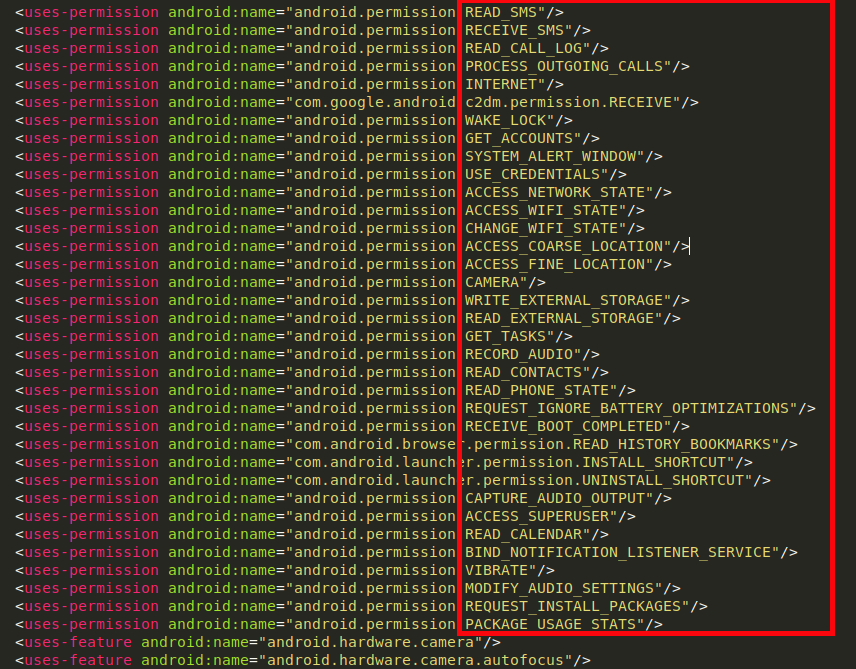
The complete functionality of this spyware can be seen in its manifest file, below.
 |
|
Fig 5: AndroidManifest.xml |
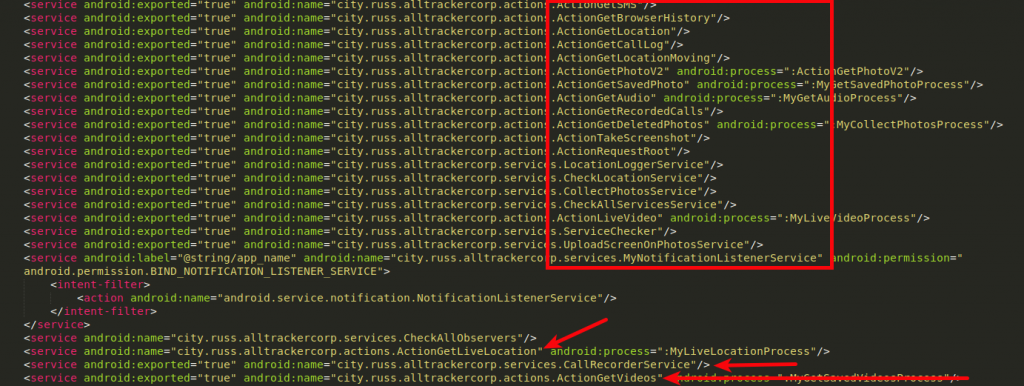
This app performs various background services:
- Read text messages
- Get browser history
- Fetch call logs
- Get GPS location
- Get clicked photos
- Record audio
- Record voice calls
- Capture screenshots
 |
|
Fig 6: Android services |
Spy Phone App
Package Name: com.spappm_mondow.alarm
Hash : 001209b1e2760f88f2bb4b68f159a473
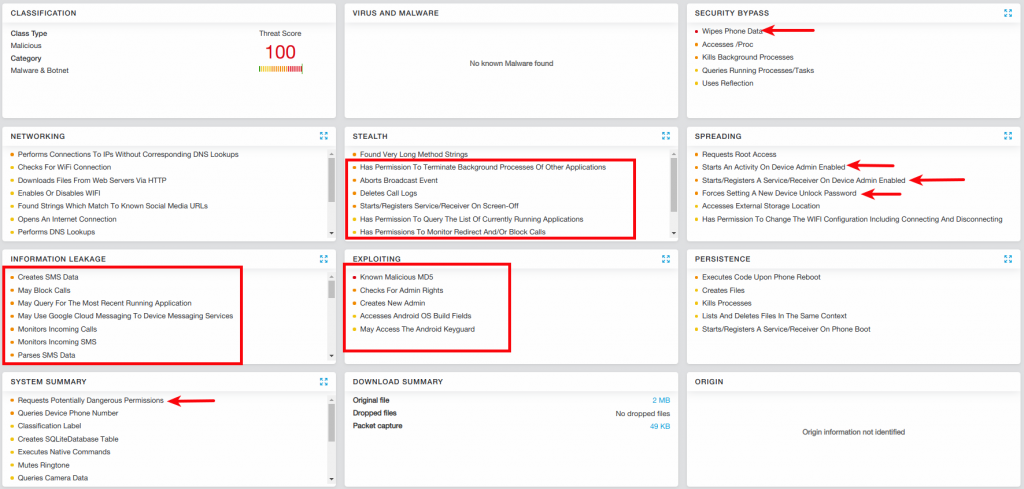
This app was delivered via Google Drive and contained almost all possible spyware functionalities, as shown in the screenshot below:
 |
|
Fig 7: Zscaler Sandbox displaying Spy Phone analysis |
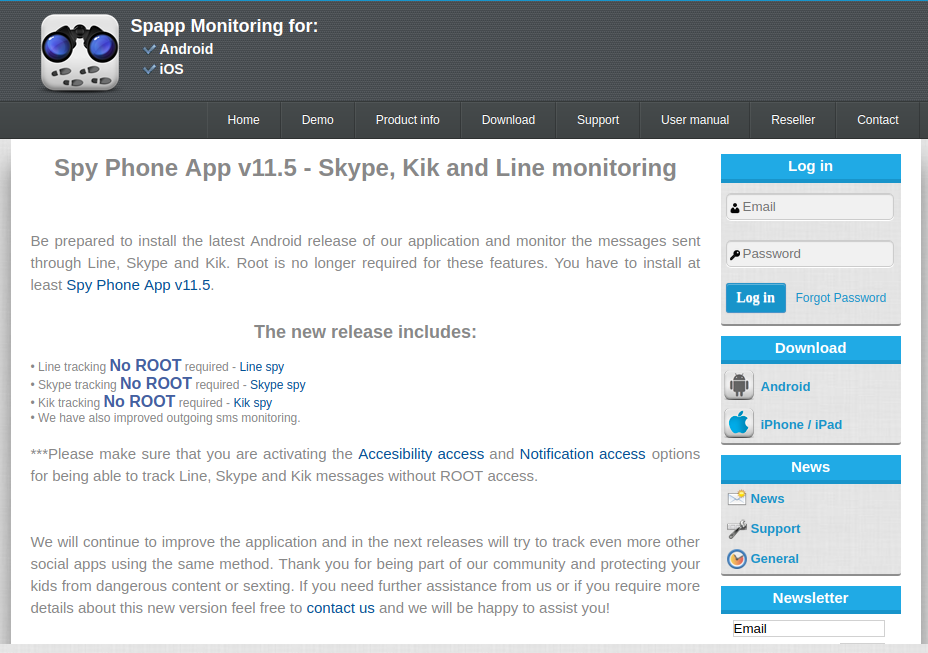
We found its platform online where the attacker can log in and check all the stolen data stored in this one place.
 |
|
Fig 8: Spy Phone App control panel |
Wi-Fi Settings
Package Name: com.wifiset.service
Hash : 8dab7a558f91e72e3edae8e20ee55c86
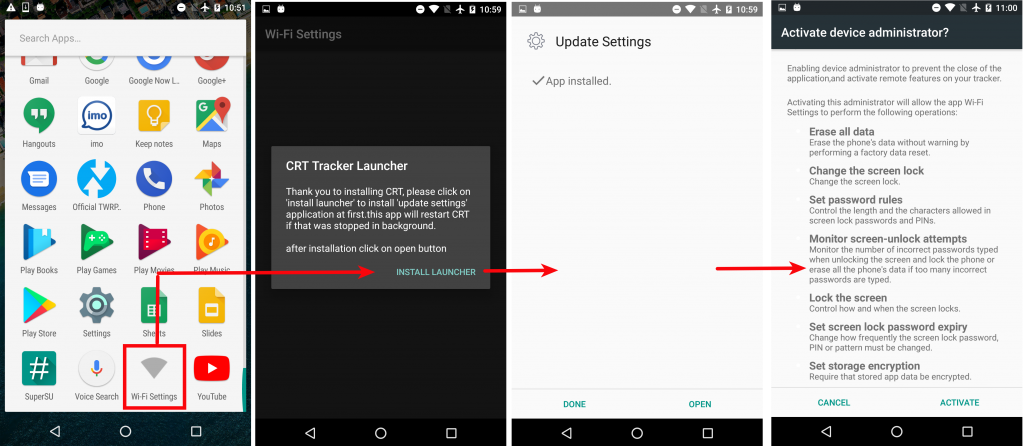
This stalkerware portrays itself as a settings app for Wi-Fi. One unique feature of this app is its method for staying persistent. During the installation process, it installs an additional app named Update Settings.
The screenshot below shows this functionality in action.
 |
|
Fig 9: Initial installation steps |
Once the initial setup is done, the attacker can enter his/her credentials and leave the rest on spyware. As soon as the spyware gets an internet connection, it starts sending the stolen data to a command & control (C&C) center/server. We noticed a major flaw with this spyware. It sends all the stolen data over plain-text (HTTP), which compromises the victim's data at the secondary level. As shown in the following screenshot, the user credentials are sent in plain text:
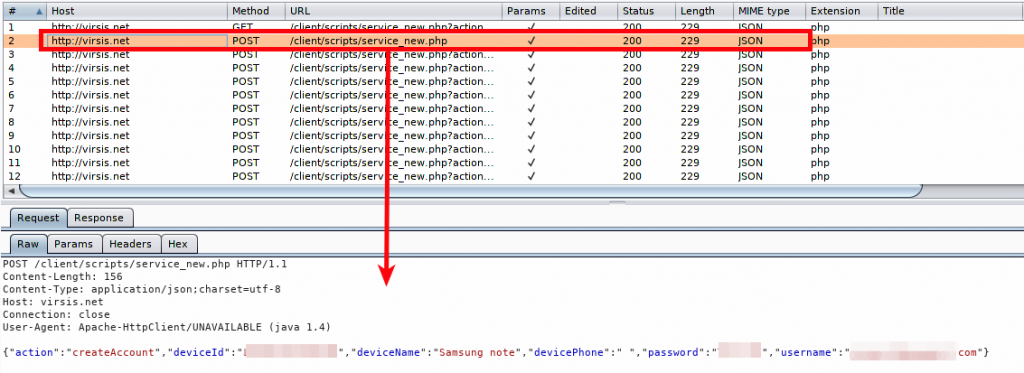 |
|
Fig 10: Plain text communication |
The screenshot below shows stolen photos being uploaded to the C&C server with basic Base64 encoding.
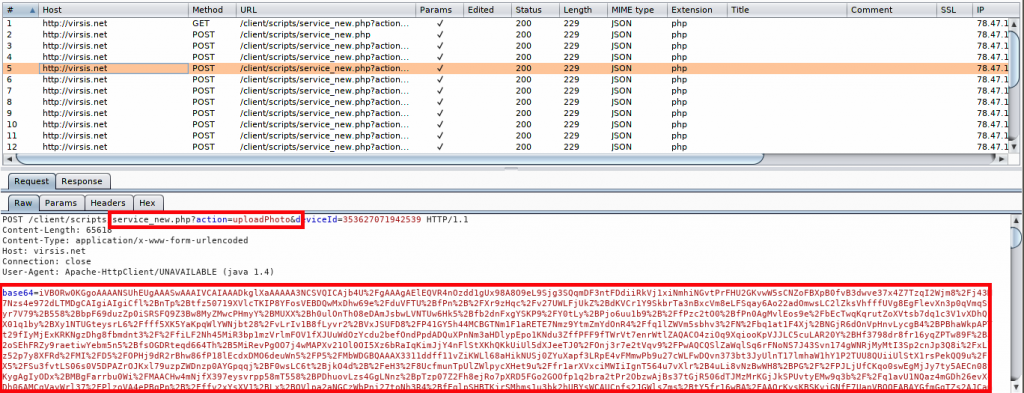 |
|
Fig 11: Spyware uploading photos from the victim's device |
Data Controller
Package Name: lookOut.Secure
Hash : 33dcfd84589c6ccf00fa5a302cefd0fe
This app portrays itself as Data Controller and has the package name lookout.Secure. It is strange to see a package called Lookout, as a legitimate company called Lookout is a highly regarded mobile security company. The attacker might have used this package name in order to trick users into trusting the app. Once installed, it asks for the purpose of use and whether the attacker wants to keep it hidden from the victim or not. (Spyware always prefers to hide itself to evade detection.)
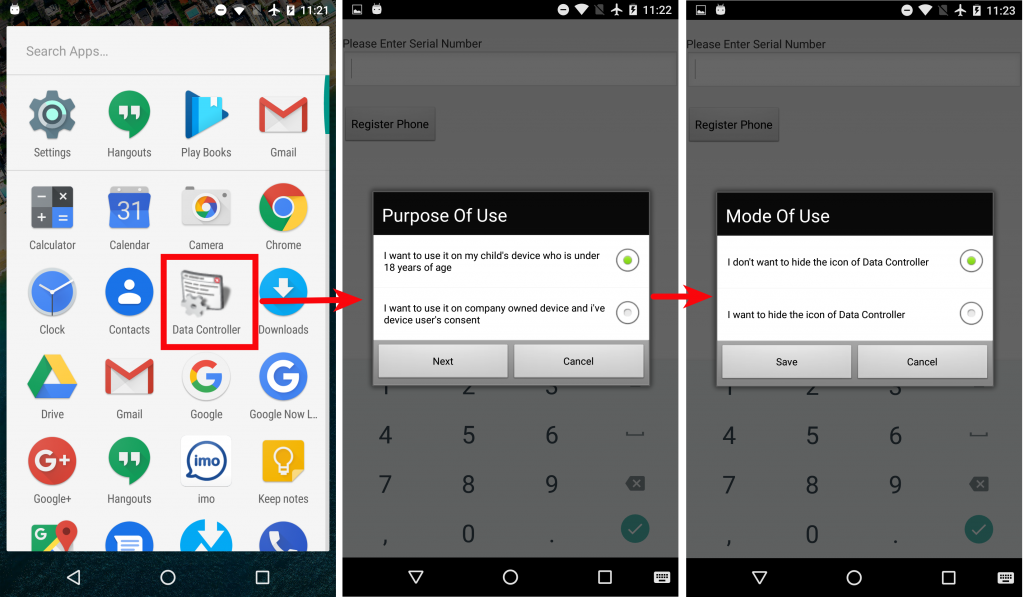 |
|
Fig 12: Initial installation steps |
The Zscaler Cloud Sandbox report shows the major spying capabilities in this spyware:
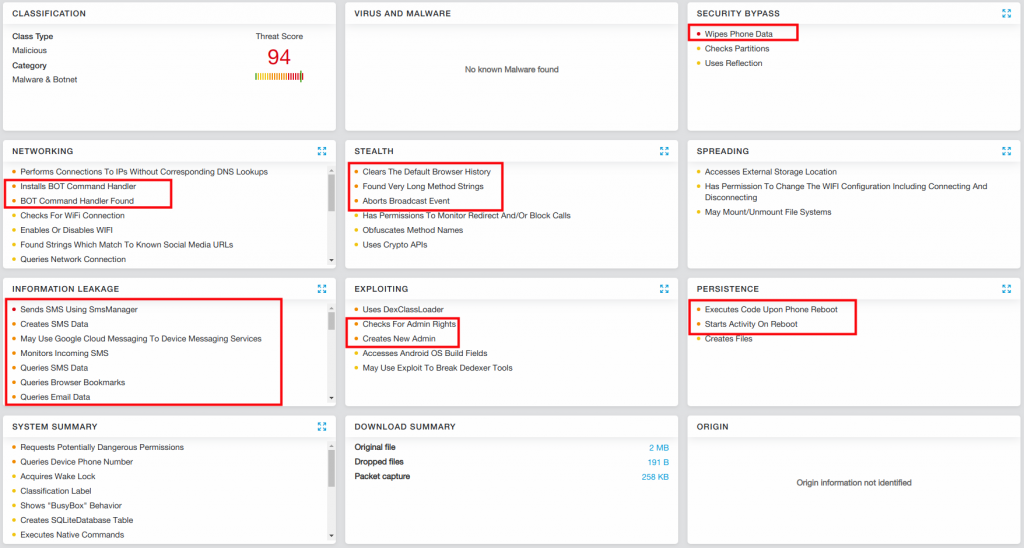 |
|
Fig 13: Sandbox report of the Data Controller app |
Auto Forward
Package Name: com.autoforward.monitor
Hash: 66dbd2d7614555440b657ae24527034a
It's common for spyware apps to portray themselves as parental-control apps. This is the case with Auto Forward spyware.
As soon as the spyware is installed, it displays itself as an app named Device. It asks for all available permissions necessary to spy, as shown in the screenshot below:
 |
|
Fig 14: Initial installation steps |
On its official website, Auto Forward assures users that the spyware works on both Android and iOS platforms.
Once installed, it steals the personal data of the victim and forwards it to its server, where the attacker can easily view stolen data such as text messages, WhatsApp activities, GPS locations, photos, a list of installed apps, and so on.
Conclusion
Spyware apps often portray themselves as parental-control apps or apps that can monitor employee whereabouts or the activities of a spouse suspected of cheating. Although there are legitimate uses, such as parents monitoring their children's location, these types of apps are often used maliciously.
Most of the spyware in this report were not properly designed. They store stolen data on a server without any security, which creates a single point of failure. Worse, a single instance of compromise can leak every victim's data into the wild.
Secondly, we observed the stolen data being transferred to C&C servers over plain-text channels, which can be compromised by man-in-the-middle attacks.
These flaws would not be acceptable with any legitimate app because they threaten the privacy of the users, potentially revealing their personally identifiable information (PII), which is obviously not a concern to the attackers.
Smartphone users who suspect their privacy may have been compromised by such apps can consider following these steps:
- Use a legitimate antivirus app that is regularly updated
- Try factory-resetting your device
- Remove suspicious apps from device administrator list
( settings --> security --> device administrators)
Zscaler customers are protected from stalkerware apps.
IOCs
| Hash |
| 97c6c8b961d57d4ebad47f5c63ec6446 |
| b0e68b66a5ba47612f2a6a33b343503b |
| 93e969ea1118a9d00be7f1c74b50fce9 |
| b44a98af29b021ad5df4ac6cc38fecf5 |
| d4ecbf666d17326deab49f75588e08b3 |
| 9eaf38020f898073af1a3ce34226c91f |
| ea1546f34a6cd517dcfec07861b7fb4f |
| 5fbb1b497c5a86815e5e8cc092d09af0 |
| 10322c7dea57269d69a85699e0357f5f |
| 3b388138584ad3168e745097d5aa4206 |
| 369a17a8e1031101f41cc31caac56b9c |
| ba63ae94bdec93abc144f3b628d151ad |
| 8dab7a558f91e72e3edae8e20ee55c86 |
| 001209b1e2760f88f2bb4b68f159a473 |
| 33dcfd84589c6ccf00fa5a302cefd0fe |
| 66dbd2d7614555440b657ae24527034a |
| URLs |
| russ[.]city/apks/alltracker_thief_v.6.5.2.apk |
| russ[.]city/apks/systeminfo_v.6.5.2.apk |
| russ[.]city/apks/systemupdater_v.6.5.2.apk |
| 206.41.116[.]121 |
| dwn[.]vys.me |