- The Flashback Trojan is a relatively new Trojan family, appearing on the scene late last summer/early September 2011. Since it's inception, there have been numerous variants - moving from being a pure social engineering play (appearing to be a fake Flash update) to leveraging exploits. The rapid evolution of this family has made it a little confusing to stay on top of. There were reports of Twitter being used for C&C updates as part of an early March variant. However, it is unclear if this communication avenue was ever actually used by the botherder.
- The latest variants of the Trojan, namely variant I and variant K, both exploit Java vulnerabilities- CVE-2011-3544 (Flashbak.I) and CVE-2012-0507 (Flashback.K). Oracle patched this latest vulnerability back in mid-February. Their CVSS risk matrix for this vulnerability can be seen below:
- Apple initially released a patch for the vulnerability April 3rd, six weeks after Oracle and then quietly announced on April 5th an update to the patch due to a few issues:

- Then there is the question of what the Trojan does/is doing. It has the capability to modify web pages (web-injects) viewed in Safari, based on a configuration file received from the C&C. However, it is not clear exactly what the web-injects will be used for. Similar functionality exists in many other bots, such as Zeus and is typically used to include additional form fields on banking sites to gather additional information such as SSN, debit card number, pin, etc.
- Finally, there is the question of how widespread the infections are. Dr. Web has reported 550K infections. Which would certainly rank this among the largest botnets. Some have claimed the numbers to be over-hyped or mis-counted. However, Kaspersky recently published a blog confirming the and even upping the number to 600K+ after sink-holing a C&C.
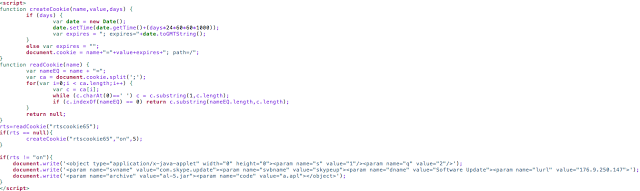
The site meta-refreshes to a blank page if JavaScript is disabled or NoScript is detected and uses a cookie to mark whether or not to embed the malicious Java applet.
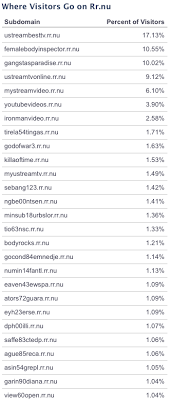
- bodyrocks.rr.nu
- femalebodyinspector.rr.nu
- johncartermovie2012.com
All of the top sites are related to this campaign, for example:
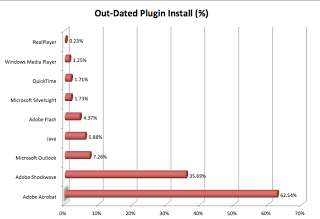
We'll close out with statistics on the browser plugins that we are seeing among our enterprise customer base. These stats were collected by querying the browser DOM during customer-logins, which allows us to identify browser plugins/extensions. We are currently seeing only about 6% of Enterprise systems with an out dated version of Java. Percentages of out-dated versions of Acrobat for example are much, much higher.