Please join our webcast for additional details regarding this attack.
Updated - October 25, 2017
Introduction
Almost four months after the last major outbreak, we are seeing a new variant of Petya ransomware dubbed "Bad Rabbit," and it's impacting multiple businesses, primarily in Russia and Ukraine. There have also been reports of businesses impacted in Germany, Turkey, and other countries. The ransomware payload contains a self-propagation module designed to perform lateral movement across the corporate network upon successful infection, which makes this threat highly virulent. The initial infection vector appears to be two Russian news agency sites : fontanka[.]ru and interfax[.]ru. [UPDATE] We have found several other news and media sites (Russian, Bulgarian, Japanese, and others) that were compromised, leading users to a fake Flash Player installer payload.
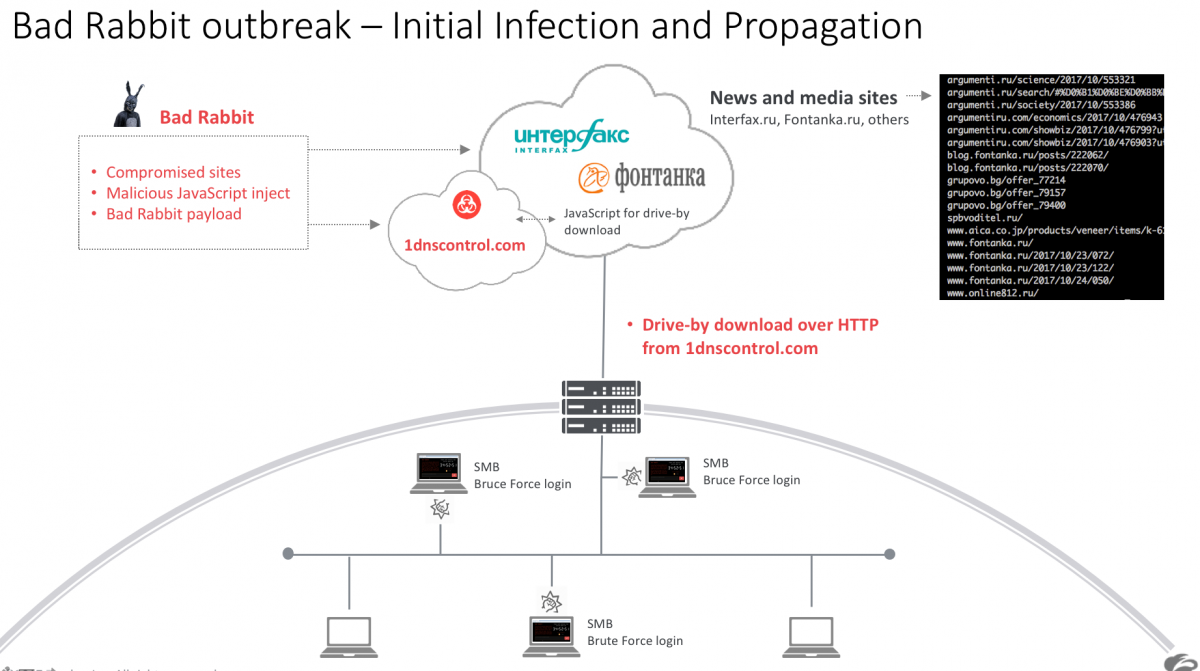
Figure 1 - Bad Rabbit outbreak overview
Bad Rabbit ransomware analysis
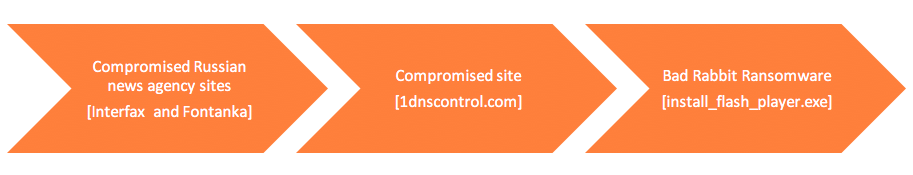
Figure 2 - Infection cycle [UPDATE: multiple other compromised Russian news and media sites were also part of this campaign]
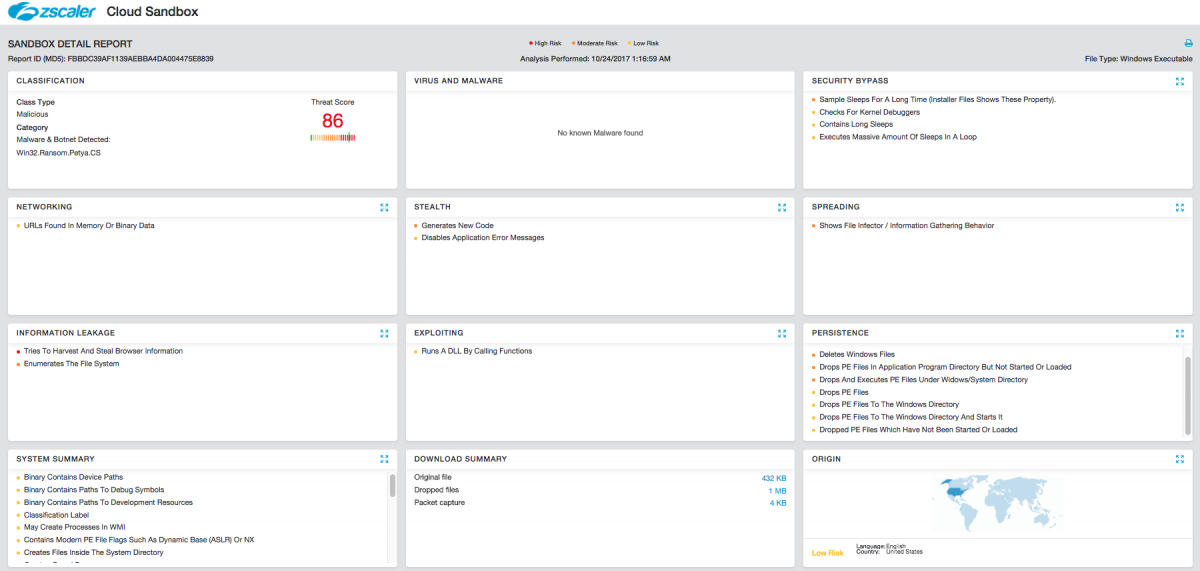
We saw multiple instances from this outbreak in the Zscaler cloud, and the new ransomware payload was flagged as malicious by the Zscaler Cloud Sandbox module. For this blog, we will analyze the attack cycle where the user was redirected from the fontanka[.]ru news site to another compromised site, as shown in Figure 2, which serves the ransomware executable payload.
Users visiting one of the compromised sites (on the day of outbreak) were prompted by a Flash update screen as shown below:
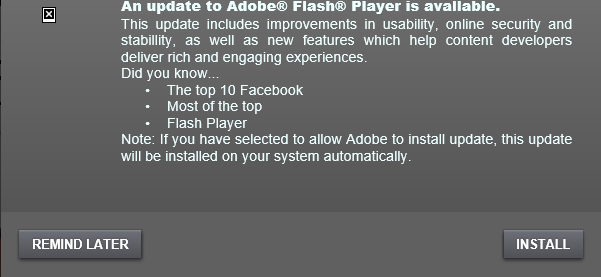
Figure 3 - Fake Adobe Flash Player update prompt
Once a user clicks the INSTALL button, the ransomware executable will be downloaded on the victim's machine. The payload will masquerade as Adobe Flash Player setup using the Adobe Flash installer icon, as shown below:
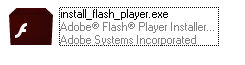
Figure 4 - Executable using fake icon
The executable payload is also signed using a fake certificate as shown below:
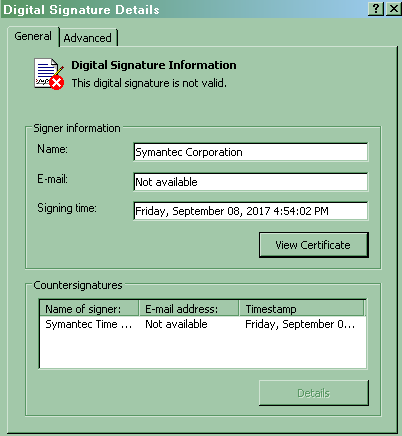
Figure 5 - Fake Symantec-issued certificate [NOT A LEGITIMATE CERTIFICATE]
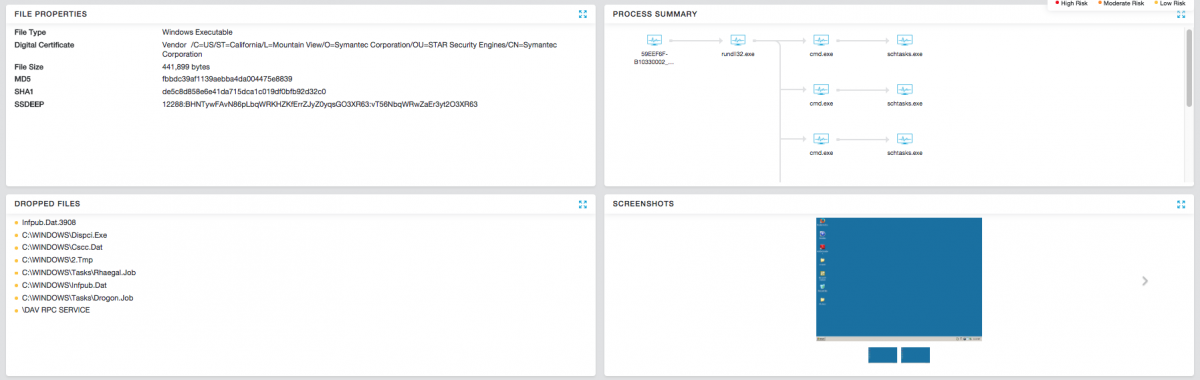
The fake Flash Player installer drops the main payload DLL file as "infpub.dat" in the Windows directory and executes it with the following arguments:
“C:\windows\system32\rundll32.exe c:\windows\infpub.dat,#1 15”
File Encryption
Infpub.dat is responsible for enumerating files on the infected system and encrypting any files that contain the following extension:
Figure 6 - File extensions targeted by Bad Rabbit
Bad Rabbit ransomware leverages AES encryption and uses CryptEncryptA API to encrypt the files on the infected machine. Unlike many other ransomware families, Bad Rabbit does not change the extension of the encrypted files; instead, the ransomware payload relies on a unicode string marker – "encrypted" – that is appended at the end of all the files that are encrypted.
Figure 7 - Encrypted file marker
Lateral movement
The ransomware contains a list of commonly used username and passwords embedded in the payload. The payload will scan the internal network for any reachable SMB shares and will perform brute force authentication using the stored credentials.
Figure 8 - Bad Rabbit embedded username and password list
Figure 9 - Brute Force login attempts to spread laterally
Upon successful infection, the system will reboot and the end user will see the dreadful ransom screen:
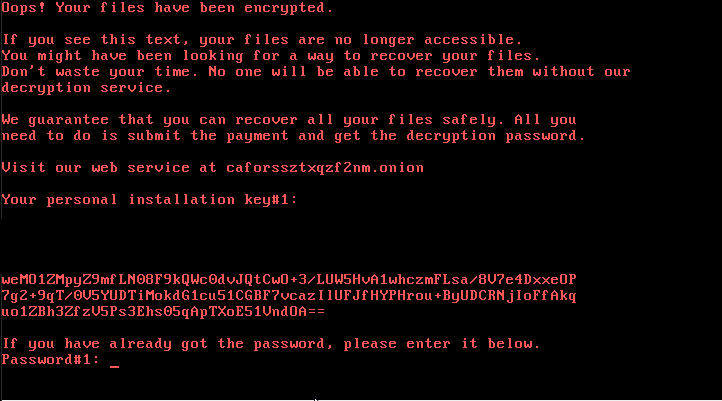
Figure 10 - Bad Rabbit ransom note
The onion site requests the user's personal installation key, so the user may receive the ransom amount and further instructions:
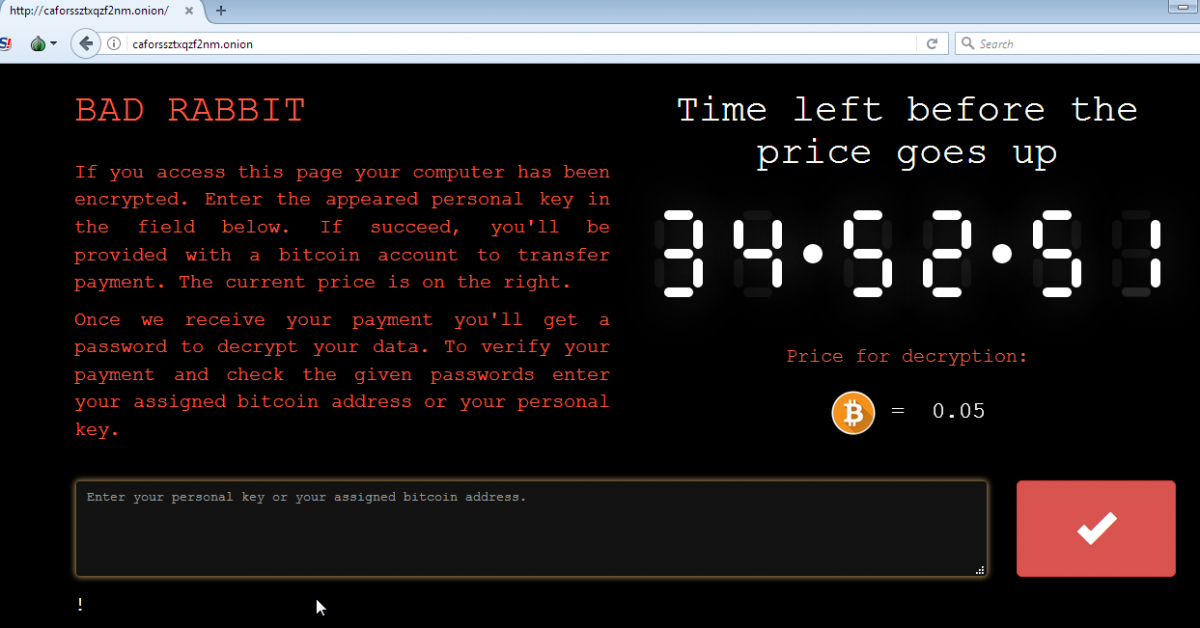
Figure 11 - Onion site for ransom payment instructions
Zscaler ThreatLabZ is actively monitoring this threat and will continue to ensure coverage for Zscaler customers. We will continue to update this blog with additional information as we further analyze the payloads.
Indicators of Compromise
MD5 hashes
fbbdc39af1139aebba4da004475e8839
b14d8faf7f0cbcfad051cefe5f39645f (dropped file)
Compromised intermediate site
1dnscontrol[.]com
Zscaler Coverage
Advanced Threat Signatures
- Malurl.Gen.XO
- mal/generic-s.z
- win32.ransom.diskcoder
Cloud Sandbox report