In almost every enterprise, mobile and cloud represent a large and growing proportion of overall traffic. While they offer many advantages in productivity, they also bring about new challenges for organizations trying to simplify their infrastructures while maintaining critical security controls.
The growing number of mobile devices, and the vast marketplace for self-serve apps, has opened the door to data loss and security breaches. In this blog, we will highlight some of the trends we’ve seen in the Zscaler cloud, particularly as they pertain to mobile privacy and data leakage.
The report's highlights can be viewed in our infographic. For more details, continue reading below.
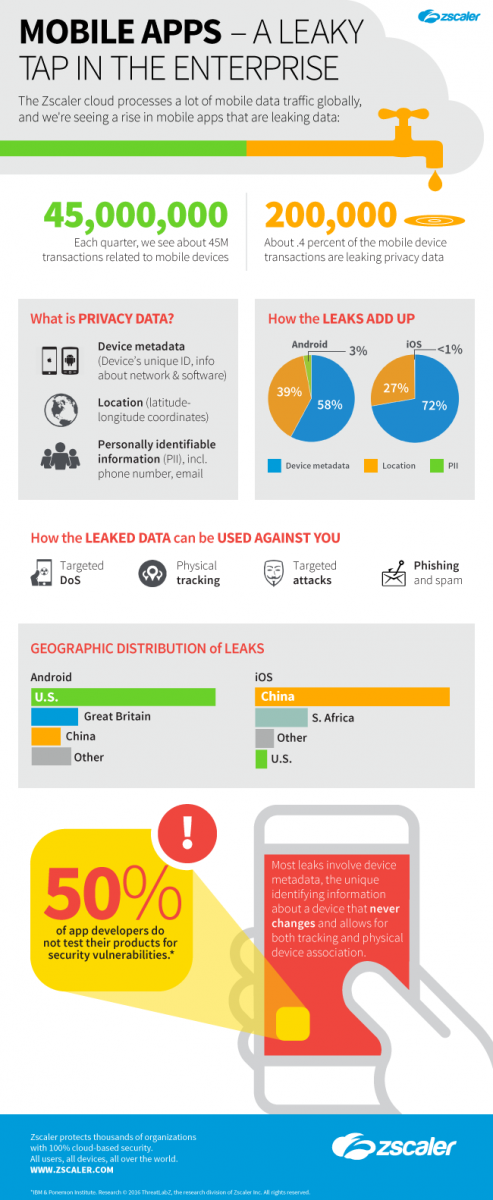
Each quarter, we see more than 45 million transactions related to mobile devices going through our cloud. The majority of the privacy-related information we see falls into one of three categories:
- Device metadata
- Location
- Personally identifiable information (PII)
Android devices
Android devices comprise around 20 million of the transactions we see, in which approximately 0.3 percent are resulting in some level of privacy leakage.
 Android privacy traffic
Android privacy traffic
The following graph details the leakage of privacy-related data of the Android platform.
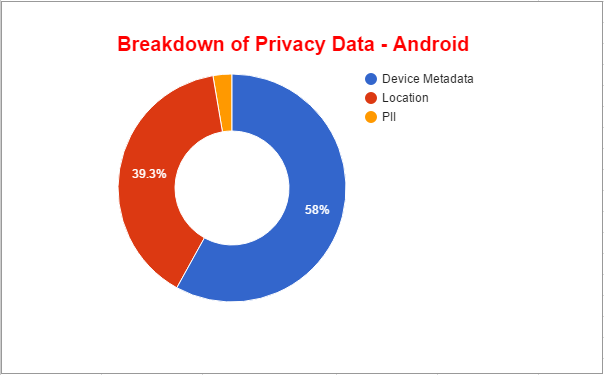
Breakdown of privacy data - Android
Breakdown of privacy data – Android
Of all the leaks, 58 percent are related to device metadata leakage, in which apps are sending identifying information, such as IMEI, MAC, IMSI numbers, Network, OS, SIM card information, manufacturer etc to their servers or ad-servers in clear text. Such data can be leveraged for tracking the device and creating targeted attacks.
Another high percentage of leaks — 39.3 percent — are related to the user’s location, including exact latitude and longitude coordinates.
The remaining three percent of transactions result in PII leakages, including the user’s mobile number and email addresses.
One percent of privacy leakages are observed from malicious transactions, and the rest are related to Android app usage.
The geographic distribution of Android traffic that is leaking data is shown in the following graph.
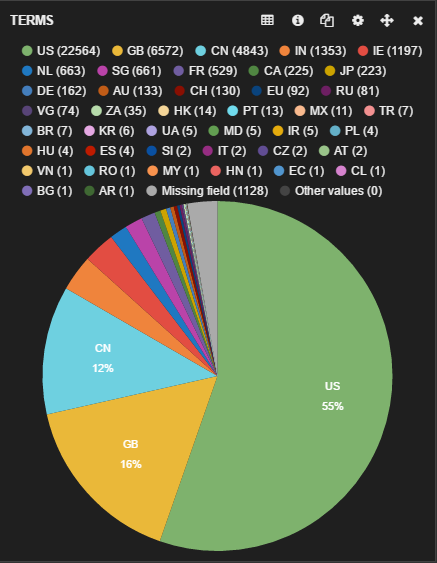
Geographic distribution - Android
iOS devices
In iOS, we see approximately 26 million transactions quarterly through our cloud, and 0.5 percent result in privacy-related information being sent.
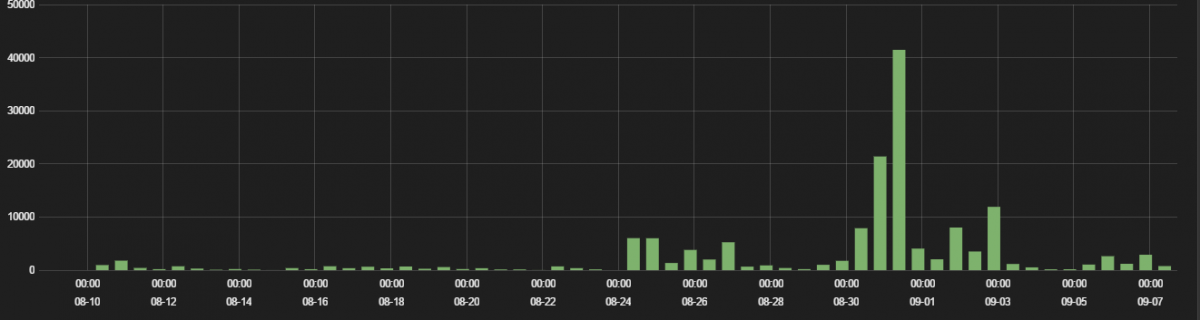
iOS privacy traffic
The following is a breakdown of privacy data being leaked on the iOS platform.
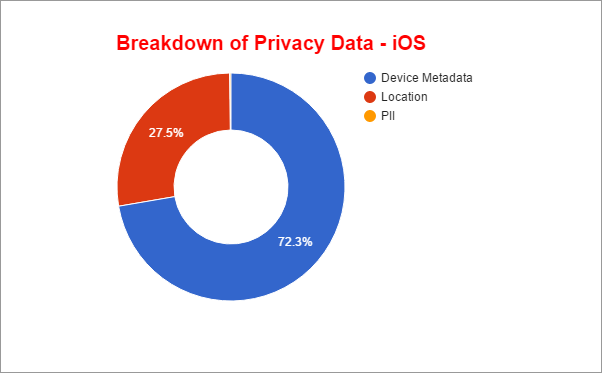
Breakdown of privacy data - iOS
Breakdown of privacy data – iOS
Of all iOS transactions that result in privacy-related information being sent, 72.3 percent of the transactions are related to the user's device information.
An additional 27.5 percent of transactions are resulting in the user's location being sent, and 0.2 percent of transactions result in sending PII-related information.
Of all the transactions in which privacy-related information is being sent, five percent of them are the result of malicious infections.
The geographic distribution for iOS privacy-related traffic is shown below.
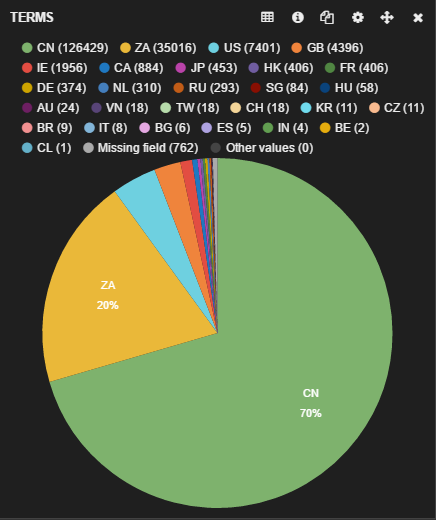
Geographic distribution - iOS
The potential for long-term threats
These statistics demonstrate that significant amounts of personal data can be leaked simply by tapping into any organization’s traffic; in our cloud alone we saw nearly 200,000 examples of such leaks. All that leaking data can be leveraged for more sophisticated attacks.
Because hardware identifiers like MAC, GSM IMEI, IMSI, and UDID are globally unique and do not change over the lifetime of a device, the collection of such IDs allows for both tracking and physical device association. These identifiers can be exploited by a range of attacks, from mobile privacy to targeted denial-of-service; for example, a GSM air interface attack where the attacker must first know the IMEI of the intended victim, a remote SMS denial-of-service attack, or remote SIM card rooting, among others.
The exact location of any person is highly valuable in this global era, where lots of spying and spoofing are done; such information can lead to mass compromisation and/or targeted attacks. Phone numbers and email addresses are the quickest way to reach any individual, and can be leveraged for spamming and phishing attacks.
Don’t count on the developers to protect you
A study by IBM & The Ponemon Institute shows that, of the 400 organizations studied, almost 40 percent do not scan the apps they develop for security vulnerabilities. Of those that do scan their apps before releasing them to market, only 15 percent test them as frequently as they should. And, even more worrisome, 50 percent of those that develop mobile apps do not allocate any budget at all to testing for security vulnerabilities.

BYOD and the self-serve application market quickly became mainstream and are now deeply rooted in organizations. But observing the leakage from these apps — and the developers’ minimal security investments — means that organizations must take steps to protect their users and the broader network infrastructure and data assets. They should be applying strict MDM policies and educating employees about app security in an effort to stave off any kind of data loss or security breach.