Blog Zscaler
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Iscriviti
Android and Windows RATs Distributed Via Online Meeting Lures
Introduction
Beginning in December 2023, Zscaler’s ThreatLabz discovered a threat actor creating fraudulent Skype, Google Meet, and Zoom websites to spread malware. The threat actor spreads SpyNote RAT to Android users and NjRAT and DCRat to Windows users. This article describes and shows how the threat actor’s malicious URLs and files can be identified on these fraudulent online meeting websites.
Key Takeaways
- A threat actor is distributing multiple malware families using fake Skype, Zoom, and Google Meet websites.
- The threat actor is distributing Remote Access Trojans (RATs) including SpyNote RAT for Android platforms, and NjRAT and DCRat for Windows systems.
Campaign Overview
The attacker utilized shared web hosting, hosting all these fake online meeting sites on a single IP address. All of the fake sites were in Russian as shown in all the figures below. In addition, the attackers hosted these fake sites using URLs that closely resembled the actual websites.
Attack Sequence
The diagram below illustrates how the malware was distributed and executed on the victim's machine during the campaign:
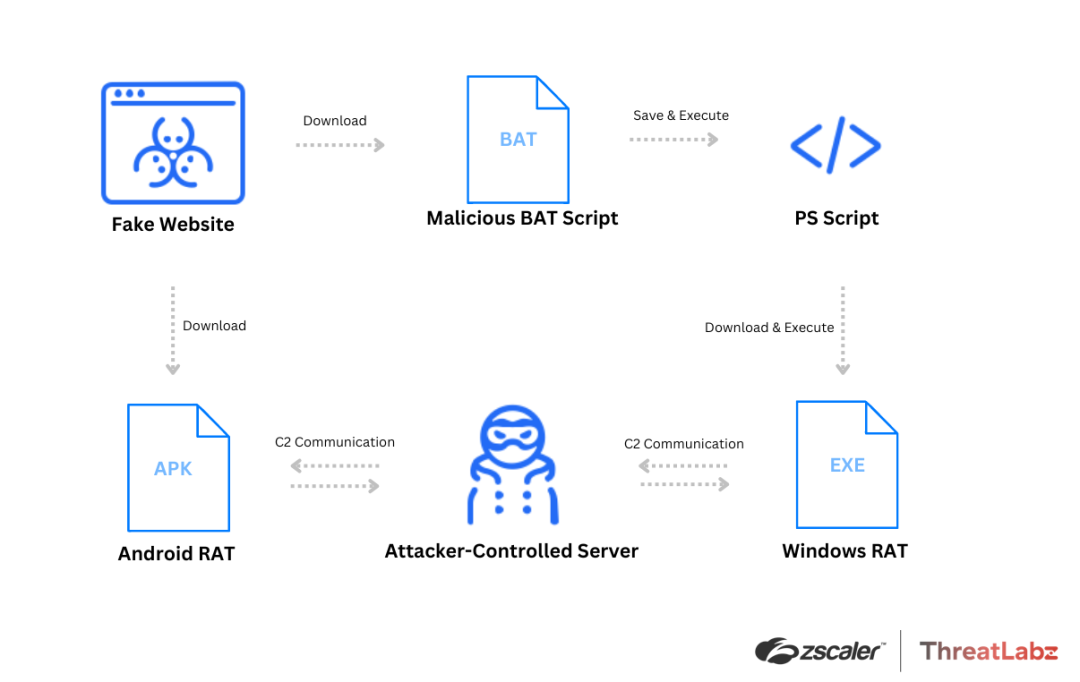
Figure 1: Attack chain and execution flow for Android and Windows campaigns.
When a user visits one of the fake sites, clicking on the Android button initiates the download of a malicious APK file, while clicking on the Windows button triggers the download of a BAT file. The BAT file when executed performs additional actions, ultimately leading to the download of a RAT payload.
Skype
During our investigation, we discovered that the first fake site, join-skype[.]info, was created in early December to deceive users into downloading a fake Skype application as shown in Figure 2.
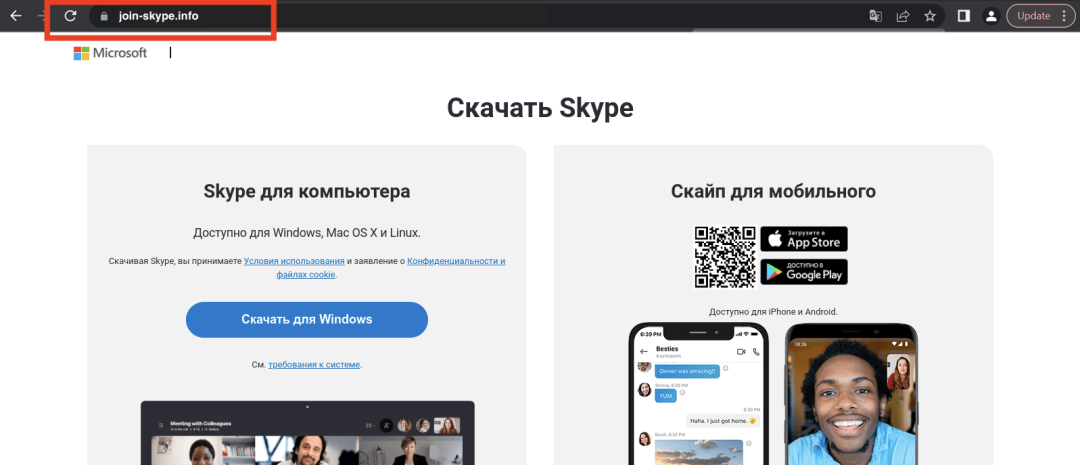
Figure 2: The fraudulent Skype website, with a fake domain meant to resemble the legitimate Skype domain. (Image courtesy of urlscan.io.)
The Windows button pointed to a file named Skype8.exe and the Google Play button pointed at Skype.apk (neither of these files was available at the time of analysis). The Apple App Store button redirected to https://go.skype.com/skype.download.for.phone.iphone, indicating that the threat actor was not targeting iOS users with malware.
Google Meet
In late December, the attacker created another fake site, online-cloudmeeting[.]pro, mimicking Google Meet as shown in Figure 3. The fake Google Meet site was hosted on online-cloudmeeting[.]pro/gry-ucdu-fhc/ where the subpath gry-ucdu-fhc was deliberately created to resemble a Google Meet joining link. Genuine Google Meet invite codes typically follow the structure [a-z]{3}-[a-z]{4}-[a-z]{3}.
The fake site provides links to download a fake Skype application for Android and/or Windows. The Windows link leads to a BAT file named updateZoom20243001bit.bat, which in turn downloads the final payload named ZoomDirectUpdate.exe. This final payload is a WinRAR archive file that contains DCRat, packed with Eziriz .NET Reactor.
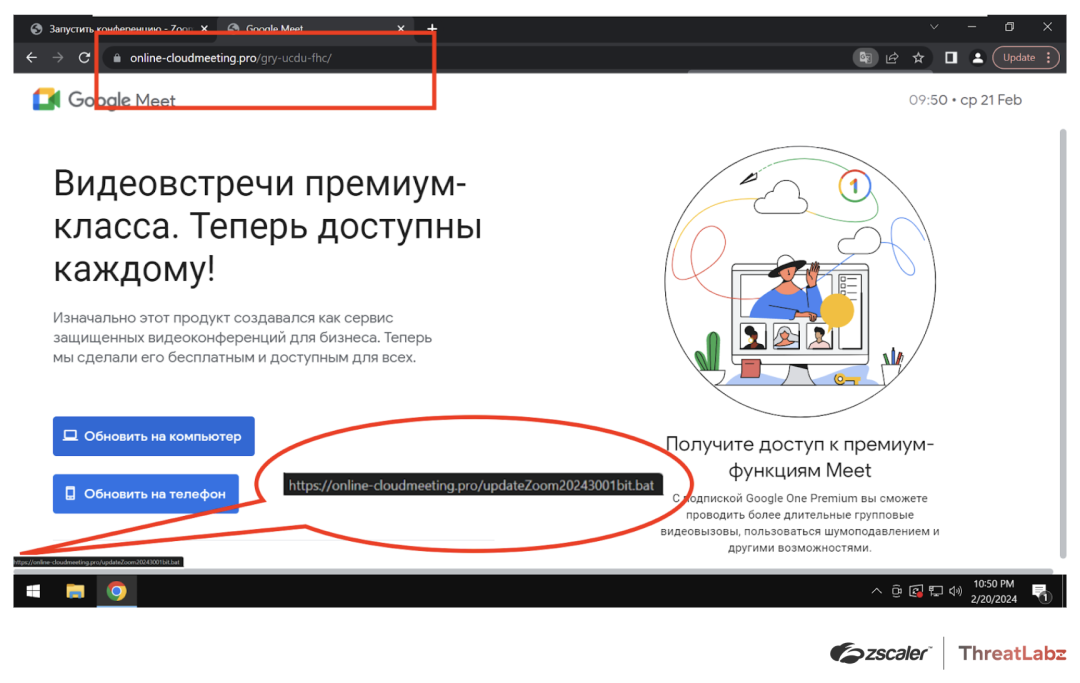
Figure 3: The fake Google Meet page, showing the fraudulent domain in the address bar for a fake Google Meet Windows application link to a malicious BAT file that downloads and executes malware.
The Android link in this figure led to a SpyNote RAT APK file named meet.apk.
Zoom
In late January, we observed the emergence of a fake Zoom site (shown in Figure 4), us06webzoomus[.]pro. The fake Zoom site, hosted at the URL us06webzoomus[.]pro/l/62202342233720Yzhkb3dHQXczZG1XS1Z3Sk9kenpkZz09/, features a subpath that closely resembles a meeting ID generated by the Zoom client. If a user clicks the Google Play link, a file named Zoom02.apk will be downloaded containing the SpyNote RAT. Similar to the fake Google Meet site, when a user clicks the Windows button it downloads a BAT file, which in turn downloads a DCRat payload.
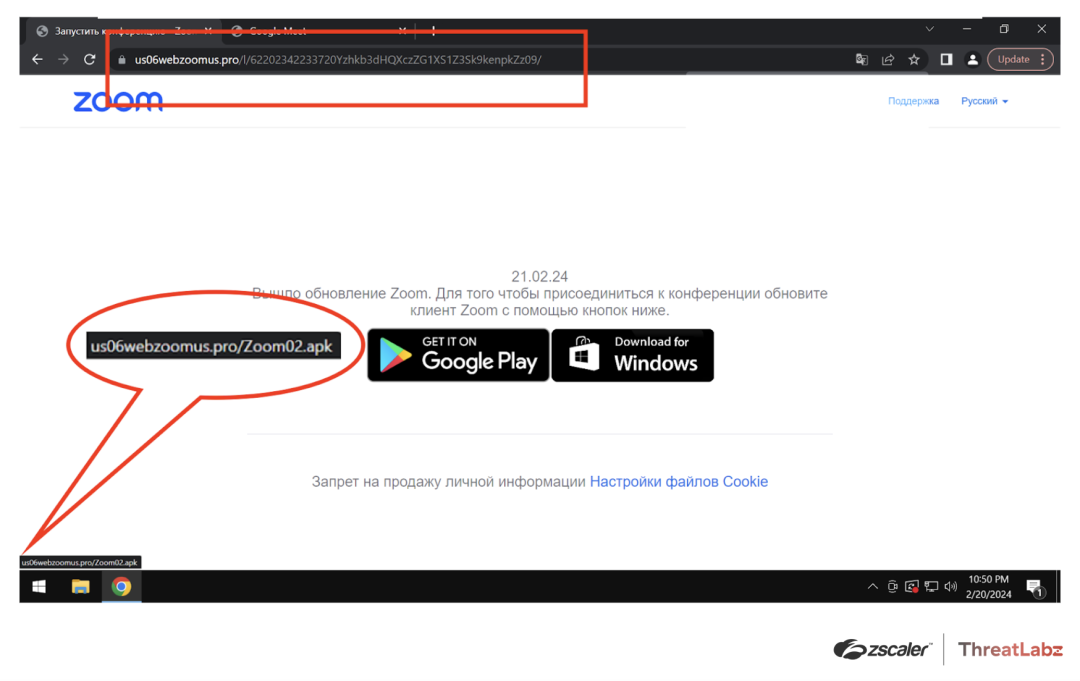
Figure 4: The fake Zoom page, showing a domain similar to the real Zoom domain in the address bar and a link to the malicious APK file that contains SpyNote RAT when the Google Play button is clicked.
Open Directories
In addition to hosting DCRat, the fake Google Meet and Zoom websites also contain an open directory (shown in Figure 5) with two additional Windows executable files named driver.exe and meet.exe (inside the archive gry-ucdu-fhc.zip), which are NjRAT. The presence of these files suggests that the attacker may utilize them in other campaigns, given their distinct names.
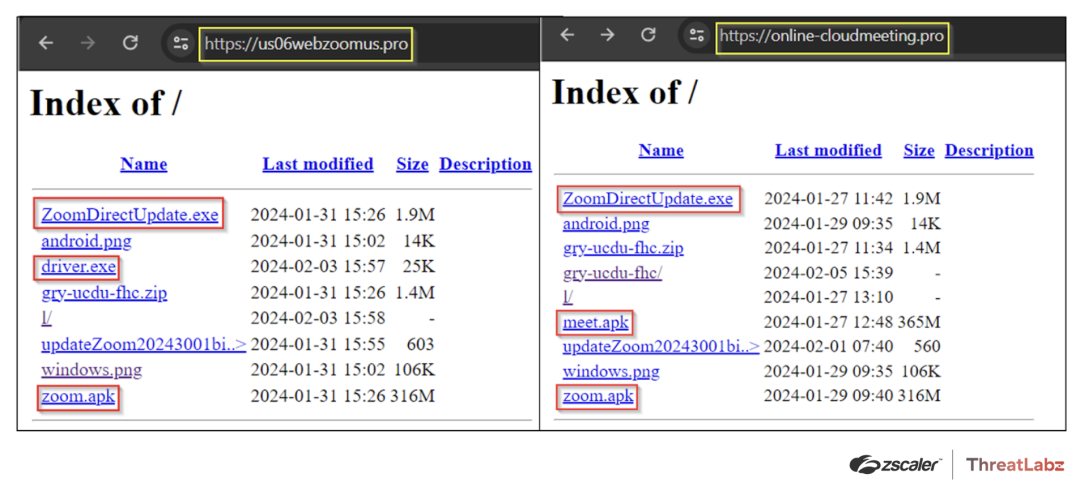
Figure 5: Example of additional malicious files hosted on the websites hosting fake online meeting applications.
Conclusion
Our research demonstrates that businesses may be subject to threats that impersonate online meeting applications. In this example, a threat actor is using these lures to distribute RATs for Android and Windows, which can steal confidential information, log keystrokes, and steal files. Our findings highlight the need for robust security measures to protect against advanced and evolving malware threats and the importance of regular updates and security patches.
As cyber threats continue to evolve and become increasingly complex, it is critical to remain alert and take proactive measures to protect against them. Zscaler's ThreatLabz team is dedicated to staying on top of these threats and sharing our findings with the wider community.
Zscaler Sandbox Coverage
During our investigation of this campaign, the Zscaler sandbox played a vital role in analyzing the behavior of different files. The sandbox analysis allowed us to identify threat scores and pinpoint specific MITRE ATT&CK techniques that were triggered during the analysis process.
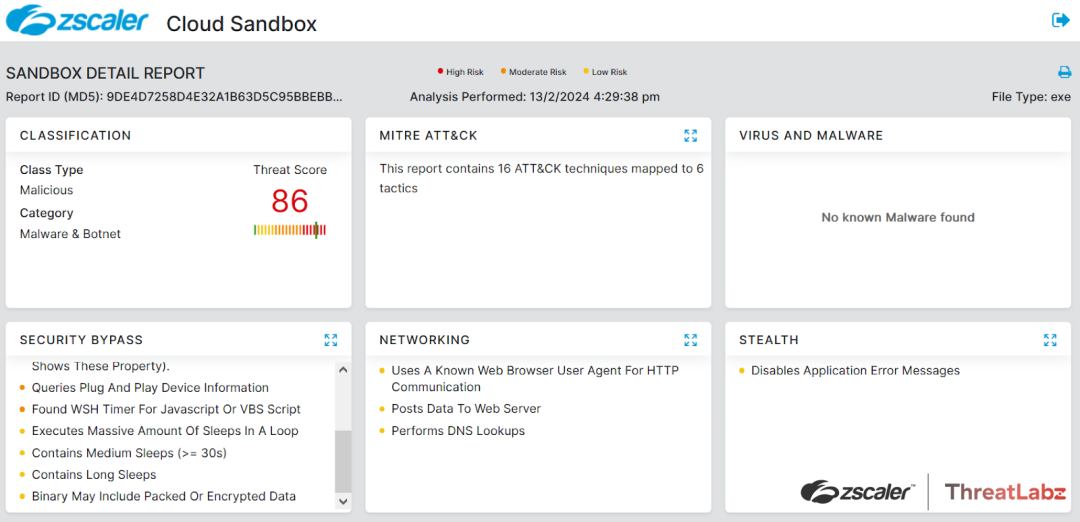
Figure 6: DCRat Zscaler sandbox report
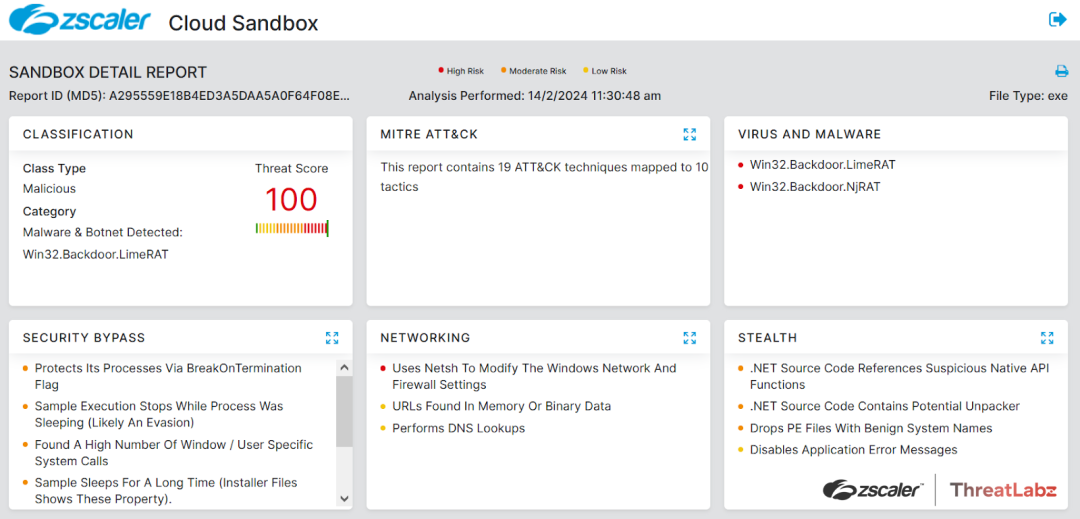
Figure 7: NjRAT Zscaler sandbox report
Zscaler’s multilayered cloud security platform detected payloads with the following threat names:
MITRE ATT&CK Techniques
Enterprise Matrix
Mobile Matrix
Questo post è stato utile?
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Inviando il modulo, si accetta la nostra Informativa sulla privacy.



