Developing an app that is downloaded millions of times means success for the developer. But, quite often, it also means the app becomes a target for cybercriminals.
This is the case with the wildly popular game Among Us. The game has been downloaded more than 100 million times from the Google Play store, so it’s not surprising that the Zscaler ThreatLabZ team has discovered a fake app portraying itself as Among Us, attempting to cash in on the real game’s popularity.
The fake app is titled Amoungus. It cleverly makes a minor spelling change to the name and uses a picture similar to the one in the real app (shown in Figure 1). Users who are not very familiar with the app but have heard about it can be fooled into thinking this is the actual game. Once installed, Amoungus displays some fake downloading and processing activities, leading the user to think the game is downloading additional features required for an Android device.
Soon after downloading the app, the user is bombarded with advertisements. There is no gaming functionality; the app is simply adware with the potential functionality to steal Gmail credentials.
The app asks users to log in or register using Gmail credentials, but the current version does not send the credentials to the attacker. This functionality seems to be under development and could be activated with future updates. Such functionality could be devastating, providing attackers with access to volumes of personal and financial information.
App details
App Name: Amoungus
Package Name: amoungus.among.us.free.online.game
Hash: 3d1e6b84b50e9dbcfdc6b609aa57d28fa06f78e1f3cd9285e07ba8e39f419bfb
Technical details
The app portrays itself as the Among Us Android game app. [Disclaimer: This blog will be discussing the technical details of the fake app Amoungus, discovered on the Google Play store, not the real Among Us app.]
As shown in Figure 1, the left image is of the actual game (which has around 100 million downloads), and the right is the fake app.
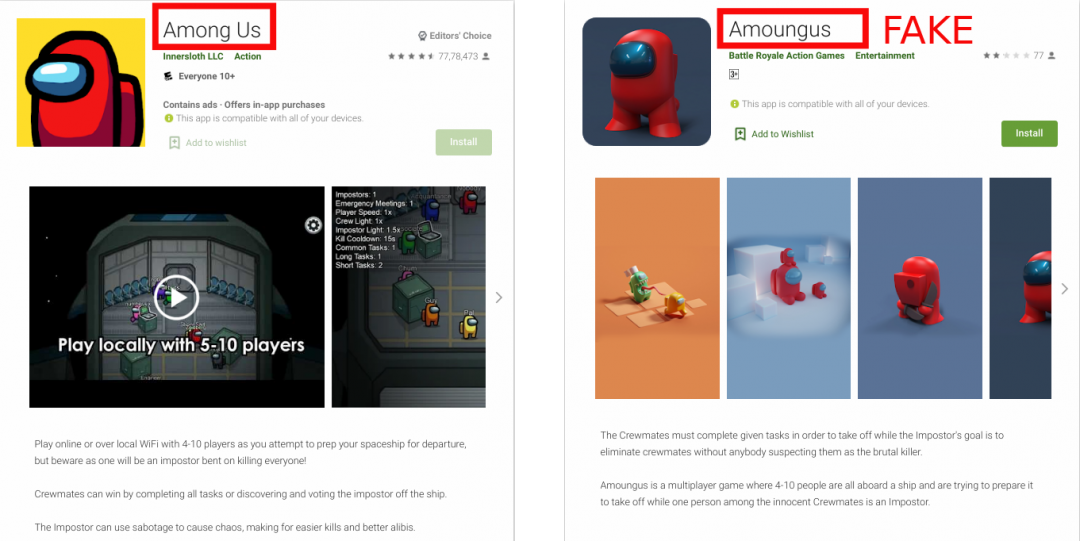 |
| Figure 1: The real Among Us vs. the fake app on Google Play. |
When checking the user reviews for the fake app, it becomes pretty obvious that the app is not doing what is described on the Google Play description page.
Figure 2 shows some user reviews, which clearly indicate that this is a potentially unwanted app (PUA).
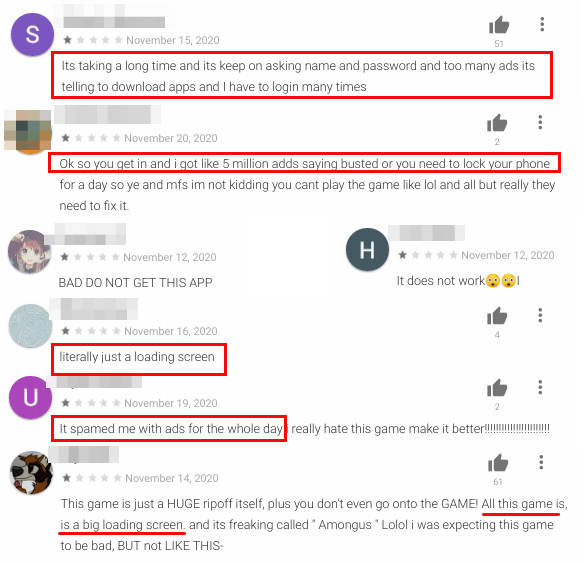 |
| Figure 2: User reviews for the Amoungus app on Google Play. |
Upon installation, the app appears to be downloading additional game features, as well as loading and processing those features. This is a common activity in other games, such as PUBG, Call Of Duty, Asphalt, and more, in which the game loads additional features from the server to enhance gameplay or improve functionality. This activity tricks the user into thinking this app is an actual game. Figure 3 shows this functionality in action.
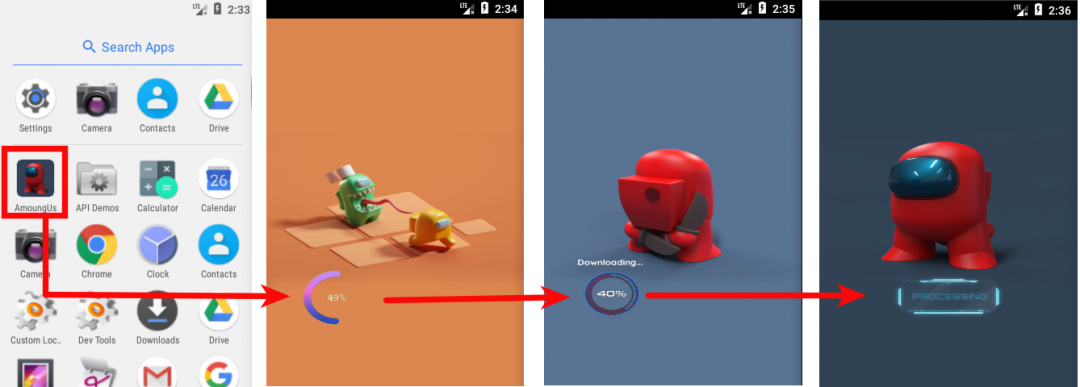 |
| Figure 3: The initial downloading and processing activities of the Amoungus app. |
In reality, these are nothing more than videos created by the attacker to mimic game functionality.
Figure 4 shows how this functionality is used and how the videos are loaded from the Resources directory.
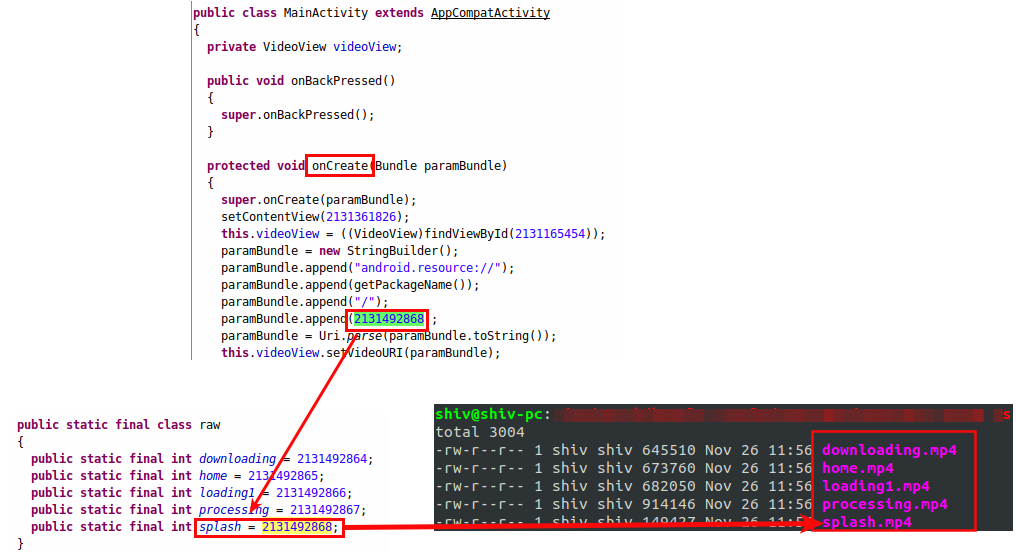 |
| Figure 4: The videos for this fake app are stored in the Resources directory. |
The app also sends details about the user's device to the server. Some of the details include:
- Android SDK version
- Android model
- Network operator name
- Device manufacturer
- Cell signal level
- Height and width of the Android display
- Device root details
- Time since last boot
- Device RAM status
The user is then bombarded with advertisements, as seen in Figure 5.
 |
| Figure 5: Some of the ads sent to the victim. |
One unique feature of this app is the functionality to steal Gmail credentials. The app asks the user to log in or register using a Gmail user name and password, although the stolen credentials are not sent back to the attacker. This functionality seems to be under development and hypothetically could be an ideal way to thwart Google Play's detection, as the current version of the app doesn't steal data, but later updates might include this functionality.
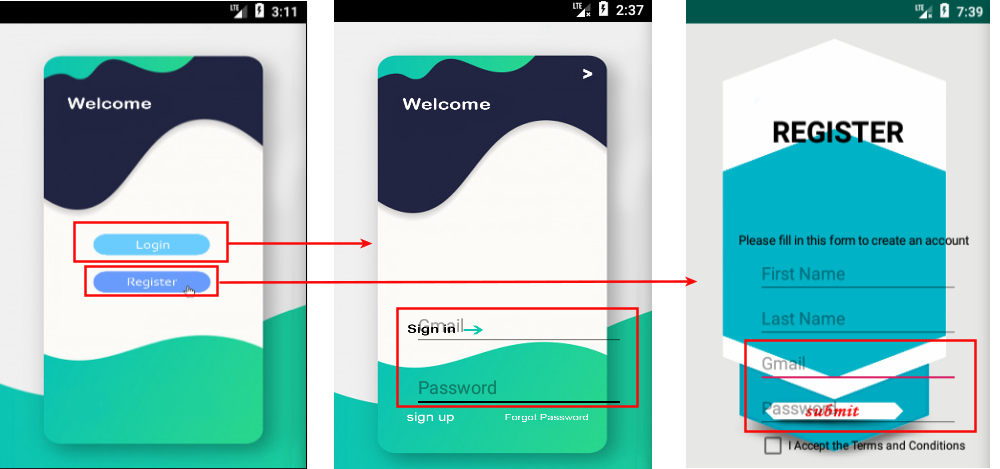 |
| Figure 6: The login and register screens of the fake app. |
When trying to log in or register, the user is reverted to the login page on a continuous loop.
Figure 7 shows the functionality where the user is looped around the same process once a user name and password are provided.
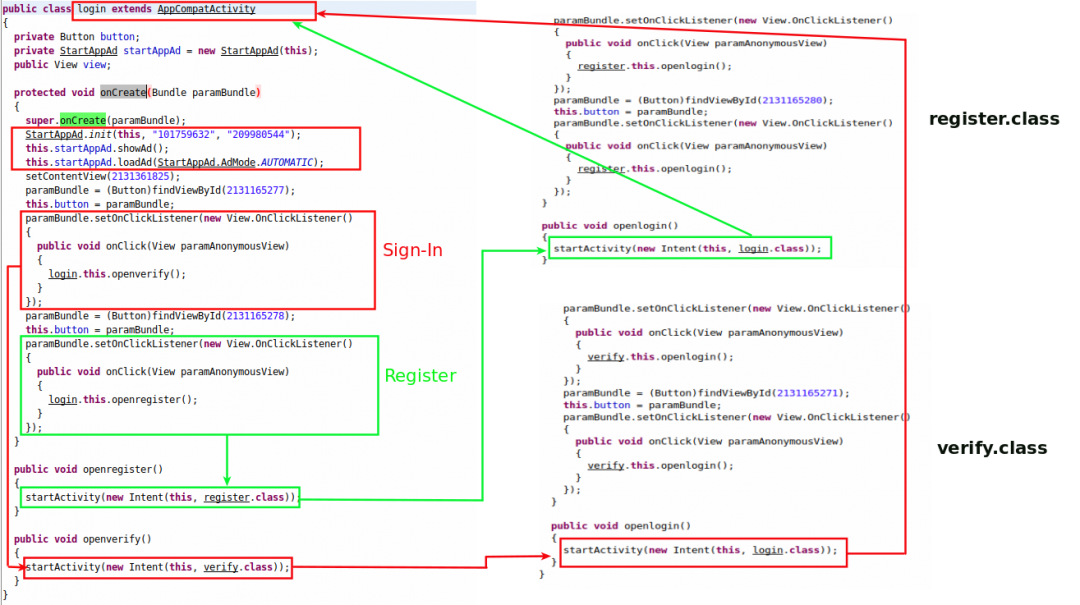 |
| Figure 7: The login or register functionality on a continuous loop. |
Further research showed that the developer had other fake apps on Google Play mimicking other famous apps. We analyzed the other fake apps and found that they all behaved in the same fashion as the fake Among Us app. Initially, videos are played showing the downloading and processing activity, and the user is bombarded with ads along with Gmail ID and password prompts, which again are sent nowhere.
Figure 8 shows other apps from the same developer.
 |
| Figure 8: Other fake apps on Google Play by the developer of Amoungus. |
Listed below are the names of the fake apps shown in Figure 8 with their approximate numbers of downloads.
- Fauji Game:10,000+
- Lite for Resident Evil: 10,000+
- Like for Call of Fire: 50+
- Amoungus: 5,000+
- Fdnmg: 1+
- Betok Indian Short Videos: 10+
- Clash of Coins: 10+
- Battle Royale Action Game: 5,000+
Based on the game names, the developer(s) seem to be targeting Indian users.
Fauji is a battle royale game that is supposed to launch in India as an alternative to PUBG.
Another app is named Betok Indian Short Videos with an icon similar to TikTok.
Fdnmg appears to be in the very early stages of development. Looking at the package name, the developer seems to be targeting this app as a fake PUBG-related app, as shown in Figure 9.
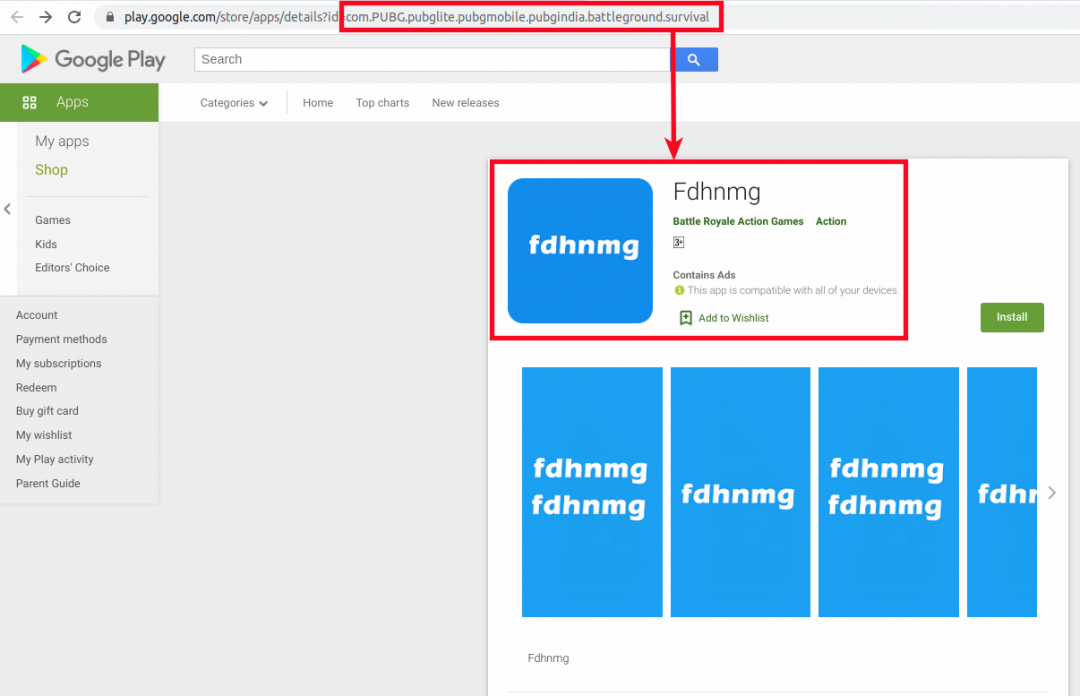 |
| Figure 9: This fake app appears to be in the very early development stage. |
Again, this app is no different than the other fake apps. It flashes videos and soon asks for a Gmail ID and password, while bombarding the victim with ads.
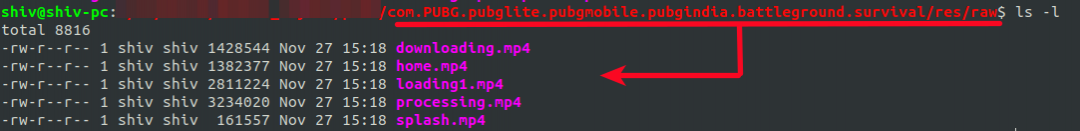 |
| Figure 10: As with the other fake apps, the videos are stored in the Registry directory. |
Similar to the other fake apps, this app does not send the Gmail credentials anywhere. But this functionality is likely under development, and the next update might actually steal the credentials.
We have reported these apps, and Google's android security team promptly removed them from the Google Play store.
Conclusion
Despite Google's diligent efforts, miscreants still manage to plunge potentially unwanted apps (PUAs) onto Google's official Android store, Google Play. While Google tries its best to protect Android users worldwide, it is also the responsibility of Android users to be vigilent when installing apps.
We advise users to download and install Android apps from official stores, such as Google Play. But there can be scenarios where PUAs enter into official stores.
To help avoid downloading PUAs:
- Be sure to read user reviews before installing any app.
- Do not simply allow any random permissions that an app may demand. For example, it makes no sense for a calculator app to ask for the "READ_SMS" permission
- Always disable the "Unknown Sources" option so that any random app cannot further install apps from third-party sources.
- If an app does not act as described, immediately uninstall it and report the app to Google.






