Update 05/04/11 @ 7.49pm IST: Thanks to feedback from an Anonymous blog poster, I've done some further investigation and this attack actually appears to be tied to the Incognito Exploit kit as opposed to the Blackhole Exploit kit.
Back in February, I posted a blog about the rising prevalence of attacks involving Blackhole exploit kits. We received numerous comments and emails about the same threat being found on various websites from our blog readers. The toolkit has been linked to from numerous compromised websites, which in turn have victimized a number of their visitors. Attackers are injecting malicious iframes into the legitimate sites, which in turn redirect to malicious websites hosting the
Blackhole Incognito exploit kit. We have observed and identified such compromised sites due to Zscaler’s advanced security features in our solution. The latest victim is Lenovo, India whose website for product warranties has been compromised, redirecting visitors silently to the
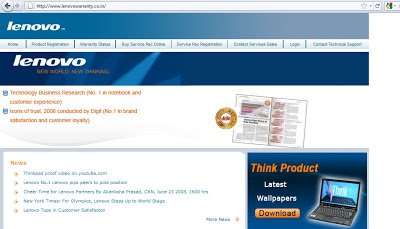
Blackhole Incognito exploit kit. Here is the screenshot of the home page of the compromised Lenovo site:
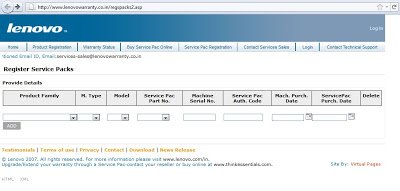
One of the pages on the site, http://www.lenovowarranty.co.in/regspacks2.asp, is infected with a malicious iframe. Here is the screenshot of that page:
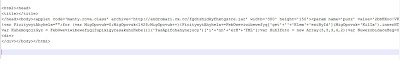
If you look at the source of page, you will find the malicious iframe injected into the source code as shown below:
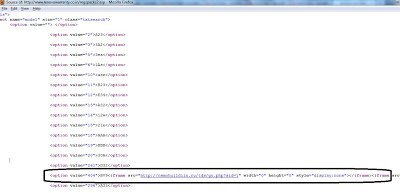
The malicious iframe points to the site “hxxp://nemohuildiin.ru/tds/go.php?sid=1". This malicious site actually redirects the user to another malicious website hosting the
Blackhole Incognito exploit kit. Here is the packet capture when you visit the mentioned malicious site:
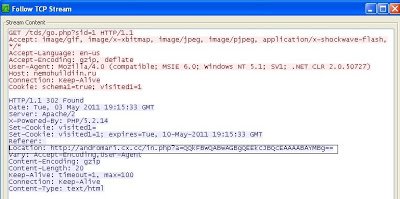
Observing the “Location” field in the HTTP header, we see the user is being redirected to another malicious website hosting the malicious toolkit, a common pattern that we’ve seen in the past. The malicious website “hxxp://andromari.cx.cc” returns obfuscated malicious JavaScript code to exploit different vulnerabilities and downloads malicious binaries. Here is the screenshot of the malicious JavaScript sent by this kit
I am not going into the details of the exploits themselves as they are related to the same vulnerabilities and toolkit, which I have discussed in an
earlier blog. The malicious site hosting the
Blackhole Incognito exploit kit only attempts to exploit the victim on their first visit. If you revisit this site, it will either redirect you to Google or simply return a “Page not found” error.
This post further supports my claim in an earlier blog, which states that “Blackhole exploit kits are rising”.
Blackhole is Exploit kits are definitely a
Bad Hole bad for web security.
Umesh
 If you look at the source of page, you will find the malicious iframe injected into the source code as shown below:
If you look at the source of page, you will find the malicious iframe injected into the source code as shown below:
 Observing the “Location” field in the HTTP header, we see the user is being redirected to another malicious website hosting the malicious toolkit, a common pattern that we’ve seen in the past. The malicious website “hxxp://andromari.cx.cc” returns obfuscated malicious JavaScript code to exploit different vulnerabilities and downloads malicious binaries. Here is the screenshot of the malicious JavaScript sent by this kit
Observing the “Location” field in the HTTP header, we see the user is being redirected to another malicious website hosting the malicious toolkit, a common pattern that we’ve seen in the past. The malicious website “hxxp://andromari.cx.cc” returns obfuscated malicious JavaScript code to exploit different vulnerabilities and downloads malicious binaries. Here is the screenshot of the malicious JavaScript sent by this kit I am not going into the details of the exploits themselves as they are related to the same vulnerabilities and toolkit, which I have discussed in an earlier blog. The malicious site hosting the
I am not going into the details of the exploits themselves as they are related to the same vulnerabilities and toolkit, which I have discussed in an earlier blog. The malicious site hosting the 




