Attacks are on the rise for K-12 schools which begs the question: How safe is your school against cyberthreats?
A growing and persistent problem for K-12 schools, Zscaler’s research has seen an alarming increase in the rate of cybersecurity incidents in the education sector:
- Encrypted Attacks - 315% rise in encrypted attacks with 207 million attacks targeted at educational institutions. Attackers are constantly using encrypted traffic to not only hide their exploits but they’re also using encrypted channels to get data whether that’s student data or school financial data.
- Ransomware - 80% rise in ransomware attacks with a 225% rise in double extortion targeted at education - a type of ransomware attack where not only does the attacker encrypt the data, but before they encrypt it and demand payment they steal and copy the data. Education is ranked the 9th most targeted industry for ransomware.
- Phishing - 47.4 million phishing attacks were targeted at education. Phishing is a common way for attackers to gain access for ransomware attacks. A better approach is needed to catch unknown and known phishing attacks using AI, as well as more training for network users to recognize cybersecurity threats.
Case study: Los Angeles Unified School District ransomware attack
Let’s look at a recent case study - the Los Angeles Unified School District (LAUSD) ransomware attack. In early October, Vice Society, a Russian-speaking group known for targeting schools and the education sector, claimed responsibility for a cyberattack against LAUSD.
- Second-largest US school district in the United States
- 600,000 students impacted
- 56% of K-12 schools report being hit by ransomware
- 45% of K-12 schools pay ransom
- Students were still able to go to school, but day-to-day operations slowed/halted
- Access to email, computer systems, and applications stopped to slow infection
The incident prompted a response from the White House, FBI, and Department of Homeland Security, demonstrating the commitment the United States has to keeping children safe at school, including their data.
Attack techniques and response strategies
Looking at common attack techniques, we can put together a picture of how these attacks are carried out as well as response strategies to prevent them.
From our perspective at Zscaler, based on data collected from our own threat researchers, product managers and engineers, every attack is relatively the same.The vast majority of attacks fall into a couple of buckets - particularly around ransomware - to get the attack executed, to move laterally, and then actually steal data.
With this framework we can go deeper into the LAUSD case study, reconstructing the attack techniques Vice Society most likely used and recommended response strategies as shown in Figure 1 below.
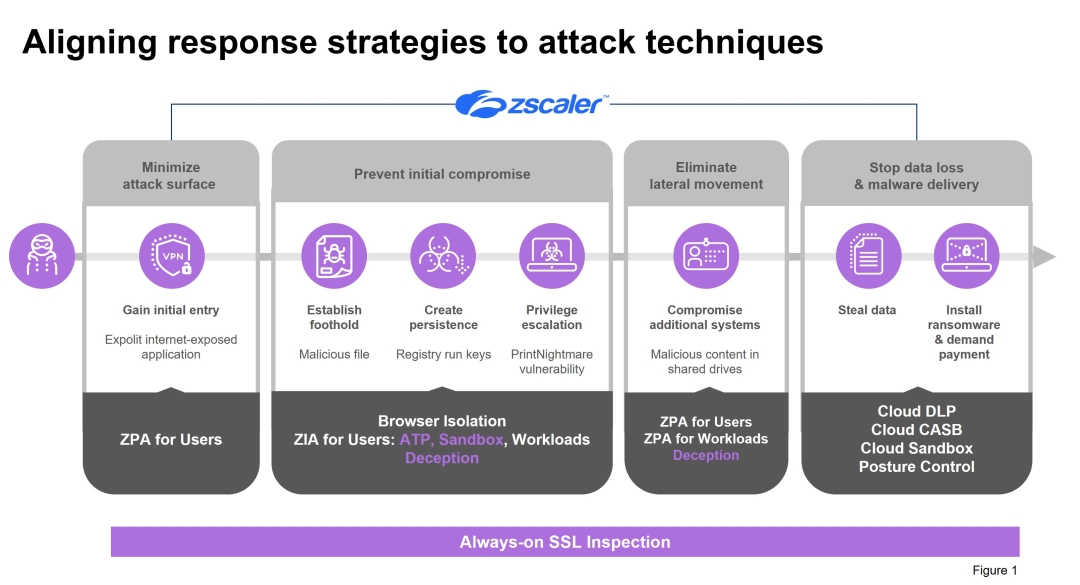
Attack technique: Gain initial entry
The attackers gain initial entry by finding and exploiting an internet-exposed application.
Response Strategy: Minimize attack surface
We often see SaaS applications or private applications hosted in a data center. Both are completely hidden behind our Zero Trust Exchange. Attackers can’t attack what they can’t see. When you put applications behind the exchange, attackers can not scan and see potential entry points through the internet. Even if they know what’s there and what to attack, they can’t find it because it’s hidden behind our exchange. Minimizing and reducing that attack surface from an application perspective is incredibly important. Zscaler Private Access (ZPA) and Zscaler Internet Access (ZIA) do this with browser isolation where a school can give access to your network in a read-only way and control functions such as copy, paste and screen shots.
Attack Technique: Establish foothold, create persistence, privilege escalation
Once attackers find an entry point, they want to compromise a single user for that application so they can get an initial foothold. In the case of Los Angeles Unified, the attacker group likely used malicious files to get that foothold. They then create persistence using registry run keys so whatever infected the user or machine will continue to infect the user over time so they don’t have to repeat the attack. Finally, the attacker needs to escalate their privileges so they can eventually move laterally. This attack group uses a PrintNightmare vulnerability to get access to other systems, setting up those privileges to move around the organization not only looking for data, but also starting to infect users, machines and systems along the way.
Response Strategy: Prevent initial compromise
We have several ways to stop compromise including our flagship Secure Web Gateway which has put us in Gartner's Magic Quadrant leadership for 10 years, and we are extremely excited to be designated a leader again in the most recent Security Service Edge (SSE) Magic Quadrant.
Attack Technique: Compromise additional systems
The goal with this technique is to compromise additional systems. In the case of ransomware, ransomware doesn’t work if only one user is affected. It needs to be widespread so it creates the kind of urgency for a school district to actually pay the ransom upfront quickly. In this case the attackers used malicious content like malicious files, but they put them in different shared drives, sending them to different users using legitimate credentials. As it continues to persist, there are more and more users, more and more systems infected and the ransomware attack can spread quickly.
Response Strategy: Eliminate lateral movement
Taking a platform approach using ZPA and Zscaler for workloads, we are hiding applications behind the exchange and making sure that if attackers do get a foothold somewhere or compromise a user, they are not able to actually look for and find applications to exploit. We also have very innovative deception technology integrated into the platform, essentially laying traps and lures like fake applications to not only get attackers to make the wrong move and go after a decoy, but you can actually watch them and see what they’re doing and see if you need to make any tweaks along the way.
Attack Technique: Steal data, install ransomware & demand payment
The goal for attackers is to get paid, but in the case of double ransomware attackers need to steal the data first and make a copy of it so they can use it as a second ransomware option.
Response Strategy: Stop data loss & malware delivery
DLP and CASB make sure you’re not being infected and the data is not being compromised in any way.
Preventing ransomware at every stage of the attack
Zscaler’s approach is to holistically prevent cyber attacks and data loss with zero trust and a full platform approach. This approach virtually guarantees defense against a ransomware attack or any resulting data loss. The net result of this approach to stopping advanced threats is significant. Zscaler customers have seen:
- 35X reduction in infected machines to protect users and secure connectivity with advanced risk-based security and access policies.
- 85% reduction in ransomware to stop attacks with detection and blocking known and unknown threats with inline AI/ML and decoys.
- 75% security FTE time saved to speed response with enriched investigations with corroborated threat intel to simplify incident response.
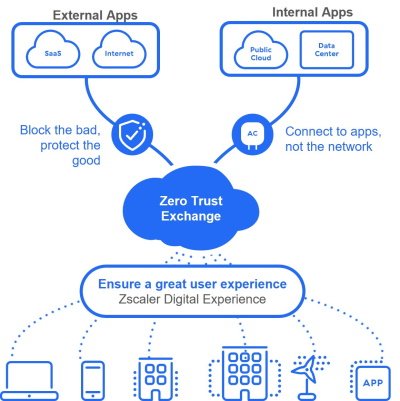
The Zscaler Zero Trust Exchange™ is an effective way to protect K-12 schools against cyberthreats and data loss while enhancing application access and user experience for hybrid education. A cloud native platform, the Zero Trust Exchange powers a complete security service edge (SSE) to connect users, workloads, and devices without putting them on the organization's network. It reduces the security risks and complexity associated with perimeter-based security solutions that extend the network, expand the attack surface, increase the risk of lateral threat movement, and fail to prevent data loss.
Visit our Zscaler for Education page for more information about how we are working with K-12 and higher education to secure the education sector with zero trust.
Other resources that may be of interest:
White Paper: Using Zero Trust to Defend Against Every Stage of a Ransomware Attack
Securing Access for K-12 Digital Environments at School and Home
SSL Inspection: Keeping K-12 Students and Schools Safe
Integration Solution Brief: saasyan and Zscaler





