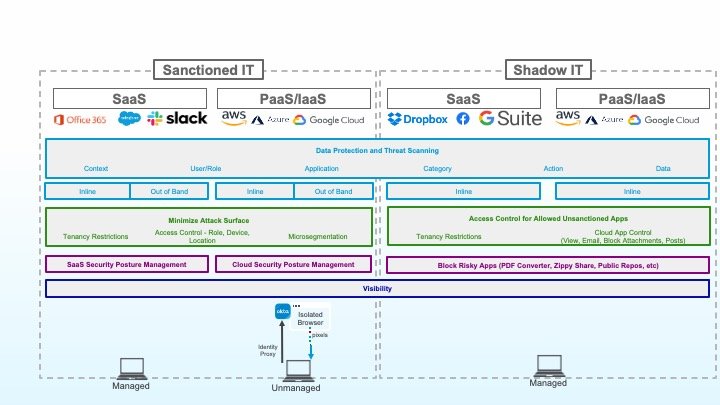
Data Loss Prevention (DLP) is the first term that comes to mind for most when thinking about data protection, but DLP is really just one piece of a broader cloud data protection strategy. DLP must build on a solid foundation of comprehensive visibility, a solid security posture, and a minimized attack surface. There are six critical challenges to laying this foundation.
Six Critical Cloud Data Protection Challenges
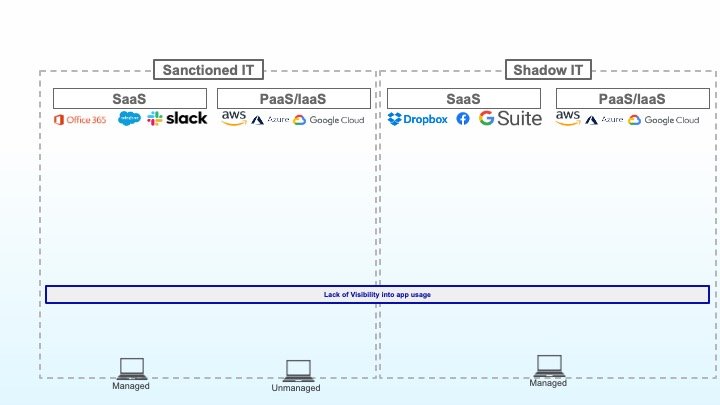
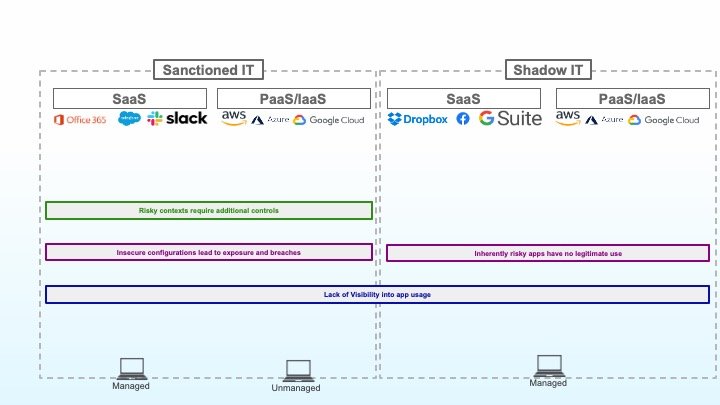
1: Lack of visibility into application usage.
You can’t protect what you don’t know about, so the first challenge to overcome is a lack of visibility into application usage. Visibility must extend across both your sanctioned IT landscape and your shadow IT landscape.
With sanctioned applications, you need insights into what applications are in use, and how they are being used. For example, insights into which AWS services your development team is using, or which third-party applications are connected to Office 365, will help you understand where they may be weaknesses in your data protection strategy.
With shadow IT applications, visibility provides the basis for deciding what to allow, what to restrict, and what to block altogether. Keep in mind that shadow IT doesn’t just mean SaaS applications - there are many PaaS/IaaS services now being used outside of IT’s purview. Protecting those applications is every bit as critical as getting a handle on shadow IT SaaS applications.
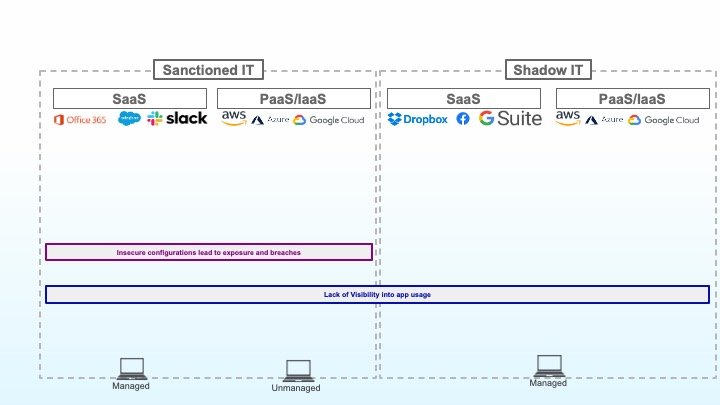
2: Insecure Configurations lead to exposure and breaches
Next up, the baseline configuration of your sanctioned applications must be properly secured. On this front, misconfiguration of cloud storage services has led to many high-profile exposures of sensitive data over the past few years, but these types of misconfigurations occur with all types of cloud applications. Overcoming this challenge means identifying and tackling identity, encryption, networking, third-party connections and sharing, and a whole host of other configurations that can result in loss of sensitive data if not appropriately secured.
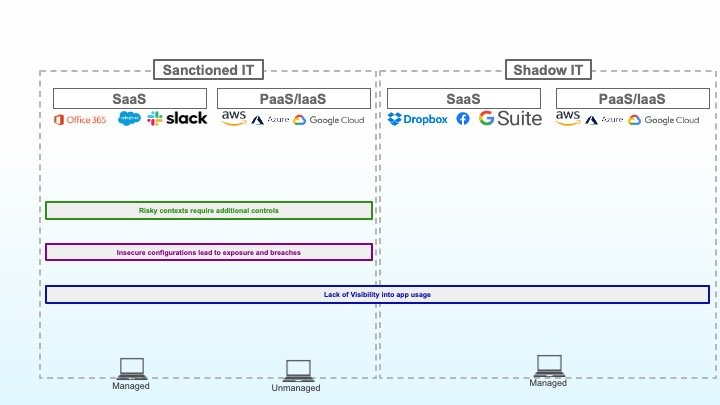
3: Risky contexts require additional controls
A privileged user on a managed device that has been appropriately protected has a different risk profile than that same user on an unmanaged device, coming from a new location, and attempting to download sensitive data. Context is key to strong access control, ensuring that the level of access provided corresponds to the risk of data loss given that context.
4: Inherently risky apps have no legitimate business use
Shifting gears to focus on shadow IT, there are some inherently risk applications that have no legitimate business use. Applications that are known to host malware, apps with questionable data protection policies, previously unknown applications, and a broad range of undesirable categories of applications all should be blocked outright on corporate networks and devices.
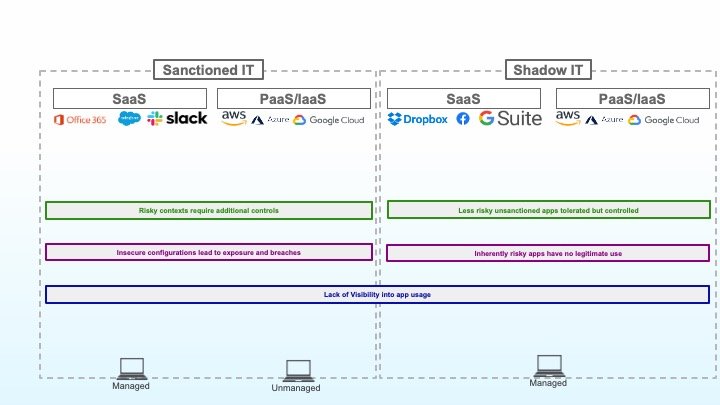
5: Less risky sanctioned apps tolerated but controlled
Not all shadow applications can be blocked. Today’s workers expect some ability to perform low-risk personal activities from their managed devices and from the corporate network. Sending personal emails, taking a break to check out The Gram, paying bills online. These are all applications that you are more than likely going to end up allowing but in a controlled fashion.
You might want to allow social media viewing but prohibit posting. Or perhaps you want to give employees the ability to read and send emails, but not upload attachments. These access control capabilities can help reduce risk, even before you apply DLP policies.
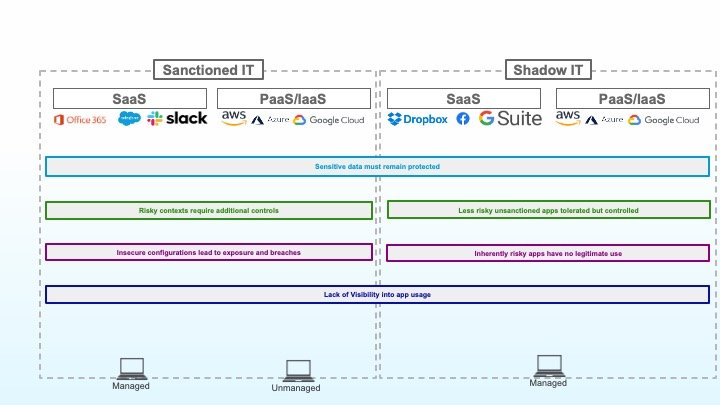
6: Sensitive data must remain protected
The final piece of the puzzle is protecting sensitive data. At this point, you’ve understood which cloud applications are in use and how, you’ve built a strong security posture for those applications, and you’ve used access control to further limit the risky contexts and behaviors that shouldn’t even be able to access sensitive data.
The final step is to leverage DLP, both inline and out-of-band, to control which data can be accessed and by whom.
Solving the six cloud data protection challenges
Taking all of this on at once might seem daunting. After all, who has the budget, team, and time to buy, implement, and maintain six separate tools from six different vendors?
Fortunately, Zscaler has built all of the capabilities necessary for you to overcome all cloud data protection challenges, across the entire landscape of sanctioned and shadow IT applications. Comprehensive data protection, built on the Zero Trust Exchange platform that is already proven and deployed across thousands of enterprises. In fact, if you’re already a Zscaler customer, enabling these capabilities might be as easy as taking a few minutes to configure them.