
What will it take to secure the future of manufacturing? Disrupting 30 years of legacy tech
Apr 15, 2025
In a firewall-free factory, security policies are not tied to physical networks—they follow the user, device, and workload dynamically.
The manufacturing renaissance spurred by smart factories and industrial automation is a double-edged sword: On one side is value and modernization, and on the other is its side-effect, a massive expansion in attack surfaces. Unfortunately, the old way of securing it all, itself exacerbates the problem.
“Billions of dollars have been and are still being poured into legacy network and security solutions,” says Deepak Patel, a Zscaler senior director overseeing product management for OT. “Thankfully, as decision makers get to truly know the business risk, the industry is starting to overcome 30-year-old inertia.”
The shortcomings of perimeter-based security
Many manufacturers still use old ways to protect their walls—VPNs, access control lists and firewalls to segment and secure their networks. It is understandable, as the industry has enough challenges to deal with. But outdated security approaches were never intended for today's connected industrial environments. “To put it simply, manufacturers need to transform their networks because otherwise it’s impossible to be secure,” according to Patel.
Legacy perimeter security assumes everything inside the network is trustworthy. This worked when factories were isolated, but now smart factories connect to the cloud, are accessed remotely, integrate with third parties, etc. The price tag for continuing with traditional security includes the following:
- Costly and complex VPNs and firewalls: Their management and maintenance puts a time- and labor-intensive burden on IT teams.
- Lateral movement: Shared VLANs allow devices to communicate between each other freely, making OT environments vulnerable to ransomware and malware spread.
- Third-party access blind spots: Suppliers and contractors often have persistent, broad network access, increasing exposure.
Examples include the ransomware attack that shut down Bridgestone Americas’ manufacturing facilities in North and Latin America for about a week in 2022. Soon later, Toyota suspended operations at all of its domestic plants in Japan after a supplier, Kojima Industries, suffered a cyberattack, leading to an output loss of about 13,000 cars.
The firewall-free factory: strengthening OT security with zero trust microsegmentation
Many companies are already making the move to agentless, zero-trust based, device-level segmentation. A major automotive company is using Zscaler solutions across their production plants, isolating every device, workload, and user from threats. By eliminating implicit trust and applying segmentation dynamically, they’re significantly reducing the attack surface.
One of the most exciting evolutions in zero trust for manufacturing is the move toward firewall-free factories. Historically, OT segmentation has relied on physical firewalls, VLANs, and access control lists (ACLs) to separate production environments from IT and external networks. But this approach has proven costly, complex, and ineffective at stopping lateral movement.
Fire your legacy firewalls
Firewalls have always been seen as the main part of industrial security. But they have problems that make them a challenge to keep managing in today's manufacturing environments.
- Operational complexity: Managing thousands of firewall rules across multiple sites and cloud environments consumes resources and is error-prone.
- High costs: Firewalls and SD-WANs require ongoing maintenance, dedicated appliances, and complex configurations that drive up costs.
- Security gaps: Firewalls assume internal traffic is safe, which makes them ineffective against insider threats and compromised devices.
True security protects individual assets, applications, and connections—not just the perimeter. By shifting to firewall-free factories, we can replace perimeter controls with zero trust microsegmentation.
How firewall-free factories work
In a firewall-free factory, security policies are not tied to physical networks—they follow the user, device, and workload dynamically. Instead of relying on IP-based segmentation, zero trust enables:
- Device-level microsegmentation: Each OT asset (PLCs, sensors, controllers, and others) is isolated in a “network of one,” stopping malware spread. Extending zero trust to LANs eliminates lateral movement without firewalls, NAC, or VLAN dependencies.
- Identity-driven access: Operators, engineers, and vendors are granted access based on who they are, not their network location.
- Zero trust remote access: Contractors and suppliers receive temporary, restricted access with full visibility and monitoring.
Agentless zero trust segmentation simplifies security by eliminating complex ACLs and firewall rules, enabling granular segmentation without infrastructure changes. It also acts as a ransomware kill switch, automatically blocking nonessential device communication to stop lateral movement without disrupting operations. This prevents ransomware from spreading across IoT and OT environments, minimizing the risk of operational downtime.
A network with Zscaler zero trust device segmentation, as in the depiction below, means the Zscaler Zero Trust Exchange is the default gateway and policy enforcement point for all traffic. It collects telemetry, learns about how factory networks work, and evolves policies to control access to IT and OT segments (after it groups them autonomously).
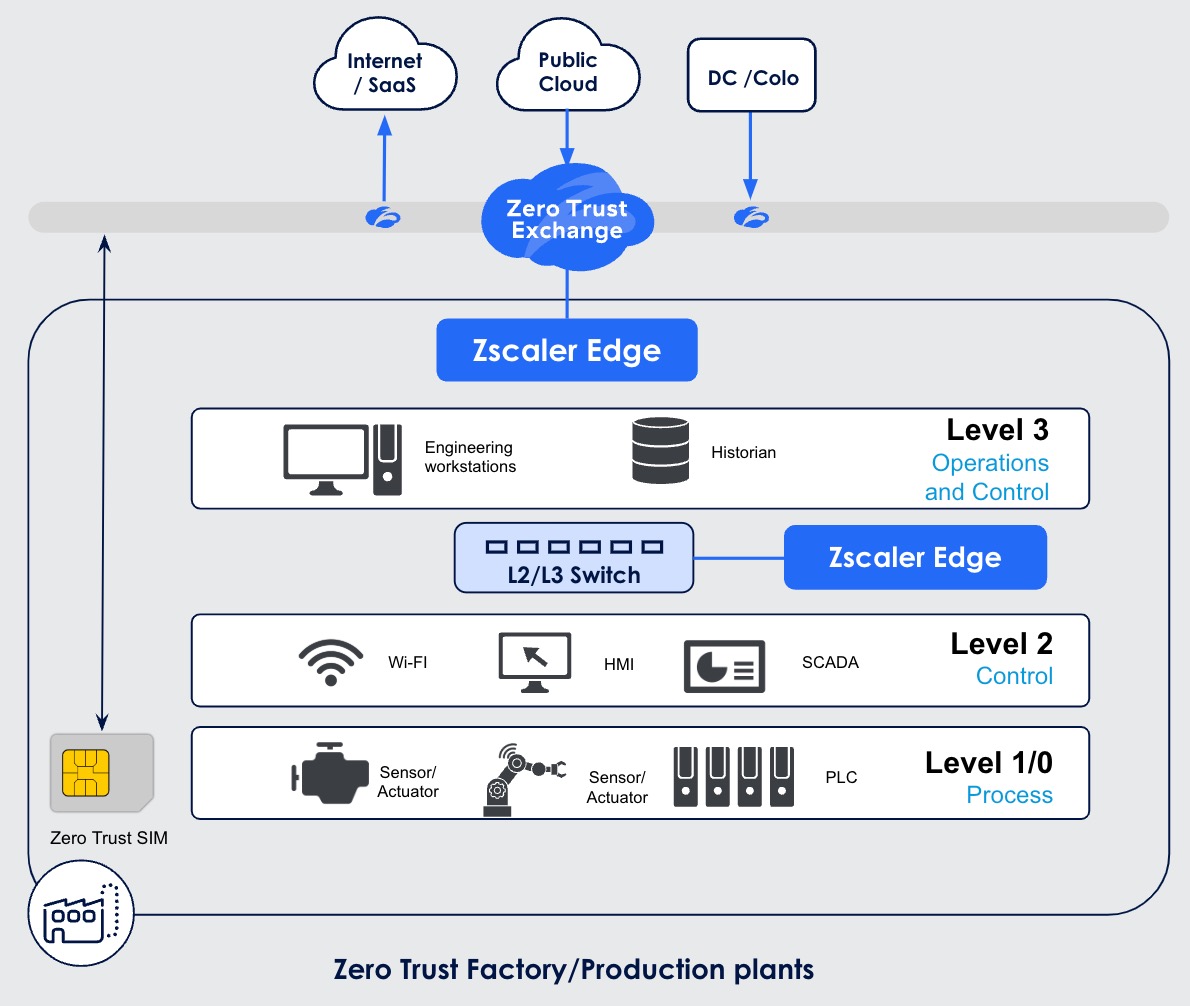
The architecture allows you to isolate OT systems into a segment of one, and restrict factory floor access to known MAC addresses. East-west firewalls, NAC appliances/agents, and micro-segmentation agents are not necessary, meaning a very small IT footprint with greater security. All this with a cratering of total cost of ownership compared to alternatives.
Advancing OT security with AI-driven zero trust segmentation
Customers are currently airgapping their factories using zero trust microsegmentation and AI-powered security automation. AI-powered segmentation enhances security and reduces operational overhead by ensuring that:
- Critical production systems remain isolated from IT and cloud environments.
- Security policies are adjusted dynamically, preventing lateral movement without manual rule-setting.
- Breach prediction technology identifies suspicious behaviors in real time, detecting and stopping threats before they escalate.
- Automated access control ensures contractors and suppliers only see what they need—without exposing our network.
By using machine learning to analyze traffic patterns, we can auto-group OT devices into a network of one, enforcing segmentation without VLAN readdressing or complex ACLs. This firewall-free model aligns with the future of manufacturing security, where protection is software-defined, AI-driven, and identity-based.
The road ahead: A zero trust blueprint for manufacturers
Manufacturers looking to modernize OT security should:
- Start with visibility: Inventory all OT, IoT, and IT devices before applying zero trust. Since most OT/IoT traffic stays local, continuous east-west visibility is critical. Automated discovery detects unauthorized assets, enforces segmentation, and improves security—without manual inventory management.
- Minimize public exposure: Ensure OT and IoT systems aren’t directly reachable from the internet to reduce risk.
- Enforce strict access controls for third-party vendors: Replace persistent, unrestricted VPN access with time-restricted, role-based access to limit supplier and contractor exposure.
- Move beyond firewalls: Segmenting OT devices shouldn’t require expensive appliances and complex rule management. Instead, use software-defined segmentation to dynamically enforce policies.
- Detect threats in real time: Implement AI-driven monitoring to detect threats before they escalate.
- Prohibit unauthorized connections: Restrict access to verified users and devices to prevent lateral movement.
- Limit unnecessary OT/IoT internet connections: Reduce risk by eliminating lateral movement.
By following these zero trust principles, manufacturers can reduce risk, shrink the attack surface, and build an OT security model that adapts to modern industrial threats.
It’s time to rethink OT security. Manufacturers need zero trust to eliminate implicit trust and continuously verify every connection. Major automotive, power management, and others are deploying it to secure OT environments and future-proof manufacturing plants. Others should follow their lead.
Recommended
